While many of the OIG’s audits, reviews, and investigations are specific to a particular component of the Department, other work covers more than one component and, in some instances, extends to Department contractors and grant recipients. The following describes OIG audits, reviews, and investigations that involve more than one Department component.
Reports Issued
The Department’s Involvement with the President’s Surveillance Program
In the weeks following the terrorist attacks of September 11, 2001, the President authorized the NSA to conduct certain classified intelligence-gathering activities intended to detect and prevent further attacks in the United States. The program was reauthorized by the President approximately every 45 days, with certain modifications. The activities carried out under these authorizations are referred to as the “President’s Surveillance Program” (PSP). Certain aspects of these activities have also been called the Terrorist Surveillance Program.
Title III of the Foreign Intelligence Surveillance Act of 1978 Amendments Act of 2008 (FISA Amendments Act) required the Department OIG, a well as OIGs from four other intelligence community agencies, to conduct a comprehensive review of the PSP. The OIG worked with the Inspectors General of the Department of Defense (DOD), Central Intelligence Agency, NSA, and Office of the Director of National Intelligence to conduct the review. On Jul. 10, 2009, as required by the FISA Amendments Act, the group submitted separate classified reports and an unclassified joint summary report to Congress.
In our 407-page classified report, the OIG’s Oversight and Review Division examined the Department’s controls over and use of information related to the PSP and the Department’s compliance with legal requirements governing the PSP. Among the major findings that are not classified, we found that only one Office of Legal Counsel attorney, Deputy Assistant Attorney General John Yoo, was cleared to work on the PSP during its first year-and-a-half of its operation. Other Department officials who were later cleared into the PSP became concerned about the factual and legal basis for Yoo’s early memoranda regarding the legality of the program and conducted a comprehensive reassessment of the legal basis for the PSP.
The OIG concluded that it was extraordinary and inappropriate that a single Department attorney was relied upon to conduct the initial legal assessment of the PSP, and that the lack of oversight and review of Yoo’s work contributed to a legal analysis of the PSP that at a minimum was factually flawed. Deficiencies in the legal memoranda became apparent once additional Department attorneys were cleared into the program in 2003 and when those attorneys sought a greater understanding of the PSP’s operation. We concluded that the strict limitations on Department access to the PSP undermined the Department’s ability to perform its critical legal function during the PSP’s early phase of operation.
Our report also described how in 2003 and 2004 certain Department officials pressed the White House not to continue the PSP without making modifications to aspects of the program. The dispute over the PSP culminated in a confrontation between Department and White House officials in the hospital room of Attorney General John Ashcroft as he recuperated from major surgery in March 2004. Following this incident, the PSP was reauthorized by then-White House Counsel Alberto Gonzales rather than the Department. The program was later modified to address concerns raised by the Department officials.
The OIG also sought as part of its review to assess the role of PSP-derived information and its value to the FBI’s overall counterterrorism efforts. The OIG interviewed FBI officials, agents, and analysts responsible for handling PSP information about their experiences with the program. These assessments generally were supportive of the program as “one tool of many” in the FBI’s anti-terrorism efforts that “could help move cases forward,” although most PSP leads were determined not to have any connection to terrorism.. The OIG found that some FBI agents and analysts criticized the PSP-derived information they received for providing insufficient details, and the agents who managed counterterrorism programs at the FBI field offices the OIG visited said that the FBI’s process for disseminating PSP-derived information failed to adequately prioritize the information for investigation. The OIG also examined several cases that have frequently been cited as examples of the PSP’s contribution to the intelligence community’s counterterrorism efforts, and we found that the PSP generally helped advance these cases. We concluded that PSP-derived information had value in some counterterrorism investigations, but it generally played a limited role in the FBI’s overall counterterrorism efforts.
The OIG also examined public statements by former Attorney General Gonzales about the PSP. Aspects of the PSP were first disclosed publicly in a series of articles in The New York Times in December 2005. Subsequently, Attorney General Gonzales was questioned about NSA surveillance activities in two public hearings before the Senate Judiciary Committee in February 2006 and July 2007. The OIG evaluated whether Attorney General Gonzales made false, inaccurate, or misleading statements to Congress in those hearings while testifying about the dispute between White House and Department officials in March 2004 concerning the PSP. The OIG concluded that Attorney General Gonzales did not intend to mislead Congress, but his testimony was confusing, inaccurate, and had the effect of misleading those who were not knowledgeable about the PSP.
The OIG also examined other aspects of the Department’s role in the PSP. For instance, certain activities that were originally authorized as part of the PSP have subsequently been authorized under orders issued by the Foreign Intelligence Surveillance Court. The OIG concluded that several considerations favored initiating the process of transitioning the PSP to FISA authority earlier than had been done, especially as the program became less a temporary response to the September 11 terrorist attacks and more a permanent surveillance tool. These considerations included the PSP’s effect on privacy interests of U.S. persons, the instability of the legal reasoning on which the Program rested for several years, and the substantial restrictions placed on FBI agents’ access to and use of Program-derived information due to the highly classified status of the PSP.
The OIG’s Evaluation and Inspections Division reviewed the Department’s efforts to detect and deter staff sexual abuse of inmates in federal prisons. We found that allegations of sexual abuse doubled from FY 2001 through FY 2008. BOP officials said they believe this increase was due to the BOP’s efforts during this period to educate and encourage staff and inmates to report such abuse.
Sexual Misconduct Allegations,
FY 2001 through FY 2008
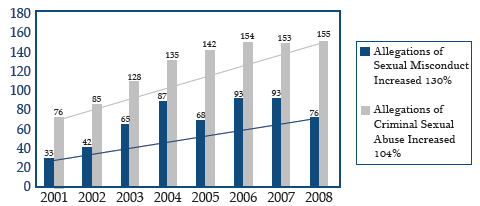
Source: BOP Office of Internal Affairs database.
Our review concluded that while the Department has made progress in implementing staff sexual abuse prevention efforts since 2001, it needs to take additional steps to effectively deter, detect, investigate, and prosecute abuse. For example, BOP officials at some prisons automatically isolate and segregate the victims and subsequently transfer them to another federal prison without first considering less restrictive options for safeguarding them from further harm. Inmates often view those actions as punitive and, as a result, may be reluctant to report their sexual abuse or cooperate with investigators.
In addition, BOP officials could not verify that all alleged inmate victims of staff sexual abuse had received appropriate victim services, such as psychological assessments and medical treatment. The OIG review also identified improvements that should be made in BOP staff training, inmate education, and program oversight.
Our review found that most staff sexual abuse investigations do not conclusively establish whether the alleged abuse occurred due to lack of physical evidence, delayed reporting, or difficulty developing further evidence without exposing the inmate to more abuse. However, since 2006 when the law changed misdemeanor sexual abuse crimes to felony crimes, the percentage of cases accepted for prosecution increased from 37 percent to 4. percent. Although some prosecutors are still reluctant to prosecute these cases, those who did had a high success rate, with all but 7 of the 90 prosecutions resulting in a conviction. We concluded that training federal prosecutors on the detrimental impact of staff sexual abuse on the inmates, on other prison staff, and on overall prison security would improve the Department’s effectiveness in prosecuting these cases. We also found that the number of defendants convicted of sexual abuse that received prison time increased after the changes to the law, but lengthier prison sentences have not resulted.
Our review also examined the USMS’s efforts to prevent sexual abuse of detainees in its custody and determined that the USMS has not established a program to prevent, detect, or investigate staff sexual abuse in its cellblocks and transportation system. While USMS officials said they believed the agency’s general policies for protecting prisoners and USMS personnel were adequate to protect against staff sexual abuse, we concluded that the USMS needs to develop policies to specifically address this issue.
The OIG made 21 recommendations to improve the Department’s efforts to prevent, detect, and respond to staff sexual abuse and better investigate, discipline, and prosecute federal personnel that sexually abuse inmates. The BOP agreed with all but two of the recommendations pertaining to its operations. In addition, the USMS agreed with our recommendations for establishing a program to address staff sexual abuse in the USMS’s cellblock and transportation operations, and the Executive Office for U.S. Attorneys (EOUSA) agreed to train prosecutors to handle staff sexual abuse cases more effectively.
The Department’s Use of Less-Lethal Weapons
The OIG’s Evaluation and Inspections Division examined the Department’s use of less-lethal weapons, including batons, pepper spray, and conducted energy devices such as Tasers. Our review found that the Department’s law enforcement components are expanding their use of less-lethal weapons, but the Department does not have specific policies to govern this use by its employees or by state and local law enforcement personnel serving on Department task forces.
The Department’s law enforcement components (FBI, ATF, DEA, USMS, and BOP) authorize and train some of their personnel to use specific less-lethal weapons. For example, FBI and DEA Special Agents are only authorized to use batons and pepper spray, while ATF, USMS, and BOP are authorized to use batons, pepper spray, “bean bag” shotgun rounds, and some form of a conducted energy device. Our review found that the use of less-lethal weapons varies widely by component. The DEA reported no use of less-lethal weapons, the FBI reported limited use, ATF and USMS statistics reported moderate but increasing use, and the BOP’s data showed the most use. There have been no reported fatalities or significant injuries resulting from the use of less‑lethal weapons by Department components during the past 5 years. However, fatalities have occurred at the state and local level, particularly following the use of Tasers or similar conducted energy devices.
Without a specific Department policy regarding the use of less-lethal weapons, Department components have developed individual policies to guide their personnel in the use of these weapons. However, all the individual policies do not address the use of these weapons by state and local task force members. For example, the FBI and the DEA do not have policies that address the use of Tasers by state and local members of their task forces, while the USMS does not mandate that state and local task force officers abide by its less-lethal weapons policies, including its Taser policy.
Although ATF, BOP, and USMS have obtained new types of less-lethal weapons in the last several years, the OIG found no coordinated Department-wide assessment of new less-lethal weapon technologies or development of use policies and training materials. Our review also found that the components were not aware of work done elsewhere in the Department, including studies funded by the National Institute of Justice, which assessed new less-lethal technologies, and investigations by the Civil Rights Division, which yielded detailed information about law enforcement policies and practices involving their use of less-lethal weapons at the state and local levels.
The OIG made four recommendations, including for the Department to coordinate the development of a Department-wide policy addressing the use of less-lethal weapons and ensure that its law enforcement components periodically analyze their use of less-lethal weapons and assess emerging trends in the use of such weapons. The Department and the components concurred with the recommendations and have begun implementing them by convening a working group to develop a Department-wide policy and by separately determining how best to analyze their less-lethal weapons use and share research on less-lethal weapons with other components.
Civil Rights and Civil Liberties Complaints
Section 1001 of the USA Patriot Act directs the OIG to receive and review complaints of civil rights and civil liberties abuses by Department employees, to publicize how people can contact the OIG to file a complaint, and to submit a semiannual report to Congress discussing our implementation of these responsibilities. On August 10, 2009, the OIG issued its 15th report summarizing its Section 1001 activities covering the period from January 1, 2009, to June 30, 2009. The report described the number of complaints we received under this section and the status of investigations conducted by the OIG and Department components.
The Department’s Management of the Federal Employees’ Compensation Act
The OIG’s Audit Division examined the Department’s management of claims submitted under its Federal Employees’ Compensation Act (FECA) program. We concluded that the Department lacks effective controls to reduce the risk of waste, fraud, and abuse in its FECA program and to ensure that employees return to work when appropriate.
Our audit focused on the five components that encompass 95 percent of the Department’s FECA costs. ATF, BOP, DEA, FBI, and USMS. We found that in comparison to other federal agencies, the Department had relatively high rates of injury, with an average rate of 4.53 injuries per 100 employees from FYs 2005 to 2008. This is the 4th highest rate of injury out of 29 major federal agencies. In addition, the Department’s overall benefit expense of $10. million for F. 2008 ranked 7th out of the 29 agencies.
Our audit determined that, with the exception of the BOP and the FBI, the other three components we audited were generally reactive rather than proactive in monitoring FECA cases. These three components also did not maintain all the information necessary to effectively manage employees’ FECA cases. For 15 percent of the cases we selected for review, no case file was maintained. In addition, 2. percent of the case files we reviewed were missing claim forms substantiating the work-related injury, 73 percent lacked evidence of a second medical opinion, and 34 percent lacked evidence of medical updates necessary to monitor an employee’s condition in order to return the employee to work when appropriate.
We determined that the Department’s weaknesses in monitoring FECA cases have resulted in a substantial amount of money that continues to be paid to employees who have remained on long-term disability without a review as to whether their current medical condition entitles them to remain on disability. While the long-term cases where the claimant remained on disability for more than 3 years were only 6 percent of the total number of the Department’s FECA cases, they. accounted for more than $153 million (or 54 percent) of the Department’s total FECA expenses from 2006 through 2008. Overall, the Department’s FECA expenses have increased an average of $6.4 million per year, the 3rd highest annual increase in the federal government since F. 2000.
The OIG made five recommendations to help improve the management of the Department’s FECA program, including implementing procedures to ensure that FECA cases are periodically reviewed, obtaining periodic medical updates and second medical opinions when necessary, and evaluating FECA cases for return-to-work opportunities or light duty assignments. The Department concurred with our recommendations.
Federal Information Security Management Act Audits
The Federal Information Security Management Act (FISMA) requires the Inspector General for each agency to perform an annual independent evaluation of the agency’s information security programs and practices. The evaluation includes testing the effectiveness of information security policies, procedures, and practices of a representative subset of agency systems. To oversee the implementation of policies and practices relating to information security, the Office on Management and Budget (OMB) has issued guidance to agencies for their FISMA requirements.
For FY 2008, the OIG audited the security programs of four Department components. the FBI, ATF, DEA, and Justice Management Division (JMD). Within these components, we selected for review two classified systems in the FBI and three sensitive but unclassified systems in other components. ATF’s Arson and Explosives Incident System, DEA’s Validation Integrity and Penetration Response System, and JMD’s Automated Configuration and Engineering System. In these five audits, we identified deficiencies in configuration management, privacy program leadership, and security awareness training. We provided more than 25 recommendations for improving implementation of the Department’s information security program and practices for its sensitive but unclassified, classified, and national security systems.
For FY 2009, we are reviewing the security programs of five Department components. the BOP, FBI, Federal Prisons Industries, Inc., (FPI), JMD, and USMS. Within these components, we selected for review two classified systems within the FBI and four sensitive but unclassified systems in the other components. BOP’s Hires System, FPI’s Services Business Group, JMD’s Interim Procurement System, and USMS’ Automated Prisoner Scheduling System. The OIG plans to issue separate reports evaluating each of these systems.
During this reporting period, the OIG continued to audit grants awarded by the Office of Justice Programs (OJP) and the Office of Community Oriented Policing Services (COPS). We continued to find the use of grant funds that were not supported by documentation or were unallowable based on the terms and conditions of the grant. In addition, we continued to find use of grant funds that were not related to grant expenditures.
For example, we audited Team Focus, Inc. (TFI) of Mobile, Alabama, which received grants of more than $2.1 million from OJP and approximately $148,000 from COPS between November 2005 and May 2008. From the $1.5 million in grants we reviewed, we identified $718,443 in questioned costs. Our audit showed that TFI drew down $273,126 in grant funds for which it had not made grant-related expenditures and charged $445,317 to grant funds that were not allowed or supported by documentation. Both OJP and COPS agreed with our findings and are working with TFI to remedy the questioned costs.
OMB Circular A-133, Audits of States, Local Governments, and Non-Profit Organizations, establishes audit requirements for state and local governments, colleges and universities, and nonprofit organizations receiving federal financial assistance. Entities that expend more than $500,000 in federal financial assistance must have a “single audit” performed annually covering all federal funds. Single audits are conducted by state and local government auditors and by independent public accounting (IPA) firms. The OIG reviews these audit reports when issued to determine whether they meet the requirements of OMB Circular A-133 and whether they contain any audit findings related to Department grants. As a result of the OIG’s review of the single audits, during this semiannual period the OIG issued to the Department’s granting agencies 53 single audit reports encompassing 306 contracts, grants, and other agreements totaling more than $91 million. The OIG also monitors these audits through the resolution and closure process.
The single audits disclosed that costs charged to Department grants were not always adequately supported, and that required financial reports were inaccurate and frequently were not filed in a timely manner. The state and local government auditors and IPA firms who conducted the single audits also found examples of inadequate controls over the procurement process and the equipment and assets purchased with Department grant funds. They also reported that grantees often did not adequately monitor their grant sub-recipients to ensure that the sub-grantees were properly accounting for the grant funds and ensuring compliance with the terms and conditions of the grant.
Ongoing Work
Coordination of FBI and ATF Explosives Investigations
The OIG is reviewing the coordination between the FBI and ATF on explosives investigations, including which component should serve as lead investigative agency at the scene of explosives incidents. In addition, the OIG is examining the component’s coordination of training programs, laboratory operations, and explosives databases.
The Department’s Preparations for Responding to a Weapons of Mass Destruction Attack
The OIG is reviewing the Department’s preparations to respond to a WMD attack. This review examines the Department’s overall disaster planning program, particularly the planning for a response to a WMD attack.
Combating Gangs and Gang Violence
The OIG is reviewing the intelligence and coordination activities of the National Gang Intelligence Center and the National Gang Targeting, Enforcement, and Coordination Center, focusing on the role of these two organizations in the Department’s anti-gang initiatives.
The Department’s Efforts Related to Identity Theft
This audit is evaluating the Department’s strategy to combat identity theft.
Protection of the Federal Judiciary and Federal Prosecutors
The OIG is examining the USMS’s protection of federal judges and prosecutors, including how the USMS district offices and EOUSA contribute to these efforts.