Review of the United States Marshals Service Judicial Security Process
Report No. I-2004-004
March 2004
Protecting the federal judiciary is one of the eight strategic goals of the Department of Justice (Department).13 The United States Marshals Service (USMS) is charged with meeting that goal by protecting members of the federal judiciary, court officers, and other threatened persons.14 To carry out its mission, the USMS Director and 94 U.S. Marshals appointed by the President and confirmed by the Senate oversee the operations of 4,761 employees (3,342 Deputy Marshals and 1,419 administrative personnel) at 350 locations around the country.
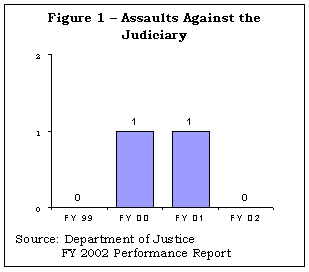
The USMS measures its effectiveness in meeting the strategic goal to protect the judiciary by tracking the number of assaults against the more than 2,000 federal judges and magistrates that the USMS protects. The target for success is zero assaults. As shown in Figure 1, there were no assaults in FYs 1999 and 2002, but there was one each in FY 2000 and FY 2001.
Since FY 2001, Congress has increased the USMS's funding for judicial security by approximately 50 percent. On April 1, 2003, the Attorney General asked Congress for more resources for judicial security. Stating that "[s]ecurity surrounding terrorist-related court proceedings requires an unprecedented level of protection for all trial participants because of the global interest and intense media attention," the Attorney General asked for "significant resources to improve courtroom security… associated with terrorist-related court proceedings."15 While increasing funding for judicial security, Congress also has expressed concern that "as the program has grown sufficient attention has not been provided to program and budget administration…."16
High-Threat Trials
Although trials with greater than normal risk may be referred to as "high risk", "high profile," "high visibility," or "sensitive" trials, the term "high-threat trial" is most commonly used by the USMS and by Congress. Recent high-threat trials included:
Sources: Senate Report 107-218, Departments of Commerce, Justice, and State, Appropriations Bill, 2003; White House Progress Report on the Global War on Terrorism, September 2003. |
The USMS Judicial Security Division
The USMS Judicial Security Division (JSD) provides for the general security of federal courthouses, federal courtrooms in other buildings, and the personal security of the federal judiciary when they are most vulnerable - away from their courtrooms and chambers.17
In FY 2002, the JSD supervised security for 117 high-threat trials, coordinated 150 personal protective services details for Supreme Court Justices traveling outside the Washington Metropolitan Area, and coordinated security for 165 judicial conferences and 20 other events attended by the federal judiciary. The JSD directs the following three program areas.
Court Security Program. This program provides operational and administrative support to the 94 USMS districts to assist them in protecting the federal judiciary and other officers of the court. The program provides operational and administrative assistance on security for judicial conferences and high-threat trials; security surveys of federal courts and other facilities and some state and local courts; security education programs for federal and state courts; security details for Supreme Court Justices outside the District of Columbia Metropolitan Area; and protective investigations and protective services details for the federal judiciary.
The program is administered by the Operational Support Team (OST), which consists of four Senior Court Security Inspectors (Deputy Marshals) and administrative personnel. Prior to FY 2003, the USMS had 3 Senior Court Security Inspectors assigned to the OST at USMS headquarters and 28 Circuit Court Security Inspectors assigned to the 13 judicial circuit courts across the country. Shortly after September 11, 2001, at the request of the Administrative Office of the United States Courts (AOUSC), Congress provided 106 additional District and Circuit Court Security Inspector positions.18 In May 2003, the USMS deployed the 106 Court Security Inspectors to the 94 federal district courts and 12 of the 13 circuit courts.19
Judicial Protective Services Program. This program provides about 4,000 contract guards, called Court Security Officers (CSOs), assigned to all federal district courts and circuit courts. The CSO's provide day-to-day security at courthouse entrances and inside the courtroom.
Central Courthouse Management Group. This group works with district personnel, the General Services Administration, and the AOUSC when planning the construction of new federal courthouses and the renovations of existing courthouses.20 The group also provides security expertise concerning prisoner movements and the safety of detention facilities.
|
Warrant Information Network
WIN is the USMS's central law enforcement information system. WIN contains more than 700,000 subjects of USMS fugitive and protective investigations and is used to track the status of all federal warrants to aid in the investigations of all federal fugitives. It is also used to access the National Law Enforcement Telecommunication System (NLETS) and National Crime Information Center (NCIC) systems to obtain criminal record information from other federal, state, local and foreign law enforcement agencies. Sources: USMS Investigative Operations Manual, April 2003. Report No. 03-03, Office of the Inspector General, November 2002. |
The Analytical Support Unit (ASU)
In addition to JSD, the Analytical Support Unit (ASU) located in the Investigative Services Division (ISD) supports the USMS's judicial security effort. The ASU provides information and investigative support to USMS investigators protecting the judiciary and conducting fugitive investigations. The ASU works with the Social Security Administration, the Department of Defense, Defense Information Systems Agency, the Department of Agriculture, and various high intensity drug trafficking task forces to locate fugitives. The ASU also administers the Warrant Information Network (WIN) and conducts assessments on threats to the federal judiciary.
Threats to the Judiciary
The USMS Policy and Procedures Manual, August 6, 1993, defines threats as any communications or actions intended to intimidate, impede, or interfere with a member of the judiciary, their staff, or their family. Threats may be direct or may be implied by suspicious behavior, such as stalking or demonstrating unusual or excessive interest in a judge or a judge's family. Threats can be verbal or written, and can be delivered in person, by mail, by telephone, or by e-mail. In some cases, threats may be reported by a third party, such as when an informant tells authorities of a plan to harm a judge. According to the USMS, most threats against judges are made by individuals angry about the outcome of a particular court case in which they, or people they know, were involved.21
The USMS requests federal judges and their staffs to report every threat. However, in 1994 the General Accounting Office (GAO) found that almost 25 percent of the judges responding to its survey did not report all or even most of the threats they received to the USMS.22 Further, in November 2001 a report prepared for the AOUSC concluded that the off-site security program, particularly the reporting of threats, was underutilized by judges.23 From FY 1998 through FY 2003, the USMS responded to an average of 691 threats to the federal judiciary each year, most of which came from known sources (Table 1).
| Table 1 - Threats to the Judiciary FY 1998 through FY 2003 | |||
|---|---|---|---|
| Fiscal Year | Number Reported | Source Unknown | Source Known |
| 1998 | 790 | 104 (13%) | 686 (87%) |
| 1999 | 814 | 109 (13%) | 705 (87%) |
| 2000 | 702 | 109 (16%) | 593 (84%) |
| 2001 | 690 | 126 (18%) | 564 (82%) |
| 2002 | 565 | 101 (18%) | 464 (82%) |
| 2003 | 585 | 105 (18%) | 480 (82%) |
| Source: USMS |
The USMS also has assigned Deputy Marshals to other Department of Justice components to collect and share information about potential threats to members of the federal judiciary. These include:
If a USMS representative to one of the above operations identifies a potential threat to the judiciary, the representative forwards the information to the OST and the appropriate districts.
The USMS Response to Threats to the Judiciary
When a threat is reported, a Deputy Marshal conducts a preliminary inquiry to determine the source of the threat and initiate an appropriate response. Unless the inquiry demonstrates the clear absence of significant risk, a protective investigation is initiated. If a threat is initially assessed as likely to be carried out, the USMS will employ a range of interim protective measures to prevent the judge from being harmed.
|
Protective Investigations
"A protective investigation is a process used by the USMS to manage a case to ensure that purveyors of Inappropriate Communications no longer present a threat to the designated protectee. A protective investigation incorporates a range of tactics and strategies designed to identify, diffuse, and manage any potential risk of harm to a protectee. This may include, when appropriate, committing the subject to a mental hospital, obtaining restraining orders, arresting the subject, or maintaining contact with the subject." Source: "Offsite Security Booklet for Judicial Officers," (USMS Publication 94, March 1999) |
The districts are responsible for providing the Deputy Marshals, administrative support, and any other resources needed during the first days of a protective services detail. If the protective services detail will take longer than a few days, the districts may request, from the OST, additional staffing and financial resources. The protective services detail ends when the USMS determines that the judge is no longer in danger.
The USMS Policy and Procedures Manual, August 6, 1993, requires districts to report the result of every preliminary threat investigation and any protective measures taken to the OST in a "Preliminary Threat Report."27 In addition, districts are required to notify the FBI, which determines if the threat warrants a criminal investigation.28
At USMS Headquarters, the preliminary threat report is reviewed by the OST and forwarded to the ASU for an assessment of the legitimacy and seriousness of the threat.29 USMS Policy Directive 99-07, Protective Investigations, January 7, 1999, requires the ASU to complete its assessment and enter the results into the WIN within a specified time period.30
In conducting its threat assessment, the ASU determines if the threat meets the specific criteria required for the communication or other behavior to be considered a threat. If the criteria are met, and if the identity of the person who made the threat is known, the ASU queries various public and law enforcement databases to determine whether the person has made threats before and if the person has any other law enforcement records.
Next, the ASU conducts a two-step threat assessment. In the first step, the ASU completes a comparative assessment that matches the characteristics of the current threat to threats in its historical threat database to identify prior threats with similar characteristics. The comparative assessment results in a report describing how closely the current threat matches the profiles of past threats with known outcomes. The historical threat database contains information on 3721 threats reported from 1980 to 1996. Each threat is catalogued by up to 30 variables, including the date of the threat, the method of delivery, if the initiator of the threat was identified, his or her motive, and if he or she carried out the threat.31 Of the threats listed in the historical threat database, no additional action happened after the threat was received in 91 percent of the cases (the USMS terms these types of threats as specious); there was some escalation of activity (such as a suspicious act or an additional communication) in 5 percent of the cases; and the threat resulted in a USMS-defined "violent outcome" (such as an act of vandalism on a judge's property or an attempted physical assault) in 4 percent of the cases (Table 2).
| Table 2 - Historical Threat Database Outcomes 1980 to 1996 | ||
|---|---|---|
| Outcome | Number | Percent |
| Specious | 3,296 | 91.02 |
| Enhanced | 182 | 5.03 |
| Violent | 143 | 3.95 |
| Total | 3,621 | 100.00 |
| Source: USMS (Note: ASU reports that while there are 3,721 threats in the database, only 3,621 have associated outcomes. The remaining 100 cases had no outcome recorded.) |
In the second step of the assessment, the ASU examines the threat using a proprietary computer-based threat analysis system. The threat analysis system is customized to address the specific needs of the USMS in protecting the federal judiciary by assessing threats using questions about the behavior and background of the threat initiator. The system organizes the details of the current threat and allows the analyst to compare the threat with known outcomes of prior cases.
The assessment results in a rating from one through ten, with higher ratings indicating cases with greater similarity to those in which there is a greater risk that the threat will escalate. Lower ratings indicate that the case has characteristics similar to those that have not escalated, and therefore are considered less serious. Of the 4,297 threats that the USMS assessed using the system through October 31, 2003, about 22 percent received a higher rating (Table 3, next page).
The comparative and threat analysis system assessments should have similar outcomes. If the comparative assessment indicates low risk, then the threat analysis system should indicate low risk as well. When comparative and threat analysis system assessments do not show a similar outcome, the ASU resolves the disparity by requesting additional information from the district to reassess the threat, or provides possible explanations for the disparity to the district. The ASU enters the comparative and threat analysis system assessment results into the WIN.
The district investigating the threat uses assessment results posted in WIN to help determine if adequate protective measures are in place. If a protective investigation is conducted, the WIN record is used by the district and the ASU to track and manage the case as new information is collected and additional investigative work is accomplished. If significant new information is collected, the district can request that the ASU reassess the threat (Figure 3, next page).
| Table 3 - Ratings for Threats | ||
|---|---|---|
| Rating | Number of Threats | Percent |
| 10 | 0 | 0 |
| 9 | 0 | 0 |
| 8 | 63 | 1.5 |
| 7 | 324 | 7.5 |
| 6 | 564 | 13.1 |
| 5 | 871 | 20.2 |
| 4 | 1,754 | 40.9 |
| 3 | 643 | 15.0 |
| 2 | 72 | 1.7 |
| 1 | 5 | 0.1 |
| Total | 4,297 | 100.0 |
| Source: USMS |
Figure 3 - USMS Threat Assessment and Protective Measures is not available electronically. |
Purpose, Scope, and Methodology
The purpose of this review was to examine the USMS's efforts to ensure the safety of more than 2,000 federal judges and magistrates. We evaluated the USMS's efforts since September 11, 2001, to improve its protection of the federal judiciary. We focused specifically on the USMS's ability to assess threats and determine appropriate measures to protect members of the federal judiciary during high-threat trials and while they are away from the courthouse. We conducted the fieldwork for this review from March 3 through October 18, 2003.
Interviews: We interviewed USMS headquarters officials in the JSD, ISD, and the Office of General Counsel (OGC). We visited and interviewed USMS district officials in the Western District of North Carolina and the Western District of New York to review the security measures associated with recent high-threat trials in those districts. We visited the Southern District of New York for information on high-threat trials and on that district's long-running protective services details for two federal judges who presided over previous terrorist trials. We reviewed USMS files collected on these two long-running protective services details and other protective services details. Substantial portions of those records are classified. For additional information on the threat assessment process, we interviewed officials with the U.S. Capitol Police and the U.S. Secret Service about their respective protective missions.
Databases: We reviewed and analyzed threat data maintained by the ASU, including the historical threat database, computerized threat analysis system, and WIN. We reviewed and analyzed USMS security clearance data provided by its Human Resources Division. We also reviewed records maintained in the USMS's Judicial Protection Information System, which was established "to identify security risks and to develop operating plans and carry out security measures to counteract threat situations" for information related to judicial security.32
Surveys: We sent a judicial security survey to all 94 USMS district offices (85 districts responded). We asked the Judicial Security Division (JSD) to conduct a self-assessment and to report post-September 11, 2001, improvements in the judicial security process. The JSD self-assessment appears in Appendix I.
USMS Training: We attended two USMS training sessions on threat assessments and the high-threat trial management process. The first session occurred on April 11, 2003, and involved the threat assessment portion of the Advanced Deputy United States Marshal training. The second session occurred on May 6 and 7, 2003, and involved District and Circuit Court Security Inspector training in San Antonio, Texas.
Additional Resources: The U.S. Capitol Police provided sample documents and other written information regarding its threat assessment process, and the U.S. Secret Service provided copies of several publications and two videotapes on its threat assessment process. In addition, we reviewed the literature generally available regarding the protective services field. We reviewed more than 50 documents, including Departmental publications, articles in professional journals, GAO reports, congressional committee reports and hearing transcripts, and other publicly available congressional information. Among the documents we reviewed were: