- To combat the online sexual exploitation of children, the FBI established the Innocent Images National Initiative (IINI) in 1995. In FYs 2006 and 2007, the FBI opened over 2,000 IINI cases each year and, on average, focused 70 percent of its 238 IINI Special Agent personnel on investigating online child exploitation criminal enterprises and producers of online child pornography – the top IINI priorities. The nature of online activity makes cyber-related sexual exploitation of children a borderless crime and requires effective coordination to address enterprises and persons that sexually exploit children through the Internet. The FBI coordinated its IINI efforts domestically under the DOJ’s Project Safe Childhood initiative and internationally through an international task force spearheaded by the FBI. We concluded that the FBI could improve its operations to address the online sexual exploitation of children in several areas. Specifically the FBI has a backlog of digital evidence in cyber crimes against children cases awaiting forensic analysis, which can impede the investigation of child exploitation cases. In addition, we found that the FBI’s undercover employees working child pornography cases were not receiving timely, routine psychological assessments as required by FBI policy. Further, the FBI lacked a policy governing psychological assessments for other employees, such as forensic examiners and non-undercover Special Agents, whose jobs expose them to child pornography and the possible adverse mental health effects associated with such exposure.
Child pornography is defined in the U.S. Code as “visual depictions… of sexually explicit conduct” involving minors.50 The advent of the Internet and continuing advances in technology have simplified the production, distribution, and ease of accessing such depictions. One distinguishing feature of Internet-facilitated child pornography from the printed counterpart is that an electronic file of the images can be easily copied, disseminated, stored, and archived. In short, the electronic file has no shelf life and may exist in perpetuity with limitless distribution potential. Additionally, the proliferation of Internet-facilitated child pornography has led to an increase in the number of violent images used in child sexual exploitation. An increasing number of victims of these crimes are younger children, including toddlers and infants.
FBI officials pointed to a rapid rise in the incidence of online sexual exploitation of children. One measure of this increase is the growing caseload of NCMEC’s CyberTipline®, created in March 1998 as a clearinghouse for collecting intelligence and leads on sexual crimes against children. In 2003, the CyberTipline® received 7,038 reports relating to cyber-facilitated child pornography; in 2007, 20,760 of such reports were received. In total, the CyberTipline® received 77,167 reports from 2003 to 2007 specifically relating to cyber-facilitated crimes against children.51
Based on our analysis of the research literature, we identified the following characteristics of online sexual exploitation of children and issues for law enforcement.52
- Internet accessibility and innovations such as digital cameras have led to a greater supply and demand in cyberspace for images of the sexual exploitation of children.
- Because cyberspace has no territorial borders, law enforcement agencies have had to operate with redefined “jurisdictions” when investigating cyber crimes against children.
- Innovations in digital storage devices have increased the volume of exploitative images of children and, consequently, the amount of digital evidence that must be forensically processed.
These characteristics present significant challenges for law enforcement officials investigating these crimes. Not only is the crime becoming more frequent, law enforcement officials must also keep pace with the constant evolution of technological capabilities being employed in the production and distribution of exploitative images of children.
Innocent Images National Initiative
To combat the online sexual exploitation of children, in 1995 the FBI established a nationwide investigative response by creating its Innocent Images National Initiative (IINI). The IINI Unit is a component of the FBI Cyber Division that investigates major online groups, producers, manufacturers, and possessors of sexually exploitative images of children. Additionally, IINI has responsibility for investigating adults who entice minors via the Internet in an effort to exploit them sexually. Since its inception, IINI has reported significant increases in the number of cases initiated and the number of convictions obtained as a result of these investigations.
IINI’s OPERATIONAL STATISTICS
FISCAL YEARS 1996 THROUGH 2007
| FY | Investigations Initiated |
Convictions53 |
|---|---|---|
| 1996 | 113 | 68 |
| 1997 | 301 | 87 |
| 1998 | 698 | 84 |
| 1999 | 1,497 | 315 |
| 2000 | 1,541 | 476 |
| 2001 | 1,559 | 557 |
| 2002 | 2,370 | 646 |
| 2003 | 2,430 | 714 |
| 2004 | 2,645 | 881 |
| 2005 | 2,402 | 994 |
| 2006 | 2,135 | 1,018 |
| 2007 | 2,443 | 1,023 |
| Total | 20,134 | 6,863 |
By comparison, the FBI’s statistics on the non-cyber-related interstate transportation of obscene matter involving children have been significantly smaller. The FBI opened 47 investigations of non-cyber-related child pornography crimes in FY 2003 and only 13 investigations in FY 2007. These figures are consistent with the ongoing trend of offenders using cyberspace as the primary venue for the sexual exploitation of children.
The FBI developed policies to help ensure that it provides adequate managerial controls over IINI. Our review of the application of these policies revealed that the FBI generally provided the necessary oversight of IINI to address the challenges of combating the online sexual exploitation of children.
Prioritization of Cyber Crimes Against Children
The investigation of cyber crimes – including those directed against children – ranks third among the overall investigative priorities of the FBI, behind only counter-terrorism and counter-intelligence.54 Within the overall category of cyber crimes against children, the FBI increased the investigative classifications of IINI from one to four in January 2002 to account for the variety of these crimes. In September 2005, the FBI further established a priority order to help Special Agents address incoming leads. The following table outlines the priority ranking of the four classifications of the FBI’s cyber crimes against children program.
PRIORITIES OF THE FBI’S IINI PROGRAM
| Ranking | Classification | FBI’s Rationale for Priority Ranking |
|---|---|---|
| 1 | Enterprises operating commercial child pornography websites or promoting and facilitating the exchange of child pornography amongst group members55 | Complex multi-subject, multi-jurisdictional, and international investigations |
| 2 | Producers of child pornography | Opportunities to identify and rescue victims from on-going exploitation |
| 3 | Online enticement of minors through mechanisms such as chat rooms | Subjects who take concrete steps to exploit children |
| 4 | Possession of child pornography | Most common violation – investigate if an enterprise-level nexus exists |
To assess the FBI’s efforts in each of the four categories and whether the FBI adhered to these priorities for investigating cyber-related child exploitation, we analyzed FBI data on case openings and resource utilization for IINI investigations that started after the September 2005 establishment of the priorities. The following table shows the number of cases opened in FYs 2006 and 2007 for each IINI investigative category. In both FYs 2006 and 2007 the FBI reported opening over 300 enterprise-level investigations, and in FY 2007, the FBI reported opening more than 1,000 child pornography production cases.
FBI IINI CASE OPENINGS
FISCAL YEARS 2006 THROUGH 200756
| Fiscal Year |
Groups and Enterprises | Producers | Enticement | Possessors | ||||
|---|---|---|---|---|---|---|---|---|
| Cases | % | Cases | % | Cases | % | Cases | % | |
| 2006 | 309 | 14 | 862 | 40 | 488 | 23 | 474 | 22 |
| 2007 | 354 | 14 | 1,079 | 44 | 456 | 19 | 564 | 23 |
The investigations of enterprise-level groups are time‑consuming because they frequently involve multiple subjects and coordination with foreign law enforcement agencies. While the proportion of opened enterprise-level cases was the lowest of the four IINI investigative categories, FBI Special Agent resource utilization data shows that 36 percent of agents working IINI cases were involved in enterprise-level investigations. As shown in the following pie chart, 70 percent of the Special Agent resources utilized on IINI cases investigated enterprises and producers of cyber-related child pornography – IINI’s top priorities. These data demonstrates that the FBI is adhering to its established priorities for investigating cyber-based sexual exploitation of children.
SPECIAL AGENT UTILIZATION FOR IINI CASES
AVERAGE FOR FYs 2006 and 200757
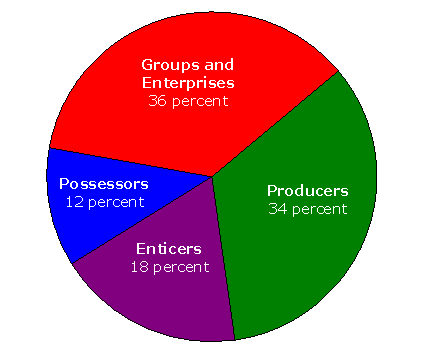
Source: OIG analysis of FBI Special Agent resource utilization data
Cyberspace has no territorial borders, requiring multi-jurisdictional investigations for cases of online sexual exploitation of children. According to a November 2003 study released by NCMEC, 79 percent of the 630 cases reviewed on Internet-related child pornography or sexual exploitation arrests involved 2 or more law enforcement agencies and 46 percent involved 3 or more agencies.58 In a typical scenario, a person living in one city may have downloaded child pornography from a website located in a different city, county, state, or country, and the victimized child may reside in yet another domestic or international location. In such a multi-jurisdictional environment, effective coordination is essential for agencies involved in investigating Internet crimes against children.
The FBI coordinates with other agencies in the investigation of cyber crimes against children through two primary mechanisms. First, the FBI participates in Project Safe Childhood, a 2006 DOJ initiative. Second, in 2004 the FBI created its IINI International Task Force (ITF), which is comprised of foreign law enforcement agencies to address this borderless crime.
Project Safe Childhood
Attorney General Alberto Gonzales made protecting children from crimes facilitated by computers a DOJ priority when announcing the Project Safe Childhood (PSC) initiative on February 15, 2006. The goal of PSC is to enhance the national response to Internet-based crimes against children through the collaboration of law enforcement agencies and non-profit organizations. Additionally, PSC requires each U.S. Attorney’s Office to designate a PSC Coordinator, who is responsible for assisting agencies in improving the response to online crimes against children.
The Attorney General specifically cited in the PSC announcement the DOJ‑supported Internet Crimes Against Children (ICAC) task forces.59 The purpose of the ICAC task forces is to help state and local law enforcement agencies in their efforts to combat cyber crimes against children through training, investigative assistance, and victim-related services. After the announcement of the PSC, the FBI issued in August 2006 an internal memorandum to cyber crime supervisors at all field offices stating that the “FBI will fully integrate ICAC task forces with state and local law enforcement” in support of the efforts to combat online sexual exploitation of children. The ICAC task forces began with 10 task forces in 1999. By October 2007, there were 59 ICAC task forces in all 50 states.
To learn about the FBI’s level of involvement with and contribution to the PSC, we interviewed the PSC Coordinator at the U.S. Attorney’s Office and representatives from the local ICAC task force at each of the five FBI field office locations that we visited.60 The PSC Coordinators at all five locations generally made positive statements regarding the FBI’s efforts in combating cyber crimes against children. For instance, the PSC Coordinator in Miami stated that although forensic examinations of evidence by the FBI generally take longer to complete than examinations conducted by other agencies, the quality of the examinations was consistently high. In St. Louis, the PSC Coordinator stated that the investigations by the FBI serve as a model for state investigators in bringing their cases to the federal level for prosecution, explaining that about half of the federal cases in that district originated in local jurisdictions but were transferred to the federal system in order to take advantage of the more severe penalties under federal law. On the other hand, a PSC Coordinator in San Francisco stated in May 2007 that the frequent turnover of staff, both at the FBI and in other agencies, adversely affected the continuity of investigations and the training of new personnel.
While conducting our site work, we identified St. Louis, Missouri, as a good example of a location with a well-established infrastructure on interagency coordination for investigating cyber crimes against children that pre-existed the PSC initiative. In 1999, law enforcement agencies from the St. Louis metropolitan area formed the Regional Computer Crimes Education and Enforcement Group (RCCEEG) of Greater St. Louis to combine the investigative resources and expertise of federal, state, and local law enforcement agencies and judiciaries. In 2001, RCCEEG became the Missouri ICAC task force after receiving an ICAC grant from OJJDP. Currently, the FBI squad that conducts investigations on cyber crimes against children is co-located with the Missouri ICAC task force at the Clayton Police Department in Clayton, Missouri. According to federal and state officials, this co-location facilitates the exchange of information and coordination on investigations between the FBI and members of the ICAC task force. Our interviews with members of the ICAC task force disclosed a high degree of satisfaction with the level of coordination between the Missouri ICAC and the FBI.
Although three other FBI field offices we visited did not adopt the co‑location concept, local ICAC representatives reported a positive working relationship and integration with its FBI counterparts in San Francisco, California; Boston, Massachusetts; and Miami, Florida.
By contrast, our fieldwork in Los Angeles identified issues of concern over the level of interagency cooperation when working investigations of cyber sexual exploitation of children. In June 2007, the PSC Coordinator at the USAO for the Central District of California praised the FBI Los Angeles Field Office for having created an effective mechanism for coordinating the FBI’s crimes against children investigations: the Sexual Assault Felony Enforcement (SAFE) team, a multi‑agency task force composed of the FBI and seven other law enforcement agencies.61 However, officials from Immigration and Customs Enforcement (ICE) and Los Angeles Police Department (LAPD) in Los Angeles stated that they rarely interacted with the FBI SAFE team. These omissions are significant because ICE specializes in cyber crimes against children with a trans-border or transnational nexus, while the LAPD houses the local ICAC task force.
In January 2008, the role of the PSC Coordinator in Los Angeles was reassigned to two Assistant U.S. Attorneys. The new PSC Coordinators informed us that they were holding meetings with the FBI, ICE, and LAPD in order to improve coordination among these agencies in cyber crimes against children investigations. These meetings discussed issues such as whether ICE would assign an officer to the SAFE team at the FBI Los Angeles Field Office, as well as the PSC’s plans for all law enforcement agencies in the jurisdiction to conduct a major initiative of investigating adults who commit cyber crimes against children using peer-to-peer networks. Regardless of the eventual outcome of these meetings and the peer-to-peer initiative, we believe that opportunities exist for the FBI SAFE team to improve its relations with its partners. We recommend that the FBI Los Angeles Field Office continue to work with the PSC Coordinators in addressing these crimes with its counterparts at the local ICE and ICAC task force.
IINI International Task Force
According to the FBI, cyber crimes against children increased by 2,050 percent from FYs 1996 to 2005. In the fall of 2004, the FBI created its IINI International Task Force (ITF) to address this global crime problem. The ITF trains law enforcement agents from other countries in the investigation of these crimes and helps the FBI establish working relationships within the international law enforcement community. Since its inception, the ITF has trained over 47 foreign law enforcement officers from Europol and 22 countries.62 According to the Chief of IINI, participating countries of the ITF generally fall into two categories: (1) developed countries where the citizens have disposable income to purchase child pornography and (2) developing countries where children are at risk of being victimized through sexual exploitation.
By participating in the ITF, foreign law enforcement officers have the opportunity to work alongside FBI Special Agents investigating cases of crimes against children.63 This also helps the FBI establish relationships with its foreign counterparts, which are crucial to the successful coordination on crimes against children investigations after the foreign law enforcement officers return to their home countries. According to the FBI, global partnership through the ITF has facilitated the exchange of intelligence between the FBI and its foreign counterparts in international investigations of cyber crimes against children.
The IINI Unit Chief believed that the ITF was helpful in investigations requiring assistance from foreign law enforcement counterparts. For example, a law enforcement officer in Toronto, Canada, who was trained in the ITF program, discovered images posted on a British website of extreme sexual exploitation of a 6‑year-old girl. The IINI Unit Chief and the Supervisory Special Agent who oversaw the investigation both informed us that these were probably the most heinous images of child sexual exploitation they had ever seen. Through analysis of these images, Canadian officers identified unique marks on the child’s clothing and forwarded the intelligence to the FBI for investigative assistance.64 The FBI eventually traced the victim to a residence in North Carolina and identified the father of the victim as the producer of the images. As a result of the global ties established by the FBI through its ITF, the FBI recovered the child victim and arrested the father, who was convicted of 4 counts of sexual exploitation of a child and sentenced to 100 years in prison.
This example demonstrates that the IINI ITF can be an effective means to secure international coordination and recover victimized children. At the outset of our audit, one IINI official mentioned the possibility of extending the ITF to include law enforcement partners from South America. In August 2008, we learned that law enforcement representatives from Brazil are among the newest members of the IINI ITF. We agree expansion of the ITF would be valuable to the FBI’s efforts in combating the sexual exploitation of children, and we encourage the FBI to pursue additional ITF partnerships.
Forensic Analysis of Digital Evidence
A criminal investigation conducted by IINI normally requires the forensic analysis of digital evidence seized. Currently, forensic analysis of digital evidence at the FBI is conducted by its Digital Evidence Section (DES), a component of the Operational Technology Division. The DES is comprised of five units, of which the Computer Analysis Response Team (CART) Unit and the Regional Computer Forensic Laboratories (RCFL) are the primary units assisting IINI. The CART Unit and the RCFLs provide forensic analysis of digital evidence for all types of crimes investigated by the FBI, including crimes against children.65 As of Fall 2008, the CART Unit was composed of approximately 255 forensic examiners.66 FBI computer forensic examiners, certified by the CART Unit, are responsible for forensically examining digital evidence supporting the FBI’s national security and criminal investigative missions, including the IINI.
In the context of cyber crimes against children, digital evidence typically comes in the form of computers, storage media, and other devices that contain child pornography collected, received, produced, or distributed by the subject and text files such as e‑mail messages or chat room transcripts showing exchanges between the adult subject and minor victims. The FBI’s forensic examiners employ specialized techniques to review digital evidence and identify material for use in investigations and prosecutions of criminals.
To evaluate the FBI’s program in the forensic analysis of digital evidence, we interviewed DES officials, evaluated policies and procedures, and reviewed data on forensic analysis of digital evidence. Our review found problems in the timely processing and forensic analysis of digital evidence.
The Process of Forensic Analysis of Digital Evidence
Forensic analysis of digital evidence formally begins when a Special Agent submits a request for services to the CART or RCFL. Upon receipt of the digital evidence, the DES assumes custody of the evidence and assigns the request for service to an available forensic examiner. Thereafter, the CART or RCFL forensic examiner works with the digital evidence through the following sequenced events:
- preserving, imaging, and authenticating the evidence;
- processing the imaged evidence to render it intelligible;
- presenting the processed evidence to case investigators on a specialized review platform to facilitate their search through the data for information relevant to the facts of their specific investigation (and as needed, assisting investigators in that search process);
- forensically retrieving information or data tagged by the investigators as relevant to their investigations; and
- preparing a report of the forensic analysis.
According to the FBI, it generally takes about 3 to 4 hours to image and authenticate the digital evidence, which involves creating a copy of the evidence seized and ensuring that the copy is an exact duplicate of the original evidence. Processing the “imaged” copy of the seized evidence consists of creating a list of all files found, as well as generating and comparing known and unknown “hash values” (or a digital “fingerprint”) to identify the files or images.67 According to the FBI, processing the evidence may take an average of 40 hours depending on the condition of the computer or digital device and the volume of data contained therein.
Regardless of the timeframe required, a thorough analysis of computer forensics is an indispensable component of an IINI investigation because digital evidence can significantly improve (or a lack of quality digital evidence can hinder) the prosecution of a cyber crime committed against a child. For example, by obtaining the system files residing in digital evidence, a Special Agent may use the forensic analysis to prove possession, receipt, production, transportation, and distribution of child pornography.68
Timeliness of Forensic Analysis of Digital Evidence in Child Exploitation Investigations
The MIOG of the FBI states that the “CART’s primary responsibility is to provide field office investigators who encounter computer-related evidence with reliable, comprehensive, and timely information and technical support.” However, the FBI does not have criteria regarding the timeframe within which a forensic examiner must assign and complete a request for services. According to DES officials, it is impractical to impose criteria on timeliness for all requests for service because the amount of digital evidence submitted for analysis varies from one request to another. One investigation may result in the seizure of a single computer, while another investigation may involve a subject with multiple computers. Even with two requests for forensic services of a comparable type and amount of digital evidence, the time required for analysis may vary based on the condition of the evidence seized and the scope of the request for forensic assistance.
The only DES criteria on timeliness that we identified in our review concerned the backlog of requests for services from CART. According to DES officials, CART defines a request for service to be in backlog status when one of the following two conditions is met:
- A lead examiner has not been assigned within 30 days of a request.
- The request was assigned to an examiner but the examination of the digital evidence has not been completed within 60 days of the requestor’s submission to CART.69
According to an FBI official, however, the 60-day period does not represent the timeframe for when the analysis of digital evidence must be completed, in part because, as described above, a significant step in the process involves interactions between forensic examiners and case investigators when reviewing data relevant to specific investigations. Instead, the definition of the backlog status of a service request is primarily intended as a tool for field managers to monitor, manage, and reprioritize forensic examinations.
Officials of the DES stated that it has implemented initiatives to foster cooperation between forensic examiners and Special Agents to facilitate the analysis process. However, the overall amount of digital evidence analyzed by the DES increased nearly 2,200 percent between FYs 2001 and 2007, from 115 terabytes to 2.57 petabytes.70 A contributing factor to the increasing workload of digital evidence is the tendency of collectors of child pornography to amass huge quantities of such materials, which has become worse in recent years as a result, in part, of the continual innovations in inexpensive storage devices for digital media. While the workload of the DES has increased dramatically, funding for the DES has decreased on an annual basis since FY 2004 from $18.2 million to $13.2 million in FY 2007. In terms of forensic analysis for child sexual exploitation investigations, the number of service requests from IINI from FYs 2005 to 2007 has remained relatively stable at about 2,400 service requests. However, the amount of digital evidence examined from these investigations in that same time period has increased by 38 percent, from 429 terabytes to 591 terabytes.
The following table illustrates for FYs 2005 through 2007 the number of IINI digital evidence service requests in backlog status at the fiscal year end.
BACKLOG OF DIGITAL EVIDENCE SERVICE REQUESTS
FOR IINI INVESTIGATIONS
FISCAL YEARS 2005 THROUGH 2007
| FISCAL YEAR | End of Fiscal Year Backlog of IINI Service Requests Not Yet Assigned or Inventoried |
|---|---|
| 2005 | 616 |
| 2006 | 527 |
| 2007 | 353 |
An IINI official stated that it has taken on average about 100 days from the date of the service request to the date the completed results are provided from the forensic examiners. Outside the FBI, representatives from the United States Attorney’s Offices also informed us that they have noted protracted processing time of forensic analysis of digital evidence from the FBI in child sexual exploitation cases.
We selected a sample of 38 cases closed between October 1, 2005, and Spring 2007 from the 5 FBI field offices that we visited, and we analyzed the amount of digital evidence collected for each case and the dates when service requests were received, assigned, and processed by DES. Of the 38 cases that we reviewed, 17 (45 percent) received forensic analysis of digital evidence and 4 of these 17 cases involved multiple examinations. Altogether, 22 examinations were conducted for these 17 cases.
We analyzed the dates when the CART field managers received the requests for forensic services and assigned them to a forensic examiner. According to DES data, these examinations were assigned, on average, within 20 days of receiving the service request. This was well within the 30‑day criteria on backlog, defined as the time period from when the CART managers receive a service request to when they assign that service request to an available examiner. For the 17 cases we reviewed, data from DES indicated that forensic analysis results were available for Special Agent review, on average, 9 days from the date when the service request was assigned to an examiner; the longest analysis in our sample took 90 days.71
The DES provided us with the national averages of all IINI-related forensic analysis of digital evidence performed by its Computer Analysis Response Teams and Regional Computer Forensic Laboratories from a database at these programs’ Intranet.72 These figures are shown in the following table. The assignment cycle represents the time frame from the date that a service request is received by the CART or Regional Computer Forensic Laboratories managers in the field or at FBI headquarters laboratories to the date that the request is assigned to a forensic examiner. The overall cycle represents the time from the date that the request is assigned to the forensic examiner to the date that the Special Agent is informed that the digital evidence is ready for review.
FBI DIGITAL EVIDENCE SECTION
NATIONAL AVERAGES FOR
ASSIGNMENT AND OVERALL CYCLES ON IINI CASES
| Fiscal Year | Assignment Cycle (in days) |
Overall Cycle (in days) |
|---|---|---|
| 2005 | 39 | 90 |
| 2006 | 35 | 65 |
| 2007 | 19 | 59 |
Despite an increasing volume of data being submitted for examination, the FBI improved its processing time related to cyber crimes against children in FYs 2005 through 2007. However, FBI officials in IINI and the DES acknowledged that the overall processing of digital evidence has in some instances taken unduly long periods of time. Interviews with IINI officials and data from DES indicate that forensic examinations of cyber crimes against children evidence take from 3 months to as long as 9 months to complete. Although we recognize that the processing of digital evidence may be complex, in our judgment taking 9 months for examiners to process and investigators to search through a case’s digital evidence is too long. To ensure timely processing of digital evidence, the DES should establish appropriate deadlines or benchmarks for completing the service requests.
Although we did not find evidence of forensic examinations and analysis taking over 9 months for the cases that we reviewed, we did find that at the end of FY 2007 CART examiners had a backlog of 353 service requests from IINI waiting either to be assigned or inventoried. While the backlog numbers kept by the FBI have decreased in the past 3 years, 353 service requests out of 2,429 in FY 2007 represent a significant backlog because the examination of the digital evidence can help the FBI locate children being exploited and expedite the process of prosecuting the subjects. The following table details the end-of-fiscal-year service requests that were in a backlog status from IINI in FY 2007, based on the four investigative categories of IINI and the two-part definitions of backlog of service requests of the DES.
END OF FY 2007 CART BACKLOG OF SERVICE REQUESTS FROM IINI
| IINI Investigative Category |
Service Requests that were Incomplete or Without Completed Exams |
Service Requests that were Unassigned |
Total |
|---|---|---|---|
| Groups and Enterprises | 54 | 27 | 81 |
| Online Enticement | 28 | 14 | 42 |
|
Producers |
119 | 34 | 153 |
|
Possessors |
52 | 25 | 77 |
| Totals | 253 | 100 | 353 |
IINI and the DES officials said they have worked closely to develop a solution to address the amount of time required to analyze the large quantities of digital evidence that often accompany investigations of online crimes against children. In March 2007, the FBI submitted to the Office of the Deputy Attorney General its Joint Proposed Revisions of Computer Forensic Examination and Cyber Protocols to Expedite the Review of Seized Digital Media in Child Exploitation and Obscenity Investigations (Joint Proposed Revision) for review. In this proposal, the FBI stated that it needs “significant additional personnel and resources” in coming years to keep up with an ever‑growing amount of digital evidence in criminal investigations. The Joint Proposed Revisions discussed a plan that included further enhancing technological tools used in previewing and processing digital evidence, hiring of 10 additional forensic examiners, and establishing 2 or more laboratories that would be devoted solely to the processing of digital evidence seized in cyber crimes against children.
On February 13, 2008, the Deputy Attorney General issued a memorandum to the FBI, the Criminal Division, the Executive Office for United States Attorneys, and United States Attorney Offices, which included both short- and long-term strategies on coping with the increasing volume of digital evidence from child sexual exploitation cases requiring forensic analysis. The short-term strategy endorsed the FBI’s plans to upgrade and expand its use of preview tools, hire additional forensic examiners, and establish new forensic laboratories dedicated to the processing of significant cases of child exploitation investigations.
Additionally, the short-term strategy also includes the construction of a new forensic laboratory in Linthicum, Maryland. This new laboratory will be devoted exclusively to working on high-priority cases of sexual exploitation of children. DES officials said they hope this new laboratory will help address the current backlog of unreviewed evidence in priority investigations.
The opening of a new laboratory partially addresses the FBI’s proposal that it submitted to the Office of the Deputy Attorney General, which requested two new forensic laboratories. Other endorsements by the Office of the Deputy Attorney General include a real-time tracking system being developed by the FBI that would track the processing of digital evidence from the time of seizure. However, there was no indication in the memorandum whether the DOJ would supplement the FBI’s budget to fund these enhancements.
The long-term strategy includes a permanent DOJ Computer Forensics Working Group that will seek to efficiently allocate resources to process the growing volumes of digital evidence. Composed of representatives from various DOJ components, including the FBI, the Computer Forensics Working Group is supposed to meet regularly and recommend “long-term prosecution and investigative strategies designed to maximize the efficient use of limited digital evidence forensic capabilities.”73 The Working Group also is supposed to recommend guidelines and performance measures for computer forensic examinations, including timeframe benchmarks for processing digital evidence.
DES officials cautioned that they believed that law enforcement would always be outpaced by fast technological changes that allow individuals to increase the amount of child sexual exploitation materials that is maintained in digital files. Specifically, DES officials believe that the amount of digital evidence seized in child sexual exploitation cases will continue to rise more quickly than law enforcement agencies’ ability to adequately cope with processing such evidence.
Mental Health of FBI Personnel
According to an ICAC manager who we interviewed, law enforcement personnel who are exposed on a regular basis to child pornography that is sexually explicit and possibly violent can suffer long‑term emotional consequences. A Supervisory Special Agent at an FBI field office we visited stated that the FBI may also be at risk as the employer of these individuals should an agent working these cases suffer trauma, a job-related breakdown or commit an illegal act as a result of exposure to images of child sexual exploitation. For these reasons, we reviewed the FBI’s efforts to address the mental health of individuals who must review child pornography as a part of their employment.
The FBI’s IINI Manual requires Special Agents to undergo psychological tests administered by the FBI’s Undercover Safeguard Unit (USU) to be certified to perform undercover investigations of cyber crimes against children. The USU assesses the psychological wellness and operational readiness of FBI personnel to engage in or continue to function in covert investigations.
One common example of undercover activity in cyber crimes against children investigations is for a Special Agent to pose as a minor in cyberspace to identify adults intending to exploit children sexually. Additionally, IINI undercover activities may involve infiltrating online groups that exploit children sexually as an investigative tool. USU psychological evaluations benefit both undercover employees and the FBI as an employer. Early detection of employees who may have a problem handling their undercover role or viewing child pornography can allow the FBI to take appropriate steps to ensure its investigations are not jeopardized or improperly handled and can also help the FBI ensure the mental health of its personnel.
Certified Undercover Special Agents
The USU administers an initial evaluation of Special Agents assigned to all undercover activities, including those related to investigating cyber crimes against children. The USU psychologist determines the psychological well‑being of the employee who must undertake undercover activities and determines the proper time interval for follow-up assessments during the remainder of the individual’s tenure in an undercover capacity.74
We reviewed evaluation data from the USU to determine whether Special Agents certified to conduct undercover investigations of cyber crimes against children had received the required follow-up assessments. Based on the July 2007 roster of the IINI, we found that 130 Special Agents, supervisors, and task force officers from the IINI Unit were certified undercover officers. We considered a psychological evaluation to be timely if it took place within the timeframe established by the FBI or no more than 1 month beyond that timeframe.75 The results of our review showed that, of the 99 undercover officers with assessment data at the USU, 68 were timely evaluated and 31 did not have timely evaluations.76 For those agents with untimely USU assessments, the delay until re-assessments were performed averaged 4.5 months and ranged from 1.5 to over 10 months. We were informed that the 10-month delay was due to the demand for the Special Agent’s time on a particular case.
We shared the results of our testing with IINI management and were informed that those employees whose evaluations were overdue would be notified to ensure that their follow-up assessments were promptly scheduled. In July 2008, we were informed by IINI management that the Special Agent whose assessment was over 10 months late had been re‑evaluated in March 2008 as a result of our finding. Although IINI management informed us that controls are in place to ensure that certified undercover officers receive the required examinations, we concluded that these controls needed improvement because approximately one-third of its undercover agents had not received timely assessments. Without timely assessments of IINI undercover employees by the USU, the FBI management would not have the necessary assurance that these individuals were mentally fit in conducting sensitive operations on cyber crimes against children.
Other FBI Employees
We identified two additional categories of FBI personnel who are not certified undercover officers but whose duties expose them to child pornography and who are not required to submit to psychological assessments: (1) Special Agents who investigate cyber crimes against children but not in an undercover capacity, and (2) forensic examiners who review digital evidence of cyber crimes against children. USU officials informed us that they would not refuse to provide a psychological assessment if requested by an employee. However, USU officials emphasized that the USU’s mission focuses on assessing undercover employees and it relies on FBI management to refer non-undercover employees on an as-needed basis. For instance, we learned that forensic examiners at the Los Angeles Field Office had received mental health screening from the USU because their supervisor requested the screening.
The DOJ recognizes the mental strain on individuals involved in the investigation of child pornography.77 In its February 2007 revision of the ICAC Task Force Operational and Investigative Standards, the DOJ notes that:
[g]iven the graphic nature of evidence routinely encountered in ICAC related cases, the mental health of investigators working such cases is a great concern. Task force supervisors at all levels are encouraged to make reasonable efforts to ensure that all assigned officers remain fit for duty.
An analysis by the FBI’s BAU-3 of the child pornography seized in FBI investigations determined that most “collections also contain multiple paraphilic themes, including bestiality, bondage, sadism, urophilia, etc.” Similarly, a 2005 study by NCMEC found that 21 percent of the images in a sample of 429 cases “had child pornography depicting violence such as bondage, rape, or torture. Most of these... images [were] of children who were gagged, bound, blindfolded, or otherwise enduring sadistic sex.”78
Considering the content of violent or sexual exploitative images of children and the mental and emotional risk it poses to FBI employees who are exposed to these images, we believe the FBI should consider broadening USU’s evaluation services to more than Special Agents working undercover assignments. Therefore, we believe the FBI should establish guidelines for providing USU-approved psychological assessments or counseling to all personnel who have had or will have exposure to child sexual exploitation material.79
FBI Research on the Online Sexual Exploitation of Children
Research on the online sexual exploitation of children is critical to an effective response to cyber crimes against children because of rapid advances in technology that provide offenders with new tools for committing such crimes. Results and insights gained through research can be refined into innovative investigative techniques and applied to improve law enforcement’s effectiveness against criminals who exploit children. Consequently, the goals and objectives of the FBI’s Cyber Crime Section for 2007 include the expansion of the “IINI’s intelligence collection and analysis capability.”
We found that the FBI’s BAU-3 and Intelligence Analysts have conducted research projects on the online sexual exploitation of children. Since 2002 the BAU‑3 has been conducting an ongoing research project on cyber crimes against children by reviewing the details of completed investigations. Using a 60-question protocol, this research project examines closed investigations conducted by IINI to address topics such as characteristics of offenders and the content of collections of child exploitation images, including the age and gender of victims. The BAU-3 has examined about 200 cases as part of this project. Although this research project is not yet completed, the BAU-3 has already issued an interim reference guide based on analyses to date and has provided training to Special Agents in courses offered by IINI.
Beyond the BAU‑3’s efforts, the FBI has also expanded its research through the use of its Intelligence Analysts. The FBI has increasingly required its Intelligence Analysts to focus on “strategic” intelligence assignments, which allow the FBI to identify patterns and forecast emerging trends in crime, instead of the more narrowly focused “tactical” assignments that focus on specific investigations. During our audit, we identified two Intelligence Analysts who perform research aimed at gathering strategic intelligence that supports the FBI’s efforts to combat cyber crimes against children.
At the FBI’s Los Angeles Field Office, an Intelligence Analyst researches current literature on digital technology to assess whether any new tools could be used to commit cyber crimes against children. Likewise, at the FBI’s San Francisco Field Office an Intelligence Analyst was conducting research related to online exploitation of children. In one assignment, the Intelligence Analyst assumed an undercover identity and visited online cyber locations frequented by adults who exploited children. The goal of this assignment was to learn behavior patterns of offenders that would assist the Special Agents in their investigations of cyber crimes against children.
This type of research should assist the FBI by allowing it to become better informed of crime characteristics, perpetrators’ psychology and patterns, as well as emerging technological trends.
Safety issues for minors in online activities constitute a critical aspect of any efforts to combat cyber crimes against children. The FBI’s 2004 to 2009 Strategic Plan called for the Cyber programs to “[e]xpand efforts to educate children and parents about Internet dangers.” Likewise, the IINI Manual states that the FBI’s cyber crimes against children operations should promote “community outreach programs regarding online safety as it relates to children.”
We found in the five FBI field offices we visited that the FBI had developed, to varying degrees, safety programs to address dangers posed to minors who engage in online activities. While the FBI offices in San Francisco, Los Angeles, and Boston did not have formal online safety programs, FBI officials said they provided presentations when requested by schools or community groups on the dangers encountered by minors during cyber activities. The frequency of such outreach activities ranged from around four a year by a Special Agent at the San Francisco Field Office to about one to four requests per month at the Los Angeles Field Office.
The other two field offices we visited, St. Louis and Miami, adopted more frequent and formalized approaches to online safety issues for minors. In St. Louis, the Cyber Squad participated in a local non-profit group specifically devoted to helping minors recognize the dangers of unsafe Internet activities. In Miami, the crimes against children squad formed a partnership with Nova Southeastern University in an initiative entitled “Safe Online Surfing.” According to the Special Agent responsible for serving as the FBI point of contact for this initiative, more than 10,000 children participated in Safe Online Surfing since its inception in 2005. The Special Agent also estimated that within that same period, he participated in about 20 presentations where he discussed with children safety issues in online activities. In addition to these presentations, the FBI’s Miami Field Office assists in developing interactive web-based activities designed to teach children about the dangers of unsafe uses of the Internet.
The five FBI field offices that we visited recognized the value of community outreach in educating the public on the safety concerns of the Internet. Field offices in Boston, Los Angeles, and San Francisco respond to requests for presentations on Internet safety. However, the partnership between the Miami Field Office and a private program resulted in a larger number of children being informed on this critical issue. We recommend that the FBI field offices consider more formalized approaches to community outreach to minors concerning online safety issues, similar to the approaches taken in St. Louis and Miami.
Cyberspace has become the primary medium for the distribution of sexually exploitative images of children. To address this situation, the FBI established its IINI program, which, according to the FBI, has opened over 20,000 investigations resulting in the conviction of almost 7,000 persons for online sexual exploitation of children since its creation in 1995. In FYs 2006 and 2007 the FBI’s timekeeping records indicated that it focused 70 percent of its IINI Special Agent personnel on investigating its top priorities – criminal enterprises sexually exploiting children online and producers of online child pornography.
Online child sexual exploitation is a borderless crime, requiring coordination among federal, state, local, and foreign agencies. The five FBI field offices that we visited generally coordinated with other state and local law enforcement agencies, particularly through the Attorney General’s Project Safe Childhood initiative. In the international arena, the FBI created an IINI International Task Force to improve the partnership between foreign counterparts in online child sexual exploitation investigations.
The FBI has supplemented these efforts with behavioral research and intelligence assessments aimed at identifying common characteristics in crimes of child exploitation and of the perpetrators of those crimes. These efforts are designed to provide law enforcement agents with insights to enhance their investigations.
However, the FBI could improve certain aspects of its efforts to combat online child sexual exploitation. We found that the FBI is experiencing long processing times for the forensic analysis of digital evidence in some cyber crimes against children cases. Specifically, the FBI reported that it has taken up to 9 months for the FBI’s forensic examiners, working with case investigators, to complete the examination of digital evidence. Such delays can prevent the FBI from timely identifying children being sexually exploited and prosecuting the perpetrators. We recommend that the FBI continue to explore strategies that would relieve backlog of digital evidence from IINI cases awaiting forensic examination and analysis.
The FBI’s Undercover Safeguard Unit (USU) is a headquarters component dedicated to assessing the psychological well-being of Special Agents who work in an undercover capacity, including those working undercover in cyberspace during IINI investigations. However, we found that certified personnel working in this undercover capacity were not receiving psychological re-assessments in a timely manner as required by FBI policy. Additionally, we found personnel not working undercover on IINI investigations but who were exposed routinely to sexually exploitative images of children, such as other Special Agents and forensic examiners, were not screened. Given the content of these images, we believe the FBI should establish guidelines for providing USU-approved psychological assessments or counseling for non-undercover employees who have had or will have exposure to child sexual exploitation material.
Finally, the FBI has policies that encourage the IINI to promote community outreach activities in educating children about the dangers of the Internet as a way to protect them from exploitation. To varying degrees, the five FBI field offices we visited have established outreach programs aimed at alerting young persons of the dangers they may encounter on the Internet. We believe that the FBI should encourage its field offices to explore the possibility of establishing partnership with programs like those instituted in Miami and St. Louis to enhance their ability to promote community outreach.
We recommend the FBI:
- Enhance its interagency cooperation in Los Angeles with ICE and the ICAC task force.
- Continue to develop strategies for DES to reduce the backlog of digital evidence related to crimes against children cases requiring forensic analysis.
- Strengthen internal controls to ensure that IINI undercover employees receive timely mental health assessments from the USU.
- Establish guidelines for providing USU-approved psychological assessments or counseling for non-undercover personnel who have had or will have exposure to child sexual exploitation material.
- Consider implementing community outreach activities on Internet safety for children, similar to the cooperative model with external organizations at the Miami and St. Louis field offices.
Footnotes
- 18 U.S.C. § 2256 (8).
- These statistics include reports sent to law enforcement where the child pornography was facilitated by commonly used electronic-sharing technologies and do not represent the full universe of CyberTipline® reports of child pornography.
- Literature on crimes against children is voluminous. The following are some of the documents we examined as part of this review: Sexual Exploitation of Children Over the Internet, Committee on Energy and Commerce, U.S. House of Representatives, 109th Congress, January 2007; Project Safe Childhood: Protecting Children from Online Exploitation and Abuse, May 2006; and Child-Pornography Possessors Arrested in Internet-Related Crimes, Copyright © 2005, NCMEC.
- Statistics on convictions include a small number of cases known as “pretrial diversion,” where the prosecutor and the defendant reach an agreement where the defendant pleads guilty and is committed to a sex offender treatment program instead of going to jail. According to FBI officials, charges are not dropped even after successful completion of the sex offender treatment program. There were 6 pretrial diversions in FY 2004, 12 in FY 2005, 5 in FY 2006, and 8 in FY 2007.
- Appendix VII lists the FBI’s overall investigative priorities.
- Enterprises that operate commercial child pornography websites are not necessarily involved in the production of the child pornography, but rather the distribution of pre-existing material.
- Due to rounding, percentage figures do not always equal 100.
- Data represented in this pie chart came from the FBI’s TURK system, which records the percentage of time devoted by Special Agents to various types of investigations. TURK then converts that information into Average On-Board (AOB) data. One AOB is the equivalent of one full-time agent working in a specific investigative area for one year. On average during FYs 2006 and 2007, out of 238 Special Agents, the equivalent of 86 full-time Special Agents worked on enterprise-level IINI investigations, 81 agents investigated producers of sexually exploitative images of children, and 72 agents worked cases related to online child sexual exploitation enticement and possession.
- Janis Wolak, Kimberly Mitchell, and David Finkelhor of the Crimes Against Children Research Center, University of New Hampshire, Internet Sex Crimes Against Minors: The Response of Law Enforcement (Alexandria, VA: National Center for Missing and Exploited Children, November 2003), ix-x, 13. According to its website, the Crimes Against Children Research Center of the University of New Hampshire “seeks to combat crimes committed against children by providing high-quality research, statistics, and program evaluation to the public, policymakers, law enforcement personnel, and other child welfare practitioners.”
- The ICAC Task Forces were created by the Office of Juvenile Justice and Delinquency Prevention (OJJDP) of the Office of Justice Programs (OJP) through the FY 1998 Justice Appropriations Act, Pub. Law No. 105-119.
- During our fieldwork we visited the following FBI field offices: San Francisco and Los Angeles, California; Miami, Florida; Boston, Massachusetts; and St. Louis, Missouri.
- We noted that although the SAFE team had members from local agencies such as the Los Angeles County Sheriff’s Department and California Highway Patrol, federal participation beyond the FBI was limited. There was one representative from the United States Postal Inspection Service, but none from the local ICAC task force or other federal agencies such as Immigration and Customs Enforcement.
- Europol, the European Police Office, is the European Union’s criminal intelligence agency. The 22 participating countries of the FBI’s ITF are: Thailand, the Netherlands, Norway, United Kingdom, Finland, Croatia, Canada, Germany, Latvia, New Zealand, Sweden, Fiji, Ukraine, Australia, the Philippines, Indonesia, Cyprus, Belarus, Chile, Panama, Iceland, and Brazil.
- The IINI’s ITF is located within IINI, where foreign members of the ITF work closely with IINI Special Agents.
- More than 450 images were identified showing the same victim.
- In 2003, The American Society of Crime Laboratory Directors (ASCLD) formally recognized digital evidence as a “scientific discipline.” Since then, any forensic laboratory formerly certified by the ASCLD must be reaccredited if that facility processes evidence in any of the following four sub-disciplines: audio, video, image, and computer forensics. The FBI’s Digital Evidence Laboratory was accredited on January 16, 2007, in all four of these sub-disciplines.
- The CART Unit, within the DES, administers the FBI digital evidence program by training, equipping, and testing the proficiency of computer forensic examiners. The CART Unit also established and enforces the digital evidence forensic protocols and procedures used by examiners. Except for approximately 45 examiners and specialty program managers who maintain digital evidence laboratories in Quantico, Virginia, and Linthicum, Maryland, the remaining examiners are deployed at locations across the country in FBI field offices and RCFLs. The total number of CART-certified personnel consists of approximately 54 percent professional support personnel and 46 percent sworn FBI Special Agents. While the CART Unit controls the processes applied by all CART-certified examiners, it does not control examination assignments of examiners in the field nor does it control their employee performance reviews. Those aspects are controlled by the local FBI field office management.
- Hash values can serve as a “fingerprint” of a digital file. According to the Scientific Working Groups on Digital Evidence and Imaging Technology, a hash value is “a numerical value used to substantiate the integrity of digital evidence and for inclusion or exclusion comparisons against known value sets.” During a digital forensic examination, the forensic examiner uses a hash value primarily to establish that: (1) a duplicate set of data created during the forensic process is an accurate representation of the source set of data; and (2) the duplicate set of data has not been altered from the source set of data during the examination process.
- Some of the system files used by the Windows operating system cannot be easily altered or tampered with by users and may assist forensic examiners in obtaining an account of activities of the subject on the computer, such as websites visited and files created and/or viewed. This holds true even when the subject has deleted files from the computer, because deleted files generally remain in the unallocated portions of the hard drive and may be recovered by a forensic examiner.
- Completed examination of digital evidence includes the completion of all 5 steps in the process of forensic analysis. Forensic analysis includes: (1) preserving, imaging, and authenticating the evidence, (2) processing the imaged evidence, (3) presenting the processed data for the investigator’s review, (4) forensically retrieving of information tagged by the investigator as relevant to the investigation, and (5) preparing a report of the forensic analysis.
- One terabyte equals 1,024 gigabytes. One petabyte equals 1,024 terabytes. According to the FBI, as printed text one petabyte equals approximately 100 billion reams of paper.
- This overall cycle covers the completion of the five sequenced events described above.
- The DES has informed us that it is working to develop and deploy a different business process management system that it believes will be capable of providing real-time or nearly real‑time information on digital evidence forensic examinations.
- See Craig Morford, Acting Deputy Attorney General, memorandum to United States Attorneys’ Offices, Executive Office for United States Attorneys, Criminal Division, and the FBI for FBI digital evidence, forensic examination, resources, and child exploitation investigations, February 13, 2008, 9.
- We noted that the intervals between assessments were from 6, 9, 12, and 24 months.
- In our judgment, it was reasonable to allow an extra month for completing the evaluations to allow for any scheduling issues that may arise.
- Of the 130 IINI certified undercover officers, the USU’s records showed that there was evidence of a USU evaluation or follow-up assessment for 99 officers. For the remaining 31 officers on the undercover roster that did not have a record of a USU evaluation or follow-up assessment, about half had their undercover assignments discontinued or they were transferred out of their IINI investigative duties before we conducted our fieldwork in Summer 2007.
- Outside of law enforcement, we noted that employees at NCMEC’s Child Victim Identification Program (CVIP) receive quarterly mental health evaluations. The CVIP “serves as the national clearinghouse for child-pornography cases across the country and the main point of contact to international agencies about child-pornography victims.”
- Janis Wolak, David Finkelhor, and Kimberly J. Mitchell, Child-Pornography Possessors Arrested in Internet-Related Crimes: Findings From the National Juvenile Online Victimization Study (Alexandria, Virginia: National Center for Missing and Exploited Children, 2005), xi and 5.
- According to the DES, it periodically informs its forensic examiners of the availability of psychological assessments and counseling, but it has made participation voluntary, unless managers recommend it for specific examiners.