I. DEA’S RESPONSE TO WEAPON AND LAPTOP LOSSES
- Since our 2002 audit the rate of loss for DEA laptop computers has decreased, but the rate of loss for weapons doubled from 0.61 to 1.37 weapons per month. Most important, the DEA was unable to provide assurance that the contents for 226 of 231 lost or stolen laptops did not contain sensitive information or personally identifiable information (PII). This is similar to the findings of our 2002 audit report. Additionally, while the DEA has improved some of its procedures relating to control and accountability for weapons and laptops since our previous audit, we found that the DEA did not correct several weaknesses identified in our 2002 audit. Specifically, the DEA did not timely and accurately report losses to appropriate DEA and Department officials and did not adequately ensure that lost property was entered in the NCIC database.
DEA Lost or Stolen Weapons and Laptop Computers
As shown in the following table, our 2002 audit of the DEA found that over a 26-month period 16 weapons and 229 laptop computers were lost or stolen, compared to 91 weapons and 231 laptop computers over a 66-month period in our follow-up audit. The DEA’s average monthly rate of loss for weapons increased by 225 percent, while the rate of loss for laptop computers decreased by more than 50 percent.21
DEA MISSING WEAPONS AND LAPTOP COMPUTERS
2002 AUDIT COMPARED TO FOLLOW-UP AUDIT22
| Category | Number of Lost or Stolen Items Reported |
Losses Reported Per Month |
||
|---|---|---|---|---|
| 2002 Audit |
Follow-up Audit | 2002 Audit |
Follow-up Audit | |
| Lost Government Weapons | 4 | 14 | 0.15 | 0.21 |
| Lost Personal Weapons23 | 0 | 6 | 0 | 0.09 |
| Lost Weapons, (unable to determine if government or personally owned) | 0 | 2 | 0 | 0.03 |
| Stolen Government Weapons | 12 | 43 | 0.46 | 0.65 |
| Stolen Personal Weapons | 0 | 26 | 0 | 0.39 |
| Total Lost or Stolen Weapons | 16 | 9124 | 0.61 | 1.37 |
| Lost Laptop Computers | 22925 | 206 | 8.81 | 3.12 |
| Stolen Laptop Computers | 0 | 25 | 0 | 0.38 |
| Total Lost or Stolen Laptops | 229 | 231 | 8.81 | 3.50 |
This table shows that the DEA made significant improvement in its rate of loss for laptop computers. Conversely, the DEA’s average monthly rate of loss for weapons more than doubled from our previous audit.
We recognize that some weapons and laptops will inevitably be stolen or lost. However, it is important that the DEA take appropriate steps to minimize loss. Moreover, when losses occur, the DEA must report the losses promptly, both within the DEA and to DOJ. Further, the DEA must be able to identify the contents of laptops, determine whether the laptops are encrypted, and ensure weapons and laptops are entered into the NCIC database in a timely manner.
We also compared the DEA and FBI rates of loss per employee, and found that the loss of weapons were similar. The FBI lost 3.49 weapons per 1,000 agents per year, while the DEA lost 3.36 weapons. For laptop computers, the FBI lost 3.49 per 1,000 agents per year compared to the DEA’s rate of 8.52 laptops.
DEA AND FBI MISSING WEAPONS AND LAPTOP COMPUTERS
FOLLOW-UP AUDITS COMPARISON
| Component | Special Agents | Number of Months | Weapons | Laptops | ||
|---|---|---|---|---|---|---|
| Total Weapons Lost or Stolen | Weapons Lost or Stolen Per 1,000 Agents Per Year | Total Laptop Computers Lost or Stolen | Laptop Computers Lost or Stolen Per 1,000 Agents Per Year | |||
| DEA | 4,929 | 66 | 91 | 3.36 | 231 | 8.52 |
| FBI | 12,515 | 44 | 160 | 3.49 | 160 | 3.49 |
Reporting Weapons and Laptop Computer Losses
The DEA’s Agent Manual requires the responsible employee to file a police report in the jurisdiction where the loss or theft of a weapon or laptop occurred. Additionally, the responsible employee or their immediate supervisor must ensure the weapon is entered in the NCIC database by the local police agency responsible for the jurisdiction in which the loss or theft was reported. Within 48 hours of the event, the responsible employee also must complete Part 1 of the DEA Form 29.
In October 2002 the DEA Administrator issued a memorandum requiring that all losses of laptop computers be reported within 48 hours of the incident to the DEA Board of Professional Conduct and the DEA Office of Professional Responsibility. The notification must include a full description of the laptop computer and circumstances surrounding the loss or theft. In addition, the notification must include a statement identifying whether the laptop contained any DEA sensitive or classified information.
The DEA Form 29 – Personal Property Negligence/Liability Assessment (see Appendix XI) is used to report within the DEA the loss or theft of a weapon or laptop. The form is required to be completed and signed by the employee and the employee’s supervisor. The form is used to record pertinent information related to the loss, including information about the employee; the type of property; whether the property was DEA-owned, rented, or borrowed; whether the incident was reported to the police; whether information on the property was entered into NCIC; and what happened to the property, such as was it lost, stolen, or damaged. Additionally, the form has an area to describe the item and an area for the employee to provide a statement regarding the events being reported. However, the form does not have a section for identifying the contents of the data stored on the laptop and whether the data included sensitive or PII. The form is also used to document the reporting office’s results of the initial investigation of the incident and is then forwarded to the DEA Board of Professional Conduct.
The NCIC is a database of criminal justice information, including information on criminal record histories, fugitives, stolen property, and individuals incarcerated in the federal prison system. Criminal justice agencies throughout the United States enter records into NCIC, which are then accessible to law enforcement agencies nationwide. DEA policy requires that data regarding lost or stolen weapons and laptops be promptly entered into NCIC so that the information is available to law enforcement personnel while conducting enforcement functions. The DEA is a non-record entering agency for the NCIC, meaning DEA employees do not enter data into the system. Rather, the DEA relies on local law enforcement agencies to perform this task. However, failure to enter missing weapon and laptop data into the NCIC could result in reducing the chances of recovering the item or identifying the weapon if it is used in the commission of a crime.
Our 2002 audit found that DEA employees did not always report lost or stolen weapons and laptops to the DEA in a complete and timely manner and did not ensure that all lost or stolen weapons and laptops were entered into the NCIC database. As a result, we recommended that the DEA ensure all missing weapons and laptops were promptly entered into the NCIC database and reiterate to all employees the policy for reporting losses of DEA property as outlined in the DEA Agents Manual, Section 6122.13, Loss, Theft, or Destruction of a Firearm. In response to our 2002 audit recommendations, the DEA distributed DEA-wide teletypes on July 25 and August 22, 2002, reminding Special Agents of the requirements of the Agents Manual.
Reporting Weapon Losses
During our follow-up audit, we reviewed the reporting actions taken by the DEA in response to lost or stolen weapons and laptop computers by examining DEA Forms 29 that were included as part of the DEA Board of Professional Conduct case files. The DEA was able to provide DEA Forms 29 for all 91 of the lost or stolen weapons. We also examined whether the losses were reported within 48 hours, entered into NCIC, and recovered.
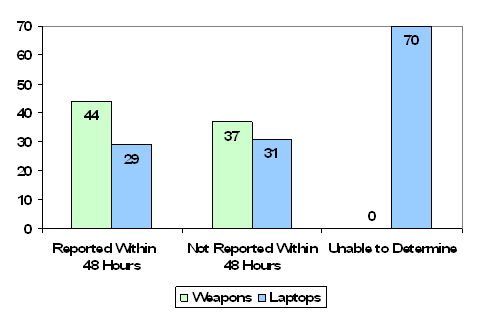
The DEA prepared 81 DEA Forms 29 reporting the 91 missing weapons (7 forms included multiple weapons). We found that 37 (46 percent) of the forms were not completed within the required 48‑hour timeframe. In 19 instances DEA personnel took over 2 weeks to report the loss, hindering a timely investigation regarding the circumstances of the loss. (Details on the number of days until losses were reported are contained in Appendix V.) In addition, 13 (16 percent) of the forms did not contain critical information, such as the correct serial number or whether the weapon was entered into NCIC. The failure of DEA to ensure that lost or stolen weapons were internally reported in a timely manner in accordance with DEA policy is a finding that we previously identified in our 2002 audit.
Timeliness of Reporting Lost or Stolen Weapon and Laptops
DEA Forms 29 Submitted
| Source: OIG analysis of DEA Board of Professional Conduct case files |
Reporting Laptop Computer Losses
We also examined 110 DEA Forms 29 for the 231 laptop computers reported missing.26 For 70 of the 110 DEA Forms 29 (64 percent) we could not determine if the forms were submitted within 48 hours as required by DEA policy because DEA personnel did not include submittal dates on the forms. We determined that 31 of the DEA Forms 29 (28 percent) were submitted late. Of these 31 forms, 20 were filed from 15 to over 1,700 days late, hindering timely investigation of the loss. We were able to determine that only 9 of the 110 DEA Forms 29 tested (8 percent) were submitted within the required timeframe. Appendix VI provides details on the number of days that laptops were reported late.
As mentioned previously, the DEA issued two teletypes in 2002 reminding Special Agents of policy regarding reporting losses of property. However, our audit results indicate that the DEA did not ensure that its staff was filing reports for lost or stolen property within the required 48 hours. DEA management needs to ensure that its staff prepares complete and accurate loss reports and submits those reports to the appropriate offices in a timely manner.
Contents of Lost or Stolen Laptop Computers
Our review of the DEA Board of Professional Conduct case files found that only 5 of the 231 lost or stolen laptop computers contained information regarding the sensitivity of the contents of the missing laptops.
For the other 226 laptops reported lost or stolen during our review period, we asked the DEA Board of Professional Conduct Chairman, Office of Professional Responsibility Deputy Chief Inspector, and Office of Security Programs Information Security Section Chief what the DEA did to determine the contents of the other lost or stolen laptop computers. In response, the DEA provided the following statement:
DEA is unable to provide, with certainty, assurance that the content of many of these laptops is not sensitive information because it does not remotely (in an automated manner) manage its laptops. The majority of DEA’s laptop computers are used as standalone computing devices. DEA’s policy prior to 2007 (Asa Hutchinson’s October 2002 Memo) did not allow sensitive data or classified information to be processed on standalone laptops. During the time prior to the PII mandate in July 2006, DEA asked only for affirmation from users that no sensitive or classified data was on the missing devices. After 2007, sensitive data was authorized to be processed on laptops that have full hard-disk encryption.
In addition to this statement, the DEA Security Programs Information Security Section Chief told us that DEA investigators attempt to determine what information may have been lost or compromised, but said there is no way to determine the contents of the missing laptop unless it is recovered. However, we found no evidence that this was done for the most of the laptops.
We asked the DEA to provide the results of any investigations it conducted to determine the contents of the 231 lost or stolen laptop computers. In response, the Office of Security Programs Information Security Section Chief was only able to provide results regarding three lost or stolen laptop computer cases. He stated that in one case the laptop contained sensitive information but was fully encrypted. In another case, the laptop was not encrypted, but did not contain Personally Identifiable Information. In the third case, the missing laptop did not contain sensitive information but did contain contract information.27 Because the DEA could not provide serial numbers for these three laptops, we could not determine whether they were part of the 231 lost or stolen laptops identified during our follow-up audit or whether these were additional losses.
In addition, since October 2002 the DEA has required that reports of lost or stolen laptops must include a statement identifying whether the laptop contained any DEA sensitive or classified information. We did not find any of these required statements in the DEA Board of Conduct case files for 226 laptops identified as lost or stolen. As a result, the DEA could not provide assurance that the laptops did not contain sensitive or PII information.
The DEA was able to confirm the contents for five of the lost or stolen laptops. Of the five, one was determined by the DEA to contain sensitive case information while the remaining four did not.
In our opinion, the DEA failed to adequately determine the contents of the lost and stolen laptops. We believe the DEA must implement policies to ensure that it identifies the contents of any lost or stolen laptops and whether these laptops contained sensitive, classified, or personally identifiable information.
Encryption of Laptop Computers
DEA reported that as of December 2007, 155 of the DEA’s 3,548 laptops that required encryption were not yet encrypted. Of the DEA’s 5,287 laptops, 1,739 were not authorized to contain sensitive information and according to DEA policy do not require encryption. In our judgment, due to the sensitivity of the data that DEA generally processes, we believe the DEA should revise its policy to ensure that all laptop computers are encrypted to minimize the risk of loss of sensitive DEA data.
As shown in the following table, 64 percent of DEA’s laptop computers had been encrypted as of December 2007.28 Of the 36 percent of laptops that were not encrypted, the DEA reported that 3 percent were in the process of being encrypted and the remaining 33 percent were exempt for encryption because they were not used to process sensitive information. According to a DEA policy, effective July 30, 2007, 1,739 laptops (33 percent) are used by Special Agents or Investigative Technology Specialist to support electronic surveillance, computer forensics, polygraph examinations and other digital monitoring functions.
DEA LAPTOP COMPUTERS ENCRYPTED
Laptops in Use as of December 2007
| Category | Number | Percent |
|---|---|---|
| Encrypted | 3,393 | 64% |
| Exempt | 1,739 | 33% |
| In Progress29 | 155 | 3% |
| Total | 5,287 | 100% |
During our fieldwork, we attempted to determine whether DEA laptops in the field offices we visited were encrypted and what data was contained on the laptops. As shown in the following table, we found that 79 of 164 laptops we examined were not encrypted. Of the 79 unencrypted laptops, we identified at least 5 that contained sensitive or personally identifiable information. In addition, the password and user ID for one of the encrypted laptops was attached to the laptop.30
NUMBER OF LAPTOPS TESTED
| Field Office | Reviewed | Encrypted | Not Encrypted |
|---|---|---|---|
| Chicago | 23 | 13 | 10 |
| Denver | 18 | 11 | 7 |
| Houston | 33 | 13 | 20 |
| Los Angeles | 47 | 5 | 42 |
| Miami | 17 | 17 | 0 |
| New York | 26 | 26 | 0 |
| Total | 164 | 85 | 79 |
Entering Losses into NCIC
DEA policy specifies that all lost or stolen personal property, including laptops, is required to be entered into NCIC. During our 2002 audit we found that the DEA did not ensure that all lost or stolen weapons were entered into the NCIC database. Specifically, we determined that 6 of the 16 lost or stolen weapons (38 percent) were not entered into the NCIC database. In this follow-up audit, we reviewed DEA loss documentation and queried the NCIC database for the 91 lost or stolen weapons. We found that 11 weapons were not entered in the NCIC database, and 7 weapons were entered with incorrect serial numbers. Serial numbers uniquely identify a weapon, and incorrect serial numbers will likely prevent an NCIC user from matching a weapon to one cataloged inaccurately in the NCIC database. We determined that 17 of the 73 weapons correctly entered in the NCIC database were recovered. Appendix VII provides details on the weapons that were not found in the NCIC database.
We determined that only two DEA Forms 29 contained enough information to show that the laptop was entered into the NCIC. There was not enough information on the DEA Forms 29 to confirm whether 229 of the 231 lost or stolen laptop computers were entered into NCIC. We queried the NCIC database for the lost or stolen laptops and found that 229 laptops did not have a record in the NCIC database.
Promptly and accurately entering information on lost and stolen weapons and laptops can assist in recovering the missing property. However, the DEA Agents Manual does not include policy pertaining to internal reporting procedures for lost or stolen laptops, including entering relevant information in the NCIC database. We believe the DEA should include procedures for reporting lost or stolen laptop computers in the manual. Further, DEA management should be required to ensure that all lost or stolen weapons and laptops have been accurately entered in the NCIC database.
Overall, we believe that the DEA still needs significant improvement in its internal reporting of lost and stolen weapons and laptop computers and in entering laptop losses into the NCIC database. Comparing our results of the DEA from this audit with those of our FBI follow-up audit, we found that the DEA and FBI were similarly poor in internally reporting weapons and laptop losses and in entering laptop losses in the NCIC database. The following table provides details of our comparison.
COMPARISON OF DEA AND FBI REPORTING
OF LOST OR STOLEN WEAPONS AND LAPTOPS
| DEA | FBI | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| YES | NO | Unable to Determine |
Total | Percent Yes |
Yes | NO | Unable to Determine |
Total | Percent Yes |
|
| Weapon Loss Reported Timely | 31 | 37 | 13 | 81 | 38% | 52 | 54 | 51 | 157 | 33% |
| Weapons Entered into NCIC | 73 | 18 | 0 | 91 | 80% | 137 | 23 | 0 | 160 | 86% |
| Laptop Loss Reported Timely | 9 | 31 | 70 | 110 | 8% | 16 | 38 | 106 | 160 | 10% |
| Laptops Entered into NCIC | 2 | 216 | 13 | 231 | 1% | 24 | 136 | 0 | 160 | 15% |
Referring and Investigating Losses
Our 2002 audit found that DEA lost or stolen weapons were reported and investigations were initiated on all 16 instances of loss. However, our previous audit also found that the DEA could not account for 229 laptops in an agency-wide reconciliation of its property inventory. In our previous audit we were also unable to test whether the DEA’s policies and procedures concerning lost or stolen laptop computers were adequate because DEA was unable to provide reliable data. Therefore, we could not determine how many lost or stolen laptop computers were reported and referred to the DEA Office of Professional Responsibility for investigation.
The DEA issued interim policy on March 30, 2007, designating the DEA Office of Professional Responsibility as the unit with the overall management of the DEA Lost or Stolen Firearm Program. The policy authorizes the Office of Professional Responsibility to determine whether it will investigate the case or refer it to the reporting office for investigation. If the case is referred to the reporting office, the office head must assign the matter for investigation to a Special Agent or Diversion Investigator who is a grade equal to or higher than the grade of the responsible employee and who is not directly associated with the responsible employee. The investigation should verify the facts and circumstances surrounding the loss, theft, or destruction as reported by the responsible employee. The investigation also should acquire facts necessary to determine whether the property was being used in an official capacity and whether personal negligence contributed to the loss or theft. According to DEA policy, a completed Report of Investigation must be submitted to the DEA Board of Professional Conduct within 30 days of the loss, theft, or destruction
As previously noted, in October 2002 the DEA Administrator issued a memorandum requiring laptop computer losses to be reported to the DEA Board of Professional Conduct and the DEA Office of Professional Responsibility within 48 hours of the incident. However, the DEA Board of Professional Conduct Chairman told us during our current audit that not all lost or stolen weapon and laptop cases have been referred for investigation to the DEA Office of Professional Responsibility. Weapons and laptops that were reported by the DEA field offices as lost or stolen were only referred by the Board of Professional Conduct to the Office of Professional Responsibility if documentation presented in the report indicated some form of misconduct was involved in the loss, theft, or destruction of the weapon or laptop.
The following table summarizes the total number of lost or stolen weapons and laptop computers that were referred to the Office of Professional Responsibility for investigation.
REFERRALS AND INVESTIGATIONS OF
WEAPON AND LAPTOP LOSSES
January 1, 2002, through June 30, 2007
| Category | Referred to the DEA Office of Professional Responsibility |
Not Referred to the DEA Office of Professional Responsibility |
Unable to Determine Whether Referred to the DEA Office of Professional Responsibility |
Total Number of Lost or Stolen Items |
|---|---|---|---|---|
| Lost Weapons | 14 | 8 | 0 | 22 |
| Stolen Weapons | 40 | 10 | 19 | 69 |
| Total Lost or Stolen Weapons | 54 | 18 | 19 | 91 |
| Lost Laptop Computers | 1 | 0 | 205 | 206 |
| Stolen Laptop Computers | 1 | 0 | 24 | 25 |
| Total Lost or Stolen Laptops31 | 2 | 0 | 229 | 231 |
Disciplining Employees Responsible for Losses
In the case of a lost or stolen weapon or laptop, the DEA Office of Professional Responsibility determines whether it will investigate the case or refer it to the reporting office for investigation. As stated previously, the Office of Deciding Officials assesses disciplinary action as deemed appropriate.
Weapon Loss
Our follow-up review of the DEA Board of Professional Conduct case files found instances when losses occurred despite reasonable precautions taken by DEA employees. However, we also found instances of lost or stolen weapons resulting from employees’ carelessness or failure to follow DEA policy. For instance, the DEA Agents Manual, Section 6122.42 Firearms Security, Safety and Storage, specifically states that DEA issued and authorized personally owned weapons may not be left unattended or temporarily stored in an official government or privately owned vehicle. As shown in the following table, we found that 44 of the 69 stolen weapons (64 percent) were stolen from official government or privately owned vehicles. The weapons stolen included pistols, rifles, shotguns, and a submachine gun. Pistols accounted for 39 of the 44 weapons stolen from vehicles (89 percent). Further details of these losses are provided in Appendix III.
WEAPONS REPORTED LOST AND STOLEN BY TYPE
JANUARY 1, 2002, THROUGH JUNE 30, 2007
| Pistol | Shotgun | Rifle | Submachine Gun |
Total Weapons | |
|---|---|---|---|---|---|
| Lost: | |||||
| Inventory | 4 | 0 | 0 | 0 | 4 |
| Miscellaneous32 | 15 | 2 | 0 | 1 | 18 |
| Subtotal | 19 | 2 | 0 | 1 | 22 |
| Stolen: | |||||
| From Official Government Vehicle | 31 | 2 | 2 | 1 | 36 |
| From Privately Owned Vehicle | 8 | 0 | 0 | 0 | 8 |
| From Residence | 13 | 0 | 0 | 0 | 13 |
| Other33 | 11 | 1 | 0 | 0 | 12 |
| Subtotal | 63 | 3 | 2 | 1 | 69 |
| Total | 82 | 5 | 2 | 2 | 91 |
Comparing the DEA follow-up audit results of lost and stolen weapons with the follow‑up audit results of the FBI, we found that the DEA and FBI both experienced weapons being stolen from government owned and privately owned vehicles in relatively similar rates. DEA had 44 weapons stolen from vehicles while the FBI had 58 weapons stolen from vehicles. We found that the DEA and FBI had 1.62 and 1.26 weapons stolen from vehicles per 1,000 agents per year, respectively.
We reviewed the DEA Board of Professional Conduct files to determine the actions taken for the 91 weapons that were lost or stolen. Although 91 weapons were reported as lost or stolen, multiple weapons were included in 7 cases; therefore, 81 actions were taken on these losses. The DEA‘s reviews resulted in the following 81 actions:
26 instances resulted in no disciplinary action;
46 instances resulted in suspensions of the responsible employees, ranging from 1 to 7 days;
1 instance resulted in suspension of the responsible employee for 30 days;
5 instances resulted in the employees receiving a Letter of Caution; and
3 instances resulted in the employees receiving a Letter of Reprimand.
We found that all 91 weapon losses were investigated by DEA Special Agents where the loss or theft occurred and referred to the Board of Professional Conduct as required by DEA policy. We also found that the disciplinary actions taken by the DEA appeared to be consistently imposed.
Laptop Computer Loss
Similar to the reports of lost and stolen weapons, many laptop computer losses could have been avoided if employees were more careful and complied with DEA policies. For example, one laptop was left in a taxi and another was stolen from checked luggage. As shown in the following table, the DEA could not provide the circumstances of the losses for 206 of 231 missing laptop computers (89 percent). These laptops were discovered missing during routine inventories and other unexplained circumstances. After our initial testing, the DEA was able to locate or find supporting documentation that accounted for 8 of the 206 missing laptops. The DEA identified 149 of these 206 laptops as missing (72 percent) when conducting annual laptop inventories. In addition, 4 laptops were lost after being left unattended and 26 laptops were believed to have been disposed of or transferred, but no supporting documentation was available to substantiate this claim. The DEA was unable to determine the circumstances of the loss for an additional 27 laptops. The remaining 25 laptop computers (11 percent) were reported as stolen from vehicles and other locations. Appendix IV includes more detail on reported laptop losses.
LAPTOP COMPUTERS REPORTED LOST AND STOLEN
January 1, 2002, through June 30, 2007
| Total | |
| Lost: | |
| Inventory | 149 |
| Left Unattended | 4 |
| No Documentation | 26 |
| Unknown | 27 |
| Subtotal | 206 |
| Stolen: | |
| From Official Vehicle | 8 |
| From Residence | 1 |
| Other34 | 16 |
| Subtotal | 25 |
| Total | 231 |
As shown in the following table, the DEA and FBI follow-up audit results for stolen laptop computers, we found that the DEA and FBI both averaged nearly 1 stolen laptop computer per 1,000 agents per year. We also noted that the DEA had 8 laptops stolen from official vehicles while the FBI had 23 laptops stolen in such a manner. The DEA averaged 0.30 laptops stolen from vehicles per 1,000 agents per year, compared to the FBI’s rate of 0.50 laptops.
FOLLOW-UP AUDIT COMPARISON OF
DEA AND FBI LAPTOP COMPUTERS STOLEN AND
LAPTOP COMPUTERS STOLEN FROM VEHICLES
| Component | Special Agents | Number of Months | Total Laptops Stolen | Laptops Stolen Per 1,000 Agents Per Year | Total Laptop Computers Stolen From Vehicles | Laptop Computers Stolen From Vehicles Per 1,000 Agents Per Year |
|---|---|---|---|---|---|---|
| DEA | 4,929 | 66 | 25 | 0.92 | 8 | 0.30 |
| FBI | 12,515 | 44 | 44 | 0.96 | 23 | 0.50 |
We reviewed the DEA Board of Professional Conduct files to determine the actions taken for the 231 laptop computers that were lost or stolen. In several instances, multiple laptops were reported on a single DEA Form 29. We found that the 206 lost laptop computers resulted in 85 Board of Conduct cases. The DEA’s reviews of laptop losses resulted in the following 85 actions.35
Seventy-three instances involved no disciplinary action.
Two instances resulted in the responsible employees receiving a Letter of Reprimand.
Ten instances resulted in the responsible employees receiving a Letter of Caution.
We also determined that each of the 25 stolen laptops was a separate Board of Conduct case and that the following actions were taken:
Eleven instances involved no disciplinary action.
Eight instances resulted in the responsible employee receiving a Letter of Reprimand.
Four instances resulted in the responsible employee receiving a Letter of Caution.
Two instances resulted in the responsible employee receiving suspensions, one for 2 days the other for 3 days.
We found that all 231 laptop losses were referred to the Board of Professional Conduct as required by DEA policy, and that that disciplinary actions taken by the DEA appeared to be administered consistently. For 226 laptops, we found that the DEA was unable to determine if the laptops contained sensitive case information or PII. However, for five laptops the DEA was able to determine the laptops’ contents and one of the five contained sensitive case information.
Our follow-up audit found that the DEA decreased its rate of loss for laptop computers since our 2002 audit by more than 50 percent. In our 2002 audit report, we reported that the DEA could not determine if any of the lost, missing, or stolen DEA laptop computers resulted in a compromise of investigative information. In this audit we found that the DEA still could not determine what was on its lost or stolen laptops. We found that for 226 of the 231 lost or stolen laptops reported in our follow-up audit review period the DEA is unable to provide any assurance that the lost or stolen laptops did not contain sensitive information. In addition, we found that the DEA did not install encryption software on all of its laptop computers.
We found in this audit that the loss rate for weapons more than doubled from 0.61 to 1.37 per month since our last review. We also determined that 48 percent of the stolen weapons resulted from employees’ carelessness or failure to follow DEA policy because Special Agents left weapons in either government or personally owned vehicles.
In addition, the DEA was not ensuring that lost or stolen weapons and laptops were entered in the NCIC database as required by DEA policy. We also found that 46 percent of the Form 29s were not prepared in a timely manner. These findings mirror weaknesses that we identified in our 2002 audit.
We recommend that the DEA:
Ensure that all DEA Forms 29 submitted are complete, accurate, and promptly submitted in accordance with DEA policy.
Ensure that weapon and laptop computer losses are accurately and promptly entered into the NCIC database.
Revise the DEA Agent Manual to include procedures for actions required by DEA personnel to report lost or stolen laptop computers. At a minimum the Agent Manual should be revised to require information on laptop make, serial number, model number, NCIC record number, and a statement on the contents of the laptop and whether it contained classified, sensitive, or PII. The DEA Agent Manual should also be revised to require that the investigation of lost or stolen laptops verify the contents of any missing laptop and ensure this information is described in detail in the case files.
Revise its policy to ensure that all laptop computers are encrypted.
In our 2002 audit we reported that the DEA had significant internal control weaknesses to account for and prevent losses of property such as weapons and laptops. This follow‑up audit found that the DEA has improved its controls and procedural compliance in some areas, such as conducting physical inventories annually and ensuring adequate segregation of duties for personnel conducting inventories, performing reconciliations, and modifying the inventory system. However, we identified continued control weaknesses in several other areas. Specifically, the DEA failed to adequately maintain documentation for laptop disposals, did not report weapon and laptop computer losses to DOJ as required, and did not institute procedures to consistently ensure the return of laptop computers from separating employees.
Internal controls relevant to accountable property management are intended to provide reasonable assurance that resources are adequately safeguarded and efficiently used and that reliable data is maintained and properly reported. Management of an agency is responsible for the design, implementation, and maintenance of internal control procedures. For this audit we tested the DEA’s internal controls over weapons and laptops by assessing its internal control structure and its compliance with procedures for conducting inventories, maintaining sufficient and accurate property records, reporting incidents of loss to the DOJ, accounting for the disposal of property, and ensuring exiting employees remit DEA-issued property.
DEA’s regulations require an annual inventory of all weapons and laptop computers. In our 2002 audit report we noted that the DEA did not perform annual physical inventories of all weapons, and the duties for maintaining records of weapons were not appropriately segregated within the Firearms Training Unit. We recommended that the DEA ensure that it conducts annual physical inventories of weapons and adequately segregates the duties of staff who conduct these inventories, perform reconciliations, and modify the inventory system. We also recommended that the DEA ensure that a valid inventory is available to all Property Custodial Assistants.
During our follow-up audit we reviewed DEA-wide inventory reports for fiscal years 2002 through 2006. We noted that DEA completed annual physical inventories of its weapons and laptop computers. Additionally, we found that duties related to weapons inventory were adequately segregated within the Firearms Training Unit. We also found that a valid inventory was made available to all Property Custodial Assistants.
Reconciling Property Records to the Financial System
In our 2002 audit report we determined that the DEA’s financial system was not integrated with its weapons inventory system, which would help ensure inventory accuracy, and the financial system did not include an audit function that allowed edits made to the Weapons Database to be tracked by an automated exception report. We recommended that the DEA develop internal controls, operating manuals, audit trails, and appropriate system requirements to ensure the reliability of inventories in its weapons inventory system – the Weapons Database. In addition, DEA’s financial system was not fully integrated with the Fixed Asset Subsystem. As a result, the systems did not automatically verify whether the number of laptops actually purchased agreed with the number of items placed into inventory. We also recommended that the DEA integrate the financial system and the Fixed Asset Subsystem so that the inventory is routinely updated when a laptop computer is purchased.
In response to our recommendations, the DEA implemented the following internal controls:
Entry capability for the Weapons Database is restricted to and appropriately segregated within the Firearms Training Unit.
Field components are provided with their respective inventories for reconciliation purposes quarterly.
The accuracy of the Weapons Database is verified quarterly by Primary Firearm Instructors and annually through a physical inventory.
The DEA’s financial system still has not been integrated with the Weapons Database. However, based on our testing of the DEA’s internal controls related to the Weapons Database, we consider the control procedures instituted by the DEA to be sufficient for ensuring that information in the Weapons Database is accurate, complete, and reliable.
Weapons
We confirmed that entries into the Weapons Database are restricted to the Firearms Training Unit staff, and we found these duties were segregated within the unit to provide the DEA increased control over its weapons. We also tested the DEA’s accounting of purchased weapons by comparing purchase documents to inventory data in the Weapons Database for the period of October 1, 2005, through February 28, 2007. Our testing included verifying the name of the manufacturer, serial number, model number, and caliber. We examined 7 bulk weapons purchases totaling 525 weapons, and we did not identify any discrepancies between the information on the purchase records and in the Weapons Database.
Laptops
We determined that the financial system has been fully integrated with the Fixed Asset Subsystem used to maintain laptop computer inventories, and the DEA has implemented policy requiring properly segregated duties of staff conducting physical inventories, performing reconciliations, and modifying the property management system.
We tested the DEA’s accounting for all DEA laptop computer purchases from October 1, 2005, through February 28, 2007. Our testing included verifying purchase records to laptop inventory records maintained in the Fixed Asset Subsystem, including the name of the manufacturer, serial number, and DEA number. In total, we tested 1,056 laptop purchases. In this testing, we were unable to trace the purchase documentation to Fixed Asset Subsystem inventory records for 68 laptops (6 percent) because:
no documentation was available for 8 purchased laptops;
9 purchased laptops were not found in the inventory provided; and
insufficient documentation was provided for 51 purchased laptops.
Further, during our testing, the DEA was unable to provide the OIG with requested purchase documentation in a reasonable amount of time because the purchase documentation for laptops is not maintained at a centralized location. In order to complete our testing we had to request that the applicable field office provide the required supporting documentation. In this effort, we had to make numerous requests of some field offices to provide the supporting purchase documentation or to provide sufficient documentation to allow us to verify the laptop with the inventory system data. These delays and the 68 laptops not in the DEA inventory system indicate a need for better controls over laptop inventory records. We believe the DEA should retain copies of all disposal documentation at centralized locations in each division office to manage the program more effectively, enable quicker reconciliations, and provide adequate audit trails.
Accuracy and Completeness of Property Records in the Weapons Database and Fixed Asset Subsystem
In our 2002 audit we selected a sample of weapons and laptop computers from these systems and physically verified their existence. Also in our 2002 audit, the DEA was able to provide all sampled weapons and laptop computers for our physical verification.
During our follow-up audit we tested the accuracy and completeness of the Weapons Database and Fixed Asset Subsystem. To perform this testing we selected samples of weapons and laptops and conducted physical verifications to assess the completeness and accuracy of DEA inventories.
Weapons
To perform our testing of the accuracy and completeness of the DEA’s weapons inventory, we selected for verification purposes samples of DEA assigned weapons. Our testing included all of the unassigned stock weapons stored in the armory at the DEA Firearms Training Unit and stock weapons maintained at DEA headquarters for the Foreign-deployed Advisory Support Teams.36 In addition, we verified all DEA‑owned weapons assigned to DEA Special Agents in DEA headquarters’ offices and in DEA field offices that we visited. We also tested personally owned weapons that Special Agents were authorized to carry for official duty at these same locations.
In total, we tested 4,331 DEA-owned and 763 personally owned weapons. We were able to verify the existence of 4,320 (99.7 percent) DEA‑owned weapons and all 763 of the personally owned weapons tested. We considered that the DEA presented the weapon if it was able to physically produce the weapon or appropriate documentation supporting that the weapon existed or had been subsequently lost, stolen, destroyed, or surplused after the draw date for our statistical sample. The following table details our testing.
WEAPONS TESTED AND VERIFIED
| Location | DEA Owned | Personally Owned | ||
|---|---|---|---|---|
| Tested | Verified | Tested | Verified | |
| DEA headquarters | 388 | 388 | 189 | 189 |
| Firearms Training Unit | 3,322 | 3,321 | 0 | 0 |
| Chicago | 101 | 94 | 80 | 80 |
| Denver | 41 | 41 | 57 | 57 |
| Houston | 78 | 78 | 91 | 91 |
| Los Angeles | 171 | 168 | 91 | 91 |
| Miami | 102 | 102 | 131 | 131 |
| New York | 128 | 128 | 124 | 124 |
| TOTALS | 4,331 | 4,320 | 763 | 763 |
Overall, our testing revealed that the DEA’s inventory records for DEA‑owned weapons were generally complete and accurate. For the 11 weapons that we could not verify, the DEA provided the following reasons for being unable to produce the weapons.
For seven weapons originally located at the Chicago field division office, the DEA believes, and the DEA Weapons Database indicated, that the weapons were destroyed. However, the DEA could not provide documentation to substantiate the destruction.
Two weapons were assigned to Special Agents from the Los Angeles Field Division. These agents were on special assignments outside the division, and therefore their weapons could not be physically verified.
We determined that one weapon from our sample was an erroneous entry in the Weapons Database. The weapon could not be tested because the DEA never actually purchased the weapon.
One non-functional training weapon located at the Firearms Training Unit could never be located.
We also tested DEA records to ensure appropriate authorization was documented for DEA personnel carrying personal firearms on official duty. All DEA Special Agent personally owned weapons that we tested had appropriate approvals for carrying the firearm in an official capacity. We also verified that the weapons presented by the Special Agents were the weapons named in the authorizations.
Laptop Computers
In addition to performing verification testing of weapons, we conducted similar testing on a sample of DEA laptop computers. Our sample consisted of 3,007 of the DEA’s 7,381 total laptop computers. Similar to our weapons testing, our sample of laptops included all laptops assigned to DEA headquarters entities and the Firearms Training Unit as well as a statistical sample of laptops assigned to the field offices where we performed our fieldwork. We considered that the DEA had accounted for the laptop if it was able to present the laptop for our verification or provide documentation supporting that the laptop existed. We also accepted documentation supporting that the laptop was lost, stolen, destroyed, or surplused after the date our statistical sample was selected.
As shown in the following table, the DEA was able to account for 2,965 (99 percent) of the 3,007 laptops in our sample. The DEA was unable to provide adequate supporting documentation to confirm that 42 laptops (1 percent) assigned to DEA headquarters locations had not been either lost or stolen. In addition, we found that 20 had not been entered into the Fixed Asset Subsystem. The DEA took immediate corrective action after we brought this to their attention by adding these 20 laptops to its inventory in the Fixed Asset Subsystem.
LAPTOP COMPUTERS TESTED AND VERIFIED
| Location | Tested | Verified |
|---|---|---|
| DEA headquarters | 2,189 | 2,147 |
| Firearms Training Unit | 554 | 554 |
| Chicago | 30 | 30 |
| Denver | 19 | 19 |
| Houston | 56 | 56 |
| Los Angeles | 59 | 59 |
| Miami | 39 | 39 |
| New York | 61 | 61 |
| TOTALS | 3,007 | 2,965 |
Besides internal DEA reporting procedures discussed in Finding I that require DEA employees to report lost or stolen weapons and laptops to the DEA in a complete and timely manner. DOJ also requires all components to submit to the DOJ Justice Management Division semiannual reports on January 1 and July 1 summarizing the loss or theft of government property that occurred within the preceding 6 months. 37In our 2002 audit we found that the DEA did not submit any semiannual Department Theft Reports for 1999 and 2000, and the first semiannual report for 2001 was submitted 36 days late. In addition, the semiannual reports were inaccurate with respect to the number of weapon losses. We recommended that the DEA submit timely and complete semiannual Department Theft Reports to the DOJ.
In this follow-up audit we again examined the DEA’s submission of semiannual Department Theft Reports. Additionally, we also analyzed in this audit the DEA’s compliance with the DOJ regulations requiring all components to immediately notify the DOJCERT of incidents involving the loss of laptops. Properly reporting losses to the DOJ helps maintain the DEA’s accountability during incidents of loss. Additionally, it assists in recovering losses and mitigating any adverse impact, such as when losing a laptop with sensitive information.
DOJ Semiannual Reports
Our follow-up review found that the DEA has not corrected its deficiency in reporting to the DOJ on the weapons and laptop computers that were lost or stolen during semiannual periods. During the time period our audit covered, 11 semiannual Department Theft Reports were supposed to be submitted to the DOJ. However, the DEA was only able to provide, and DOJ only had on file, three semiannual reports (January 1 to June 30, 2005; June 1 to December 31, 2006; and January 1 to June 30, 2007). The DEA did not submit semiannual reports for all of 2002 through 2004; July 1 to December 31, 2005; and January 1 to May 31, 2006.
We also reviewed the three Department Theft Reports submitted by the DEA during our audit period and found that only one report was complete and accurate. The report for the period ending December 31, 2006, did not report as many weapons and laptops missing as compared to the files we reviewed at the Board of Professional Conduct. The report for the period ending June 30, 2007, did not report any weapons missing even though DEA records showed four weapons were reported lost during the previous 6 months. The reports for the periods ending December 31, 2006, and June 30, 2007, were submitted in a timely manner. However, we were unable to determine if the report for the period ending June 30, 2005, was submitted when required. When we asked about the eight missing reports, the Deputy Assistant Administrator, Office of Administration, told us that the administrative clerk responsible for preparing the semiannual theft reports typed over the prior reports and failed to maintain a paper or electronic copy the reports.
During the period of January 1, 2002, through June 30, 2007, 87 weapons and 200 laptops should have been reported to the DOJ on semiannual Department Theft Reports. As shown in the following table, DOJ was not aware of 67 weapons and 176 laptops that were lost or stolen because the DEA did not submit to the DOJ Justice Management Division the required semiannual Department Theft Reports. Therefore, only 20 weapons (23 percent) and 24 laptops (12 percent) were reported to the Justice Management Division as required by DOJ regulations.
ACCURACY OF DEA’S SEMIANNUAL REPORTS TO DOJ
Semiannual Reports due June 30, 2002 through June 30, 2007
| Semiannual Period Ended | Weapon Losses | Laptop Losses | ||||
|---|---|---|---|---|---|---|
| DEA Records | Reported to DOJ | Not Reported to DOJ | DEA Records | Reported to DOJ | Not Reported to DOJ | |
| 06/30/02 | 4 | 4 | 11 | 11 | ||
| 12/31/02 | 12 | 12 | 62 | 62 | ||
| 06/30/03 | 10 | 10 | 20 | 20 | ||
| 12/31/03 | 6 | 6 | 52 | 52 | ||
| 06/30/04 | 6 | 6 | 11 | 11 | ||
| 12/31/04 | 12 | 12 | 9 | 9 | ||
| 06/30/05 | 8 | 18 | (10) | 3 | 6 | (3) |
| 12/31/05 | 15 | 15 | 13 | 13 | ||
| 06/30/06 | 6 | 6 | 2 | 2 | ||
| 12/31/06 | 4 | 2 | 2 | 14 | 8 | 6 |
| 06/30/07 | 4 | 4 | 3 | 10 | (7) | |
| Total | 87 | 20 | 67 | 200 | 24 | 176 |
Department of Justice Computer Emergency Response Team
DOJCERT assists in handling computer security incidents throughout DOJ.38 DOJ regulations require all components to submit immediate reports summarizing incidents involving the loss of both classified and unclassified systems to DOJCERT.
We contacted DOJCERT officials to determine if the DEA submitted the required incident reports for laptop computers that were identified as lost or stolen during our review period. The DOJ Assistant Director, Property Management Services, told us that DOJCERT was not required to track or report lost and stolen laptops prior to May 2006 when Office of Management Budget Memorandum 06-15, Safeguarding PII was issued. In addition to emphasizing an agency’s responsibility to safeguard PII, the memorandum also reminded agencies of the responsibility to promptly report security incidents. According to the DEA, it reported 15 laptops to the Board of Professional Conduct as lost or stolen between May 2006 and June 2007. However, DOJCERT only received reports from the DEA on three laptops during this timeframe.
We discussed this issue with the Unit Chief of the Validation, Integrity, and Penetration Response Unit – the DEA office responsible for reporting lost and stolen laptop incidents to DOJCERT. The Unit Chief told us that if the DEA employee responsible for the lost or stolen laptop does not notify the DEA Help Desk of the incident, then the Validation, Integrity, and Penetration Response Unit would be unaware of the incident and thereby unable to report it to DOJCERT. The Unit Chief said that his office reported all laptop incidents reported to him by DEA personnel.
In our 2002 audit report we found that weapons excessed to law enforcement agencies were supported by proper documentation, but the DEA did not follow up with the law enforcement agencies to ensure that shipped weapons were actually received. We recommended that the DEA ensure confirmations for receipt of the weapons were documented by the Firearms Training Unit. For this follow-up audit, we again tested DEA disposal procedures for its weapons and laptop computers.
Our testing included verifying that DEA records contained proper DEA supporting documentation for destroying and excessing weapons and laptops, including the DEA Forms 12 – Receipt For Cash Or Other Items and the DEA Forms 17 – Firearms Control Record (see Appendices IX and X).39 We also reviewed documentation on confirmations from law enforcement agencies indicating receipt of DEA surplused weapons. During our follow‑up audit, we selected a statistical sample of excessed and destroyed weapons and laptop computers using the data in the DEA’s Weapons Database and Fixed Asset Subsystem for the period covering January 1, 2002, through February 28, 2007.
Weapons
According to the DEA Chief Armorer, who is responsible for surplusing and destroying DEA weapons, the General Services Administration must provide authorization before a weapon is surplused or destroyed. Weapons that are excessed or destroyed are never deleted from the Weapons Database; instead the weapon category column in the Weapons Database is updated to indicate destroyed or surplused.
Our statistical sample included 295 weapons (43 destroyed and 252 surplused) from a universe of 7,300 destroyed and surplused weapons. We found that the DEA maintained appropriate supporting documentation for all items tested, including completed DEA Forms 17 as appropriate and confirmations from local law enforcement agencies affirming their receipt of the weapons.
Laptop Computers
DEA policy states that disposal documents for laptop computers must be maintained for a period of 3 years after disposal. We selected a sample of excessed and destroyed laptop computers from the DEA’s Fixed Asset Subsystem database. Our sample included 166 disposed laptops from a universe of 3,214 destroyed and excessed laptops. Our testing found that the DEA could not provide sufficient supporting documentation for 15 of the 166 (9 percent) laptops that it disposed. For 13 of the 15 instances we found that DEA did not retain documentation concerning the disposal for 3 years as required. The DEA provided insufficient documentation to support the disposal for the other two instances.
The DEA’s laptop disposal process is decentralized, and the supporting documentation for disposals is maintained at each DEA location worldwide. During our testing, the DEA was unable to provide requested disposal documentation in a reasonable amount of time. We originally asked for supporting documentation for disposals on June 28, 2007. However, it took approximately 90 days to complete our testing. We had to make numerous requests of some field offices to provide supporting disposal documentation or to provide sufficient documentation to allow us to verify the disposal data with the inventory system. Along with our recommendation for the DEA to centralize its laptop inventory records, we also believe the DEA should retain copies of all disposal documentation at centralized locations in each division office to manage the program more effectively, enable quicker reconciliations, and provide adequate audit trails of disposals. This added control would also elevate the DEA’s oversight over laptop disposals and increase the overall accountability for excessing laptops.
Exit Procedures for Departing Employees
In our 2002 audit report we found that although there was a category for weapons on the DEA’s Employee Clearance Record form, details such as serial numbers or the make and model of DEA weapons assigned to the outgoing employees were not required to be included on the form. In addition, the form did not identify laptop computers as a sign-off item or provide details of the type of accountable property that was retrieved from an employee who left the DEA. We recommended that the DEA ensure that details such as property descriptions, DEA property numbers, and weapon serial numbers were included on the Employee Clearance Records for each employee separating from the agency.
The DEA Form 171a – Employee Clearance Record (see Appendix XII), is used by the DEA to document that departing personnel have returned DEA property assigned to the individual. Items such as building passes, laptops, credentials, and weapons are included on the form. The DEA requires that an Employee Clearance Record certifying that all DEA-issued property has been returned to the DEA be completed for all departing employees. The “Security Activity” section of the form addresses weapons and the “Immediate Supervisor” section addresses personal custody property items, which includes assigned laptops. The separating employee must obtain signatures of responsible officials (e.g., Primary Firearms Instructors and Property Custodial Assistants) on the Employee Clearance Record verifying that all DEA-issued weapons and laptops were turned over to the DEA before employment separation.
During our follow-up audit we reviewed Employee Clearance Records at the selected DEA field division offices. We reviewed Employee Clearance Records for departing employees for the period of January 1, 2005, through August 2, 2007. We tested the forms to verify that for weapons the make, model, caliber, and serial number was included, and the appropriate official signed the form verifying receipt of the DEA-issued weapon. Our testing found that the DEA was appropriately completing this section on the Employee Clearance Record forms, providing the DEA a sound control over the weapons assigned to departing employees.
Our review of the Employee Clearance Record forms found that appropriate DEA supervisors signed the form certifying that all personal property items had been returned by the separating employee. However, the DEA was still not documenting the Employee Clearance Records with specifics on returned laptops, particularly DEA property numbers and laptop make and model plus its serial numbers. Therefore, due to the lack of specific details used in identifying a laptop computer on the Employee Clearance Records, we were unable to determine whether the outgoing employee returned the specific DEA-issued laptop.
In 2002 the DEA revised its policy to strengthen its procedures for ensuring that departing employees return all property that was issued to them or reimburse the government for the cost of the property if it was not returned. Our review concluded that the DEA’s employee exit controls for weapons were adequate, and the DEA was complying with the associated procedures. However, our testing of Employee Clearance Records revealed that the DEA procedures to account for the proper return of DEA‑issued laptops were inadequate, thereby increasing the potential for property loss upon employee separation.
During this follow-up audit we found that the DEA has improved its internal controls over its weapons and laptop computers in some areas, such as in conducting annual physical inventories. However, our audit revealed that other deficiencies in the DEA’s control over its weapons and laptop computers continued since our previous audit. Specifically, the DEA failed to adequately maintain documentation for laptop disposals, neglected to submit required semiannual reports of weapon and laptop losses to DOJ, and did not institute adequate procedures to ensure that property is recovered from employees before they leave DEA service.
We recommend that the DEA:
Ensure that each division office maintains supporting documentation for laptop purchases and disposals.
Prepare and submit to DOJ Justice Management Division complete and accurate semiannual Department Theft Reports regarding the loss of weapons and laptop computers and to DOJCERT incident reports regarding the loss of laptop computers.
Strengthen the exit processing for departing employees to ensure that documentation on the Employee Clearance Record clearly indicates specifics on remitted laptops.
Because the audit periods were different lengths, we analyzed the rate of loss on a monthly basis.
Our review period for the 2002 audit covered 26 months, from October 1, 1999, to November 30, 2001. Our review period for the follow-up audit covered 66 months, from January 1, 2002, to June 30, 2007.
Personally owned weapons authorized for official use were not tested in the 2002 audit.
We were unable to determine whether these weapons were government owned or personally owned because the serial numbers were not in the file.
The DEA reported that it could not account for 229 laptops during the prior audit. No detail was given as to the number of lost versus stolen.
DOJCERT assists in handling computer security incidents throughout DOJ. DOJ regulations require all components to submit immediate reports summarizing incidents involving the loss of both classified and unclassified systems to DOJCERT. DOJCERT maintains a database of reported incidents. The DEA’s lack of reporting to DOJCERT is discussed in Finding II.
On March 28, 2007, the DEA submitted a memorandum to the DOJ Chief Information Officer requesting a 60-day extension, to May 31, 2007, for meeting the DOJ requirement to ensure that all unclassified laptops had encryption to protect sensitive data. This memorandum noted that the DEA began encrypting laptop computers in mid‑November 2006. The DOJ Chief Information Officer approved the DEA’s request. According to DEA policy implemented on July 30, 2007, all laptop computers used to process sensitive information must be encrypted.
DEA officials informed us that these laptops were assigned to personnel in temporary duty status, have compatibility issues with the encryption software, require additional memory, or need batteries.
Our review of the contents of laptops at the field sites visited consisted of a visual inspection of the programs and recently modified files contained on the laptops. Our review did not examine the entire contents of the laptops.
A total of 231 laptops were lost or stolen for 110 cases filed.
These weapons were lost under a variety of circumstances. For example, one weapon was left on top of a Special Agent’s car and presumably lost as he drove off. One weapon was destroyed in a bombing and another was destroyed in a fire.
These weapons were stolen under a variety of circumstances. For example, one weapon was stolen from a boat loading dock where it was left unattended. Another was placed in a briefcase and left behind in a restaurant.
These laptop computers were stolen under a variety of circumstances. For example, several laptops were reported stolen from hotels and temporary quarters. Another laptop was reported stolen from checked luggage.
Several DEA Forms 29 reported multiple lost or stolen laptops on a single form.
According to the DEA, the Foreign‑deployed Advisory Support Teams are comprised of DEA Special Agents and Intelligence Research Specialists that provide guidance and conduct bilateral investigations to identify and dismantle illicit drug trafficking and money laundering organizations in Afghanistan.
See DOJ Order 2630.2A, Protecting and Controlling Federally Controlled Property and Loss/Theft Reporting Procedures.
According to DOJCERT, computer security incidents are any unexpected, unplanned event that could have a negative impact on IT resources. Computer security incidents include the loss of both classified and unclassified systems, unauthorized removal of computer equipment, and exploited weaknesses in a computer system that allows unauthorized access to password files.
The DEA Form 12 – Receipt for Cash or Other Items and the DEA Form 17 – Firearm Control Record are forms used by the DEA to track who has custody of laptop computers and weapons.