Introduction
Between December 2005 and November 2006, the Criminal Division reported 24 security incidents to DOJCERT, including 5 incidents involving potential PII loss and 10 incidents potentially involving classified information.83 The Criminal Division considers a reportable data loss to be information on lost electronic media (CD-ROM, disk, or tape), and electronic devices (BlackBerry device or laptop), or information intentionally or inadvertently released from its network. Several Criminal Division policies refer to the term “Sensitive But Unclassified” without defining it. In general, the Criminal Division considers all of its information to be sensitive and relies on the Department’s definition of the term “sensitive information.”84 The Criminal Division uses the definition of PII found in OMB Memorandum M-06-19 and therefore considers PII to be “any information about an individual” that is “maintained by an agency... which can be used to distinguish or trace an individual’s identity.” To define classified information, the Criminal Division relies on the National Security Information definition in Executive Order 12958, as Amended, Classified National Security Information, dated March 25, 2003.
Reporting Procedures
The Criminal Division uses a single Incident Response Plan for addressing the reporting of sensitive, PII, and classified computer security incidents. The division has updated its plan to conform to the DOJCERT template of November 2006 and identifies the seven categories of incidents that should be reported to DOJCERT within specified timeframes. Reporting procedures are as follows for sensitive, PII, and classified information.
Sensitive and PII Reporting Procedures
Criminal Division employees are required to report a potential sensitive computer security incident “immediately” to the division’s Information Technology Management Help Desk when it is determined that an incident has occurred. The Help Desk should then log the incident information into its ticketing database and notify the Incident Response Team consisting of the Incident Response Team Coordinator, the Information Systems Security Manager, and the Network Security Officer. The Incident Response Team members should then determine the information that needs to be collected for the initial informal incident report and provide this report either verbally or in written form to DOJCERT. Once more information becomes known, the Network Security Officer should send a formal Preliminary Incident Report to DOJCERT, usually within 24 hours.
If a computer security incident involving a potential loss of PII occurs during normal work hours, Criminal Division employees should follow the same process as when reporting a sensitive data loss, except that the Incident Response Team makes an informal verbal or written report to DOJCERT within 1 hour. The Network Security Officer is directed to follow up with a formal Preliminary Incident Report within 24 hours. Chart 10 shows the Criminal Division’s reporting procedures for loss of sensitive information, including PII.
Chart 10: Flowchart of Criminal Division’s Reporting Procedures for
Loss of Sensitive Information, Including PII
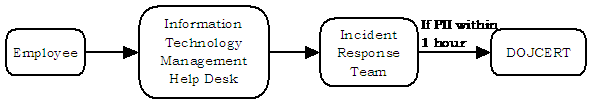
Classified Information Incidents
The Criminal Division is required to follow the procedures contained in the Department’s Security Program Operating Manual for reporting classified incidents. In addition to the notifications to the Help Desk and DOJCERT described above, the Incident Response Team also is required to notify the Department’s Security and Emergency Planning Staff (SEPS). Chart 11 shows the Criminal Division’s reporting procedures for loss of classified information.
Chart 11: Flowchart of the Criminal Division’s Reporting
Procedures for Loss of Classified Information

After-Hours Reporting Procedures
If a sensitive, PII, or classified incident occurs after normal work hours, the employee involved should call the Help Desk representative who is on-call after hours. The Help Desk should notify the Incident Response Team who then notifies DOJCERT and SEPS (if the incident involves classified information). The Help Desk or a member of the Incident Response Team is required to follow up with the employee to ensure that all of the facts about the incident are collected and the incident has been properly reported to DOJCERT via a Preliminary Incident Report. According to the Criminal Division’s Incident Response Plan, if the employee does not receive a return phone call from the Help Desk representative within 10 minutes, the employee then should report the computer security incident directly to DOJCERT. If the incident involves classified information the employee should also notify SEPS. Chart 12 shows the Criminal Division’s procedures for after-hours reporting of sensitive, PII, or classified computer security incidents.
Chart 12: Flowchart of the Criminal Division’s After-Hours Procedures for Reporting Loss of Sensitive, PII, or Classified Information
[Image Not Available Electronically]
Indications of Compliance with Reporting Procedures
Criminal Division officials told us that they believed their employees were following the correct reporting procedures. While we did not validate this statement, our analysis of the Archer Database showed that the Criminal Division was not always reporting computer security incidents, including PII, within the required timeframes specified in both the DOJCERT and Criminal Division Incident Response Plans. Between December 2005 and November 2006, the Criminal Division reported 60 percent of its computer security incidents to DOJCERT within the required timeframes. However, none of the PII incidents that occurred on or after July 12, 2006 were reported within the required 1-hour timeframe.85 Table 9 shows the Criminal Division’s reporting in each category.86
| Table 9: The Criminal Division’s Timeliness in Reporting Incidents to DOJCERT | |||||
|---|---|---|---|---|---|
| Category | Reporting timeframe* | Incidents reported | Reported within timeframe | Reported after timeframe | Could not compute timeliness** |
Category 0 (Exercise/Test) |
None |
0 |
N/A |
N/A |
N/A |
Category 1 |
1 hour |
1 |
0 |
1 |
0 |
Category 2 |
2 hours |
0 |
N/A |
N/A |
N/A |
Category 3 |
1 day |
8 |
2 |
4 |
2 |
Category 4 |
1 week |
8 |
6 |
2 |
0 |
Category 5 (Scans/Probes) |
1 month |
3 |
3 |
0 |
0 |
Category 6 (Investigation) |
None |
2 |
N/A |
N/A |
2 |
Category 7 |
1 month |
2 |
1 |
1 |
0 |
Total |
24 |
12 |
8 |
4 |
|
PII incidents occurring on or after 7/12/06*** |
1 hour |
4 |
0 |
4 |
0 |
* For purposes of this table, reporting timeframes for Categories 0-7 refer to the timeframes defined in the Incident Response Plan. Reporting timeframe for PII incidents refers to the timeframe defined in OMB Memorandum M-06-19. ** Some records did not include information to indicate when DOJCERT received the reports. Category 0 and 6 incidents, for which there are no reporting timeframes, are also included in this category. *** PII incidents were reported in varying incident categories. Source: Archer Database |
Ensuring All Incidents Are Reported
While the Criminal Division uses several methods to ensure that employees report incidents of data loss, it primarily relies on training and the Rules of Behavior. The annual Computer Security Awareness Training that is required of all Department employees includes a segment on protecting, preventing, and reporting PII loss or compromise. The Rules of Behavior require users to immediately report any evidence of tampering with a computer. A member of the Information Technology Management staff also told us that employees must read and sign the Rules of Behavior when they are hired and must review them on a yearly basis.
Additionally, Criminal Division officials told us that when each computer in the Criminal Division starts up it displays a security statement screen and gives examples of security incidents, which serves as a daily reminder to all employees of their responsibility to report incidents. The Criminal Division also said it uses a physical property inventory to identify missing electronic devices.
Notification to Affected Parties
The Criminal Division has not developed policies concerning notification to affected parties in the event of a loss of PII.
Determining the Type of Data Lost
The Criminal Division said that it generally interviews its employees and obtains a statement of facts as the primary means for determining what information was on a disk, laptop, or other electronic device that was lost, stolen, or compromised. According to one Information Technology Management official, employees “know what was on the device.”
In addition to interviewing the employee, the Criminal Division said that it has controls in place to monitor what is on electronic devices. For example, the Criminal Division said that a record is made of all e-mail that passes through a server to and from a BlackBerry device, so that if a BlackBerry device were lost, a method to identify the e-mail information on the device is available. Also, the Criminal Division said that a “kill signal” can be sent to a BlackBerry device once its loss is known, rendering it useless and the information on it inaccessible.
As of January 31, 2007, the loss of PII has been confirmed in one of these five incidents. The remaining four incidents involve potential losses of PII.
The Department’s Security Program Operating Manual defines sensitive information as “any information, the loss, misuse, modification of, or unauthorized access to, could affect the national interest, law enforcement activities, the conduct of Federal programs, or the privacy to which individuals are entitled under Section 552a of Title 5, U.S. Code, but that has not been specifically authorized under criteria established by an executive order or an act of Congress to be kept classified in the interest of national defense or foreign policy.”
We did not analyze incidents for timeliness that occurred before OMB established the 1-hour timeframe in July 2006.
Our calculations are based on Categories 1 through 5 and Category 7. We did not include incidents found in Categories 0 and 6 because they had no associated time criteria, nor did we include incidents for which the Archer Database contained no information to indicate when DOJCERT received the report that an incident had occurred.