The background section provides information about the roles and responsibilities of the staff within the Department’s Office of the Chief Information Officer and the development of the Department’s computer security incident reporting procedures by that office. We also describe the Department’s reporting requirements for classified computer security incidents.
The Chief Information Officer
Within the Department of Justice (Department), the management and protection of sensitive information, including personally identifiable information (PII), falls under the responsibility of the Office of the Chief Information Officer (CIO). The CIO, who is also the Deputy Assistant Attorney General for Information Resource Management, is responsible for overseeing the management, acquisition, and integration of the Department’s information resources, including:
- Formulating Department-wide information technology (IT) policies and strategic plans;
- Ensuring that investments in IT processes are aligned with the Department’s overall strategic goals, budget, and enterprise architecture;
- Making recommendations concerning the IT budget requests of the Department’s components; and
- Overseeing the security of the Department’s information systems.15
The creation of the role of CIOs in the government is attributed to the Clinger-Cohen Act of 1996, previously called the Information Technology Management Reform Act of 1996.16 This Act mandates a CIO in each federal agency.
Since the appointment of the current CIO in 2002, the following IT security policies have been issued:
July 2002 |
DOJ IT Strategic Plan |
November 2003 |
DOJ Order 2640.2E, Information Technology Security |
May 2004 |
DOJ Computer System User Rules of Behavior |
May 2005 |
DOJ Security Program Operating Manual |
September 2005 |
DOJ Order 2880.1B, Information Resources Management Program |
November 2005 |
DOJ Order 2740.1, Use and Monitoring of DOJ Computers and Computer Systems |
June 2006 |
DOJ IT Strategic Plan, Fiscal Years 2006-2011 |
August 2006 |
Information Technology Security Program Management Plan |
November 2006 |
DOJ Incident Response Plan Template, (originally created in December 2003, updated annually) |
December 200617 |
IT Security Standards (17 policies) |
December 2006 |
DOJ Configuration Management Plan |
In these documents, the Department has established extensive security policies and incident response procedures for the Department’s IT systems. Additionally, several memorandums have been issued by the CIO providing further requirements on reporting computer security incidents, particularly those involving loss of PII.
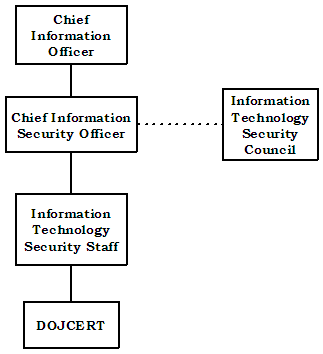
The Office of the CIO falls organizationally within the Department’s Justice Management Division (JMD).18 The CIO has supervisory responsibility for five offices. One of these five offices is the Information Technology Security Staff, whose mission is to ensure the protection of the Department’s information systems that collect, process, transmit, store, or disseminate either classified or Sensitive But Unclassified information, including PII.19 The Information Technology Security Staff is headed by the Chief Information Security Officer. See Chart 1 for the Office of the CIO organization chart.
Chart 1: Organizational Chart for the Office of
the Chief Information Officer
The Chief Information Security Officer
In June 2003, the CIO appointed a Chief Information Security Officer to help support the Department’s IT security mission and goals, and to develop and maintain a Department-wide information security program. This program includes issuing procedures for detecting, reporting, and responding to security incidents, and conducting periodic risk assessments that seek to identify the magnitude of harm that could result from unauthorized access, use, disclosure, disruption, modification, or destruction of the information and information systems that support the operations and assets of the Department.20
The Chief Information Security Officer also is responsible for ensuring the Department’s compliance with various federal laws, standards, and directives regarding electronic information security, such as the E-Government Act of 2002, the Federal Information Security Management Act (FISMA) of 2002, the Privacy Act of 1974, National Institute of Standards and Technology (NIST) standards, and Office of Management and Budget (OMB) and DOJ directives. (See Appendix X for a summary description of each of these laws, standards, and directives.)
The CIO’s Information Technology Security Council
The CIO created an Information Technology Security Council (the Council), chaired by the Chief Information Security Officer, in August 2003 to address the security goals outlined in the Department’s IT Security Program Management Plan, which is the guiding document for managing the Department’s overall IT security program. The plan establishes goals and performance measures; identifies initiatives, resources, schedules, and controls; provides templates, guidelines, and tools for IT staff to ensure systems meet federal and Department certifications and accreditations; and describes IT security management strategies, roles and responsibilities, program implementation, and the goals and action plans for the security program.
The Council is composed of IT security staff from each of the Department’s components. The Council created four project management teams devoted to different areas of IT security.21 These teams develop templates and implementation guidance documents, and test cases for developing, implementing, and testing the security controls in the specific areas of security that are covered by each team.
Cyber Defense Operations Team. The Department’s response to a computer security incident is handled by the Cyber Defense Operations Team, which is chaired by the Department of Justice Computer Emergency Readiness Team’s (DOJCERT) Project Manager and also includes representation from all of the Department components. The team meets monthly to discuss changes in incident reporting standards and procedures. Any comments are incorporated into the Incident Response Plan template, which is updated at the beginning of each fiscal year. For example, in the November 2006 Incident Response Plan template, DOJCERT included for the first time reporting requirements for incidents of PII and data loss, and defined the information that components need to gather when a data loss occurs or when data has been potentially compromised.
DOJCERT
DOJCERT was established in 2000 within the Information Technology Security Staff to fulfill the Department’s obligations under the Government Information Security Reform Act, which directed federal agencies to “establish procedures for detecting, reporting, and responding to security incidents.”22 In November 2003, the Department updated its Information Technology Security order to require all components to respond to and report all computer security incidents to DOJCERT in accordance with rules set forth by DOJCERT.23 These requirements for incident response and reporting are also part of the Department’s efforts to attain the goals in Homeland Security Presidential Directive 7, which established a national policy for federal departments and agencies to identify and prioritize United States critical infrastructure and key resources and to protect them from terrorist attacks.24
DOJCERT is a centralized incident response team that provides Department-wide support for computer security incidents and can be contacted 24 hours a day, 7 days a week.25 The CIO has assigned DOJCERT the responsibility to provide leadership and guidance to all Department components in incident response planning and plan evaluation. DOJCERT’s stated objective is to work in coordination with all Department component incident response teams to provide a central point of information collection, information dissemination, and response planning.
DOJCERT Incident Response Plan. DOJCERT is the organization to which all Department components are required to report computer security incidents, including data loss incidents. DOJCERT developed an Incident Response Plan template in December 2003 that established a Department-wide standardized approach for handling and reporting computer security incidents and that provided detailed incident response procedures within each component. DOJCERT periodically updates the template to reflect new statutory or OMB requirements or emerging computer security threats.
As explained earlier, DOJCERT revised its Incident Response Plan template in November 2006 to require for the first time that the components add language that identifies the loss of PII as a distinct type of reportable incident, and that defines the category and timeframe (1 hour) that should be used to report these data loss incidents.
The Incident Response Plan identifies seven categories of computer security incidents, such as Unauthorized Access and Improper Usage, that all Department components are required to report to DOJCERT, and includes reporting timeframes for each category.26 The DOJCERT Incident Response Plan also provides:
- Requirements for incident response handling,
- Agency objectives for incident response handling,
- Organizational structure for incident response handling,
- Roles and responsibilities for key elements and personnel,
- Preparation and training guidelines,
- Policy and procedures for handling incidents, and
- Incident reporting procedures for all Sensitive But Unclassified and classified incidents.
Each Department component is required to develop its own Incident Response Plan that is aligned with the requirements and goals of the DOJCERT Incident Response Plan. In addition, each component must conduct an exercise of that plan at least annually.27 DOJCERT reviews each component’s plan annually for compliance with the DOJCERT Incident Response Plan template.
DOJCERT has also instituted regular monthly reporting requirements (in addition to the required reporting of security incidents as they occur) to collect additional details on incidents in two of the reporting categories and to promote component familiarity with the DOJCERT process and staff.28 The DOJCERT template is a technical document for component IT staff and is not distributed to all employees.
DOJCERT’s Archer Database. To manage and track the reporting process, DOJCERT maintains an Incident Response and Vulnerability Patch Database (commonly called the Archer Database, after the vendor that developed it) where incidents are recorded and monitored. Using the Archer Database, reports can be generated on all Sensitive But Unclassified incidents. All the components we reviewed have online access to this database.29 Each component can choose whether to complete the online Incident Report Form, e-mail or fax the completed form to DOJCERT, or telephone DOJCERT with the specifics of the incident. Department components with access to the Archer Database are able to use it for their own internal tracking purposes as well.
DOJCERT’s Educational and Technical Support. DOJCERT also provides information resources, technical support, coordination activities, and educational support to the Department on incident response. Furthermore, DOJCERT tracks the implementation of critical patches on IT systems and applications. As part of its educational support responsibilities, DOJCERT provides annual training to all component IT security staff to meet the FISMA requirements for Incident Response and IT Contingency Plan training and testing.30 Since 2002 DOJCERT has developed and distributed online, to component CIOs and their staff, a quarterly newsletter that provides the Department with security awareness information, security tips, training information, and updates to DOJCERT operations.
DOJCERT Reporting Responsibilities. DOJCERT reports all of the Department’s computer security incidents, except spam, to the Department of Homeland Security’s United States Computer Emergency Readiness Team (US-CERT). US-CERT is a partnership between the Department of Homeland Security and the public and private sectors that was established in 2003 to protect the nation’s Internet infrastructure. US-CERT also coordinates defenses against and responses to cyber attacks across the nation.31 It is responsible for analyzing and reducing cyber threats and vulnerabilities, disseminating cyber threat warning information, and coordinating incident response activities.
Additionally, DOJCERT is responsible for reporting all actual or potential data loss incidents to appropriate components in the Department. If the incident involves PII, it is reported to the Department’s Office of Privacy and Civil Liberties in the Office of the Deputy Attorney General. If there is evidence that a crime has occurred – for example, computer crimes, child pornography, e-mail threats, successful malicious activity directed towards the Department, or financial fraud – then these incidents are reported to the Federal Bureau of Investigation (FBI), the U.S. Secret Service, the Criminal Division, the Office of the Inspector General (OIG), or other appropriate agencies. Additionally, DOJCERT reports any information that could be relevant to terrorism investigations to the FBI and the U.S. Secret Service.
Reporting Classified Incidents
Classified incident reporting in the Department is governed by the Department’s Security Program Operating Manual (SPOM).32 Classified computer security incidents are to be reported by the components’ Security Programs Manager to the Department Security Officer, who is the Director of the Security and Emergency Planning Staff (SEPS).33 SEPS maintains a separate database to track these reports. The SPOM defines nine categories of classified security incidents that are to be reported, including:
Any incident involving a possible loss, compromise, or suspected compromise of classified information, foreign or domestic, and... Any event involving [IT] systems, equipment or media which may result in disclosure of classified information to unauthorized individuals, or that results in unauthorized modification or destruction of system data, loss of computer system processing capability, or loss or theft of computer system media.34
The SPOM also requires components to report all IT-related classified incidents to DOJCERT in addition to notifying the Department Security Officer. DOJCERT notifies SEPS of all data loss incidents, including classified data losses, via e-mail. DOJCERT, in its Incident Response Plan template, requests that components, if possible, sanitize and declassify the incident report and then report it through normal channels to DOJCERT.
Attorney General Order 2572-2002 designates the CIO to carry out the duties assigned under 40 U.S.C. § 1425. DOJ Order 2880.1B, Information Resources Management Program, September 27, 2005, further establishes the authority of the Office of the CIO in the Department and outlines the office’s duties and responsibilities.
Designation of Chief Information Officers, 44 U.S.C. § 3506, February 10, 1996.
The Federal Information Security Management Act (FISMA) of 2002 mandates that all IT systems in the government must undergo certification and accreditation once every 3 years. The National Institute for Standards and Technology (NIST) issued government-wide technical guidance for the certification and accreditation process in Special Publication 800-53, Recommended Security Controls for Federal Information Systems (February 2005). The publication identifies 17 categories of information security, called “control families,” and sets minimum security standards within each control family. The Office of the CIO has written 17 separate policies describing how the Department will meet the standards in each control family.
JMD is the management arm of the Department and is led by the Assistant Attorney General for Administration. The four offices in JMD are the Controller; Human Resources; Information Resource Management; and Policy, Management, and Planning.
The other four offices under the CIO are E-Government Services, Policy and Planning, Operations Services, and Enterprise Solutions.
Information Technology Security Program Management Plan, Version 5.41, August 2006.
The four project management teams are the IT Security Employee Services Team, the Computing Environment and Enclave Defense Team, the Cyber Defense Operations Team, and the Certification and Accreditation Management Team.
Pub. L. No. 106-398, the Government Information Security Reform Act, October 30, 2000. This Act expired in November 2002 and was superseded by FISMA in December 2002.
DOJ Order 2640.2E, Information Technology Security, November 28, 2003.
Homeland Security Presidential Directive 7, Critical Infrastructure Identification, Prioritization, and Protection, December 17, 2003.
See Appendix XII for a description of the seven categories and the associated timeframes. An additional category is used for training exercises only.
The IT Security Standard Incident Response Control Family, November 2006, written by DOJCERT, describes the Department’s overall policy for incident response. The policy requires that each component develop and implement a formal written incident response policy, provide annual training to incident response personnel, test its incident response plan at least annually, develop a capability for responding to and recovering from incidents that have occurred, track and document incidents, report incidents promptly, and provide assistance to users who need to report security incidents.
The two categories are Spam and Scans/Probes/Attempted Access. Scans, probes, and attempted access include “any activity that seeks to access or identify a Department computer, open ports, protocols, service, or any combination for later exploit. This activity does not directly result in a compromise or denial of service.” See Appendix XII.
The United States Marshals Service (USMS) informed us that only one person had been trained to use the Archer Database and that this individual had been on extended sick leave. Due to work schedules and recent staff vacancies in the security office, the USMS has been unable to train any other staff to access the Archer Database. Therefore, the USMS reports new incidents to DOJCERT via telephone instead of through the Archer Database.
FISMA established the responsibilities of agencies to assess their security risks.
Department of Homeland Security website, www.us-cert.gov/aboutus.html, February 28, 2007.
The Department Security Officer reports to the Deputy Assistant Attorney General for Human Resources, who reports to the Assistant Attorney General for Administration. The Assistant Attorney General for Administration is the head of the Justice Management Division.