Introduction
Between December 2005 and November 2006, the USMS reported 15 security incidents to DOJCERT, none of which involved the loss of PII or involved classified information. The USMS stated that reportable losses include the loss of electronic devices such as desktop computers, laptops, or BlackBerry devices that possibly contain classified or investigative case-sensitive information or printed documents that include PII. However, the USMS stated it did not begin tracking or reporting sensitive data loss incidents, including PII, to DOJCERT until the August 2006 Department memorandum that instructed all components to report these incidents to DOJCERT.144
The USMS defines sensitive information as synonymous with Law Enforcement Sensitive. In the USMS Security Programs Manager policy, Law Enforcement Sensitive information is defined as unclassified information of a sensitive and proprietary nature that if disclosed could cause harm to law enforcement activities by jeopardizing investigations, compromising operations, or causing life-threatening situations for confidential informants, witnesses, or law enforcement personnel.145 These categories are designated as law enforcement sensitive:
- Informant and witness information;
- Grand Jury information subject to the Federal Rules of Criminal Procedure, Rule 6(e), Grand Jury Secrecy Proceedings and Disclosure;
- Investigative material;
- Law enforcement sources and undercover operations;
- Law enforcement intelligence sources and methods;
- Federal law enforcement agency activities;
- Federal support to state and local law enforcement activities;
- Information pertaining to the judiciary, to include investigations of inappropriate communications; and
- Personnel information pertaining to employees of the USMS.
While the USMS does not currently have a definition for PII, it considers those records requiring protection under the Privacy Act to be a subset of Limited Official Use information. The USMS defines Limited Official Use information as unclassified information of a sensitive, proprietary, or personally private nature that must be protected against release to unauthorized individuals. The following categories of information are designated as Limited Official Use information:
- Tax information subject to 26 U.S.C. § 6103, Confidentiality and Disclosure of Returns and Return Information;
- Information that could be sold for profit;
- Personal information subject to the Privacy Act;
- Memorandums or reports that disclose security vulnerabilities;
- Information that could result in physical risk to individuals;
- Company proprietary information;
- Audit staff work papers;
- Draft audit reports;
- Information offered in confidence during the conduct of internal audits, comprehensive assessments, program reviews, and evaluations;
- Program and budget information on intelligence-related activities; and
- Sensitive Antideficiency Act material.146
The USMS uses the definition of classified information contained in Executive Order 12958, as Amended, Classified National Security Information, dated March 25, 2003.
Reporting Procedures
Reporting Procedures for Non-Classified Incidents
The USMS relies on four policies when reporting computer security incidents:
- USMS Incident Response Plan, December 8, 2005;
- USMS Directive 2.34, Security Programs Manager, November 9, 2005;
- USMS Directive 12, Information Resources Management, effective October 6, 2003, updated April 3, 2006; and
- USMS Directive 7.1, Management of Personal Property, October 6, 2003.
It should be noted that the four policies provide conflicting chain-of-command reporting procedures. For example, the policies instruct employees to report computer security incidents to staff titles and internal departments that either no longer exist or are incorrect. Therefore, the reporting procedures described here are the actual practices as described in interviews with USMS officials, supplemented by the policies.
USMS employees are to immediately report suspected computer security incidents involving sensitive information loss including PII to the Office of Information Technology’s Help Desk at USMS Headquarters and the employee’s supervisor. If the incident involves lost or stolen property, the employee is also required to notify the office property custodian (as required by USMS Property Management regulations for reporting lost or stolen property) and the Office of Investigations (as appropriate for stolen property).147 The Help Desk should then notify the appropriate Systems Administrator in the Office of Information Technology as soon as possible to help evaluate the incident.148 The Help Desk, after recording general information about the incident, should then notify the Computer Security Program Manager, also at Headquarters, who interviews the employee involved about the circumstances surrounding the event. With the information gathered during the interview, the Computer Security Program Manager is required to report the incident to DOJCERT via a telephone call. The USMS does not currently use their electronic access to DOJCERT’s Archer Database for reporting incidents online. Chart 20 shows the USMS’s procedures for reporting sensitive information loss, including PII.
Chart 20: Flowchart of the USMS’s Procedures for Reporting Sensitive Information Loss, Including PII
[Image Not Available Electronically]
Reporting Procedures for Data Loss that Include PII
As of April 2007, the USMS had not yet updated its Incident Response Plan to reflect requirements for investigating and reporting data loss incidents that include the loss of PII. DOJCERT added the data loss and PII requirements to its Incident Response Plan template in November 2006 with the requirement that all components incorporate this update by December 29, 2006. The USMS stated that it planned to update its Incident Response Plan and include this revision by mid-March 2007. The USMS did e-mail its staff on August 29, 2006, informing them of their responsibility to report all known incidents of sensitive data loss and PII “within 1 hour of discovery or detection.”149 The USMS does not have procedures for reporting computer security incidents after hours.
Reporting Procedures for Classified Information
If classified information is involved in a computer security incident, employees must promptly report by telephone and confirm in writing the circumstances of the incident to the USMS Document Security Program Manager, who is responsible for the receipt, handling, safeguarding, and storage of all classified material within the USMS.150 The Document Security Program Manager is responsible for notifying the USMS Security Programs Manager. The USMS Security Programs Manager is required to then notify the Department’s Security Officer, Security and Emergency Planning Staff (SEPS). Chart 21 shows the USMS’s procedures for reporting classified information loss.
Chart 21: Flowchart of the USMS’s Procedures for Reporting Classified Information Loss
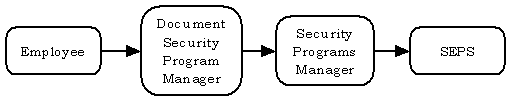
Additional Reporting Requirements
According to the USMS policy on Management of Personal Property, employees are required to notify the property custodian through their supervisor if an incident involves lost or missing electronic equipment, including a laptop or desktop computer or a BlackBerry device.151 The property custodian should complete a form/affidavit with descriptive information about the event and forwards that form to the Office of Property Management. The Office of Property Management is required to refer reports of loss to the Board of Survey if the loss is likely to have been the result of willful intent, gross negligence, neglect, misuse, theft, or misconduct. If the loss involves sensitive property such as desktop and laptop computers or BlackBerry devices that possibly contain classified or investigative case-sensitive information, a copy of the report should be provided to the Office of Internal Affairs (also known as Internal Investigations).152 The property custodian should also report lost sensitive property to the NCIC. In the event of stolen property, the employee should notify the local police department.
Indications of Compliance with Reporting Procedures
USMS officials told us that they believed their employees were following the correct reporting procedures. While we did not validate this statement, our analysis of the Archer Database showed that the USMS was not always reporting computer security incidents within the required timeframes specified in both the DOJCERT and USMS Incident Response Plans. Between December 2005 and November 2006, the USMS reported 62 percent of its computer security incidents to DOJCERT within the required timeframes. We did not analyze any USMS PII incidents for timeliness because the USMS did not report any incidents involving PII. Table 15 shows the USMS’s reporting in each category.153
Table 15: The USMS’s Timeliness in Reporting Incidents to DOJCERT |
|||||
| Category | Reporting timeframe* | Incidents reported | Reported within timeframe | Reported after timeframe | Could not compute timeliness** |
|---|---|---|---|---|---|
Category 0 (Exercise/Test) |
None |
0 |
N/A |
N/A |
N/A |
Category 1 |
1 hour |
2 |
0 |
2 |
0 |
Category 2 |
2 hours |
0 |
N/A |
N/A |
N/A |
Category 3 |
1 day |
4 |
1 |
2 |
1 |
Category 4 |
1 week |
2 |
2 |
0 |
0 |
Category 5 (Scans/Probes) |
1 month |
0 |
N/A |
N/A |
N/A |
Category 6 (Investigation) |
None |
0 |
N/A |
N/A |
N/A |
Category 7 |
1 month |
7 |
5 |
1 |
1 |
Total |
15 |
8 |
5 |
2 |
|
PII incidents occurring on or after 7/12/06*** |
1 hour |
0 |
N/A |
N/A |
N/A |
* For purposes of this table, reporting timeframes for Categories 0-7 refer to the timeframes defined in the Incident Response Plan. Reporting timeframe for PII incidents refers to the timeframe defined in OMB Memorandum M-06-19. ** Some records did not include information to indicate when DOJCERT received the reports. Category 0 and 6 incidents, for which there are no reporting timeframes, are also included in this category. *** PII incidents were reported in varying incident categories. Source: Archer Database |
Ensuring All Incidents Are Reported
The USMS stated that it relies primarily on the Department’s required annual Computer Security Awareness Training to educate and remind staff of their reporting responsibilities as well as what is considered a reportable incident. However, we were informed during an interview that employees did not have access to this training in 2006 due to technical difficulties the USMS had in supporting the Computer Security Awareness Training online. The USMS also said that it relies on several written policies and memorandums to inform staff of their responsibilities to report lost or stolen government-issued equipment that may contain sensitive information.
In August 2006, the USMS e-mailed a memorandum to all USMS employees informing them of their responsibility to report all incidents involving known loss of sensitive data and PII within 1 hour of discovery or detection.154 Additionally, the memorandum stated that the loss of any data storage devices, such as laptops, flash drives, disks, and tapes, should be reported within the same 1-hour timeframe.
As stated above, the USMS policy on Management of Personal Property requires employees to make the loss of property known immediately through his or her supervisor to the property custodian. Property custodians are required to maintain accountability for all property on the accountable property record through physical inventories and the maintenance of current property records. A comprehensive physical inventory of all accountable property is required every 2 years.
USMS Rules of Behavior, which all employees must read and sign, require employees to report all actual or suspected security violations, vulnerabilities, and incidents to the first-line supervisor and other appropriate staff.155
Notification to Affected Parties
The USMS has not developed policies concerning notification to affected parties in the event of a loss of PII.
Determining the Type of Data Lost
To determine the type of data lost or compromised, the USMS primarily relies on the Chief of Enterprise Management at Headquarters interviewing the employee involved. The Chief said that she questions the employee using an internal form containing 23 questions. Several of the questions ask about applications accessed from the lost laptop or BlackBerry device, whether information was saved to the hard drive, and the type of information the lost device contained. The Chief said that she intends to eventually train the Help Desk to conduct these initial interviews and complete the interview forms. However, the Chief or a member of her staff will remain the point of contact for notifying DOJCERT.
DOJ Memorandum, Reporting Incidents Involving Data Loss and Personally Identifiable Information, Vance Hitch, CIO, August 7, 2006.
USMS Directive 2.34, Security Programs Manager, November 9, 2005.
USMS Directive 2.34, Security Programs Manager, November 9, 2005, Attachment III F.2.
USMS Directive 12, Information Resources Management, Appendix H, effective October 6, 2003, updated April 3, 2006. The Office of Investigations is also known as Internal Investigations.
There are 50 Systems Administrators to support 400 locations in 94 USMS districts. While the majority of the USMS offices do not have a Systems Administrator, in the locations where one exists the employee reports a data loss first to the Systems Administrator, who then reports the incident to the Help Desk. In locations where no Systems Administrator exist, the employee calls the Help Desk at Headquarters and the employee’s supervisor.
USMS E-Mail to All Staff, Notice From OSD Re: Reporting Incidents Involving Data Loss and Personally Identifiable Information, August 29, 2006.
USMS Directive 2.34, Security Programs Manager, Attachment C, November 9, 2005, pp. 13-14.
The property custodian is the Chief Deputy U.S. Marshal within a district office or the head of office within a Headquarters component. See USMS Directive 7.1, Management of Personal Property, October 6, 2003.
USMS Memorandum to All USMS Employees, Reporting Losses of USMS Property, Director, November 5, 2002.
Our calculations are based on Categories 1 through 5 and Category 7. We did not include incidents found in Categories 0 and 6 because they had no associated time criteria, nor did we include incidents for which the Archer Database contained no information to indicate when DOJCERT received the report that an incident had occurred.
USMS e-mail to all staff, Notice From OSD Re: Reporting Incidents Involving Data Loss and Personally Identifiable Information, August 29, 2006.
USMS Directive 12, Information Resources Management, Appendix C, Rules of Behavior, effective October 6, 2003, updated April 3, 2006.