Introduction
Between December 2005 and November 2006, the DEA reported 43 security incidents to DOJCERT, including 6 incidents involving potential PII loss and 2 incidents potentially involving classified information.87 The DEA considers a reportable computer security incident to be any loss of electronic devices that might contain sensitive information such as laptops, flash drives, removable hard drives, tapes, or CD-ROMs.
The DEA considers all of its information to be sensitive, categorizing it as either Sensitive But Unclassified, Law Enforcement Sensitive, For Official Use Only, or DEA Sensitive. The DEA defines Sensitive But Unclassified information as information subject to controls outside the formal system for classifying National Security Information and considers Sensitive But Unclassified information as exempt from release to the public under the Freedom of Information Act. Law Enforcement Sensitive information is a subset of Sensitive But Unclassified. The term For Official Use Only is used to identify information or material that, although unclassified, may not be appropriate for public release. DEA Sensitive information is information, media, or material that must be afforded a higher level of protection than Sensitive But Unclassified information. According to the DEA, this includes information and materials:
- That are investigative in nature;
- To which access is restricted by law;
- That are critical to the operation and mission of the DEA;
- That, if disclosed, would violate a privileged relationship; and
- That relate to any DEA employee’s identification or location if revealing such information would negatively affect an operation or mission.88
The DEA has adopted the definition of PII that was published in OMB Memorandum M-06-19 on July 12, 2006. The DEA broadcast this definition to all DEA employees in an e-mail from the DEA’s CIO and the DEA’s Chief Inspector on October 12, 2006.89 The broadcast e-mail defined PII as:
any information about an individual maintained by an agency, including, but not limited to, education, financial transactions, medical history, criminal or employment history, and any information which can be used to distinguish or can be traced to an individual's identity, such as their name, social security number, date and place of birth, mother's maiden name, biometric records, etc., including any other personal information which is linked or linkable to an individual.
The DEA uses the definition of classified information contained in Executive Order 12958, as Amended, Classified National Security Information, dated March 25, 2003.
Reporting Procedures
The DEA outlined its reporting procedures for DEA Sensitive, Law Enforcement Sensitive, For Official Use Only, and PII in its October 12, 2006, e-mail to all DEA employees. These procedures apply to information on electronic devices such as flash drives, laptops, hard disks, tapes, and CD-ROMs as well as to printed information. These procedures are also contained in the DEA’s eight Incident Response Plans, all of which have been updated to reflect the changes DOJCERT made to the November 2006 Incident Response Plan template.90
The DEA’s written procedures for reporting computer security incidents involving Sensitive But Unclassified information, both electronic and paper, instruct all employees to report computer security incidents immediately to the DEA Headquarters Help Desk after determining that an incident has occurred.91 The Help Desk is required to then notify the Information Security Section. The Information Security Section should then notify DOJCERT of incidents via the Archer Database. If the incident involves PII, the Information Security Section is required to report the incident to DOJCERT within 1 hour. The DEA Command Center is staffed 24 hours a day, 7 days a week. If an incident is reported outside normal business hours, the Help Desk should report it to the DEA Command Center instead of the Information Security Section, and the DEA Command Center should ensure that DOJCERT is notified within the required timeframe. Chart 13 shows the DEA’s procedures for reporting sensitive information loss, including PII.
Chart 13: Flowchart of DEA’s Reporting Procedures for Loss of Sensitive Information, Including PII
[Image Not Available Electronically]
Incidents involving classified information must be reported following the same procedures as outlined in the Incident Response Plans. The DEA Incident Response Plans require the DEA to notify the Department’s Security and Emergency Planning Staff (SEPS) of all incidents involving classified information and DOJCERT. Chart 14 shows the DEA’s procedures for reporting of classified information loss.
Chart 14: Flowchart of the DEA’s Reporting Procedures for Loss of
Classified Information
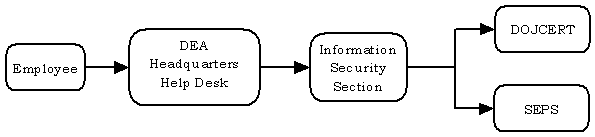
In the event a device has been stolen, the employee reporting the theft is required to contact the local police and obtain a police report, after reporting the incident to the Help Desk. The DEA should then notify other law enforcement agencies about the loss of DEA information if there is a suspicion that such loss could have an impact on those agencies. The DEA should also notify the FBI about losses resulting from the theft of government equipment of significant value.
Indications of Compliance with Reporting Procedures
DEA officials told us that they believed their employees were following the correct reporting procedures. While we did not validate this statement, our analysis of the Archer Database showed that the DEA was not always reporting computer security incidents, including PII, within the required timeframes specified in both the DOJCERT and DEA Incident Response Plans. Between December 2005 and November 2006, the DEA reported 75 percent of its computer security incidents to DOJCERT within the required timeframes. However, only 17 percent of the PII incidents that occurred on or after July 12, 2006, were reported within the required 1-hour timeframe.92 Table 10 shows the DEA’s reporting in each category.93
Table 10: The DEA’s Timeliness in Reporting Incidents to DOJCERT |
|||||
| Category | Reporting timeframe* | Incidents reported | Reported within timeframe | Reported after timeframe | Could not compute timeliness** |
|---|---|---|---|---|---|
Category 0 (Exercise/Test) |
None |
3 |
N/A |
N/A |
3 |
Category 1 |
1 hour |
7 |
2 |
5 |
0 |
Category 2 |
2 hours |
0 |
N/A |
N/A |
N/A |
Category 3 |
1 day |
8 |
4 |
2 |
2 |
Category 4 |
1 week |
2 |
1 |
1 |
0 |
Category 5 (Scans/Probes) |
1 month |
3 |
3 |
0 |
0 |
Category 6 (Investigation) |
None |
6 |
N/A |
N/A |
6 |
Category 7 |
1 month |
14 |
14 |
0 |
0 |
Total |
43 |
24 |
8 |
11 |
|
PII incidents occurring on or after 7/12/06*** |
1 hour |
6 |
1 |
5 |
0 |
* For purposes of this table, reporting timeframes for Categories 0-7 refer to the timeframes defined in the Incident Response Plan. Reporting timeframe for PII incidents refers to the timeframe defined in OMB Memorandum M-06-19. ** Some records did not include information to indicate when DOJCERT received the reports. Category 0 and 6 incidents, for which there are no reporting timeframes, are also included in this category. *** PII incidents were reported in varying incident categories. Source: Archer Database |
Ensuring All Incidents Are Reported
The DEA told us that it has taken a number of steps to ensure employees are aware of procedures for reporting computer security incidents. The DEA said that most plans or manuals are available to all DEA employees on a common server called Webster. One of the documents required for employees to review is the DEA’s Interim Information Technology Rules of Behavior that instructs employees to immediately report all security incidents or suspected incidents to the DEA Help Desk.94 Employees are required to review these Rules of Behavior when they are hired and annually thereafter.
To further reinforce these rules, the Deputy Chief Inspector in the Office of Security Programs sent a memorandum to the DEA Deputy Assistant Administrator in the Office of Information Systems advising of an amendment to the Rules of Behavior. The memorandum stated that “[a]ll personnel shall immediately report any loss of sensitive information or PII to the HELPDESK.” This requirement was further reinforced in the most recent annual Computer Security Awareness Training, which explained the requirement to protect PII information and report any loss of PII information.
Notification to Affected Parties
The DEA has not developed policies concerning notification to affected parties in the event of a loss of PII.
Determining the Type of Data Lost
The DEA said that it primarily relies on employee interviews for identifying what was on lost equipment such as laptops and BlackBerry devices. However, under certain circumstances DEA officials told us they can use computer forensics to determine what file was last accessed by an employee on a server. Doing so could suggest what information might have been downloaded to a lost laptop.
According to the DEA, its internal documents and DOJCERT and SEPS records showed that only one incident involving classified information occurred during the review period. Further, of the six incidents cited by the OIG as involving potential PII loss, only two were actual or suspected losses of PII. However, the numbers that DEA cites are not reflected in the DOJCERT’s Archer Database data, which we used for each of the nine components reviewed in our analysis. See the Purpose, Scope, and Methodology section of this report for a more detailed discussion of our method for deriving our numbers.
DEA Policy, Control and Decontrol of DEA Sensitive Information, REF 99-001, June 2, 1999.
DEA Headquarters broadcast e-mail to all DEA personnel, Personally Identifiable Information (PII) Media Loss Reporting Requirements and Procedures, October 12, 2006.
One Incident Response Plan covers several IT systems that are part of the same IT network. The remaining seven Incident Response Plans cover seven stand-alone IT systems. The procedure defined in the Incident Response Plans is the same in each of the eight plans.
However, in interviews with DEA officials we were told that the employee reporting the loss is to notify his or her direct supervisor and the supervisor is responsible for ensuring that the Help Desk is notified. Further, if a device has been reported lost or stolen, the supervisor is required to initiate a search for that device while the incident is being reported.
We did not analyze incidents for timeliness that occurred before OMB established the 1-hour timeframe in July 2006.
Our calculations are based on Categories 1 through 5 and Category 7. We did not include incidents found in Categories 0 and 6 because they had no associated time criteria, nor did we include incidents for which the Archer Database contained no information to indicate when DOJCERT received the report that an incident had occurred.
The Incident Response Plans are also on the Webster server and available to DEA employees should they need to find out how to report sensitive or PII computer security incidents.