While many of the OIG’s audits, reviews, and investigations are specific to a particular component of the Department, other work spans more than one component and, in some instances, extends to Department contractors and grant recipients. The following audits, reviews, and investigations involve more than one Department component.
Reports Issued
Use and Conduct of Polygraph Examinations in the Department
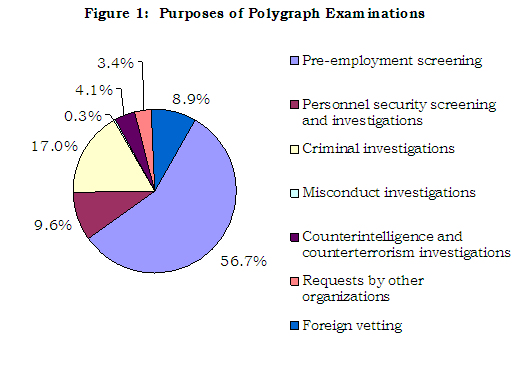
The OIG’s Evaluation and Inspections Division examined the conduct and use of polygraph examinations in 11 Department components and the oversight mechanisms used to ensure that polygraphs are employed in accordance with established professional and technical standards. The review was an informational report that described the policies governing polygraph examinations in the Department and the situations under which Department employees are required to take the examinations.
As described in the report, some Department components have used polygraph examinations as a tool in criminal investigations and in some administrative misconduct investigations involving Department employees for over 70 years. In recent years, the use of polygraph examinations by the Department has expanded to include, among other usages, pre-employment screening, personnel security screening, and foreign counterintelligence and counterterrorism investigations. During FY 2002 through 2005, the FBI, DEA, ATF, and OIG conducted more than 49,000 polygraph examinations.
| Source: Component data |
However, our review found no Department-wide policy concerning the conduct and use of polygraph examinations. Rather, each Department component has developed its own policies, procedures, and practices to govern polygraph examinations.
Within the Department the FBI is the only component with policies and procedures for compelling its employees to undergo polygraph examinations in personnel security and misconduct investigations. In addition, no other Department component has issued policies defining the circumstances under which employees can be compelled to submit to polygraph examinations in administrative misconduct investigations.
The Department has periodically considered proposals to develop a Department-wide polygraph policy, but none has been acted upon to date. For example, in response to an OIG misconduct investigation in 2004, the Justice Management Division (JMD) stated that it believed, in the absence of a Department polygraph policy, that the Department could not compel Department employees to take a polygraph in a misconduct investigation. JMD proposed developing a Department polygraph policy, but the Department did not act on this proposal.
As part of this review, in June 2006 the OIG met with JMD officials to discuss whether the Department’s position on compelled polygraphs had changed. JMD officials stated that it would reexamine whether the Department has the legal authority to compel employees to submit to polygraph examinations during investigations of administrative misconduct and, if so, what procedural steps would be required to exercise that authority.
The OIG report also provides information on several issues related to polygraph examinations, including the status of Executive Branch polygraph policy, the Office of Personnel Management’s authorities for approving the use of polygraph examinations for competitive service employees, recent initiatives to establish standard federal polygraph policies and procedures, federal requirements for examiner training and certification, federal requirements for quality control and assurance reviews, the consequences of refusing or failing a polygraph examination, and the circumstances under which an employee can be compelled to submit to polygraph testing.
Civil Rights and Civil Liberties Complaints
Section 1001 of the Patriot Act directs the OIG to receive and review complaints of civil rights and civil liberties abuses by Department employees, to publicize how people can contact the OIG to file a complaint, and to submit a semiannual report to Congress discussing our implementation of these responsibilities. In August 2006, the OIG issued its ninth report summarizing its Section 1001 activities from January 1, 2006, to June 30, 2006.
The report described the number of complaints we received under this section, the cases that were opened for investigation, and the status of these cases. We also reported the findings from our investigation into allegations from an Egyptian national concerning alleged improper treatment during his arrest by the FBI on September 12, 2001, and his incarceration in a federal prison. This investigation revealed that several correctional officials violated BOP procedures in processing the male detainee into the facility by conducting a body cavity search that did not comply with BOP policy. We further found that the correctional officers later tried to conceal their role in this incident.
We also reported on the progress of our ongoing review of the FBI’s use of two authorities amended by the Patriot Act: National Security Letters and requests for certain business records pursuant to Section 215 of the Patriot Act.
The Department’s Information Security Program Pursuant to FISMA
The Federal Information Security Management Act (FISMA) requires the OIG for each agency to perform an annual independent evaluation of the agency’s information security programs and practices by testing a representative subset of agency systems. The Office of Management and Budget (OMB) has issued guidance to agencies on how to implement policies and practices relating to information security that are compliant with FISMA requirements.
For FY 2006, the OIG reviewed the security programs of four Department components: the FBI, ATF, DEA, and JMD. Within these components, we selected for review three classified systems — JMD’s Cyber Security Assessment and Management (CSAM) Trusted Agent-Secret, the FBI’s System Security Information database, and the DEA’s Merlin system — and two sensitive but unclassified systems — JMD’s CSAM Trusted Agent and ATF’s Headquarters Network Infrastructure. The OIG plans to issue separate reports in FY 2007 evaluating each of these systems.
On September 28, 2006, we submitted a response to the OMB questionnaire providing updated information on the overall effectiveness of the Department’s IT security program. Our review disclosed that the Department had ensured that systems within the FBI, ATF, DEA, and JMD were all certified and accredited, system security controls were tested and evaluated within the past year, and system contingency plans were tested in accordance with FISMA policy and guidance. However, we found that electronic authentication risk assessments were not performed by the FBI, ATF, or DEA. We also found that the Department’s plan of action and milestones process for tracking system vulnerabilities and corrective actions were not fully implemented in accordance with Department policy within the FBI and ATF. Moreover, Department-wide system configuration policy was not always implemented as required within the DEA and JMD. With respect to IT security awareness training, we found that ATF did not fully ensure that all of its employees were trained as required by Department policy.
The OIG also evaluated the Department’s compliance with OMB’s guidelines for securing sensitive data to assess whether information security and privacy controls are being developed and implemented. The Department has established a task force to develop a comprehensive solution for safeguarding wireless access to personally identifiable information on the Department’s internal systems and to assess technical solutions to manage remote access to personally identifiable information. Although the Department is in the process of implementing additional security controls to protect personally identifiable information, we found that the Department is not fully compliant with federal policy for all automated systems currently listed within the Department’s IT inventory database. For example, the Department failed to ensure that personally identifiable information is transported and stored offsite only in encrypted form. We also found that the Department is not requiring users who access the system remotely to provide two independent ways of authenticating identity, as required by the National Institute of Standards and Technology Special Publications 800-53 and 800-53 A. As a result of our review, we provided six recommendations to ensure the Department’s compliance with federal policy for securing personally identifiable information.
Purchase Card Expenditures Related to Hurricane Katrina Recovery Efforts
In the aftermath of Hurricane Katrina, purchases using government purchase cards gained attention for weak internal controls that could result in improper and wasteful purchases, as well as missing and stolen assets. In September 2006, the OIG’s Audit Division issued a report examining the $5.2 million in hurricane-related purchase card expenditures that the Department reported for August to December 31, 2005. The report described whether Department components: 1) employed effective internal controls over hurricane relief purchase card transactions to ensure that problems were minimized, 2) authorized and validated hurricane-related purchase card transactions, and 3) received the hurricane-related goods and services that were purchased.
We found that nearly all of the hurricane-related purchase card transactions tested were authorized and valid, and the goods and services were received. However, the report identified internal control issues that should be corrected to ensure that future government funds are not at risk. The report found that for the FBI and ATF, the number of overall cardholders per administrative officer (also known as span of control) could significantly impact the oversight of a purchase card’s use. In a previous OIG review, we recommended a span of control of no more than 7 cardholders per administrative officer, or a total of 300 transactions per month. Six of the eight components maintained an average span of control of four cardholders to one administrative officer. However, ATF had on average 65 cardholders per administrative officer, with 23 administrative officers responsible for over 100 cardholders. The FBI had on average 23 cardholders per administrative officer, with 5 administrative officers responsible for 50 or more cardholders. In addition, we found that the FBI and ATF had administrative officers who were cardholders in the same group, which could allow the administrative officers to approve their own transactions. Further, we determined that approving officials and cardholders need refresher training that emphasizes prohibited purchases, requirements to document the availability of funds, and the importance of retaining adequate documentation.
The OIG made three recommendations: 1) ensure that a maximum span of control of 7 cardholders to 1 administrative officer, or a total of 300 transactions per month, is maintained; 2) reinforce policies on what items are not allowed to be purchased with purchase cards, the requirement to document the availability of funds, and the importance of retaining required supporting documentation; and 3) institute required purchase card refresher training at the FBI, ATF, USMS, and OJP. The Department generally concurred with the recommendations.
Accountability Organizations’ Access to Information
The OIG’s Evaluation and Inspections Division reported on issues that federal Offices of Inspector General and state and city audit organizations encountered in obtaining timely access to information — including documents and testimony — required to conduct evaluations, audits, and investigations. We also identified the most successful strategies used by accountability organizations for overcoming access problems. The review was initiated at the request of the Domestic Working Group, a group of federal, state, and local inspectors general and audit agencies organized under the auspices of the Government Accountability Office.
Our report, which summarized survey results from 128 accountability organizations, found that most survey respondents did not experience significant access problems in terms of denial of information. However, many organizations reported that they experienced delays in the receipt of information, which also can significantly hamper the effectiveness of their oversight work.
To overcome any access issues, survey respondents said they used a variety of strategies, including addressing issues early in the process, encouraging agency managers to support access to information, communicating frequently with agencies under review, and ensuring the protection of sensitive information.
Investigations
The following are examples of cases that the OIG’s Investigations Division investigated during this reporting period:
A joint investigation by the OIG’s Fraud Detection Office and the New York Field Office led to the arrest of a painter at the World Trade Center on charges that he received more than $1 million from the September 11 Victim Compensation Fund based on his fraudulent claim that he was permanently disabled and unable to work as a result of back injuries sustained during the September 11 terrorism attacks. Videotape evidence gathered by the OIG demonstrated that the painter continued to engage in physical activities, such as bicycling and dancing, which were inconsistent with the injuries he claimed. In addition, the OIG found that the painter continued to paint houses in his neighborhood and fraudulently concealed from the hearing officer a back injury that he sustained in a motor vehicle accident that occurred prior to September 11, 2001. Judicial proceedings continue.
An investigation by the OIG’s Fraud Detection Office resulted in the County of York, Pennsylvania, agreeing to pay the United States $16 million to settle allegations under the False Claims Act that it knowingly submitted inflated claims to the former INS for housing INS detainees. The settlement arose from an intergovernmental services agreement between York and INS to house INS detainees in York County Prison. The parties entered into the agreement in 1995, and INS agreed to pay York $50 a day per detainee. In 2000, INS agreed to increase the rate to $60 a day based on York’s certified statement of prison operating costs and its representation of the inmate population of the prison. In this statement, however, York inaccurately represented to INS that the average daily population of the prison was 996 inmates for the applicable period, rather than 1,544 as the county reported separately to the state. Understating the population allowed York to claim higher costs per inmate and thus increased the rate at which INS reimbursed York for housing federal detainees. This representation resulted in an inflated rate charged to the United States for detainees housed from October 1999 through March 2003. The OIG investigation, which arose from a referral by the OIG’s Philadelphia Audit Office, was initiated prior to INS’ transfer to the DHS.
Ongoing Work
Cost Tracking and Planning for Department IT Initiatives
In accordance with the requirements of the Department’s FY 2006 Appropriations Conference Report, the OIG was directed to provide an inventory of major Department IT systems and report on research, plans, studies, and evaluations that the Department has produced, or is in the process of producing, concerning its information systems. In response, the OIG issued the first of three reports in March 2006: A report of the Department’s major IT system investments by investment title/component, investment description, implementation status, and actual and projected costs. The second report will provide an audited verification of the information detailed in the unaudited report. The third report will detail the Department’s research, plans, studies, and evaluations along with an analysis identifying the depth and scope of the problems the Department has experienced in the formulation of its IT plans.
The Integrated Wireless Network (IWN) is intended to link approximately 80,000 federal, state, and local law enforcement officers and public safety agencies in a secure, interoperable wireless service that provides communications in support of law enforcement, first responder, and homeland security requirements. IWN currently is a joint project of the Department, DHS, and the Department of the Treasury. The OIG is assessing the implementation of the IWN project, including its cost and deployment status.
The Department’s Financial Statement Audits
The Chief Financial Officers Act of 1990 and the Government Management Reform Act of 1994 require annual financial statement audits of the Department. The OIG’s Audit Division oversees and issues financial statement audit reports based on the work performed by independent public accountants. The FY 2006 financial statement audit currently is in process. The results will be included in the Department’s FY 2006 Performance and Accountability Report, which is expected to be issued by November 15, 2006.
The Department’s Internal Controls Over Terrorism Reporting
The Department measures its counterterrorism efforts in part by reporting terrorism-related statistics in its performance plans, budget requests, and statistical reports. An OIG audit is examining whether the Department and its components have adequate internal controls to ensure accurate reporting of terrorism-related statistics.
Violent Crime Task Force Coordination
At the direction of the House and Senate Appropriations Committees, the OIG is examining whether investigations conducted by four of the Department’s violent crime task forces are well coordinated. Among other issues, the review will examine information-sharing efforts among the FBI’s Safe Streets Task Forces, ATF’s Violent Crime Impact Teams, DEA’s Mobile Enforcement Teams, and USMS’s Regional Fugitive Task Forces.
Information Security
The OIG has initiated a review to document the processes and requirements that Department components follow when investigating and reporting losses of sensitive information, including laptops containing sensitive or classified information.
Oversight of Intergovernmental Service Agreements
The OIG is conducting an audit of the USMS’s and the Office of the Federal Detention Trustee’s oversight of Intergovernmental Service Agreements (IGA), which are agreements with state and local prisons to house federal detainees awaiting trial or sentencing. Our objective is to determine if the USMS and the Office of the Federal Detention Trustee employ an effective monitoring and oversight process in light of the more than $755 million spent on IGAs in FY 2005.
Grant Closeout Process Utilized within the Department
The OIG is reviewing the grant closeout processes used by OJP, Office of Community Oriented Policing Services (COPS), and Office on Violence Against Women. In conducting the audit, the OIG will determine whether the grant closeout processes are adequate to ensure that expired grants are closed in a timely manner; grant funds are drawn down in accordance with federal regulations, Department policy, and the terms and conditions of the grant; and remaining grant funds are deobligated prior to closeout.