While many of the OIG’s audits, reviews, and investigations are specific to a particular component of the Department, other work covers more than one component and, in some instances, extends to Department contractors and grant recipients. The following describes OIG audits, reviews, and investigations that involve more than one Department component.
Reports Issued
Protection of the Federal Judiciary and Federal Prosecutors
The OIG’s Evaluation and Inspections Division examined the Department’s protection of federal judges and prosecutors, the third in a series of reviews on the issue. During the past several years, threats and inappropriate communications to federal judges, U.S. Attorneys, and AUSAs have increased dramatically, growing from 592 in FY 2003 to 1,278 in FY 2008. Overall, during this 6-year period, there were 5,744 threats directed at these federal officials. Although no federal judge or AUSA was killed or seriously injured during the time period we reviewed, we found deficiencies in the USMS’s and EOUSA’s response to threats that affect their ability to protect federal officials.
We found that judges, U.S. Attorneys, and AUSAs do not consistently and promptly report threats, which hampers the ability of the USMS to protect these federal court officials from harm. Although we could not determine the precise number of unreported threats, our interviews and surveys indicate that as many as 25 percent of all threats or inappropriate communications were not reported to the USMS. We also found that in about one-quarter of the reported threats made in FY 2007 and FY 2008, 2 or more days elapsed between receipt of the threat by the judge or AUSA and when they reported the threat to the USMS. Our review recommended that the Department provide additional guidance to ensure that threats are reported promptly.
Number of Threats Against Federal Court Officials Investigated by the USMS,
FY 2003 Through FY 2008
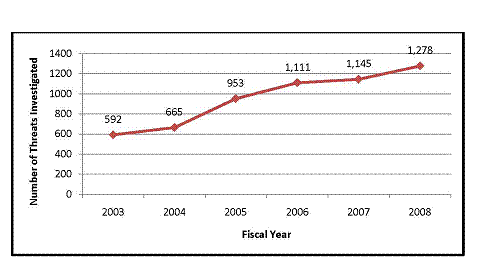
Sources: USMS FY 2008 Budget and www.ExpectMore.gov
We found that when threats are reported, the USMS does not consistently perform or document its risk assessments, and the USMS cannot ensure that protective measures are commensurate with the threats or that even the minimum protective measures are implemented. In reviewing a selected sample of threat cases involving 25 judges and AUSAs, we determined that the USMS did not record the risk level ratings for any of these threats in its threat database. Through our interviews and database review, we also determined that only 1 of the 25 judges and AUSAs received all four protective measures called for by USMS protocols. In addition, five judges and AUSAs were not provided any of the low risk level protective measures they should have received.
We also found that the USMS does not fully or effectively coordinate with other law enforcement agencies to respond to threats against federal judicial officials. Our review determined that 639 (40 percent) of the 1,587 threats in the USMS database contained no information regarding notification to the FBI, even though such notification is required by USMS policy. USMS policy also requires USMS district offices to contact local law enforcement agencies to request that the USMS be notified whenever a police agency responds to any emergency call at a judge’s residence. However, when we tested the USMS contact numbers contained in three of the letters the USMS district offices provided to local law enforcement agencies, two of the letters had non-working USMS contact numbers.
In addition, EOUSA and the USAOs have not implemented adequate measures to protect USAO personnel against threats. For example, we determined that many USAO staff members assigned security duties lack threat response expertise and training similar to that of the USMS’s judicial security staff members, who are specifically trained in threat response procedures.
USAO and USMS staff responsible for responses to threats against U.S. Attorneys and AUSAs did not consistently share important information with each other and were not cognizant of each other’s roles and responsibilities. Moreover, the USAOs were not consistently notifying EOUSA of threats against or protective measures provided to U.S. Attorneys and AUSAs. This lack of notification prevents EOUSA from providing emergency support or tracking trends in threats against USAO personnel.
In this report, the OIG made 14 recommendations to improve the protection of federal judges and prosecutors, including recommendations to improve the guidance given to federal judges, U.S. Attorneys, and AUSAs on the need for prompt reporting of threats; to ensure that the USMS provides federal judicial officials with protective measures that are commensurate with the risk level of the threat; and to ensure better coordination between the USMS, the USAOs, and other law enforcement agencies who share responsibility for protecting federal judicial officials. The USMS and EOUSA stated that they concurred with all of our recommendations and have begun implementing corrective action.
Explosives Investigation Coordination between the FBI and ATF
The OIG’s Audit Division examined the coordination between the FBI and ATF on explosives investigations. Our review found inadequate coordination between these two agencies and a lack of effective management by the Department of these agencies’ coordination efforts. We also found that conflicts occurred throughout the country regarding which agency is the lead agency for federal explosives investigations and about their differing explosives-handling techniques.
Federal law gives the FBI and ATF concurrent jurisdiction to investigate most federal explosives crimes. Despite attempts at coordination, these components have developed separate and often conflicting approaches to explosives investigations and activities such as explosives training, information sharing, and forensic analysis.
After ATF was transferred from the Department of the Treasury to the Department of Justice in 2003, the Attorney General issued a memorandum (the 2004 Memorandum) that attempted to define the roles of the FBI and ATF in explosives investigations and related activities. However, our audit found that the Department, the FBI, and ATF did not implement the 2004 Memorandum’s procedures for explosives information sharing and database consolidation, training, and laboratory resources. In addition, the 2004 Memorandum contained ambiguous directives for determining lead agency authority for explosives matters. A subsequent 2008 Memorandum of Understanding between the FBI and ATF did not clarify investigative jurisdiction and instead reiterated many of the ambiguous elements of the 2004 Memorandum.
We surveyed FBI and ATF explosives specialists, field managers, and state and local bomb squads and found that 33 percent of ATF explosives specialists and 40 percent of FBI bomb technicians reported having been involved in disputes with their counterparts at explosives incidents. The disputes primarily involved which agency should lead federal explosives investigations or which techniques should be used to neutralize explosives. These disputes can delay investigations, confuse local first responders about which agency is the federal lead on explosives matters, and undermine federal and local relationships.
The FBI and ATF maintain separate explosives-related databases to manage laboratory forensic reports, incident reporting, and technical explosives-related information and intelligence, even though the 2004 Memorandum required the FBI and ATF to consolidate their records of criminal explosives incidents reported by federal, state, and local agencies into ATF’s Bombing and Arson Tracking System (BATS). The agencies’ separate explosives databases caused a duplication of effort, and the lack of reporting to the BATS database undermined the database’s ability to accurately determine trends in explosives incidents.
The 2004 Memorandum also directed ATF to coordinate all Department post-blast explosives training and certify all explosive detection canines deployed by Department components. However, the FBI and ATF have not implemented either directive and continued to separately operate explosives-training facilities and programs and disagree on certain aspects of explosives training. In addition, the FBI and ATF each maintain separate laboratories for explosives-related analyses. The Department has not developed the guidance directed by the 2004 Memorandum on how resources and workloads should be allocated between the two agencies’ laboratories.
The OIG audit made 15 recommendations to the Department, the FBI, and ATF to improve explosives-related coordination, including: implementing a new Department directive that clearly defines jurisdiction between the agencies; establishing a formal procedure for the Department to resolve jurisdictional disputes; requiring reviews of the most efficient uses of Department explosives training programs and laboratory resources; and issuing new agency guidelines to promote explosives-incident reporting and information sharing by both agencies. The Department said it agreed in concept with each of our recommendations, and it has established four working groups, composed of representatives from the Deputy Attorney General’s Office, the FBI, and ATF, to address the recommendations of our report.
Combating Gangs and Gang Violence
The OIG’s Evaluation and Inspections Division examined two gang intelligence and coordination centers the Department established in 2006 to combat gang-operated criminal networks in the United States – the National Gang Intelligence Center (NGIC) and the National Gang Targeting, Enforcement, and Coordination Center (GangTECC).
In January 2006, NGIC was established as a multi-agency center administered by the FBI, where intelligence analysts from federal, state, and local law enforcement could work together to develop and share gang-related information. In June 2006, the Department formed GangTECC to coordinate multi-jurisdictional gang investigations. GangTECC is administered by the Criminal Division.
We concluded that the two centers have not significantly improved the coordination and execution of the Department’s anti-gang initiatives. In particular, the NGIC has not established a centralized gang information database for collecting and disseminating gang intelligence, as directed by statute, due to technological limitations and operational problems. In addition, the communications infrastructure that would allow NGIC to access gang-related information from state databases had not progressed beyond the development phase. Also, NGIC has few regular users outside of the FBI and GangTECC, receives few requests for information, and produces reports that are of limited usefulness. In discussions with NGIC and GangTECC personnel and other law enforcement officials about why NGIC was not used more frequently, we found that NGIC was not perceived as an independent, multi-agency center by many law enforcement personnel, and was repeatedly referred to as being “FBI-centric” in the products it generates and the intelligence analysis it provides.
GangTECC has a broad, multi-purpose mission but no operating budget. The lack of an operating budget has prevented GangTECC managers from taking some actions essential to its operations, including hosting case coordination meetings and conducting effective outreach to the law enforcement community. Also, GangTECC has not established itself as the central coordination and deconfliction entity as envisioned because GangTECC member agencies and federal prosecutors are not required to inform GangTECC of their gang-related investigations and prosecutions.
In examining the relationship between NGIC and GangTECC, we found that the two entities have not worked together effectively because of differing leadership and management philosophies, funding sources, and investigative priorities. While the two centers share an office suite, their co-location has not led to the anticipated partnership of NGIC and GangTECC, and communication between the two centers remains limited and ad hoc.
We made 15 recommendations to improve the Department’s anti-gang efforts, including that the Department consider merging the NGIC and GangTECC under common leadership. The Department agreed in concept with all of our recommendations. In addition, the Department stated that it is considering establishing a partnership between NGIC, GangTECC and the Organized Crime Drug Enforcement Task Force Fusion Center and the DEA’s Special Operations Division.
The Department’s Efforts to Combat Identity Theft
The OIG’s Audit Division assessed the Department’s coordination of its identity theft efforts and the specific efforts of several Department components to address the fast growing crime of identity theft. Our audit found that the Department had not taken a coordinated approach to combating identity theft and that, to some degree, identity theft initiatives had faded as priorities.
Specifically, we determined that the Department did not have its own internal strategy to combat identity theft and instead relied on a strategic plan issued by the President’s Identity Theft Task Force in April 2007. Yet, the President’s Identity Theft Task Force ceased operations in September 2008, and the Department had not appointed any individual or office to have responsibility for coordinating the Department’s identity theft efforts or ensuring further implementation of the President’s Task Force recommendations.
We found that in the absence of Department leadership and oversight, the implementation of the President’s Task Force recommendations by Department components was inconsistent. For example, one recommendation of the President’s Task Force was that Department prosecutors reevaluate their monetary thresholds for prosecuting identity theft cases. However, 53 of the 94 USAOs did not report on whether they had considered or implemented this recommendation. In addition, the audit determined that 28 of the 94 USAOs did not participate in local identity theft task forces or working groups, despite the President’s Task Force recommendation that these offices increase their use of these task forces as a way to increase identity theft prosecutions.
Our audit also determined that the Department’s Bureau of Justice Statistics (BJS), which annually conducts the National Crime Victimization Survey, was not timely in its reporting on identity theft victimization, with delays of up to 4 years in reporting data.
In 2005, the FBI created an identity theft file in the NCIC database accessible to all law enforcement agencies. The file was intended to help protect victims and identify imposters when they were encountered by state and local law enforcement. However, this feature of NCIC was underutilized and most FBI and other Department personnel we interviewed during the audit were unaware of its existence.
In addition, our audit found confusion among Department investigators, prosecutors, and victim specialists about their responsibilities under federal law to identify and notify victims of identity theft.
Our audit recommended that additional leadership is needed to ensure that the Department’s efforts to combat identity theft are coordinated and prioritized. In this regard, our report made 14 recommendations to the Department and its components, including that the Department better coordinate its identity theft efforts and that all Department components involved in identity theft issues designate an official or office with responsibility for monitoring their agency’s identity theft efforts. The Department and each of its components involved in the review concurred with the recommendations and stated that it would implement them.
The Department’s Financial Statement Audits
The Chief Financial Officers Act of 1990 and the Government Management Reform Act of 1994 require annual financial statement audits of the Department. The OIG’s Audit Division oversees and issues the reports based on the work performed by independent public accountants. During this reporting period, we issued the audit report for the Department’s Annual Financial Statement for FY 2009.
The Department received an unqualified opinion on its FY 2009 financial statements. At the consolidated level the Department had two significant deficiencies, both of which were repeat issues. The first significant deficiency related to weaknesses in the general controls environment over the financial management system for two of the Department’s nine reporting components. The Department’s other significant deficiency related to financial reporting and consists of several serious but isolated issues, including the USMS’s funds management controls; the Assets Forfeiture Fund and Seized Asset Deposit Fund’s seized and forfeited property reporting controls; OJP’s recording of budgetary upward and downward adjustments; the DEA’s process for deobligation of funds; UNICOR’s inventory count controls; and the Offices, Boards and Divisions’ process for considering economic factors in its funding analysis of its earmarked funds.
The audit found that the Department has continued to make progress in its financial management systems and has continued to address major weaknesses identified in our previous annual financial statement audits. For example, at the component level the number of significant deficiencies decreased from 14 in FY 2008 to 8 in FY 2009. The Department and its components deserve credit for these substantial improvements.
Yet, our audit noted that the Department still does not have a unified financial management system to readily support ongoing accounting operations and preparation of financial statements. As discussed in past years, we believe the most important challenge facing the Department in its financial management is to successfully implement an integrated financial management system to replace the disparate and, in some cases, antiquated financial systems used by Department components.
In the FY 2009 consolidated Independent Auditors’ Report on Compliance and Other Matters, no instances of significant non-compliance with applicable laws and regulations or other matters were identified. Although instances of non-compliance were reported at some of the components, the consolidated auditors determined that none of the component-level non-compliance issues caused the Department as a whole to be in significant non-compliance.
Federal Information Security Management Act Audits
The Federal Information Security Management Act (FISMA) requires the Inspector General for each agency to perform an annual independent evaluation of the agency’s information security programs and practices. The evaluation includes testing the effectiveness of information security policies, procedures, and practices of a representative subset of agency systems. To oversee the implementation of policies and practices relating to information security, the Office of Management and Budget (OMB) has issued guidance to agencies for their FISMA requirements.
For FY 2009, the OIG is reviewing the security programs of five Department components: the BOP, FBI, UNICOR, Justice Management Division (JMD), and USMS. Within these components, we selected for review two classified systems within the FBI and four sensitive but unclassified systems in the other components: BOP’s Hires System, UNICOR’s Services Business Group, JMD’s Interim Procurement System, and USMS’s Automated Prisoner Scheduling System. The OIG plans to issue separate reports evaluating each of these systems.
| Comparison of FY 2009 and FY 2008 Audit Results | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Reporting Entity |
Auditors’ Opinion On Financial Statements |
Number of Material Weaknesses1 |
Number of Significant Deficiencies2 |
|||||||
| Financial | Information Systems |
Financial | Information Systems |
|||||||
| 2009 | 2008 | 2009 | 2008 | 2009 | 2008 | 2009 | 2008 | 2009 | 2008 | |
| Consolidated Department of Justice | U3 | U | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 1 |
| Offices, Boards and Divisions | U | U | 0 | 0 | 0 | 0 | 1 | 1 | 0 | 0 |
| Assets Forfeiture Fund and Seized Asset Deposit Fund | U | U | 0 | 0 | 0 | 0 | 1 | 3 | 0 | 1 |
| Federal Bureau of Investigation | U | U | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 |
| Drug Enforcement Administration | U | U | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 |
| Office of Justice Programs | U | U | 0 | 0 | 0 | 0 | 1 | 1 | 0 | 1 |
| U.S. Marshals Service | U | U | 1 | 1 | 0 | 0 | 0 | 1 | 1 | 1 |
| Federal Bureau of Prisons | U | U | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 1 |
| Federal Prison Industries, Inc. | U | U | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 1 |
| Bureau of Alcohol, Tobacco, Firearms and Explosives | U | U | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 |
| Component Totals | 1 | 1 | 0 | 0 | 5 | 8 | 2 | 5 | ||
1. A material weakness is a significant deficiency (see below), or combination of deficiencies, that results in more than a reasonable possibility that a material misstatement of the financial statements will not be prevented or detected by the Departmentís internal control on a timely basis.
2. A significant deficiency is a deficiency, or combination of deficiencies, that is less severe than a material weakness, yet important enough to merit attention by those charged with governance. A deficiency in internal control exists when the design or operation of a control does not allow management or employees, in the normal course of performing their assigned functions, to prevent or detect and correct misstatements on a timely basis.
3. Unqualified opinion – An auditorís report that states the financial statements present fairly, in all material respects, the financial position and results of operations of the reporting entity, in conformity with generally accepted accounting principles.
Civil Rights and Civil Liberties Complaints
Section 1001 of the USA Patriot Act directs the OIG to receive and review complaints of civil rights and civil liberties abuses by Department employees, to publicize how people can contact the OIG to file a complaint, and to submit a semiannual report to Congress discussing our implementation of these responsibilities. On February 18, 2010, the OIG issued its 16th report summarizing its Section 1001 activities covering the period from July 1, 2009, to December 31, 2009. The report described the number of complaints we received under this section and the status of investigations conducted by the OIG and Department components.
Department Grant Funds Received by ACORN and Its Affiliates
In response to a congressional request, the OIG’s Audit Division examined whether the Association of Community Organizations for Reform Now, Inc. (ACORN) and its affiliates received any federal funds through grant programs administered by the Department since FY 2002.
The OIG review found that the Department did not award any direct grants to ACORN. We found that a recipient of a Department grant had entered into a sub-award agreement with ACORN. In addition, ACORN affiliates received one direct grant from the Department and three sub-awards from grantees of Department funds. In total, these grants and sub-awards to ACORN or its affiliates totaled approximately $200,000 between FY 2002 and FY 2009.
Our review determined that the Department components that awarded the funds did not conduct any audits or financial reviews of the five grants or sub-awards made to ACORN or its affiliates. However, the OIG issued an audit in 2008 of the National Training and Information Center (NTIC) in Chicago, Illinois, which included its $20,000 sub-award agreement with an ACORN affiliate, the American Institute for Social Justice (AISJ). Our audit found that NTIC had mismanaged the grant and did not properly oversee some of its 36 sub-grantees, including the ACORN affiliate, AISJ. The OIG audit included the full $20,000 sub-award to AISJ in the total amount of NTIC’s questioned costs.
Finally, we determined that ACORN affiliates submitted five applications for Department grant funds from FY 2003 to FY 2009 that were denied.
During this reporting period, the OIG continued to audit grants awarded by the OJP and the Office of Community Oriented Policing Services (COPS). We found that the use of some grant funds were not supported by documentation, were unallowable based on the terms and conditions of the grant, or were not used for appropriate grant expenditures.
For example, we audited the Fond du Lac Tribal and Community College in Cloquet, Minnesota, which had received $789,548 of Department grant funds as of October 28, 2009, to provide training and education to American Indians and other under-represented group members interested in a law enforcement career. Our audit found that the College’s grant records inaccurately accounted for grant-related costs, lacked adequate detail concerning an employee’s grant-funded activities, and did not implement monitoring procedures to evaluate contractor performance. Additionally, the grantee expended funds in unapproved budget categories without receiving OJP approval. In total, we identified $205,836 in unallowable or unsupported expenditures. OJP agreed with our recommendations and is working with the College to remedy these questioned costs.
Accounting and Authentication of Drug Control Funds and Related Performance
The OIG is required by 21 U.S.C. § 1704(d) to perform an annual attestation review of detailed accounting of funds expended by each drug control program and related performance summary, as implemented by the Office of National Drug Control Policy Circular, Drug Control Accounting, dated May 1, 2007. The OIG’s Audit Division oversees and issues the reports based on the work performed by independent public accountants. An attestation review is less in scope than an examination and, therefore, does not result in the expression of an opinion. However, the accountants reported that nothing came to their attention that caused them to believe the submissions were not presented in all material respects in accordance with the requirements of the Office of National Drug Control Policy Circular.
Single Audit Act Reports
OMB Circular A-133, Audits of States, Local Governments, and Nonprofit Organizations, establishes audit requirements for state and local governments, colleges and universities, and nonprofit organizations receiving federal financial assistance. Entities that expend more than $500,000 in federal financial assistance must have a “single audit” performed annually covering all federal funds received by the entity. Single audits are conducted by state and local government auditors and by independent public accounting (IPA) firms. The OIG reviews these audit reports to determine whether they meet the requirements of OMB Circular A-133 and whether they contain any audit findings related to Department grants. The OIG then issues the single audit to the Department. During this semiannual period, the OIG reviewed and issued to the Department’s granting agencies 59 single audit reports encompassing 489 contracts, grants, and other agreements totaling approximately $660 million. The OIG also monitors these audits through the resolution and closure process.
The single audits disclosed that costs charged to Department grants were not always adequately supported and that required financial reports were inaccurate and frequently were not filed in a timely manner. The state and local government auditors and IPA firms who conducted the single audits also found examples of inadequate controls over the procurement process and the equipment and assets purchased with Department grant funds. They also reported that grantees often did not adequately monitor their grant sub-recipients to ensure that the sub-grantees were properly accounting for the grant funds and ensuring compliance with the terms and conditions of the grant.Ongoing Work
The Department’s Preparations for Responding to a WMD Incident
The OIG is reviewing the Department’s preparations for responding to an incident involving a weapon of mass destruction (WMD). The review is assessing whether the Department is prepared to fulfill its responsibilities in response to a WMD attack and also whether Department components’ field offices in the National Capital Region are prepared to carry out a coordinated response if a WMD incident occurs in the Washington, D.C., area.
FBI and DEA Aviation Operations
The OIG is examining the FBI’s and DEA’s management of their aviation operations. Among other issues, this audit is reviewing the controls and criteria for deploying air-based services.
Audit of the Electronic Intergovernmental Agreement System
The OIG is evaluating whether the Electronic Intergovernmental Agreement (eIGA) system, used by the Office of the Federal Detention Trustee and the USMS to determine compensation for state and local detention facilities who house federal detainees, results in equitable reimbursement rates.
The Department’s Use of Material Witness Warrants
The OIG has initiated a review of the Department’s use of the material witness warrant statute, 18 U.S.C. 3144. The review is examining trends in the Department’s use of material witness warrants over time. The review is also examining the Department’s treatment of material witnesses in national security cases, including issues such as length of detention, conditions of confinement, and access to counsel, as well as the Department’s controls over the use of material witness warrants.