Introduction
Between December 2005 and November 2006, ATF reported 70 computer security incidents to DOJCERT, including 8 incidents involving potential PII loss and 1 incident potentially involving classified information.62 According to ATF officials we interviewed, a reportable computer security incident is the loss of any data on an electronic device such as a laptop or BlackBerry device, receipt of an e-mail with a virus, or a server failure or hard drive crash in which all information was not backed up and could not be fully restored or reconstructed. ATF policy defines a computer security incident as “any event or condition that has the potential to affect the security or accreditation of an automated information system and that may result from either intentional or unintentional actions.”63 ATF considers “security incident” synonymous with “security violation,” which is defined as “an event that may result in the disclosure of sensitive information to unauthorized individuals or that results in the unauthorized modification or destruction of system data, the loss of computer system processing capability, or the loss or theft of any computer system resources.”64
ATF policy defines sensitive information as a category of unclassified information. Sensitive information is used synonymously with Sensitive But Unclassified and defined as “any information, the loss, misuse, or unauthorized access to, or modification of which could adversely affect the national interest or the conduct of federal programs.”65
ATF has no written definition of PII but stated that in practice it defines PII as a collection of several pieces of information that can be used to identify a specific person or to construct an identity; for example, a social security number plus an address constitutes PII. What constitutes PII is a judgment call, according to ATF staff we interviewed, and they believed there should be more guidance from the Department regarding this definition. According to these officials, PII was not a term that was used prior to the May 2006 Department of Veterans Affairs’ laptop theft. 66
ATF uses the definition of classified information contained in Executive Order 12958, as Amended, Classified National Security Information, dated March 25, 2003.67 This order requires all components in the Department and other executive branch agencies to use its uniform definitions.
Reporting Procedures
ATF has three written policies that define procedures for reporting computer security incidents:
- Automated Information System Security Program (ATF H 7250.1), dated July 26, 2006;
- Computer Security Incident Response Capability Incident Response Plan, dated July 24, 2006; and
- Computer Security Incident Response Capability, (ATF Order O 7500.4A), dated April 12, 2005.
The Automated Information System Security Program establishes the requirements for managing ATF’s information systems to ensure the confidentiality, integrity, and accountability of those systems. It complements the DOJCERT and ATF Incident Response Plans by providing more detailed security roles and responsibilities for all employees and by expanding on the responsibilities and reporting instructions for specific staff in the event of a computer security incident. However, this policy also provides contradictory guidance to ATF employees. In two sections of the policy, it lists the Help Desk as the primary point of contact for all users to contact when reporting computer security incidents. In two other sections, it lists the Information Systems Security Office as the primary point of contact.
ATF’s July 2006 Incident Response Plan conforms to the DOJCERT Incident Response Plan template, and lists the roles and responsibilities for ATF employees when reporting all suspicious computer events or incidents to ATF’s Help Desk or Security Office. Section 9.3 of this plan, titled “Incident Reporting,” includes ATF-specific procedures for reporting computer security incidents for the categories of technical/non-sensitive, sensitive, and classified information. DOJCERT added the data loss and PII requirements to its Incident Response Plan template in November 2006 with the requirement that all components incorporate this update by December 29, 2006. As of April 17, 2007, ATF has updated its Incident Response Plan to reflect requirements for reporting data loss incidents that include the loss of PII, but has not yet submitted it to DOJCERT for approval. ATF stated that this update will also include after-hours reporting procedures.
The Computer Security Incident Response Capability policy also describes expanded duties, responsibilities, and guidance to all ATF employees to respond to computer security incidents.
Reporting procedures are to be initiated as soon as an employee realizes that a potential computer security incident has occurred. Reporting procedures for non-sensitive, sensitive, and classified information are described below.
Non-Sensitive Information
For non-sensitive information, all ATF employees are required to report computer security incidents to the Help Desk by telephone, facsimile, e-mail, or in person, or via secure U.S. Postal Service mail. According to ATF officials, in practice the employee, although not required by written policy, will also notify his or her supervisor.68
According to ATF officials, the Help Desk is used as the main point of contact for all incidents and is responsible for reporting all incident-related information to the Information Systems Security Office.69 The person serving as the Information Systems Security Officer also serves as the Computer Security Incident Response Capability Coordinator. The Information Systems Security Office is required to report computer security incidents to DOJCERT within the timeframes required for the priority level of the incident as established in the DOJCERT Incident Response Plan. The Information Systems Security Office is required to notify DOJCERT by logging into the Archer Database and recording the incident. The Archer Database also serves as ATF’s incident tracking system. When appropriate, the Information Systems Security Office may also notify managers such as the employee’s Division Chief and the Office of Operations Security and even the Department’s CIO.
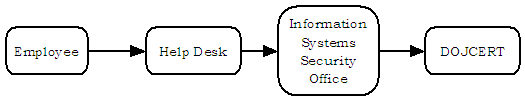
When laptops or BlackBerry devices are lost or stolen, the ATF Investigations Division, Office of Professional Responsibility, and Security Operations must be notified. Also, in the event of a theft of a laptop or BlackBerry device, the employee involved is required to contact local law enforcement and may be required to provide a copy of the police report to his or her supervisor. For such thefts, the Information Systems Security Office also is required to notify the FBI, which should enter the stolen device’s serial number into the National Crime Information Center (NCIC) system.70 The ATF Investigations Division should be notified by the Information Systems Security Office of all incidents in which employee misconduct may be involved. Chart 5 shows ATF’s reporting procedures for loss of non-sensitive information.
Chart 5: Flowchart of ATF’s Reporting Procedures for Loss of Non-Sensitive Information
Sensitive Information
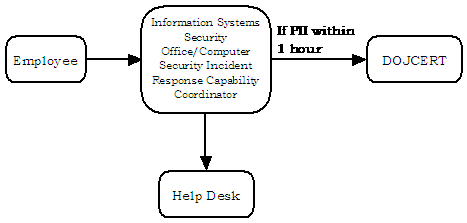
If sensitive information, including PII, is involved, ATF employees are required to contact the Information Systems Security Officer/Computer Security Incident Response Capability Coordinator directly. The Officer is then required to contact DOJCERT within the timeframes required for the category of incident. The Officer is also required to notify the Help Desk. Chart 6 shows ATF’s reporting procedures for loss of sensitive information.
Chart 6: Flowchart of ATF’s Reporting Procedures for Loss of
Sensitive Information
Classified Information
If classified information is involved, employees are required to contact the Information Systems Security Officer/Computer Security Incident Response Capability Coordinator in person or via secured facsimile or secure telephone. ATF officials told us that in practice the employee, although not required by written policy, will also notify his or her supervisor. The Computer Security Incident Response Capability Coordinator has a Top Secret clearance to respond to such incidents. The Information Systems Security Office is then required to contact both DOJCERT and Security and Emergency Planning Staff (SEPS), which handles the Department’s classified incidents. ATF does not provide DOJCERT or SEPS with details concerning the specific classified information that was lost or compromised. Chart 7 shows ATF’s reporting procedures for loss of classified information.
Chart 7: Flowchart of ATF’s Reporting Procedures for Loss of
Classified Information

Indications of Compliance with Reporting Procedures
ATF officials told us that they believed their employees were following the correct reporting procedures. While we did not validate this statement, our analysis of the Archer Database showed that ATF was not always reporting computer security incidents, including PII, within the required timeframes specified in both the DOJCERT and ATF Incident Response Plans. Between December 2005 and November 2006, ATF reported 78 percent of its computer security incidents to DOJCERT within the required timeframes. Further, 66 percent of the PII incidents that occurred on or after July 12, 2006 were reported within the required 1-hour timeframe.71 Table 7 shows ATF’s reporting in each category.72
| Table 7: ATF’s Timeliness in Reporting Incidents to DOJCERT | |||||
|---|---|---|---|---|---|
| Category | Reporting timeframe* | Incidents reported | Reported within timeframe | Reported after timeframe | Could not compute timeliness** |
Category 0 (Exercise/Test) |
None |
2 |
N/A |
N/A |
2 |
Category 1 |
1 hour |
13 |
2 |
10 |
1 |
Category 2 |
2 hours |
0 |
N/A |
N/A |
N/A |
Category 3 |
1 day |
9 |
5 |
2 |
2 |
Category 4 |
1 week |
5 |
3 |
1 |
1 |
Category 5 (Scans/Probes) |
1 month |
18 |
17 |
0 |
1 |
Category 6 (Investigation) |
None |
5 |
N/A |
N/A |
5 |
Category 7 |
1 month |
18 |
18 |
0 |
0 |
Total |
70 |
45 |
13 |
12 |
|
PII incidents occurring on or after 7/12/06*** |
1 hour |
6 |
4 |
2 |
0 |
* For purposes of this table, reporting timeframes for Categories 0-7 refer to the timeframes defined in the Incident Response Plan. Reporting timeframe for PII incidents refers to the timeframe defined in OMB Memorandum M-06-19. ** Some records did not include information to indicate when DOJCERT received the reports. Category 0 and 6 incidents, for which there are no reporting timeframes, are also included in this category. *** PII incidents were reported in varying incident categories. Source: Archer Database |
Ensuring All Incidents Are Reported
Although ATF uses several methods to ensure employees know to report computer security incidents involving potential data loss, it relies primarily on training. ATF uses the Department’s required annual Computer Security Awareness Training to educate and remind staff of their reporting responsibilities as well as of what is considered a reportable incident. All employees are also required to read and sign ATF’s Conduct and Accountability and Rules of Behavior statements that address employees’ responsibilities regarding the reporting of any incidents of improper use and the security and care of accountable property assigned to them. ATF also told us that it conducts property audits annually in which all staff are asked to bring in their accountable property to check against inventory. If property (such as a laptop or a BlackBerry device) is missing, the inventory uncovers the loss.
Notification to Affected Parties
ATF has not developed policies concerning notification to affected parties in the event of a loss of PII.
Determining the Type of Data Lost
To determine the type of data lost or compromised, ATF relies on interviewing the employee involved through an investigation conducted by the Computer Security Incident Response Capability team (which includes the Information Systems Security Officer as Computer Security Incident Response Capability Coordinator). The team determines, among other things, the type of incident, its level of impact, what action needs to be taken, and who should be involved in the investigation process. In interviewing the employee, the team attempts to determine what information may have been stored on the device. ATF staff told us that the Information Systems Security Office created a list of interview questions to help identify the lost or compromised data. ATF may also try to identify information on the employee’s hard drive through the network system.
As of January 31, 2007, the loss of PII had been confirmed in two of these eight incidents. The remaining six incidents involve potential losses of PII.
ATF H 7250.1, Automated Information System Security Program, July 26, 2006, p. B-13.
Previous regulatory guidance from NIST on information systems did not specifically define PII and as a result, Department components were not required to identify which systems process or store PII. OMB Memorandums M-06-15 and M-06-19 issued in May and July 2006 respectively, required federal agencies to identify and ensure adequate safeguards to protect systems that contain PII, defined PII, and required, for the first time, that all incidents involving PII be reported to US-CERT within 1 hour.
Executive Order 12958 provides for three classification levels. The “Top Secret” classification shall be applied to information, the unauthorized disclosure of which reasonably could be expected to cause exceptionally grave damage to the national security. The ‘‘Secret’’ classification shall be applied to information, the unauthorized disclosure of which reasonably could be expected to cause serious damage to the national security. The ‘‘Confidential’’ classification shall be applied to information, the unauthorized disclosure of which reasonably could be expected to cause damage to the national security.
According to ATF officials, ATF employees in the field offices report security incidents to their field supervisors who in turn report the incidents through their chain of command to the Help Desk and the Information Systems Security Office at ATF Headquarters.
Help Desk staff also are responsible for recording all incident reports from employees and making an initial assessment of the criticality (classified, mission-critical, and so forth) and the priority level of the incident and for assigning the incident to the Computer Security Incident Response Capability team for investigation.
The NCIC is a computerized index of criminal justice information (i.e., information on criminal histories, fugitives, stolen property, missing persons, foreign fugitives, immigration violators, violent gangs, and terrorist organizations) maintained by the FBI.
We did not analyze incidents for timeliness that occurred before OMB established the 1-hour timeframe in July 2006.
Our calculations are based on Categories 1 through 5 and Category 7. We did not include incidents found in Categories 0 and 6 because they had no associated time criteria, nor did we include incidents for which the Archer Database contained no information to indicate when DOJCERT received the report that an incident had occurred.