 |
The FBI is responsible for counterterrorism, foreign counterintelligence, and for addressing other national security threats. The FBI also investigates cyber crimes, public corruption, civil rights violations, organized crime, violent crimes, and other violations of federal law. FBI Headquarters in Washington, D.C., coordinates the activities of more than 30,000 employees in 56 domestic field offices, approximately 400 satellite offices, and 61 foreign liaison posts overseas that are responsible for the wide range of national security, criminal, and other matters within the FBI’s jurisdiction. |
Reports Issued
The FBI’s Use of National Security Letters in 2006
In March 2008, the OIG issued its second report evaluating the FBI’s use of national security letters (NSL). Under five statutory provisions, the FBI can use NSLs to obtain records, such as toll billing records and subscriber information from telephone companies, transactional records from Internet service providers, bank records from financial institutions, and full or limited consumer credit information from credit reporting agencies.
The USA Patriot Improvement and Reauthorization Act of 2005 (Patriot Reauthorization Act) directed the OIG to conduct two reviews of the FBI’s use of NSLs. Our first report, issued in March 2007, reviewed the FBI’s use of NSLs from 2003 through 2005. We found serious and widespread misuse of NSL authorities, such as issuing NSLs without proper authorization, making improper requests under the statutes cited in the NSLs, and conducting unauthorized collection of telephone or Internet e-mail transactional records.
In our follow-up report issued in March 2008, we determined that the FBI and the Department have made significant progress implementing recommendations in our first report and adopting corrective actions to address the serious problems we identified. Measures implemented by the FBI include a new NSL data system designed to facilitate the issuance and tracking of NSLs and ensure accurate reports to Congress and the public on NSL usage; issuing NSL guidance memoranda and conducting training of field and headquarters personnel; and creating a new Office of Integrity and Compliance modeled after private sector compliance programs. We also found that the FBI has devoted substantial time, energy, and resources ensuring that its field managers and agents understood the seriousness of the FBI’s shortcomings in its use of NSLs and their responsibility for correcting these deficiencies. In addition, the Department’s National Security Division instituted periodic national security reviews of FBI field and Headquarters divisions to assess whether the FBI was using various intelligence techniques, including NSLs, in accordance with applicable laws, guidelines, and policies.
Our report also analyzed three NSL reviews conducted by the FBI following the release of our first report. One review examined a random 10 percent sample of counterterrorism, counterintelligence, and foreign computer intrusion cyber investigation case files active in FBI field offices between 2003 and 2006. This review confirmed the types of NSL-related deficiencies and possible intelligence violations that we identified in our first report. The FBI’s statistically valid sample of field case files found a rate of NSL violations (9.43 percent) higher than what we found (7.5 percent) in the non-statistical sample of NSLs we examined in our first report.
Regarding NSL usage in 2006, we found a continued upward trend in the use of NSLs, with 49,425 NSL requests issued in 2006 – a 4.7 percent increase from the previous year. For the 4-year period, from 2003 through 2006, the FBI issued more than 192,000 NSL requests.
NSL Requests (2003 through 2006)
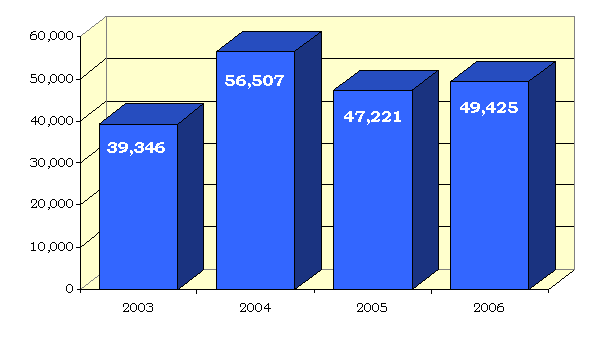
On average, approximately one-third of all counterterrorism, counterintelligence, and cyber investigations that were open at any time during 2006 employed NSLs. Our review also found that the percentage of NSL requests related to investigations of U.S. persons continued to increase, from approximately 39 percent of all NSL requests in 2003 to approximately 60 percent in 2006.
In response to the directive in the Patriot Reauthorization Act to identify any “improper or illegal” use of NSLs, we described 84 possible intelligence violations involving the use of NSLs in 2006 that were self-reported to FBI Headquarters. Of these 84 possible violations, the FBI concluded that 34 needed to be reported to the President’s Intelligence Oversight Board (IOB) in 2006. The 34 matters that were reported included errors, such as issuing NSLs without proper authorization, improper requests, and unauthorized collection of telephone or Internet e-mail records. We found that 20 of these violations were attributable to mistakes made by the FBI, while 14 resulted initially from mistakes by recipients of NSLs. The number of possible intelligence violations identified by FBI personnel in 2006 was significantly higher than the 26 violations reported from 2003 through 2005, of which 19 were reported to the IOB. We believe that the increase may be due in large part to the attention garnered by our first NSL review and to increased training, guidance, and oversight by the FBI. Although the number of self-reported violations increased, the large number of unreported violations found during the FBI’s three NSL reviews demonstrated that the overwhelming majority of violations were not identified and self-reported by the FBI.
As directed by the Patriot Reauthorization Act, we also examined whether NSLs issued after the effective date of the Patriot Reauthorization Act contained the required certifications to impose non-disclosure and confidentially requirements on NSL recipients. In the random sample of NSLs we reviewed, we found that 97 percent of the NSLs imposed non-disclosure and confidentiality requirements and almost all contained the required certifications. We found that a small percentage of the justifications for imposing this requirement were perfunctory and conclusory, and a small number of the NSL approval memoranda failed to comply with internal FBI policy.
We made 17 additional recommendations to help improve the FBI’s use and oversight of NSLs, including to provide additional guidance and training for FBI agents on the proper use of NSLs and on the reviewing, filing, and retention of NSL-derived information; reinforce the need for FBI agents and supervisors to determine whether there is adequate justification for imposing non-disclosure and confidentiality requirements on NSL recipients; regularly monitor the preparation and handling of NSLs; and provide timely reports of possible intelligence violations to FBI Headquarters. The FBI agreed with the recommendations and said it would implement additional actions to address our findings.
The FBI’s Use of Section 215 Orders for Business Records in 2006
In March 2008, the OIG issued a follow-up report on the FBI’s use of Section 215 orders to obtain business records. Section 215 of the USA Patriot Act allows the FBI to seek an order from the Foreign Intelligence Surveillance Act (FISA) Court to obtain “any tangible thing,” including books, records, and other items, from any business, organization, or entity provided that the item or items are for an authorized investigation to protect against international terrorism or clandestine intelligence activities.
Our first report, issued in March 2007, examined the FBI’s use of this authority from 2002 through 2005. The Department’s Office of Intelligence Policy and Review, on behalf of the FBI, submits two different types of Section 215 applications to the FISA Court: “pure” Section 215 applications and “combination” Section 215 applications. A “pure” Section 215 application refers to a Section 215 application for any tangible item, and it is not associated with any other FISA authority. A “combination” Section 215 application refers to a Section 215 request that is added to a FISA application for pen register/trap and trace orders, which identify incoming and outgoing telephone numbers called on a particular line. We also found two instances involving improper use of Section 215 orders in 2005 and significant delays within the FBI and the Department in processing requests for Section 215 orders throughout the time period that we reviewed.
Our second report examined the FBI’s use of Section 215 orders in 2006 and, as required by the Patriot Reauthorization Act, the minimization procedures for business records that the Attorney General was required to adopt in 2006. We found that the FBI and the Department processed 15 “pure” Section 215 applications and 32 “combination” Section 215 applications in 2006 that were formally submitted to and approved by the FISA Court. Six additional 215 applications were withdrawn by the FBI before they were formally submitted to the FISA Court. Our review found that FBI agents encountered similar processing delays for Section 215 applications as those identified in our previous report. However, both the FBI and Office of Intelligence Policy and Review were able to expedite two Section 215 requests in 2006 when the FBI identified them as emergency requests.
Our review did not identify any illegal use of Section 215 orders in 2006. However, we found two instances when the FBI received more information than it requested in the Section 215 orders. In one case, approximately 2 months passed before the FBI recognized it was receiving additional information that was beyond the scope of the FISA Court order. The FBI reported this incident to the IOB, and the additional information was sequestered with the FISA Court. In the other case, the FBI quickly determined that it inadvertently received information not authorized by the Section 215 order and isolated the records. However, the FBI subsequently concluded that the matter was not reportable to the IOB and that it should be able to use the material as if it were “voluntarily produced” because the information was not statutorily protected. We disagreed with this conclusion, and our report recommended that the FBI develop procedures for identifying and handling information that is produced in response to, but outside the scope of, the Section 215 order.
In response to the Patriot Reauthorization Act’s directive to identify any “noteworthy facts or circumstances” related to the use of Section 215 orders, our report discussed another case in which the FISA Court twice refused to authorize a Section 215 order based on concerns that the investigation was premised on protected First Amendment activity. The FBI subsequently issued NSLs to obtain information based on the same factual predicate and without a review to ensure the investigation did not violate the subject’s First Amendment rights. We questioned the appropriateness of the FBI’s actions because the NSL statute contains the same First Amendment caveat as the Section 215 statute.
Finally, as directed by the Patriot Reauthorization Act, we examined the interim procedures adopted by the Department for Section 215 orders to minimize the retention and prohibit the dissemination of non-publicly available information about U.S. persons. We concluded that the interim minimization procedures adopted in September 2006 do not provide specific guidance for minimization procedures that the Patriot Reauthorization Act appeared to contemplate. The OIG report recommended that the Department develop specific minimization procedures related to Section 215 orders.
We provided the full classified report to Congress, the Department, the FBI, and the Office of the Director of National Intelligence.
The FBI’s Management of Confidential Case Funds and Telecommunication Costs
The OIG’s Audit Division examined the FBI’s management of confidential case funds that support its undercover activities. The FBI uses confidential funds to conceal its identity from criminals, vendors, or the public during an undercover activity or operation. The audit stemmed from a recently concluded OIG investigation in which an FBI telecommunications specialist in a field office pled guilty to stealing over $25,000 in confidential funds intended for undercover telecommunication services. The investigation also revealed that the employee took advantage of weak controls over field division confidential funds to convert FBI money for her own use.
The audit found that the FBI lacked an adequate financial system to manage confidential case funds effectively. FBI field divisions used an antiquated information system called the Financial Management System to process confidential case fund expenditures. The Financial Management System could not track details pertaining to confidential payments, such as commercial vendor names, invoice numbers, or whether a supported case was open or closed. Consequently, FBI employees were left to develop various “work-arounds” to the system in an effort to track confidential case fund requests made by FBI special agents working in undercover capacities. As a result of the audit, the FBI agreed to revise its plans for a new financial management information system to replace its antiquated system.
Since the FBI treats telephone surveillance bills as confidential case costs, the audit examined the procedures used by FBI field divisions to pay these bills. The audit discovered that the volume of undercover telephone bills, coupled with the inconsistent way various FBI field offices handled confidential case funds, resulted in the FBI routinely paying covert telecommunication costs late. These late payments sometimes resulted in telecommunication carriers terminating FBI surveillance delivery lines for non-payment.
In examining the personnel and security files of FBI field division employees who had daily access to confidential case funds, we found that nearly one-half of the sampled employees had financial histories that indicated personal monetary problems, such as late loan payments and bankruptcies. Our audit noted that the FBI had not developed procedures specifically to ensure that employees with financial concerns were not placed in situations where they could process confidential case funds without enhanced supervision.
The audit recommended that the FBI improve its processing and tracking of confidential case funds, how it tracks and pays undercover telecommunication expenses, and its oversight of confidential case fund management. The FBI agreed with the recommendations and has begun to implement them.
Implementation of the Communications Assistance for Law Enforcement Act
In 1994, Congress passed the Communications Assistance for Law Enforcement Act (CALEA) to enable court-ordered electronic surveillance in light of the rapid deployment of new technologies and wireless communication services. To facilitate CALEA implementation, Congress appropriated nearly $500 million to the Telecommunications Carrier Compliance Fund (TCCF). The Attorney General designated the FBI to manage the TCCF and reimburse telecommunications carriers for the cost of modifying equipment, facilities, or services installed or deployed before 1995.
Under CALEA, the OIG biennially reports to Congress on the equipment, facilities, and services modified to comply with CALEA requirements. Our sixth CALEA audit, issued in March 2008, found that over a 10-year period the FBI spent nearly $452 million on licensing agreements with manufacturers to provide CALEA solutions on equipment used by telecommunications carriers. In addition to these licensing agreements, the FBI directed nearly $7.5 million in TCCF funds to pay wire line carriers for deploying, activating, and testing CALEA solutions. By the end of 2007, the FBI had expended a total of $459 million in TCCF funds, and Congress rescinded over $40 million from the TCCF. Our audit found that only $5,037 remained in the TCCF, and that the FBI is working with the Department to transfer the remaining funds to the Working Capital Fund.
We also found that the FBI has continued to develop tools and implement resources to help facilitate and measure CALEA compliance of various telecommunications providers. The FBI hosted and attended forums and other types of meetings with law enforcement personnel, developed and updated its “AskCALEA” website, conducted and issued annual threat assessment surveys, and surveyed telecommunications providers regarding the status of CALEA solutions on their networks. In light of the TCCF rescissions, the FBI is concentrating its efforts on working with and testing new telecommunications providers to ensure that CALEA solutions are developed and deployed for emerging technologies.
The FBI’s Combined DNA Index System (CODIS) includes a national information repository that permits the storing and searching of DNA specimen information to facilitate the exchange of DNA information by law enforcement agencies. During this reporting period, the OIG audited several state and local laboratories that participate in CODIS to determine if they comply with the FBI’s Quality Assurance Standards and National DNA Index System (NDIS) requirements. Additionally, we evaluated whether the laboratories’ DNA profiles in CODIS databases were complete, accurate, and allowable. Below are examples of our audit findings:
The Tulsa Police Department Forensic Laboratory in Tulsa, Oklahoma, was in compliance with the standards governing CODIS activities with the following exceptions. First, the Tulsa Laboratory was storing weekly backup server tapes in a manner inconsistent with NDIS security requirements. Second, the Laboratory uploaded two forensic profiles into NDIS without making it clear which sample was from the suspect and which sample was obtained from the victim’s husband in order to eliminate him as a source of the DNA. The Laboratory agreed with and addressed all of our findings before audit work was completed. Therefore, we made no formal recommendations.
The Utah Department of Public Safety Bureau of Forensic Services Laboratory in Salt Lake City, Utah, was in compliance with the standards governing CODIS activities with the following exceptions. We noted exceptions with the Laboratory’s compliance with security requirements regarding CODIS user accounts, concurrent login restriction controls, and the frequency of changing passwords. We also found that the Laboratory stored evidence in an unsecured short-term container – a practice that did not fully comply with quality assurance standards. Finally, the Laboratory did not submit its external quality assurance audit to the FBI within the required 30 days due to a miscommunication. Laboratory officials have since taken corrective action to address these deficiencies. We made two recommendations, and the FBI agreed with both recommendations.
Investigations
During this reporting period, the OIG received 928 complaints involving the FBI. The most common allegations made against FBI employees were IOB violations, job performance failure, waste, misuse of government property, and off-duty misconduct. The OIG opened 18 cases and referred other allegations to the FBI’s Inspection Division for its review.
At the close of the reporting period, the OIG had 44 open criminal or administrative investigations of alleged misconduct related to FBI employees. The criminal investigations covered a wide range of offenses, including release of information, waste, and job performance failure. The administrative investigations involved serious allegations of misconduct. The following are examples of cases involving the FBI that the OIG’s Investigations Division handled during this reporting period:
An investigation by the OIG’s Washington Field Office led to the arrest of an FBI security specialist on charges of accepting an illegal gratuity. OIG investigators determined that the security specialist, who was responsible for negotiating, reviewing, and making recommendations for the purchase of more than $1.9 million of office shredders, accepted a paid family vacation valued at over $7,500 from the company that was awarded the shredder contract. The security specialist is on indefinite suspension from the FBI. Judicial proceedings continue.
An investigation by the OIG’s Chicago Field Office led to the arrest of an FBI financial manager on charges of embezzlement of government funds. The investigation determined that the financial manager stole funds totaling $22,425 that were designated for undercover operations for her own personal use. She also falsified receipts to make it appear that invoices were paid, but instead deposited the money into her own bank accounts. The financial manager resigned her position as a result of our investigation. Judicial proceedings continue.
An investigation by the OIG’s Washington Field Office determined that an FBI special agent, without authorization, arranged for the use of an FBI undercover real estate company to conduct a private real estate transaction – the sale of a $1.3 million home – that benefited her personal friends. The investigation also disclosed that the special agent facilitated the FBI’s lease of an apartment for undercover purposes on property where she had a personal interest and then used the apartment for unauthorized personal purposes. Although the special agent obtained approval from management before entering into the undercover rental agreement, she did not disclose to the FBI her personal ties to the property. Based on the OIG’s investigation, the FBI notified the special agent that it was proposing her dismissal for her lack of candor during the OIG investigation.
The OIG’s Dallas Field Office investigated allegations that an FBI supervisory language specialist assigned to the Language Support Program encouraged subordinates to report fraudulent time and attendance invoice statements of their work and accepted gifts from subordinates. The investigation determined that during the supervisory language specialist’s tenure there was no system to properly account for linguists’ daily hours, billing records submitted by linguists did not always match the times worked, and linguists were permitted to work off-site without proper approval. The investigation also concluded that the supervisory language specialist accepted gifts from subordinates and, in violation of contract terms and without FBI oversight, provided pre-signed blank authorization request forms for overtime/holiday pay to linguists. The FBI terminated the supervisory language specialist from her position based on her dereliction of supervisory responsibilities and her lack of candor during her OIG interview.
Ongoing Work
The FBI’s Use of Exigent Letters and Other Improper Requests
As a follow-up to our reviews of the FBI’s use of NSLs, the OIG is investigating the FBI’s use of exigent letters and other improper requests to obtain telephone records. We previously reported on a practice by which the FBI used over 700 exigent letters rather than NSLs to obtain telephone toll billing records. We determined that by issuing exigent letters rather than NSLs the FBI circumvented the NSL statutes and violated the Attorney General’s Guidelines and internal FBI policy. Our forthcoming report is examining in greater detail the FBI’s use of exigent letters and its issuance of “blanket” NSLs used to “cover” or “validate” the information obtained from exigent letters and other improper requests.
FBI Reports of Alleged Abuse of Military Detainees
The OIG is reviewing FBI employees’ observations and actions regarding alleged abuse of detainees at Guantanamo Bay, Abu Ghraib prison, and other venues controlled by the U.S. military. The OIG is examining whether FBI employees participated in any incident of detainee abuse, whether FBI employees witnessed incidents of abuse, whether FBI employees reported any abuse, and how those reports were handled by the FBI. In October 2007, a draft report was provided to the Department, FBI, Department of Defense, and Central Intelligence Agency for comment and classification review. That review is ongoing.
The FBI’s Efforts to Combat Crimes Against Children
The OIG is auditing the FBI’s ability to meet the goals of its Crimes Against Children Program. We are assessing the FBI’s efforts to establish or enhance initiatives designed to decrease the vulnerability of children regarding acts of sexual exploitation and abuse; develop a nationwide capacity to provide a rapid and effective investigative response to crimes involving the victimization of children; and enhance the capabilities of state and local law enforcement investigators through training programs, investigative assistance, and task force operations.
The FBI’s Efforts to Resolve Terrorist Threats and Suspicious Incidents
FBI guidance requires the reporting of terrorist threats and suspicious incidents to its National Threat Center Section. Threats and suspicious incidents are recorded in the FBI’s Guardian database, which enables users to enter, assign, and manage the FBI’s response to terrorism threats and suspicious activities while simultaneously allowing field offices and Joint Terrorism Task Force members to view the information. The OIG is assessing the process and guidance for recording, resolving, and sharing information on terrorism threats; the FBI’s compliance with the proper recording and resolution of threats; and the status of the FBI’s IT tools for tracking the resolution of such threats.
The FBI’s Watchlist Nomination Practices
As a follow-up to our audit of the Department’s watchlist nomination processes, we are examining in more detail the FBI’s practices for nominating individuals to the consolidated terrorist watchlist. This review includes determining if the FBI appropriately places individuals on the watchlist in a timely manner, if records are updated with new information, and if individuals are removed from the watchlist in a timely manner.
Sentinel IV: Status of the FBI’s Case Management System
The OIG is assessing the status of the Sentinel project. We are evaluating whether the FBI’s management controls and provisions of the Sentinel contract provide reasonable assurance that Sentinel will be completed on time and within budget.
Review of the FBI’s Disciplinary System
The OIG is reviewing the FBI’s system for reporting and investigating allegations of employee misconduct and for disciplining employees who are found to have committed misconduct. This is the fifth in a series of reviews of Department component disciplinary systems.
The FBI’s Foreign Language Translation Services
This review is assessing the FBI’s progress in translating foreign language material. As a follow-up to our July 2004 audit, the OIG is assessing the extent of any translation backlogs and the efforts taken by the FBI to address them. We also are determining if controls are in place to ensure appropriate prioritization of work, accurate and timely translations, and proper security of sensitive information.
The FBI’s Security Check Procedures for Immigration Applicants
The OIG is examining the FBI’s name check and fingerprint identification checks for immigration applications.