Review of the United States Marshals Service Judicial Security Process
Report No. I-2004-004
March 2004
The USMS Headquarters' Assessments of Reported Threats Routinely Exceed Internal Standard
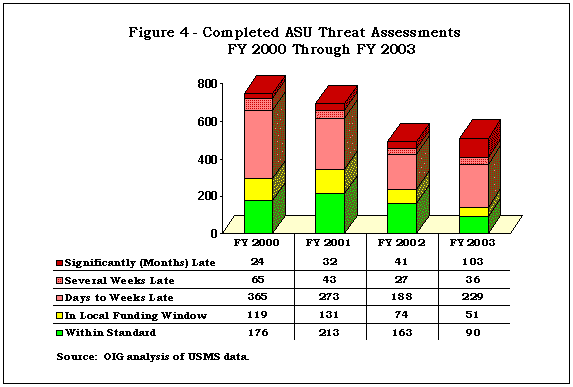
After two federal judges were assassinated in the late 1980s, the USMS developed a comprehensive system to assess threats and provide protective measures for federal judges. To ensure that threats were rapidly assessed and appropriate protective measures implemented, the USMS established policies and performance standards that require the ASU to assess all threats to the judiciary and post the results in WIN within a specified time period. To evaluate the timeliness of the ASU's assessments, we compared the date that ASU received the threat from the OST and the date that the ASU entered the assessment results in WIN from FY 2000 through FY 2003. We found that only 27 percent of threat assessments were completed within the standard time (Figure 4, next page).
Because threat assessments provide analytical information the JSD uses to allocate additional resources to districts to help them respond to threats when protective services details need to extend beyond a few days, we also examined how many threat assessments the ASU completed within a few days. We found that only 42 percent of the threat assessments were completed within the time that the USMS allows before additional resources may be provided.
From FY 2000 through FY 2003, the number of threats sent to the ASU for assessment decreased by 30 percent, from 841 cases to 585 cases.33 Despite the reduced number of threats, the ASU completed fewer assessments within the standard. In FY 2000 the ASU completed 176 cases in less than the standard time, but in FY 2003 it completed only 90 cases within the standard time. The number of cases in which the ASU's assessment was severely late also increased substantially. Specifically, the number of cases in which ASU took several months or more to complete its assessment more than quadrupled, from 24 cases in FY 2000 to 103 cases in FY 2003.
In examining the reasons for the USMS's failure to meet established timeframes, we found that the number of analysts that USMS has dedicated to assessing threats has decreased since the office was established in 1996. The ASU initially was staffed with six analysts, and the number of positions was later reduced to five. When we reviewed the program, only four of the five analyst positions were filled. The reduction in staff was compounded by the fact that the analysts perform duties other than conducting threat assessments. The ASU Chief told us that, at any given time, only "two or three" of the four analysts are conducting threat assessments. The analysts spend their remaining time assisting with fugitive cases and working on special projects and reports. Although these other efforts are important, the result is that fewer resources are available for assessing threats to the judiciary.
In response to USMS budget requests, Congress has repeatedly criticized the USMS's failure to hire employees to fill all of the USMS's authorized and funded positions. In response, the USMS told Congress that, in conformance with the Attorney General's direction to fight the war on terrorism by focusing resources on front-line positions, it has held off on filling headquarters positions except on a case-by-case basis.34 Nonetheless, a 2003 OIG audit noted that the USMS does not track where excess funds are expended.35 The failure to hire employees to fill positions and the unreconciled reallocation of salary dollars are particularly significant in an organization as small as the ASU, where one position represents 20 percent of the workforce.
ASU's "triage" system for threats does not ensure that the threats the USMS rates as most serious are processed timely. In February 2003, the USMS implemented a new practice under which the OST assigns a rating of high, medium, or low to all threats before forwarding them to the ASU for assessment. The ratings are assigned by an OST senior court security inspector based on his or her expert opinion; there are no written criteria for assigning the ratings. The ASU assesses all threats rated high first, followed by all threats rated medium, and then all threats rated low on a first-in/first-out basis.
We found that the triage system has not ensured that all threats rated "high" are processed in a timely manner. Data from the first eight months of operation under the triage system (February 2003 through September 2003) show that 68 threats were rated "high" for assessment out of a total of 408 threats reported. Yet only 20 of the assessments (37 percent) were completed within the standard time. Of the 48 assessments that took longer than the standard time, 30 took up to 10 days to complete, and 11 took from 10 days to as long as 47 days to complete.
Moreover, because the formal assessment of threats initially prioritized as "medium" or "low" is delayed, the triage system may have negative effects on the threat assessment process. The lack of written criteria for assigning ratings risks that some serious threats will be rated "medium" or "low," resulting in a delayed assessment. Also, one of the most important factors considered in assessing a threat is determining whether the person has made multiple threats and if the threatening behavior is escalating. The USMS considers these threats to be more serious. If all threats are not processed in a timely manner and in the order they are received, the assessments may not identify that other threats by the same person are pending, and the seriousness of the threat may not be accurately determined.
The USMS's Analysis of Threats Relies on an Outdated Analytical Tool
The database that the USMS uses to perform the comparative assessment on reported threats has not been updated since 1996 and therefore lacks current data on threats (including those involving terrorism) needed to reliably assess reported threats against the federal judiciary. When the ASU conducts a threat assessment, it compares the available information about the current threat and its initiator to information about prior cases contained in the historical threat database. The USMS ceased adding information on threats to the historical threat database in early FY 1996 and began entering threat assessments into WIN. As of September 30, 2003, ASU records showed that a total of 8,694 threats had been reported to the USMS since 1980. However, the historical threat database does not contain any information on 4,973 of those threats that were reported since 1996, including cases involving terrorism after September 11, 2001.
The ASU stopped adding information into the historical threat database because ISD decided that it would be more cost-effective to enter the data into WIN than to update the DOS-based, historical threat database program. In addition, according to the USMS, because many individuals who make threats also have outstanding warrants, entering threat information directly into the WIN system could speed the identification and apprehension of these individuals.36
Our analysis of WIN data since June 1996 did not substantiate the USMS's reasoning. We found that only 19 percent (772 of 3,756) of the individuals who made threats also had warrants issued for their arrest. Those 772 warrants represented only about one-sixth of one percent of the 483,983 warrants that were entered into WIN since June 1996. Moreover, the districts and the ASU cannot rely solely on WIN for threat information. Although WIN can be used to collect and share some information regarding threats to the federal judiciary, it was designed to support the USMS fugitive program and has been modified to collect and process only some threat information. For example, WIN provides the summary results of post-1996 threat assessments conducted by ASU but does not contain all of the threat details that were used to conduct the assessment.
While WIN was designed to systematically collect all relevant categories of information on threats in a format that supports the use of the information for future assessments, according to the ASU Chief, the USMS has not added a comparative threat assessment capability to WIN as originally planned. Therefore, although information on threats has been entered into the WIN since FY 1996, the ASU continues to conduct the comparative assessments on new threats using the outdated historical threat database.
The USMS continues to rely on the outdated historical threat database to allocate resources. The USMS's analysis of the historical threat database showed that, of all threats received from 1980 to 1996, 91 percent were "specious" (i.e., nothing further happened), 5 percent resulted in some form of escalation (e.g., additional threats, stalking), and 4 percent resulted in violence (e.g., vandalism of the judge's property or worse). According to Court Security Inspectors assigned to the OST, the USMS continues to allocate resources, including conducting threat assessments and implementing protective measures in response to threats, based on the presumption that only one in ten threats will escalate or result in violence. However, the extent to which the database is outdated casts serious doubt on the validity of that presumption.
In summary, our review showed that the USMS often fails to assess reported threats within its standard time and relies on an outdated assessment tool to assess threats to the federal judiciary. Without timely assessments, the USMS cannot fully identify and assess serious threats to judicial operations and personnel. Further, without any information on recent terrorist-related threats in the historical threat database, the validity of the ASU's comparative assessments for judging the severity of threats against the federal judiciary and identifying appropriate protective measures is questionable. The USMS's failure to ensure that threat assessments are both timely and based on current and complete data reduces the capability of the USMS to adequately protect the federal judiciary.
The USMS Has Limited Capability to Collect and Assess Intelligence to Identify Potential Threats to the Federal Judiciary
We found several limitations that prevent the USMS from effectively collecting and assessing intelligence from the districts and other sources, such as the FBI's JTTFs, to identify potential threats to the federal judiciary. The USMS's capability to collect and assess intelligence is limited by the lack of a central information collection capability; internal prohibitions on collecting information; incomplete participation in the FBI's JTTFs; insufficient security clearances; and inadequate secure communication systems.
These limitations persist, in part, because since September 11, 2001, the USMS has failed to implement new authority granted by Congress in the Patriot Act, and failed to act on internal studies to improve its information collection and sharing capabilities.
The USMS disbanded its centralized unit that collected, assessed, and shared information on threats to the judiciary, and issued internal guidance that limited information collection. Prior to 1994, the USMS had a formal centralized intelligence collection and assessment program operated by its Threat Analysis Division. However, during a 1994 reorganization of the USMS headquarters, the Director eliminated the Threat Analysis Division. Further, on April 5, 1996, the USMS Office of General Counsel (OGC) issued an opinion that directed the USMS to limit intelligence collection (including information in the databases used to track and assess threats) and threat investigations relating to extremist groups. The 1996 OGC opinion was based on the Attorney General Guidelines issued in 1983 which have been superceded, and cautioned Deputy Marshals that they could be held personally liable for collecting information not directly related to specific threat investigations.37 After the 1996 OGC memorandum, the USMS dismantled its remaining centralized intelligence capability by destroying all intelligence files not directly related to specific threat investigations.
The ISD Assistant Director told us that currently the USMS headquarters' only threat assessment capability resides with the ASU, but that the ASU is still prohibited from collecting and sharing information not related to specific reported threats. Moreover, even if the current OGC limitations on intelligence collection were removed, the current ASU staff could not provide a centralized information collection and sharing capability because, as described previously, it is unable to meet its current threat assessment workload.
Because the USMS headquarters has no centralized capability to collect and share information not related directly to a specific threat investigation, it must rely on Deputy Marshals in the districts and assigned to other Departmental intelligence operations (e.g., the BOP Sacramento Intelligence Unit, DEA's El Paso Intelligence Center, and the FBI's JTTFs) to collect and share information on potential threats to the federal judiciary. If one of these Deputy Marshals learns of a potential threat to the judiciary, he or she forwards that information to both OST and the appropriate districts. While these actions have some value, the information is not made available to all Deputy Marshals responsible for judicial security or systematically assessed and retained to identify trends and emerging threats. More importantly, we found that the current ad hoc efforts do not always provide threat information to the responsible field offices. For example:
The USMS's participation in the JTTFs is limited. According to October 2003 JTTF membership rosters provided by the FBI, the USMS has assigned only 50 Deputy Marshals to represent it on 29 of the 56 FBI field office JTTFs (6 of the Deputy Marshals were assigned by USMS headquarters and 44 were assigned by districts). Moreover, only 25 of the 50 are full-time representatives. The other 25 Deputy Marshals assigned to field office JTTFs, as well as the one Deputy Marshal assigned to represent the USMS on the NJTTF, are part-time representatives.
The USMS had planned to increase JTTF participation by assigning an additional 22 Deputy Marshals to the JTTFs, but was unable to do so. For FY 2003, the USMS requested $2.3 million to fund 22 additional Deputy Marshals to be assigned to field office JTTFs. Congress provided all of the requested funds, but directed that 18 of the new Deputy Marshals be assigned to "districts with the highest priority needs" at a cost of $1.4 million.38 The USMS complied with the congressional direction regarding the $1.4 million, but an FY 2003 OIG audit could not establish where the USMS allocated the rest of the money.39
The USMS JTTF representatives and their supervisors lack appropriate security clearances. In addition to the absence of full-time representatives on many JTTFs, the USMS's ability to access and share JTTF information on threats to the judiciary is also limited by a lack of security clearances. The July 2001 Memorandum of Understanding between the USMS and the FBI requires that Deputy Marshals assigned to a JTTF - as well as their appropriate supervisory personnel - must have Top Secret security clearances verified by the FBI to access JTTF intelligence. However, our review indicated that not all USMS representatives have the security clearances necessary for full access to JTTF intelligence. According to an October 2003 Top Secret clearance roster provided by the USMS, only 33 of the 50 Deputy Marshals listed on FBI JTTF rosters had a Top Secret security clearance.40
The lack of appropriate security clearances is not limited to the USMS representatives assigned to the JTTFs. While 92 of the 94 U.S. Marshals have Top Secret clearances, the Chief Deputy Marshals in 22 districts did not have the Top Secret Clearances required to supervise JTTF members or receive or review classified information.41 Overall, the USMS Top Secret clearance roster showed that only 876 of 4,761 USMS employees (17 percent), only 696 of 3,342 Deputy Marshals (16 percent), and only 26 of 106 of the recently assigned District and Circuit Court Security Inspectors (25 percent) possess a Top Secret clearance. In response to our survey, 25 of 85 responding USMS districts (29 percent) reported that they did not have any Deputy Marshals with a Top Secret clearance.
Further, some intelligence information has additional restrictions and requires a special authorization in addition to a Top Secret clearance for access. As the Joint Committee on Select Intelligence Inquiry concluded, "without [Sensitive Compartmented Information] clearances, non-intelligence community agencies are often unable to access vital counter-terrorism information."42 However, few USMS personnel have the additional authorizations to access Sensitive Compartmented Information. As of June 2003, only 144 USMS employees (3 percent) were authorized to access Sensitive Compartmented Information. Of those 144 individuals, 26 were assigned to just one district where a high-threat trial was underway.
According to the Chairman of the USMS Executive Working Group tasked by the Director to examine USMS intelligence capabilities, the wide-spread lack of clearances at all levels represents a barrier to improving intelligence collection and sharing. In the two cases we looked at, we found that the USMS's lack of effective participation in JTTFs negatively impacted the USMS's ability to provide appropriate security to the federal judiciary.
One intelligence-sharing breakdown occurred during a JTTF investigation of a terrorist cell. Arrests were imminent and, once the suspected terrorists were arrested, the USMS would be responsible for transporting and housing them, as well as for providing courtroom security. However, the responsible USMS district (which did not have a representative on the JTTF) was unaware of the investigation or the impending arrests until a few hours before they took place. This short notice precluded adequate planning for the extensive security measures needed to handle a large number of suspected terrorist prisoners.
The other case occurred during a high-threat trial that involved individuals who were accused (and subsequently convicted) of providing financial aid to terrorists. In that case, classified information that the district later considered critical to trial security was not disclosed to the USMS by the JTTF during the trial because the District's part-time representative to the JTTF did not have a Top Secret security clearance.
The USMS lacks the secure systems needed for Deputy Marshals to effectively share intelligence on threats to the judiciary. As of August 20, 2003, the USMS reported that only 51 of the 94 districts had the necessary secure communications equipment to effectively share classified information.43 In comparison, the U.S. Secret Service and the FBI indicated that they have fully implemented secure communications systems for sharing classified information and are working to further improve this capability.44
Further, threat information is contained in automated and manual systems maintained by individual districts, the JSD, and the ISD. The current systems do not interact to provide the USMS with a secure electronic information system that it needs to enable Deputy Marshals to collect and share threat information among all USMS districts. For example, to test the utility of the current USMS system of records for conducting threat investigations, we obtained information on two protective services details that the USMS currently has underway in the Southern District of New York. We found the information regarding the protective services details in several places, including WIN; historical budget records and operational plans from JSD manual records; current budget and operations plans from the district; and classified material maintained by JSD and ISD. A Deputy Marshal assessing a threat would be faced with the need to collect information from a variety of sources.
The USMS has taken only limited action to improve its information collection and sharing capabilities after September 11, 2001. After September 11, 2001, Congress passed the Patriot Act, which clarified the authority of federal agencies to collect intelligence and law enforcement information.45 Subsequently, the Attorney General Guidelines were revised to support law enforcement agencies' use of new powers relating to information collection and criminal procedures to more aggressively pursue potential criminal activity especially as it relates to terrorism.46 However, the USMS has not revised its internal guidance (i.e., the 1996 OGC opinion) to improve the collection and sharing of information on threats to the federal judiciary.
In addition, internal USMS studies conducted after September 11, 2001, identified the need for better information sharing. In September 2001, the Deputy Director of the USMS directed the Assistant Director in charge of the ISD to lead an Executive Working Group to examine the USMS's "capabilities with regard to the collection, analysis, maintenance, and dissemination of information and/or intelligence related material that impacts our criminal investigations and protective operations missions."47 A White Paper prepared in February 2003 for the Executive Working Group and other senior USMS staff described the limited USMS intelligence capabilities and the need for a centralized intelligence capability and better intelligence sharing, and concluded that the USMS "has no formal process to assess and disseminate information…to prepare for threats or to… participate fully in intelligence sharing."
A "Needs Assessment" prepared for the USMS Director in July 2002 identified a three-phase plan to catalog existing information resources, identify new resources, and develop a centralized information sharing program. The proposal envisioned a staff of 18. The program would collect information from the districts, USMS representatives on JTTFs, and USMS liaisons that would be assigned to the intelligence units of other agencies, including the Central Intelligence Agency, the Foreign Terrorist Tracking Task Force, the Secret Service Protective Intelligence Division, and others. The key goal of the new USMS unit would be to "fuse" information from across mission areas. To date, this program has not been implemented.
In summary, as of October 2003, the USMS has not taken basic steps to ensure that it has access to the information it needs to accomplish its judicial protection mission. To meet its responsibility to the federal judiciary, the USMS needs a centralized information sharing program to collect and share intelligence in order prevent acts of violence. Currently, two trial judges are under express death threats from terrorist groups, and other trials involving similar terrorist groups are underway. Despite the recognized importance of developing JTTF protective intelligence to support the USMS mission, including the expressed interest of the Congress in the USMS's participation in the JTTFs, the USMS has not established complete participation in all of the FBI's JTTFs. Without a structured, centralized intelligence process; the necessary Top Secret clearances; and the technology to facilitate intelligence sharing, the USMS cannot effectively access and use JTTF intelligence or other intelligence sources to identify potential threats to the federal judiciary.
The USMS Lacks Adequate Risk-Based Standards for Determining Protective Measures on Terrorist and Other High-Threat Trials
The USMS Policy and Procedures Manual (Manual) provides limited and outdated guidance for determining appropriate protective measures for high-threat trials. The chapter of the Manual that contains guidance and standards for judicial and court security, Volume X, has not been revised since July 1, 1993, and does not address protective measures to be applied when providing security on terrorist and other high-threat trials.48 For example, ten U.S Marshals and Deputy Marshals that we interviewed noted that the guidance in the Manual does not address many types of trials that present significant risks to the judiciary, such as criminal cases involving espionage, prosecutions of gang violence, and cases with cooperating witnesses. Moreover, a significant defining issue in recent high-threat trials - that the defendants are associated with international terrorist groups - is not included.
Our review of the Manual confirmed that it provides limited and inadequate guidance on determining protective measures on high-threat trials. For example:
Almost half of the USMS districts we surveyed identified the protective measures described above as valuable technology for ensuring judicial security. However, in the absence of adequate guidance and risk-based standards to ensure that appropriate protective measures are selected, the U.S. Marshals cannot ensure that the protective measures chosen are consistent with successful approaches applied in similar circumstances. Consequently, we found that, although districts developed the Operational Plans required by the Manual, they did not consistently apply similar protective measures in response to similar threats. For example:
Although specific protective measures must be selected based on the characteristics and risks of each individual trial or threat, the inconsistent approaches used in the field were not readily apparent to the USMS because it does not complete after-action reports on the protective measures taken. Without effective and current standards, and routine after-action reports, the USMS cannot identify inconsistent protections, needed improvements, or successful protective measures for ensuring the security of the federal judiciary.
The lack of adequate standards for protective measures during high-threat trials also prevents the USMS from ensuring that the districts are consistently provided additional resources to support appropriate protections. The USMS could not identify how many high-threat trials have taken place because USMS headquarters (specifically the JSD) only keeps records on high-threat trials for which it provides additional funding. The JSD does not track requests that are rejected, and USMS districts are not required to track or report the number of high-threat trials that occur.
In our survey, we requested that each USMS district estimate the percentage of trials that it perceived as involving increased risk. The responses we received (from 85 districts) indicated that about 20 percent of trials involved a "substantial potential for violence." According to the AOUSC, 12,817 trials were completed in U.S. District Courts in FY 2002.51 Extrapolating from the districts' responses to our survey, the number of trials with "substantial" risks could have exceeded 2,400. In contrast, JSD records from the last three fiscal years show that JSD provided support for an average of only 139 trials each year (Table 4). Without adequate risk-based standards, and without after-action reports to evaluate and improve its protection of the judiciary, the USMS cannot effectively ensure that the most significant risks are addressed and that its resources are used appropriately.
| Table 4 - JSD Funded High-Threat Trials | |||
|---|---|---|---|
| Fiscal Year | Number of "High-Threat Trials" Funded | ||
| 2001 | 139 | ||
| 2002 | 117 | ||
| 2003 | 162 | ||
| Source: JSD |
USMS Guidance on Protective Services Details is Outdated
When a protective investigation indicates that an individual may carry out a threat, and interventions such as the arrest or commitment of the individual for psychiatric observation are not feasible, the USMS district can implement increased personal protective measures to protect the threatened judge away from the court building. The USMS refers to these off-site protective measures, which can range from an escort to and from work to around-the-clock protection for the judge and his family, as "protective services details."
The USMS's guidance for protective services details is contained in its Policy and Procedures Manual, Volume X, January 1993, and in USMS Policy Directive 99-07, January 7, 1999, Protective Investigations. The Manual and Policy Directive are supplemented by The U.S. Marshals Service Protective Investigations Program, A Procedural Handbook for Threat Investigators and Supervisors, January 1999. Although our survey of USMS districts indicated that the use of protective services details has increased since September 11, 2001, the USMS guidance has not been updated.
In FY 2002, JSD provided resources for 21 protective services details, several of which included around-the-clock protection.52 The JSD only tracks protective services details for which it provides resources or expert advice. It does not track the total number of protective services details that are implemented throughout the USMS. In our survey, 71 of the 85 districts (84 percent) reported that they had used protective services details. Of those 71 districts, 14 (20 percent) reported that they had increased the use of protective services details since September 11, 2001. Despite the reported increasing use, we found that the USMS guidance on protective details has not been revised and contains outdated information. For example:
As with the application of security measures for high-threat trials, in the absence of clear standards, the districts we visited did not use a consistent approach for deciding when to implement protective services details or its makeup. The districts we visited could identify no specific criteria for determining the nature and extent of the protections they employed in each case. We also found that two individual protective services details on different judges were maintained while they were both inside the same secure courthouse, unnecessarily duplicating the protective coverage.