I. DATA ACCURACY AND TIMELINESS
- Our prior audit in June 2005 found that the TSC was operating two vastly different versions of the TSDB and the TSC lacked sufficient internal controls to ensure the integrity of the databases, resulting in names excluded from the watchlist and inaccurate and incomplete records. In our current review, we found that the TSC was operating two versions of the TSDB in tandem and the TSC had not taken adequate steps to ensure that the content of the two databases was identical. Further, we found significant numbers of duplicate records. In addition, because of internal FBI watchlisting processes, we found that the FBI bypasses NCTC and the TSC and enters a nomination into a downstream screening system prior to submitting the nomination to NCTC. As a result, the TSC is unable to ensure that consistent, accurate, and complete terrorist information is disseminated to frontline screening agents in a timely manner. Moreover, the TSC had determined that the TSDB contained over 2,000 watchlist records that did not belong in the database. This TSC review also identified at least eight records that were missing from the downstream databases and were therefore not available to frontline screening agents. While we recognize that no process will be perfect, omissions of a terrorist identity, as well as the existence of inaccurate, incomplete, or outdated watchlist records can have significant ramifications. Our findings indicate that the TSC needs to further improve its controls over the TSDB to help ensure the integrity and effectiveness of the watchlist.
In concert with NCTC’s implementation of its Terrorist Identities Datamart Environment (TIDE) database, the TSC developed a web-based version of the TSDB called the Nomination Tracking Processor (TSDB NTP) in March 2005. As shown in Exhibit 2-1, the TSDB NTP facilitates the receipt of data from NCTC, provides direct connectivity to the NCIC VGTOF data system, and enables the initiation and monitoring of data quality assurance efforts of the TSC.30 However, the TSDB NTP system is unable to export watchlist data to most screening agencies or process expedited and domestic terrorist nominations into the TSDB. As a result, the TSC has retained a legacy version of the TSDB to accommodate these processes.31 These two versions of the TSDB are interconnected to help ensure that nominations are properly exported to downstream watchlist agencies.
EXHIBIT 2-1
TSDB Operating Environment
[Image Not Available Electronically]
Source: The Terrorist Screening Center
TSC officials stated that while this operating environment is not optimal, they needed to maintain the legacy version of the TSDB because the TSDB NTP is unable to process expedited nominations or connect electronically with all of the related downstream screening databases. With two versions of the TSDB, however, i t is critical that the TSC maintain strong controls to ensure that each name nominated for inclusion in the TSDB NTP is appropriately included in the legacy version and accurately marked for export to the relevant downstream supporting systems in a timely manner.
However, we determined that the TSC did not implement the necessary controls to ensure that both databases contained a complete and accurate version of the terrorist watchlist. Specifically, the NTP and legacy databases were not synchronized, which caused inconsistent record counts between the two systems. As a result, names were omitted from the downstream screening databases. In addition, we noted that records had been inappropriately maintained in the TSDB without any watchlist designation. These findings are discussed in detail below.
Inconsistent Record Counts
At the beginning of this audit, we were informed by the TSC Chief Information Officer (CIO) that the NTP and legacy versions of the TSDB were interconnected to help ensure that the watchlist was properly exported to frontline screening agencies. Therefore, the two databases should be identical in content and should contain the same number of records. However, on March 16, 2007, we found that the TSDB legacy database had 689,631 records while the NTP had 689,613 records – a difference of 18 records. Although the difference is a small portion of the universe of records, omitted records can result in a missed opportunity to identify a known or suspected terrorist.
We brought the record discrepancy to the attention of the TSC CIO, who said he was surprised to learn that the systems were not in balance. Upon further review, the CIO learned and reported to us that the IT staff at the TSC was aware that the record counts sometimes varied. Despite the increased risk created by continual transactions between the two databases as well as recent system modifications, the TSC IT staff did not appear to have examined the differences, researched a valid explanation for the discrepancies, or sought a correction for whatever condition was causing the record counts to be out of balance.
Through subsequent analysis, on March 26, 2007, the TSC determined that the record difference between the two databases had increased to 38 records – 5 records were missing from the TSDB legacy system while at the same time it contained an additional 33 records that were not in the TSDB NTP system. These omissions and inaccuracies resulted from problems in a number of different areas.
Records Missing from the TSDB Legacy Database
Because the TSDB legacy database facilitates the export of data to downstream screening databases, any information that is missing from the system is not made available to all appropriate law enforcement and intelligence officials for screening of persons against the watchlist. As a result of our review, the TSC identified five records that were missing from the TSDB legacy system, which caused the exported watchlist to be incomplete.
One record, nominated on December 22, 2006, was never transmitted from the TSDB NTP system. As a result, this known or suspected terrorist record was not watchlisted for over 3 months. TSC officials were unable to determine why the record was not sent. However, as a result of our review, the TSC subsequently added this record to the watchlist.
Three records nominated on March 5, 2007, were transmitted by the TSDB NTP system but were never imported into the TSDB legacy system. According to TSC officials, the import process for the file containing these records was interrupted. The individual processing the file should have received a notification that the process failed. However, because multiple files are processed each day, TSC officials could not readily identify who processed the file nor provide an explanation as to why corrective action had not been taken. The TSC CIO stated that as a result of our review, the TSC has taken corrective action by modifying the software so that if the transfer process is interrupted again and the user restarts the program, the application returns to the last successfully imported identity and restarts the process to ensure that no records are lost by the interruption.
On December 20, 2006, the NTP system appropriately processed a request for the deletion of one record. However, the record was not deleted from the TSDB legacy system at the same time. As a result, this name continued to be inappropriately exported to downstream screening databases for nearly 2 months. On February 6, 2007, the individual was re-nominated by NCTC through the TSDB NTP, resulting in the two systems being synchronized for this record. On February 21, 2007, the original request for deletion was inappropriately processed in the TSDB legacy system resulting in the name not being watchlisted for approximately 1 month until we brought it to the TSC’s attention in early March 2007.
TSC officials explained that earlier versions of the TSDB legacy database could not process multiple actions for a single record, such as both a modification and a deletion, within one daily import file. TSC officials also theorized that for this record it appears that the December 20, 2006, file contained both a modification and a deletion. Because the TSDB legacy system processed the modification first, the deletion did not process, remained within the queue, and was processed 2 months after it was submitted. TSC officials stated that they have modified the processing order of the queue to prevent this anomaly from occurring again.
Additional Records in the TSDB Legacy Database
As a result of our review, the TSC identified 33 additional records contained within the TSDB legacy system that were omitted from the TSDB NTP system. According to TSC officials, the errors associated with each of the 33 records resulted from deficient historical data and technological complications.32 TSC officials agreed that none of the records should have been included in either database. TSC officials stated that they have now ensured that these records have been submitted to the internal quality assurance unit for corrective action.
Inaccurate Display of Watchlist Designation
The State Department’s Consular Lookout and Support System (CLASS) is one of the downstream screening systems that receives watchlist information from the TSDB. CLASS consists of two modules – CLASS/Visa and CLASS/Passport, which are used for processing visa and passport applications. According to State Department policies, individuals who are designated as a U.S. citizen or a U.S. person are ineligible for inclusion in the CLASS/Visa module.33 Non-U.S. persons are eligible for inclusion in both CLASS/Visa and CLASS/Passport. Therefore, an individual’s TSDB record can be exported to CLASS/Visa, CLASS/Passport, or both data systems based upon their status as a non-U.S. person. The TSC has included these criteria in the TSDB legacy software to ensure that watchlist records are correctly nominated and exported to the appropriate CLASS module during the data transfer process.
TSC users viewing the TSDB NTP system see check boxes that clearly identify the downstream screening systems to which each record is disseminated. However, the series of check boxes includes only one CLASS box that does not delineate between CLASS/Visa and CLASS/Passport and has the generic label “CLASS.”
The TSC plans to correct the CLASS designation in the TSDB NTP system to appropriately reflect that U.S. persons are not eligible for export to CLASS/Visa. In addition, as part of its planned system upgrades, the TSC intends to modify the TSDB NTP to accommodate designations for both CLASS/Visa and CLASS/Passport. This will help ensure that once the TSC begins to use the NTP system to export watchlist records to the downstream databases, the appropriate records are sent to each of the CLASS modules and individuals are watchlisted in the correct systems.
Future of the TSDB
We were told by TSC officials that they intend to streamline the TSDB by incorporating the functionality of the legacy system into the TSDB NTP and eliminating the legacy version. To minimize the impact on operations, the TSC plans to implement the changes in an incremental and phased approach. TSC officials anticipate that the project will be completed by the end of calendar year 2007.
It is essential that the TSC maintain and distribute to frontline screening agents a complete subset of known or suspected terrorist identity information. Therefore, the TSC should work aggressively to implement its plan to consolidate the TSDB NTP and legacy systems. Further, we believe that for as long as the TSC must maintain its current operating environment, the TSC must closely monitor the content of each to ensure that the record counts agree and that all watchlist records are accounted for and disseminated as appropriate. As a result of our audit, the TSC CIO stated that he had implemented a policy whereby the contents of the two systems are reconciled manually on a daily basis.
Records Not Designated for Any Watchlisting
According to its governing MOU, the TSC is responsible for regularly reviewing the contents of the TSDB and promptly adjusting or deleting outdated information. During the course of our review, we were informed by TSC officials that in September 2006 they had identified 2,682 records that were not being exported to any downstream screening database. Working with NCTC, the TSC confirmed that 2,118 of these records did not belong in the TSDB and needed to be removed from the consolidated watchlist.34 TSC officials conducted a manual review of the remaining 564 records and determined that 8 had not been appropriately watchlisted and needed to be renominated to the TSDB.35
Despite being responsible for removing outdated or obsolete data from the TSDB, however, the TSC did not have a process for regularly reviewing the contents of the TSDB to ensure that the database does not include records that do not belong on the watchlist. TSC officials told us that they intend to begin performing a periodic review of the database to identify any records that are being stored in the TSDB that are not being exported to any downstream systems. We believe it is essential that the TSC regularly review the TSDB to ensure that all outdated information is removed, as well as to affirm that all records are appropriately watchlisted.
FBI Procedure for Processing Watchlist Data
The FBI’s Terrorist Review and Examination Unit (TREX) receives requests from FBI agents to include individuals with known or suspected ties to terrorism on the terrorist watchlist. These requests are provided on nomination forms, which are also used to modify previous submissions or remove records from the watchlist. Analysts at TREX review the nomination information for accuracy and completeness. Once verified, nomination forms for known or suspected domestic terrorists are electronically forwarded to the TSC where a TSC analyst manually enters the information into the TSDB. This information is electronically distributed to the downstream screening agency data systems, including the FBI VGTOF, part of the NCIC system.
By contrast, once the TREX analyst verifies an FBI-generated international terrorist nomination, the analyst enters the information into VGTOF directly and then submits the nomination form to NCTC. Following its review and vetting, the NCTC analyst manually enters the information into its database – TIDE – that in turn feeds the information to the TSDB. Because TREX has already entered the record into VGTOF, it is not necessary for the TSC to export the record it receives from TIDE to VGTOF. Therefore, these records are not exported from the TSDB to VGTOF.36 Because these VGTOF records will not receive electronic modifications or deletions from the TSDB, the TSC and TREX have agreed that TREX will be responsible for ensuring FBI-originated international watchlist records in VGTOF are accurate, complete, and current.
The FBI’s direct entry of international terrorist watchlist nomination data into a downstream screening database bypasses NCTC and the TSC and makes it difficult for these agencies to carry out their responsibilities related to watchlist nominations and records. In our opinion, this process does not comport with the nomination and data flow procedures outlined in the MOU and agreed to by the partner agencies, which requires agencies to provide directly to NCTC, rather than directly into a downstream database, information related to known or suspected international terrorists. Additionally, we believe the FBI’s practice is cumbersome for the TSC and creates unnecessary data errors, anomalies, and inconsistencies as described below.
To test for data accuracy and consistency, we reviewed a judgmental sample of 50 FBI-originated additions or modifications to the watchlist.37 We found that while the records for the domestic terrorist nominations were generally accurate, the international terrorist nominations were not. We identified 16 records with 28 instances in which the identifying information related to international terrorists was inconsistent between the nomination form, VGTOF, TIDE, TSDB, or other screening systems. According to TSC personnel, TREX analysts frequently augment the data on the nomination forms with information they glean from FBI case files and enter this additional information into the VGTOF system. However, this supplemental case information is not forwarded to NCTC and as a result the information is not included in TIDE, not sent to the TSDB, and not made available, if appropriate, to downstream screening systems. Further, because TREX enters the record into VGTOF before the addition of any other existing information from other government databases to which NCTC has access, this additional information is often not included in VGTOF. As a result, vital information on watchlist subjects is not being shared with all appropriate screening agencies.
In addition, we found that the FBI’s procedures for processing international terrorist watchlist nominations are cumbersome for the TSC and can inadvertently create an incomplete watchlist. The difference in procedures between the FBI’s and other agencies’ watchlist nominations requires TSC analysts to review every incoming international terrorist nomination and indicate within the record whether it is an FBI source record. If a terrorist watchlist record is improperly designated as an FBI source record, the subset of terrorist watchlist records in VGTOF will be incomplete because that record will not be exported to or modified within VGTOF. TSC staff told us that they were also concerned about this because, when reviewing nominations from NCTC, it is often difficult to distinguish between FBI source records and nominations received from other agencies. TSC staff stated that there was a period of time (possibly as long as a year) in which many records had been improperly designated as an FBI-originated record or not. In March 2007, the TSC and NCTC addressed this problem by developing a method to permit TSC analysts to more easily identify FBI source records.
In response to these concerns, FBI officials informed us that they had implemented nomination procedures to ensure that FBI international terrorist information was entered into VGTOF in the most efficient manner. Yet, our review of 70 FBI record transactions (50 nominations previously mentioned and 20 deletions) revealed that although the transactions were entered into VGTOF in a timely manner, the transactions were not incorporated in the TSDB in a timely fashion.38 Specifically, 18 of the 70 transactions took more than 5 days for TREX to process, with 1 transaction taking 35 days. In addition, we identified 2 instances in which TREX erroneously delivered nomination forms for domestic terrorists to NCTC that resulted in delays of 6 and 16 days, respectively.
Delays in including terrorist information in the consolidated database present a significant vulnerability to the integrity of the consolidated watchlist. Further, the FBI’s current practice of bypassing NCTC and the TSC and entering international terrorist-related data directly into VGTOF increases the likelihood that watchlist information within the TSDB, TIDE, VGTOF, and other downstream databases is inaccurate and incomplete. As a result, we recommend that the FBI, NCTC, and TSC work together to design a more consistent and reliable process by which FBI-originated international terrorist information is provided to NCTC for inclusion in TIDE and disseminated to the TSDB and downstream screening systems, including VGTOF.
As shown in Exhibit 2-2, the TIDE and TSDB systems store all information known about an individual in a single “identity” record using five core identifying fields, including [SENSITIVE INFORMATION REDACTED]. However, the downstream screening agency data systems do not store information at the identity level. Rather, the identity information is split into separate watchlist records to reflect unique combinations of the five core fields.
EXHIBIT 2-2
Record Overview
[SENSITIVE INFORMATION REDACTED]
Source: The Terrorist Screening Center
Multiple records containing the same unique combination of identifying information can increase the number of records that a call screener must review when researching a specific individual. In addition, when multiple records for a single identity exist, it is essential that identifying information and handling instructions be consistent. Otherwise, the screener may mistakenly rely on one record while a second, more complete or accurate record may be ignored. This can result in important information being missed. Further, inconsistent handling instructions may pose a safety risk for law enforcement officers.
In our June 2005 report, we identified 31 instances in which 5 core identifying fields were the same and recommended that the TSC implement corrective action to address the duplicate records and develop an ongoing process to review the TSDB for duplicate records.
In our current audit, we identified a significant increase in duplicated records – 2,533 repeated combinations in these 5 fields involving over 6,262 watchlist records. For example, one unique combination of the 5 core fields had 19 associated records.
In response to the apparent duplicates we identified, TSC officials explained that the duplicates were the result of multiple TIDE identity records for a single individual, system-generated duplicate records, and improperly processed expedited nominations. TSC officials stated that, while they did not have an ongoing process by which they reviewed the TSDB for duplicate records, as a result of our finding the TSC will review the TSDB on a weekly basis for duplicate records. The results will be forwarded to the TSC’s internal quality assurance unit for further review and action.
Multiple Identity Records for the Same Individual
Of the 2,533 instances in which the core identifying fields were the same, TSC stated that most were not necessarily duplicate records. Rather, because the records have different TIDE record numbers, the TSC was unable to independently determine whether these records were duplicates. TSC officials explained that NCTC has indicated to them that many of these occurrences are inherent to old data. For example, prior to the implementation of HSPD-6 in 2003, both the FBI and the State Department may have maintained information regarding a single terrorist identity. During the blending of all sources of international terrorist information, both records may have been included in the TIDE data system resulting in duplicated data. In addition, TSC officials explained that some terrorist information remained classified and, as a result, could not be linked to unclassified data.39 To ensure that the most complete subset of unclassified information was disseminated, NCTC created multiple identity records for some individually known or suspected terrorists. As a result, rather than the optimal one identity record with multiple watchlist records, some individuals have multiple identity records that contain multiple identical watchlist records.
Through additional data analysis of the duplicate records we identified, the TSC identified at least one instance in which both the FBI and another government agency nominated the same individual. Because both records pertain to the same individual, the identifying information and instructions for handling the subject should be consistent. However, we identified significant differences in the handling instructions and warnings for the individual. Specifically, one record indicated that the individual was “armed and dangerous with violent tendencies” and also had a valid federal arrest warrant. The other record did not contain this information. Moreover, our analysis of the instances in which the five identifying fields were the same indicates that at least 20 percent have some discrepancy in handling instruction, identifying information, or watchlist export designation. These descriptions and instructions are used by frontline law enforcement personnel to assess and determine the level of threat posed by the individual encountered and help to protect themselves and others. Therefore, it is essential that this information be accurate and consistently applied to all records related to one individual.
Because these multiple records occur in TIDE, the TSC believes the review of the 2,533 possible duplicates more appropriately falls to NCTC. In June 2006, NCTC implemented an Identity and Person Merge project. Through this project, NCTC intends to resolve the duplication of identity data across multiple TIDE identity record numbers. However, until the identity information is consolidated, NCTC analysts should apply new information for an existing individual to each TIDE identity record for the individual. Through this process, NCTC intends to ensure that users of TIDE do not miss information about an individual that is potentially relevant to their work because they viewed the “wrong” TIDE identity when conducting their analysis. NCTC and the TSC anticipate that NCTC initiatives will help to alleviate many of these multiple identity records. However, until corrected we believe that these multiple records can affect a screening agent’s ability to protect against terrorism and can also pose significant risks to the safety of frontline law enforcement officers.
System-Generated Duplicates
According to TSC officials, the TSDB should not contain multiple watchlist records for a single identity from TIDE with identical information in the five core identifying fields. We determined that the TSDB contained one TIDE identity with two associated watchlist records with duplicated identifying information. The TSC determined that these two records resulted from a nomination from NCTC in February 2005 in which the two records were either improperly included in the daily import file or an error occurred during the import process on that day. Based on our review, t he TSC submitted this record to its internal quality assurance unit, and the duplicate record was deleted.
Expedited Nominations
When the TSC is informed about an individual who poses an imminent threat, it creates an “expedited” watchlist record directly into the TSDB. The TSC then forwards all of the information gathered on the subject to NCTC or the FBI for subsequent creation of a record through the standard nomination process. Once the record is submitted through the standard processes, the original expedited record should be deleted. However, our review of the duplicate record issue identified three expedited records that had been improperly processed and not deleted from the TSDB after the record was submitted through the standard nomination process.
According to TSC officials, these duplicated records (the expedited and subsequent routine nomination) should contain identical information. Our analysis revealed two instances in which either an additional date of birth or passport number was missing. According to the TSC CIO, these three expedited nominations have been submitted to the TSC’s internal quality assurance unit for further review, and the duplicated records have been deleted.
Inclusion of Known Terrorists in the TSDB
We also performed limited testing on the TSDB to examine the completeness of the watchlist by determining if known terrorists were included in the consolidated database. We selected for our review a total of 49 names: 10 from NCTC, 4 from news media accounts, 17 from the FBI’s Most Wanted list, 16 from the State Department’s List of Terrorists under Executive Order 13224, and 2 from the Rewards for Justice website.40 We searched the TSDB for these 49 names, and found that each was recorded in the TSDB. TSC officials also said they regularly checked their database against names reported in the news, broadcast on television, or included on lists such as the FBI’s Most Wanted.
However, our review of the 49 known terrorist names also revealed that the handling instructions for individuals from the FBI’s Most Wanted list had significant discrepancies. Specifically, two VGTOF records indicated that the watchlist subjects were armed and dangerous, but the TSDB records did not reflect this handling instruction. In addition, we identified four records containing discrepancies in identifying information between TIDE and TSDB. As previously discussed, it is essential that the TSC ensure that individuals are properly and consistently recorded in the TSDB and downstream screening systems, so that appropriate actions are taken if the individual is encountered by a frontline screening agent.
It is critical that the TSC ensure that the TSDB contains comprehensive information and that each watchlist record is appropriately disseminated to downstream screening systems in a timely manner. While we recognize that no process will be perfect, the potential effect of omissions of a terrorist identity, or the existence of an inaccurate, incomplete, or obsolete watchlist record, requires the TSC and its partner agencies to take all available actions to minimize such errors.
Despite our identification in our June 2005 audit of deficiencies related to the TSC’s information technology management and overall database reliability, our current audit determined that the TSC has not yet implemented routine processes to ensure that the TSDB contained all proper watchlist nominations and did not contain duplicate data resulting from improperly processed records, system malfunctions, and historical data deficiencies. Moreover, despite being responsible for removing outdated or obsolete data from the TSDB, the TSC did not have a process for regularly reviewing and verifying the contents of the TSDB. We believe that it is essential that the TSC regularly review the TSDB to ensure that all obsolete and out-of-date information is removed. Finally, because of internal FBI watchlisting processes, the TSC cannot ensure that accurate and complete terrorist information has been disseminated to downstream screening systems in a timely manner.
We recommend that the TSC:
-
Implement its plan to consolidate the TSDB NTP and legacy databases in a timely manner. In the interim while the two systems coexist, the TSC should establish a formal procedure to regularly review the TSDB NTP and legacy databases to ensure that the information in these systems remains synchronized.
Develop procedures to regularly review and test the information contained in the TSDB to ensure the data is complete, accurate, and non-duplicative.
Modify the TSDB NTP to accommodate designations for both CLASS/Visa and CLASS/Passport. In addition, the TSC should review and correct the records identified in the TSDB NTP to appropriately reflect that U.S. persons are not eligible for export to CLASS/Visa.
Review and correct the records identified in the TSDB NTP to ensure that the IBIS handling instructions are appropriately applied.
Develop procedures to regularly review the information in the TSDB to ensure that outdated or obsolete data is removed in a timely manner.
We recommend that the FBI:
Working with the TSC, revise the watchlist nomination process to provide international terrorist nominations directly to NCTC for inclusion in TIDE, submission to the TSC, and dissemination to all downstream databases, including VGTOF.
Our review indicated that the TSC had the foundations of a sound quality assurance plan that will improve the accuracy of the TSDB. The TSC is also continuing its efforts to perform a record-by-record review of the TSDB. However, we are concerned the TSC has not instituted adequate internal controls to ensure that its quality control initiatives are properly implemented. In addition, the TSC’s quality assurance efforts have been hampered by the growth in workload as the size of the watchlist increases.
To test the quality assurance plan, we reviewed 120 TSDB records that had been through the TSC’s quality assurance process in FYs 2006 and 2007 and identified several instances in which the individual was not appropriately watchlisted, as well as inconsistencies between the TSDB record and other available information. These inconsistencies make it more difficult for screening agents to determine if encountered individuals are on the watchlist.
Overview of the TSC’s Quality Assurance Process
In our June 2005 audit report, we identified weaknesses in the completeness and accuracy of the TSDB. During the TSC’s earliest days, it had 12 staff assigned responsibility for nominations and data integrity tasks, including one staff member that was dedicated solely to quality assurance matters. During our initial audit, TSC management acknowledged that the organization needed to focus more attention on ensuring the quality of the watchlist. We recommended that the TSC regularly review and test the information contained in the TSDB to ensure data is complete, accurate, and non-duplicative. We also recommended that the TSC coordinate with participating agencies and establish procedures to identify and resolve missing and conflicting record information.
In response to our recommendations, the TSC increased its quality assurance efforts and implemented a data quality improvement plan that detailed the TSC’s intent to conduct a record-by-record review of the TSDB. As of March 2007, the TSC had 34 staff on-board in its Nominations and Data Integrity Unit (NDIU), which is responsible for performing or overseeing all of the TSC’s activities related to ensuring the quality and accuracy of the watchlist, including:41
Reviewing incoming watchlist data (referred to as the single review queue).
Performing reviews of historical records following an encounter where the TSC identifies a potential discrepancy in watchlist records.
Conducting special quality assurance projects, such as performing a targeted review of the No Fly list or individuals with particular handling codes.
Single Review Queue
Implemented in March 2006, the single review queue is a feature of the TSDB that segregates the incoming data feed from NCTC so that quality assurance analysts can test each record before releasing that record for inclusion in the TSDB. Prior to the implementation of the single review queue, each watchlist addition or modification the TSC received underwent numerous, separate reviews by individual subject matter experts (persons who were knowledgeable about the requirements of the specific databases used by various screening agencies). In implementing the single review queue, the TSC sought to make the nomination acceptance and review process more efficient. The single review queue was designed to have individual analysts in the NDIU be responsible for guiding individual records through the process of loading the information into the TSDB. The single review queue begins with the use of a computer program that analyzes incoming records against more than 45 business rules.42 A business rule is an automated information technology function in which the record is analyzed for specific deficiencies and compliance with criteria.
Once the business rules have been applied to all of the records received, the records are routed to the NDIU for manual review. Although t he TSC has drafted a standard operating procedure (SOP) describing the single review queue process, it does not detail how NDIU analysts should conduct this manual record review. We observed NDIU analysts reviewing records in the single review queue and found that, in general, the review included: (1) determining whether the person met the criteria for inclusion in the TSDB (i.e., nexus to terrorism and quantity of identifying information); (2) confirming the supporting downstream screening systems to which the record should be exported; (3) resolving any issues identified during the execution of the business rules; and (4) comparing information contained in watchlist nominations, such as [SENSITIVE INFORMATION REDACTED], to source documents and source databases. The NDIU has seven individuals serving as subject matter experts who are consulted when NDIU analysts are unable to resolve all issues related to watchlist nominations prior to these nominations being sent to downstream screening databases. Generally, each record is reviewed by fewer persons than before the implementation of the single review queue. As of March 2007, 10 of the 34 staff members in the NDIU were dedicated to the single review queue.
Encounter-Driven Quality Assurance Reviews
In addition to data integrity work that is performed when new or modified data is processed through the single review queue, the NDIU receives referrals from the TSC Call Center for data checks on specific TSDB records. If a call center operator identifies a potential discrepancy in a watchlist record or obtains additional data relevant to a watchlist subject, the operator alerts the NDIU to perform a quality assurance review of the record. Generally, this occurs following a frontline screening agency’s encounter with a watchlist subject.
In April 2005, TSC management began requiring call center operators to perform limited data quality tests while handling encounters. Because the operators have access to all of the databases that interact with the TSDB, they were in a position to point out inconsistencies in the information contained in the records on specific individuals in the various databases. This process was modified slightly in November 2006 when the TSDB was upgraded to incorporate quality assurance activities. As a result of the upgrade, individual watchlist records in the TSDB now contain a record (referred to as a QA ticket) in which TSC staff can record all quality assurance work that has been performed on that record.43 With the upgrade, call center screeners were instructed to create a QA ticket in the TSDB for each positive screening encounter for which they identified any erroneous or inconsistent information in the database records.44 In addition, the call screeners were told to create a QA ticket if they obtained new information that should be added to the watchlist records.45
When a call center operator prepares a QA ticket, the TSDB electronically routes the QA ticket to the NDIU for further action. An encounter-driven QA ticket indicates that the encounter revealed that information needs to be added or modified, or it will indicate that a call screener identified a discrepancy with the completeness and accuracy of the records. Upon receipt of QA tickets, dedicated NDIU staff review the information from the call center screener and perform a full quality assurance review of all affected records. The QA ticket is closed when all necessary changes have been communicated to the source agencies and fed back into the TSDB, which then updates the downstream screening databases. As of March 2007, the NDIU had 9 individuals dedicated to responding to QA tickets.46
Special Quality Assurance Projects
The TSC also examines historical TSDB records for accuracy and completeness through targeted reviews of specific subsets of the watchlist records. Examples of special projects that the TSC has conducted include a review of TSDB records for individuals on the No Fly list and individuals with particular handling codes. As of March 2007, the TSC assigned 8 of the 34 NDIU staff to these kinds of special projects.
OIG Analysis of TSC Quality Assurance Efforts
To examine the TSC’s efforts to ensure the quality of the information in the TSDB, we examined the TSC’s review of records in the single review queue and its review of encounters and special projects. In total, we examined 156 TSDB records. Of these 156 records, 36 involved a request for deletion. We determined that each of these records had been appropriately deleted from the consolidated watchlist. Using the remaining sample of 120 records, we performed tests to determine if the watchlist records were accurate. We found that, in general, the TSC’s actions to review records as part of a targeted special project successfully ensured the quality of the data, and we identified virtually no errors in the 15 records we tested in connection with special project reviews. In contrast, our examination of 105 records subjected to the single review queue or post-encounter quality assurance reviews revealed that 38 percent of these tested records continued to contain errors or inconsistencies that were not identified through the TSC’s quality assurance efforts. Our results are discussed in detail below.
Review of TSC No Fly List Special Project
The first major subset of TSDB records that the TSC began reviewing as a special project was the Transportation Security Administration (TSA) No Fly watchlist records. The No Fly list includes individuals who, in general, are considered a threat to civil aviation and should be prevented from boarding commercial aircraft.47
To assist the TSC in its review of the No Fly list, the DHS temporarily assigned 10 federal air marshals to the TSC. The process included a review of the available information for each individual listed on the No Fly list and a determination of whether the individual should remain on the No Fly list. In addition to reviewing each entry on the No Fly list, the TSC performed a concomitant quality assurance review of all information contained in the TSDB’s records for individuals on the No Fly list. As a result, all of the TSDB’s records associated with individuals who were on the No Fly list underwent a comprehensive quality assurance review.
When the TSC began its review in July 2006, the No Fly list contained 71,872 records. As a result of the review, the TSC identified 22,412 records for removal from the No Fly list and placement on the TSA’s Selectee list.48 For another 5,086 records, the TSC determined that the individual did not require inclusion on either the No Fly or Selectee list. The resulting No Fly list changes the TSC identified are displayed in Exhibit 3-1. As of January 31, 2007, the TSC had determined that the No Fly list should contain 34,230 records.49
EXHIBIT 3-1
Results of TSC Review of No Fly List
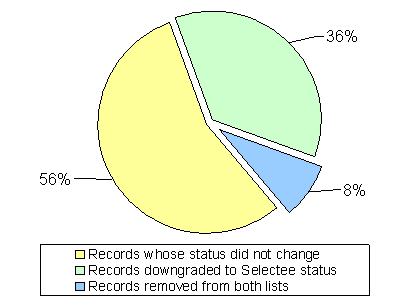
Source: The Terrorist Screening Center Nominations and Data Integrity Unit
We reviewed a sample of 15 TSDB records that had undergone a quality assurance review as part of the TSC’s review of the No Fly list. We did not find any data inaccuracies or inconsistencies in the records we reviewed. Each record’s basic information [SENSITIVE INFORMATION REDACTED] were shown consistently in all of the affected databases, and each record remained the same or was downgraded from the No Fly list in accordance with the final recommendation from the NDIU.
We did, however, identify an issue with the implementation of the status changes that the TSC identified during its review of the No Fly list. TSC officials told us that although the No Fly records were reviewed at the TSC, the status changes for known or suspected international terrorists could not be reflected in the TSDB until the changes were processed in TIDE at NCTC. The correct watchlisting status could then be uploaded from TIDE to the TSDB during the normal daily data feed. In turn, the TSC would export the No Fly and Selectee lists to the TSA for dissemination to the airlines on a daily basis.
According to TSC officials, NCTC and the airlines told the TSC that they could not effectuate all of the 27,498 changes (22,412 downgrades from the No Fly to the Selectee list plus 5,086 removals from the No Fly list) at once due to resource limitations. TSC management had previously decided not to send any record changes to NCTC until this special project was nearing completion. TSC management explained that TSC analysts needed the time to complete their quality assurance checks for each individual, particularly those with multiple TSDB records. The first changes were sent to NCTC on January 19, 2007. We were told that NCTC and the airlines could only process between 500 and 1,000 record changes a day. As a result, the TSC agreed to limit the number of changes it provided to NCTC and the airlines each day.
This piecemeal approach to implementing the changes in all of the databases meant that the status of many individuals was incorrectly shown on the TSA’s No Fly and Selectee lists for a period of time.50 According to TSC officials, all of the changes had been passed back to NCTC as of March 21, 2007. However, as of May 31, 2007, the TSC and NCTC were in disagreement about the proper No Fly-list status of 108 records.
Review of Routine Quality Assurance Matters
Unlike our review of the No Fly list special project, our examination of records passed through other TSC quality assurance processes revealed that the reviewed records were still likely to contain errors or inconsistencies. We selected a judgmental sample of 105 new and historical TSDB records that had undergone the single review queue or encounter-driven quality assurance processes.51 We examined the records to ensure that each record was exported to the appropriate screening databases. Additionally, we reviewed the records to determine if basic information [SENSITIVE INFORMATION REDACTED] was shown consistently in all of the affected databases.
Watchlist Designation and Handling Code Errors
Our review revealed that 7 of the 105 TSDB records examined were not being exported to all appropriate downstream watchlists. Specifically, three records were not exported to CLASS Visa. Moreover, these three records and an additional three records were not exported to [SENSITIVE INFORMATION REDACTED].52 Additionally, one record was not properly exported to the Interagency Border Inspection System (IBIS).
We discussed these records with NDIU officials who agreed with our findings. As a result of the TSC’s failure to export the four records to IBIS or CLASS Visa, which are used by U.S. screening agencies, the watchlisted individuals could be issued a U.S. visa erroneously or inappropriately allowed to enter the United States. The TSC’s failure to export the six records to [SENSITIVE INFORMATION REDACTED] can prevent U.S. allies from identifying known or suspected terrorists and sharing additional intelligence.
Our review also revealed that in two instances the TSDB records did not correctly indicate how the record would be seen within the IBIS system. When records are exported from the TSDB to the IBIS system, watchlist records can be identified with a special, less-intrusive handling code, as described earlier. We identified two TSDB records that were exported to IBIS with the special handling designation but should not be because the subjects were considered armed and dangerous or were not deemed a U.S. person. In addition to incorrect IBIS handling designations, an additional three records contained improper VGTOF handling codes. As discussed earlier, VGTOF handling codes instruct law enforcement officers how to properly handle an encounter with a watchlist subject. Incorrect watchlist designations and handling codes can place frontline screeners at increased risk.
Inconsistent or Incomplete Watchlist Records
Our review of the 105 TSDB records submitted to the TSC’s single review queue or encounter-driven quality assurance examinations also revealed that 35 TS DB records and the source or downstream records contained inconsistent identifying information in one or more data fields. In total, we identified 54 instances of inconsistent information. Our results are displayed in Exhibit 3-2:
| EXHIBIT 3-2 TSDB Record Inconsistencies |
|
|---|---|
| TSDB Record Field | Inconsistencies53 |
[SENSITIVE INFORMATION REDACTED] |
|
| TOTAL | 54 |
During our review, it became apparent that both the TSC’s quality assurance efforts and our reviews of watchlist records identified errors and inconsistencies in incoming records from the source agencies – NCTC and the FBI. We discussed the watchlist nomination process with NCTC and FBI officials, and both agency representatives stated that records are reviewed for accuracy, completeness, and consistency before the records are forwarded to the TSC. However, these efforts are failing to identify a significant number of deficiencies in the nominated records. The TSC’s quality assurance efforts, therefore, are hampered by the inaccurate and incomplete source material.
However, inconsistent records can confuse or delay TSC Call Center operators in their efforts to determine if encountered individuals are a positive match for watchlisted known or suspected terrorists. Further, inconsistent information among databases involved in terrorism screening indicates that at least one record may be incorrect. Incorrect records can also misinform frontline screening agents and contribute to the misidentification and delay of an innocent person or the inappropriate release or admittance of a dangerous individual.
Quality Assurance Management and Oversight
In general, we believe the actions the TSC has taken to improve quality assurance since our last audit are positive steps. We also recognize that it is impossible to completely eliminate the potential for errors. However, we identified inaccuracies in the TSDB that persisted even after undergoing the quality assurance process. This underscores the need for additional actions to ensure that the TSDB is a reliable source of information about known or suspected terrorists. Specifically, as described below, we believe that the TSC should: (1) work with the participating agencies to improve coordination related to quality assurance work, including establishing areas of responsibility and timeframes for following up on quality assurance matters; (2) develop a comprehensive standard operating procedure for quality assurance matters; (3) regularly review the NDIU’s quality assurance work; (4) develop a reliable and secure method for tracking quality assurance matters that involve classified correspondence; and (5) develop quality assurance benchmarks to monitor the TSC’s progress in conducting a record-by-record review of the TSDB.
Coordinating with Participating Agencies
According to TSC personnel, NDIU analysts should follow up on all quality assurance matters every 30 days. However, the TSC does not have a mechanism such as a standardized report or digital dashboard that catalogs all outstanding quality assurance matters.54 As a result, NDIU analysts are not prompted to follow up on long-outstanding quality assurance matters for which the TSC is waiting for a response from another agency, such as NCTC. Rather, it is up to each individual analyst to take follow-up action.
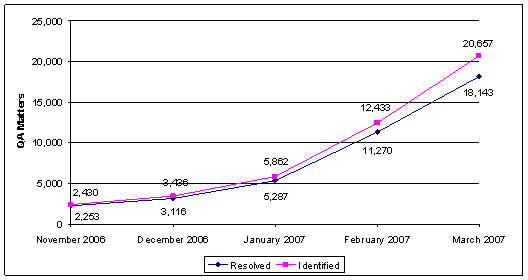
We examined a sample of 51 quality assurance matters opened between February 2006 and February 2007 and found that the matters were open from 0 days (the matter was closed the same day as it was opened) to 329 days. On average, quality assurance matters in our sample were open for 80 days. We also obtained TSC data related to the number of quality assurance matters identified and resolved between November 2006 and March 2007.55 This data shows that the TSC is identifying incomplete or inaccurate information in TSDB records faster than the matters are being resolved.
EXHIBIT 3-3
Cumulative Growth in Quality Assurance Matters
Source: The Terrorist Screening Center
Exhibit 3-3 shows that the cumulative difference between quality assurance matters identified and addressed has increased from 177 in November 2006 to 2,514 in March 2007. A significant portion of the increase in quality assurance matters processed by the TSC resulted from its implementation of its No Fly special project in January 2007. However, the TSC is regularly identifying errors or concerns with known or suspected terrorist records. To resolve inaccuracies and inconsistencies in watchlist records, the TSC usually must involve the source agencies – NCTC and the FBI. TSC officials acknowledged that the TSC and the participating agencies have not established timeframes for the resolution of quality assurance matters.
We believe that the TSC needs to work more closely with watchlisting agencies to better coordinate quality assurance efforts. This includes setting a standard for the timeliness of response to quality assurance matters, as well as delineating the roles and responsibilities of the various agencies involved. To improve the overall quality of the watchlist, the TSC needs the source agencies to provide records that are accurate, complete, and consistent, and to respond to quality assurance matters within a reasonable time. Without such an agreement, the TSC must expend additional effort to resolve errors that should have been identified earlier in the nomination process and continue to remind watchlist agencies about individual quality assurance matters.
Further, the delayed closure of quality assurance matters directly affects the accuracy of the consolidated watchlist database because records can contain inaccurate and incomplete information for extended periods of time while the matter is being resolved. Therefore, in concert with the development of established timeframes for resolving quality assurance matters, we recommend that the TSC develop a tickler system or aging schedule for its quality assurance work.
Standard Quality Assurance Procedures
During our audit, we personally observed NDIU analysts conducting quality assurance reviews of watchlist records. We noted that the analysts’ method of performing their reviews was not always consistent. For example, some analysts inspected all of the documents supporting a TSDB record, while other analysts relied solely upon summary information. We also found that the analysts were not documenting their quality assurance work consistently. The TSC has an SOP for its quality assurance efforts which was last revised on August 16, 2005. The document did not provide complete guidance to the analysts on the processing of quality assurance matters. Further, this SOP informs the analysts to review the record, but does not detail what fields, supporting information, and other aspects of the record the analysts should be verifying and comparing. In addition, these procedures do not instruct the analysts on the necessary actions to take when inaccurate or incomplete information is identified. Moreover, this protocol does not mention the existence of special projects within the TSC’s quality assurance efforts. We believe that the TSC should develop a detailed, comprehensive quality assurance SOP to better guide the NDIU analysts through all aspects of their work.
NDIU Analyst Oversight
The TSC provides only a few days of training to its quality assurance analysts in the NDIU. Following the completion of that training, the analysts begin working independently and no additional routine training or refresher courses are required. However, staff meetings are held on an ad-hoc basis to discuss specific issues that have been encountered. The TSC does not have a mechanism for regularly spot-checking the work of its quality assurance analysts to help ensure that the analysts are performing appropriate reviews and keeping abreast of any process changes. We believe that the TSC should develop a system for performing regular spot-checks of NDIU analysts’ work to identify any weaknesses and needs for additional training. This process should be included within the comprehensive quality assurance SOP.
Handling Classified Quality Assurance Matters
Prior to April 2007, the TSC was using an in-house system called quality assurance tracker to catalog all classified correspondence related to quality assurance matters.56 However, TSC officials determined that the database: (1) had reached its storage capacity, (2) temporarily lost an estimated 2,000 records in January 2007, (3) did not have a reliable process for backing up the data, (4) did not create any standard management reports, (5) had no method for audit tracking, (6) had not been examined and tested thoroughly by the FBI, and (7) was used by very few staff. Therefore, the TSC shut down the database in April 2007 to prevent any more problems with its use.
The TSC researched several possible long-term methods for tracking classified quality assurance correspondence. As of April 2007, the TSC’s temporary method was to use electronic folders on a classified server. We believe that this method will not be an effective method for tracking classified correspondence. In addition, a quality assurance analyst in the NDIU told us that the electronic folder method will be more time-consuming and less useful than tracking their individual correspondence within e-mail accounts and, as a result, some analysts do not plan to use the temporary system. We believe the TSC needs to develop a more effective and user-friendly means for temporary tracking of classified quality assurance correspondence.
Progress on the TSC’s Record-by-Record Review of the TSDB
In responding to our earlier audit, TSC officials reported that they planned to conduct a record-by-record review of all records within the TSDB. In February 2006, TSC officials estimated that this review would not be complete until 2012. At the time of our current audit, the record-by-record review was ongoing through the three-pronged strategy of the NDIU – the single review queue, encounter-driven quality assurance reviews, and special projects. TSC officials told us that they plan to examine the TSDB following the completion of the on-going special projects and determine how many TSDB records have not yet been reviewed. The TSC then plans to review any previously unexamined records in an effort to examine the entire TSDB.
In February 2007, TSC officials told us that since the inception of the single review queue in March 2006 over 670,000 TSDB records had been reviewed and the agency had revised its estimated completion date. TSC officials now project that the record-by-record review will be complete by the end of 2007.
Yet, we believe that the TSC may have overstated the number of records reviewed and is underestimating the amount of time and effort that it will take to complete its review of the entire TSDB. We base these conclusions on the following factors:
As previously discussed, the TSC’s single review queue and encounter-driven quality assurance processes do not sufficiently ensure the quality of the watchlist records. Therefore, the TSC should reconsider records examined in these processes in its count of records reviewed.
The number of records reviewed is not limited to the review of unique records. Rather, the TSC’s quality assurance process allows for one record to be reviewed multiple times: through the single review queue, following each request to modify or delete the record, in accordance with one or more special projects, and subsequent to each encounter. Therefore, we believe that the TSC’s cumulative tally of records reviewed can include records counted multiple times.
Between September 2006 and April 2007, the TSDB grew at an average rate of over 20,000 records per month, or approximately 174,000 additional records during this 8-month period. This growth adds to the analysts’ workload. Since April 2004, the TSDB has more than quadrupled in size, growing from 150,000 to 724,442 records in April 2007.
In February 2007, there were about 3,000 open quality assurance matters that required follow-up.
We believe that, if the number of records in the TSDB continues to grow at the current rate and the number of quality assurance matters similarly increases, the NDIU will not complete the record-by-record review of the TSDB by the end of 2007 as anticipated. We recommend that the TSC accurately determine the magnitude of the unexamined portion of the TSDB so that agency officials can implement a sound plan for examining those records and develop a realistic completion date for the endeavor. Further, the TSC should establish benchmarks against which it can measure its progress.
TSC Efforts to Enhance Terrorist Watchlisting
Although we identified several actions that the TSC should take to help improve the accuracy and completeness of watchlist records, our audit also revealed a recent TSC initiative that we believe is a noteworthy practice for enhancing watchlist records. Specifically, we noted that the TSC runs a report each week of NCIC hits in VGTOF and compares these hits to positive encounters in its Encounter Management Application (EMA) database to determine if each hit was called into the TSC Call Center. Performing this review offers the TSC an opportunity to educate local law enforcement officers about the importance of the TSC mission and determine if there have been additional known or suspected terrorist encounters of which the TSC was previously unaware. If the encountered individual was a positive identity match to a terrorist watchlist record, then any new information obtained during the encounter should be added into the TSDB record to enrich the record and provide added value to the intelligence community. TSC officials stated that currently they are identifying an average of 40 to 70 encounters each week that are not being called into the TSC. When the TSC identifies a hit that was not called into the call center, this information is relayed to the FBI. In turn, the local FBI field office is asked to follow up with the local law enforcement agency that ran the NCIC check. The FBI field office sends an agent to the local, state, or tribal law enforcement agency to obtain any information about the encounter and to remind the law enforcement agency that they should call all NCIC hits for known or suspected terrorists into the TSC Call Center.
We believe this practice can provide useful information for enriching the watchlist records. However, we noted that although the NCIC hit report is run on a weekly basis, it is taking an additional 2 weeks to notify the FBI of these encounters. Our concern with the 2-week time lag is that some local, state, and tribal law enforcement personnel will not remember clearly the encounter by the time they are contacted by the FBI, which can result in a missed opportunity to obtain new information. TSC officials told us that they are working with the FBI to expedite this process.
We were also told that other law enforcement agencies do not always follow up with the TSC to inform them about any newly obtained encounter information. Considering that approximately 60 percent of the encounters are identified by the CBP, the TSC should explore methods for performing similar enrichment exercises related to other screening agency encounters.
The TSC has made significant strides in its quality assurance efforts since our last review, including the creation of the NDIU and the development of new quality assurance processes. In addition, the TSC’s goal to perform quality assurance testing of all new and historical records in the TSDB is a positive step. However, we believe that more needs to be done to ensure the accuracy of the watchlist records.
The number of quality assurance matters identified by the TSC increased from about 2,500 in November 2006 to over 20,000 in March 2007, with the number of unresolved matters increasing from 177 to 2,514 during this period. Additionally, the overall size of the consolidated terrorist watchlist has quadrupled in size since the TSC’s inception, increasing from about 150,000 records in April 2004 to over 700,000 as of April 2007. This growth further adds to the amount of work for the TSC quality assurance staff to ensure the quality of the records in the consolidated watchlist database.
Our review found that the TSC has not developed a detailed plan of action and benchmarks or milestones to accomplish its goal of reviewing every record in the watchlist database. Additionally, we found errors in records that had undergone routine TSC quality assurance reviews, but a higher quality for watchlist records examined in TSC special project reviews.
We also found that the TSC’s SOP for quality assurance matters did not provide sufficient guidance for analysts to use in performing their examinations of watchlist records. Further, the TSC’s oversight and internal controls over the quality assurance process did not detect the continued existence of significant record errors and omissions. Finally, we believe the TSC is hampered by the lack of agreements with the nominating and screening agencies. Such agreements could improve the timeliness for resolving quality assurance matters and help ensure that additional information is obtained during encounters with known or suspected terrorists.
Without a standardized process, adequate internal controls, and agreements with source and watchlist agencies, watchlist records may remain inaccurate and incomplete for an unnecessary amount of time. Before the records are corrected or updated, law enforcement agencies may encounter watchlisted individuals. Additionally, inaccurate records can cause screeners to unnecessarily delay or detain individuals misidentified as a known or suspected terrorist.
We recommend that the TSC:
Correct the records identified by the OIG containing incorrect watchlist designations, handling code errors, and inaccurate and inconsistent information.
Coordinate with NCTC and the FBI to implement an agreement that establishes the areas of responsibility and the timeframes for data quality assurance matters.
Develop a comprehensive standard operating procedure that describes the TSC’s three-pronged quality assurance strategy and details the methodology to be used in performing quality assurance reviews.
Develop a process to perform regular spot-checks of NDIU analysts’ work to identify any weaknesses and need for additional training.
Develop an improved and user-friendly process for tracking classified correspondence related to quality assurance matters.
Develop a tickler system or digital dashboard for all pending quality assurance matters.
Develop a comprehensive plan, including benchmarks or milestones, to complete the record-by-record review of the TSDB.
Coordinate with other partner agencies to establish a formal process for relevant encounter information to be captured by frontline screening agents and returned to the TSC to update watchlist records.
III. TERRORIST WATCHLIST REDRESS
The TSC has developed comprehensive procedures, has dedicated staff, and coordinates with partner agencies to help ensure that it effectively and efficiently processes complaints from individuals experiencing delays or difficulties due to terrorist watchlist screening. Our review found that the TSC was following its procedures and reaching appropriate resolutions in such redress reviews. TSC redress disposition data indicated that nearly half of the total closed redress reviews resulted in a modification to or removal of a terrorist watchlist record. We believe that the TSC’s redress review results provide a further indicator that watchlist data needs continuous monitoring and attention.
We also found that there are excessive delays in closing redress matters. Additionally, we believe that the TSC should use information related to terrorist watchlist identities that are frequently the subject of watchlist encounters to proactively initiate redress reviews before complaints are filed.
Overview of the TSC’s Redress Efforts
Persons stopped as a result of watchlist matches may be actual watchlist subjects, individuals misidentified to a terrorist identity, or someone mistakenly included on the watchlist. As a result of the terrorist watchlist screening process, individuals may complain that they were adversely affected and seek relief. Individual government agencies involved in terrorist watchlist screening should have a redress process to effectively resolve the complaint and respond to the complainant. Similarly, the TSC should have reasonable procedures to provide redress for individuals from faulty watchlist identifications.
When we initiated our first TSC audit in 2004, the TSC did not have an established process for handling inquiries related to private individuals who sought watchlist information following their involvement in a screening encounter. In January 2005 the TSC assigned staff to address terrorist watchlist screening complaints and began to develop a strategy for redress matters. In our previous audit report, we recommended that the TSC develop formal procedures for handling redress inquiries. In response, the TSC formalized its process by implementing an official Redress SOP in July 2005 and a revised version in May 2007.57
In brief, individuals who believe they were unnecessarily and adversely affected by watchlist-related screening procedures may file a redress complaint with the agency involved in the event. For example, if an individual is prohibited from boarding a commercial airline flight, the person would contact the TSA to file a redress complaint. If the TSA determines that the event was related to terrorist watchlist screening, the complaint is forwarded to the TSC for review. Once the TSC has completed its examination, it makes any necessary changes to associated watchlist records and forwards its results back to the TSA, which provides feedback to the complainant.
In November 2005, the TSC created a separate Redress Office to process redress matters. As of April 2007, the TSC Redress Office was managed by the Redress Officer and supported by four analysts and one management assistant. TSC officials said they plan to expand the Redress Office to seven analysts.58 The analysts in this office are responsible for reviewing redress inquiries, corresponding with partner agencies for clarification or additional information, and recommending to the Redress Officer how to dispose of an inquiry. The Redress Officer is responsible for supervising the analysts, reviewing each redress evaluation, facilitating coordination with other agencies, and finalizing the disposition of the redress inquiry.
We believe the TSC has taken a number of other positive steps to address redress matters since our prior audit. For example, the TSC helped to spearhead the creation of a multi-agency agreement addressing watchlist redress. In addition, the TSC has enhanced its own procedures for handling redress matters.
However, in this audit we identified areas in need of continued improvement and further development, such as the timeliness of redress matter resolution and utilizing encounter information to provide redress without a complaint being submitted. These issues are discussed below.
Multi-agency Redress Agreement
In December 2006, a multi-agency agreement entitled Memorandum of Understanding on Terrorist Watchlist Redress Procedures (Redress MOU) was developed by a working group of representatives from the various agencies involved in terrorist watchlisting and screening. Representatives from the Privacy and Civil Liberties Oversight Board of the Executive Office of the President were also included in the development of the MOU.59 As of April 2007, the Redress MOU was being circulated for signature by the heads of the TSC, DOJ, DHS, State Department, the Office of the Director of National Intelligence (ODNI), the FBI, the Central Intelligence Agency (CIA), NCTC, the Department of Defense (DOD), and the Department of the Treasury.60
The Redress MOU formalizes the responsibilities of each agency in adjudicating redress inquiries. The agreement requires each agency to assign redress responsibilities to a senior official and commit necessary resources to ensure the efficiency of the redress process and compliance with the Redress MOU. The Redress MOU notes that the TSC has ultimate authority on redress decisions related to the terrorist watchlist.61
Overview of the Terrorist Watchlist Redress Process
On February 20, 2007, DHS and the State Department implemented the Traveler Redress Inquiry Program (TRIP). This program established a centralized portal for persons to file complaints regarding difficulties experienced at screening points during travel, such as airports, train stations, and border crossings. DHS headquarters officials informed us that TRIP will also help coordinate the resolution of complaints, monitor trends in complaints, and measure redress process efficiencies.
Exhibit 4-1 shows a basic illustration of the U.S. government’s process for addressing redress inquiries related to the terrorist watchlist.
EXHIBIT 4-1
Flowchart of Terrorist Watchlist Redress Process
[Image Not Available Electronically]
Source: The Terrorist Screening Center
Receipt of Redress Complaints
Complainants file redress inquiries with the frontline screening agencies involved in the encounters, such as to the FBI or through TRIP for DHS and the State Department.62 As shown in Exhibit 4-1, the screening agency reviews the complaint and determines if the inquiry relates to a possible terrorist watchlist match.
Individuals can also be affected by screening protocols unrelated to the terrorist watchlist, such as through random search procedures or other security screening practices. Despite someone’s actual presence or non-presence on the terrorist watchlist, individuals may assume they have been mistakenly included on the watchlist or misidentified to a terrorist watchlist identity and submit a complaint requesting relief. If the screening agency determines that the complaint is not related to the terrorist watchlist, it should resolve the matter internally and respond to the complainant. For example, an airline may deny a person from boarding an airplane because of drunkenness or disorderly behavior. Complaints related to these types of matters and others unrelated to the terrorist watchlist should not be referred to the TSC.
However, the screening agency should refer to the TSC all redress inquiries determined to pertain to a possible watchlist match. From January 2005 through February 2007, the TSC received 438 such redress referrals. As illustrated in Exhibit 4-2, 96 percent of the redress inquiries referred to the TSC were forwarded by DHS components (CBP, TSA, Immigration and Customs Enforcement (ICE), and other DHS entities). The TSA referred nearly one-half of all redress inquiries received by the TSC. Non-DHS agencies referred a total of 19 redress matters, including the FBI (9 referrals), the State Department (3 referrals), state and local law enforcement agencies (6 referrals), and the Executive Office of the President (1 referral).
EXHIBIT 4-2
TSC Redress Referrals by Referring Agency
(January 2005 through February 2007)
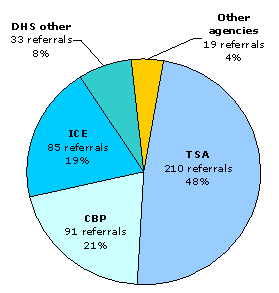
Source: The Terrorist Screening Center Redress Office
TSC Redress Process
When the TSC receives a redress complaint, the TSC Redress Office analyst assigned responsibility for resolving the complaint determines the relationship of the complainant to the terrorist watchlist and places the individual in one of the following three categories: (1) non-related, (2) positive match, and (3) misidentified.
Non-related – The analyst may determine that the complainant does not match a terrorist watchlist identity and was not the subject of an encounter involving a potential match. Essentially, the inquiry should not have been referred to the TSC in the first place. In these cases, the TSC returns this matter to the appropriate screening agency for resolution.
Positive Match – A complainant who matches an identity on the terrorist watchlist and was the subject of at least one watchlist-related encounter is considered a positive terrorist watchlist match. For positive match redress referrals, a Redress Office analyst conducts a complete review of the watchlist records to ensure information on the individual meets the criteria for watchlisting and is accurate, complete, and current. This review will also include contacting the nominating agency to obtain any new information on the individual not yet available to the TSC.
After reviewing this information, the analyst recommends that a record: (1) remain unchanged, (2) be modified, or (3) be removed from the watchlist. If it is determined that the watchlist record is accurate, complete, and current, the analyst then recommends that no changes be made to the record or the watchlist status of the individual.
For some redress inquiries, the analyst recommends a modification to the record. This could entail updating the record with new information or correcting errors in the record. Another recommended revision may include changing the watchlist status of an individual, such as removing a person from the Selectee list or escalating a person’s watchlist status from the Selectee list to the No Fly list.
The last disposition scenario for a positive match record involves removing the identity record from the terrorist watchlist altogether. Based on a review of relevant and current information, the analyst may determine that an identity does not meet the criteria for inclusion on the terrorist watchlist.
Misidentification – An individual who is the subject of a terrorist-related screening but whose identity is not on the terrorist watchlist is considered to have been misidentified. Redress referrals for misidentified complainants are processed by the TSC similarly to positive match referrals. The Redress Office analyst assigned the inquiry reviews the terrorist watchlist record involved in the misidentification and ensures that the record is accurate, complete, and current. The analyst then recommends any necessary changes to the record or watchlist status.
If, as a result of a redress review, the TSC recommends a change to the watchlist record or status (for either a positive match or misidentification referral), the Redress MOU and the TSC Redress SOP both require that the TSC discuss its findings with the nominating agencies. While the nominating agencies may provide input, the TSC has the ultimate authority to resolve all terrorist watchlist redress matters. Finally, the TSC Redress Office ensures that the necessary changes are made to watchlist records before closing its review and alerting the frontline screening agency of its resolution. The TSC does not respond to the complainant. Rather, the TSC coordinates with the frontline screening agency, which should submit a formal reply to the complainant.
The TSC’s revised May 2007 Redress SOP includes an expansion of the redress disposition categories. The non-related category was expanded to capture two additional situations: (1) instances in which the TSC administratively closes its review because screening agencies do not comply with TSC redress requirements, and (2) occasions that a redress complaint was considered moot because the terrorist identity to which the redress inquiry refers was already removed from the watchlist through normal watchlist modification or quality assurance procedures. In addition, the TSC renamed its misidentification category to “near match.” Lastly, the TSC added one disposition category to use when the TSC Call Center incorrectly identified an individual as a positive watchlist match. The TSC believes its expansion of disposition categories will allow it the ability to better track its redress resolutions and to identify areas in the watchlist process that could be improved. For instance, the Redress Office could find that the TSC Call Center’s percentage of incorrect identifications has increased significantly and recommend that a thorough review be conducted.
Disposition of Redress Complaints
The TSC tracks its processing and disposition of redress inquiries in a TSC database. At the time of our review, the database included only those disposition categories used by the TSC prior to the revision of the TSC’s Redress SOP. The disposition for the 388 redress inquiries closed by the TSC between January 2005 and February 2007 is shown in Exhibit 4-3.
| EXHIBIT 4-3 TSC Redress Complaint Disposition (January 2005 through February 2007) |
||
| Disposition | Number of Complaints |
Percentage of Complaints |
|---|---|---|
| Misidentification | 52 | 13% |
| Positive Match (no change) | 136 | 35% |
| Positive Match (remove record) | 76 | 20% |
| Positive Match (modify record) | 97 | 25% |
| Non-related | 27 | 7% |
| Total | 388 | 100% |
Misidentified Complainants
TSC redress complaint disposition data show that 13 percent of the 388 closed redress inquiries were for complainants who were misidentified to a terrorist identity and were not an actual watchlist subject.
According to the TSC, the most common cause of a misidentification is name similarity. As previously discussed, the watchlist is identity-based and relies on name searches in order to vet persons against the watchlist. This can result in a person with an identical or similar name being identified as a terrorist watchlist identity. In many instances the screening agency can use additional identifying information, such as a date of birth or a passport number, to eliminate the individual as a terrorist watchlist match.63
Positive Watchlist-Match Complainants
Of the 388 redress complaints reviewed by the TSC between January 2005 and February 2007, 80 percent involved complainants who were on the terrorist watchlist. Through its redress review process, the TSC determined that watchlist records for 35 percent of the closed positive watchlist-match redress complaints required no change, 25 percent required some modification to the watchlist records, and 20 percent necessitated removing the complainant’s identity from the watchlist.
Therefore, the TSC determined through its review that 45 percent of the watchlist records related to redress complaints were inaccurate, incomplete, not current, or incorrectly included.64 TSC officials stated that, in some instances, at the same time that a nominating agency was going through the process of having an individual removed from the watchlist, that individual filed a redress complaint. In other instances, the TSC Redress Office found inaccuracies in the watchlist record or discovered additional, relevant information that had not been passed to the TSC.
Specifically, in 76 redress reviews, the TSC determined that the individual should not be watchlisted. In an additional 97 instances, the TSC found that the watchlist record was inaccurate or incomplete. The TSC’s redress review results indicate that the watchlist includes individuals that should not be watchlisted and that other records contain deficiencies. These results are further evidence that watchlist data needs continuous monitoring and attention.
At the time of our review, the TSC did not track whether a change to the watchlist record was the result of a TSC redress review or whether the change was coincidental to a concurrent nominating agency submission of information to update the watchlist record. The TSC believes its expanded disposition categories will better account for these scenarios and provide a more accurate picture of redress resolution. The TSC Privacy Officer acknowledged that the high percentage of records requiring modification or removal may point to deficiencies in the terrorist watchlist nomination process and with nominating agencies not providing the TSC additional information important to appropriately update terrorist records.
Timeliness of Processing Redress Complaints
For each redress complaint it receives, the TSC develops a file folder and inputs information into a redress tracking database. The redress file contains information obtained, verified, and developed by the Redress Office. The file contains the Redress Office’s review of relevant databases, correspondence with partner agencies, rationale for the resolution of the complaint, and management review.
We judgmentally selected 20 redress inquiries the TSC received between January 2006 and February 2007 and reviewed the corresponding redress files to determine if the TSC followed its Redress SOP for resolving a redress complaint. We found the TSC complied with its Redress SOP in all 20 cases, including reviewing the applicable screening and intelligence databases, coordinating with partner agencies, and reaching appropriate resolutions.
We also reviewed TSC redress files and statistics to determine the efficiency of redress reviews. Our analysis of TSC data reveals that it took the TSC, on average, 67 days to close its review of a redress inquiry.65 For redress matters referred to the TSC during the last semiannual period in our review (July through December 2006), it took the TSC an average of 57 days to finalize its review.
In addition to closed matters, we also analyzed the number of days that pending TSC redress matters had been open. The TSC had a total of 50 open redress inquiries as of February 27, 2007 and the average number of days these matters were open was 61. Of these inquiries, 38 percent were open over 60 days, including 2 inquiries that were pending over 180 days. Exhibit 4-4 details the number of days the 50 redress matters were open as of February 27, 2007.
| EXHIBIT 4-4 Open TSC Redress Matters (as of February 27, 2007) |
||
| Number of Days Open | Number of Open Redress Matters |
Percentage of Total Open Redress Matters |
| 180 days or more | 2 | 4% |
| 90-179 days | 12 | 24% |
| 60-89 days | 5 | 10% |
| 30-59 days | 11 | 22% |
| less than 30 days | 20 | 40% |
| Total | 50 | 100% |
Our analysis of closed and open redress matters indicates that it takes, on average, about 2 months for the TSC to finalize its review of a redress inquiry. TSC redress files included copies of e-mails and records of discussion between the TSC Redress Office and nominating agency personnel, as well as an accounting of other significant actions taken by TSC analysts to resolve the inquiry. TSC officials stated that each redress review is unique and that more complex cases require a longer review period.
Our review of TSC redress files revealed that long review periods were caused by a variety of factors. In some instances, the TSC took a significant amount of time to finalize its determination before coordinating with other agencies for additional information or comment. A TSC official involved in redress also stated that the Redress Office staffing level sometimes affected the TSC’s ability to reach timely determinations. At times, the Redress Office used staff from other TSC units on a collateral, part-time basis. These persons would process redress matters when not performing their primary responsibilities and as time permitted. However, the TSC determined that this collateral assignment method did not provide the most efficient or effective means of resolving redress matters and, as a result, stopped this practice as of April 2007.
Other lengthy redress reviews were affected by nominating agencies not providing timely feedback to the TSC or not efficiently processing watchlist paperwork. The coordination TSC conducts with nominating agencies on redress matters includes corresponding with subject matter experts and case agents for clarification or updated information, requesting necessary watchlist processing documents (such as the FBI’s terrorist watchlist nomination and modification form), and resolving differences of opinion between the TSC and nominating agency. For two redress matters, we found that the TSC repeatedly requested the FBI to file necessary paperwork in order to modify the watchlist records, and that it was finally able to close the matters over 140 days after its original requests. Further, we reviewed another redress file showing the FBI closed a preliminary investigation on an individual in November 2005. However, it did not notify the TSC that it determined the individual had no nexus to terrorism and should be removed from the watchlist. The TSC’s redress review finally effected the overdue removal of this individual from the watchlist in January 2006.
Additionally, our file review found that certain screening agencies were slow to update their databases with accurate and current information. For instance, the State Department and the CBP did not revise encounter records in the IBIS database in a timely fashion to reflect modified or removed terrorist identities. For example, in one case the CBP did not make a TSC-requested change for more than 130 days.
TSC officials noted that no response timeframes have been established with partner agencies for redress matters. The Redress MOU states that one of the goals of the redress process is to provide for a timely review, but explicit timeframes are not defined. We believe that timeliness measures should be established for resolving terrorist watchlist redress complaints and responding to complainants. The TSC Privacy Officer stated a next step in improving terrorist watchlist-related redress coordination among government agencies is to negotiate timeframes for redress processing. Given the TSC’s responsibility for the content of the consolidated terrorist watchlist and its role in developing the Redress MOU, we recommend that the TSC attempt to coordinate timeliness measures for the entire watchlist redress process.
Response to Redress Complainants
The TSC does not respond to complainants filing redress inquiries. Instead, the TSC notifies the frontline screening agency of its disposition decision as it relates to the terrorist watchlist. The frontline screening agency involved in the watchlist-related encounter prompting the complaint is responsible for responding to the complainant. TSC policy dictates that responses to complainants neither confirm nor deny the existence of watchlist records relating to the complainant. This nondisclosure policy exists to protect U.S. counterterrorism operations and intelligence objectives and to safeguard the personnel involved in these sensitive activities. The TSC works with screening agencies such as the TSA in developing appropriate language for responding to complainants.
While the FBI is not the user of the NCIC database during a terrorist watchlist-related encounter involving a state or local law enforcement officer, it is the de facto screening agency in instances involving its NCIC database, and therefore responsible for responding to redress complaints concerning its database.66 In May 2007, the FBI implemented a watchlist redress policy, identifying its Terrorist Review and Examination Unit (TREX) as responsible for processing the FBI’s review of redress matters and for responding to complainants for NCIC-related complaints.67 However, before it developed this policy, the FBI had not decided how it would respond to complainants, and we found that as of June 2007 it had not responded to a redress complainant on a matter the TSC had closed on February 13, 2007, and had forwarded to the FBI for action.
If a complainant is not satisfied with the disposition of an initial redress inquiry, the complainant may file an administrative appeal where available by the screening agency. The Redress MOU outlines the responsibilities for each agency in processing an administrative appeal of an original redress inquiry determination. Additionally, the TSC adopted a separate Redress Appeals SOP in November 2006 to expressly describe its administration of an appealed redress decision. The TSA is the only frontline screening agency that has developed its own process for redress appeals.
The TSC Redress Appeals SOP stipulates that a complete analysis of the appeal be performed by the TSC Legal Department, a unit separate from the Redress Office. The TSC prohibits the TSC Redress Office and any personnel involved in the original redress review from direct involvement in the redress appeal process. According to the SOP, the TSC will alert NCTC and the nominating agency that an appeal has been submitted, and it will facilitate necessary communication between the nominating and screening agencies. The final recommendation or decision is determined by the TSC Redress Appeals Board, comprised of TSC Deputy Directors. For an appeal involving a No Fly watchlist status, the TSC recommends a disposition and the TSA has the final decision authority.
As of May 1, 2007, the TSC had received four redress appeals. It resolved two appeals, and these resulted in downgrading the watchlist status of the individuals. The remaining two appeals had been pending resolution for 83 and 167 days, according to the TSC. The TSC stated that staffing constraints hindered its ability to more quickly resolve these redress appeals. The TSC informed us that in April 2007 it was able to assign redress appeal duties to a permanent staff position and the TSC believes that this action will improve the TSC’s timeliness in resolving redress appeals.
It is possible for the TSC and other watchlist agencies to use available information to provide unsolicited relief to non-watchlist persons identified by the terrorist watchlist process. Besides its standard redress reviews, the TSC Redress Office also conducted ancillary evaluations of persons reported to have been identified by terrorist watchlist screening who had not filed a formal complaint. Additionally, the U.S. government, including the TSC and screening agencies, has information on persons misidentified as a terrorist watchlist subject in the various screening databases. However, the U.S. government, including the TSC, is not currently coordinating the use of this data in attempts to proactively reduce the incidence and impact of misidentifying persons as watchlist subjects.
TSC Informal Redress Reviews
Typically, the TSC undertakes a redress review only when an individual submits a formal redress request. Occasionally, however, the TSC Redress Office reviews records outside this formal process. The TSC may be asked by a government official to look into a matter or it may acquire from a news media publication the name of a person possibly stopped due to the terrorist watchlist. For instance, a newspaper may publish an article explaining that a foreigner was not allowed to board a flight destined for the United States and the TSC Redress Office believes that the TSC should research the events. In such a case, the TSC Redress Office performs an evaluation similar to its formal redress review for such matters. First, it determines if the person was the subject of a terrorist watchlist-related encounter. If so, it reviews the related watchlist record for accuracy and completeness, making changes and updates as necessary.
The TSC Redress Office maintains a log that records the intake and resolution of these proactive reviews. Our review of this log shows that since this initiative began in December 2005, the TSC had resolved 76 cases through March 1, 2007, tracking them according to its redress disposition categories. Exhibit 4-5 shows that over 80 percent of these reviews involved an individual who experienced a watchlist-related encounter (misidentification and positive-match categories). Of the 32 positive matches, terrorist records were modified or removed from the watchlist for 16 of the reviews.
| EXHIBIT 4-5 TSC Informal Redress Reviews (December 2005 through March 1, 2007) |
||
| Disposition Category | Number | Percent |
| Misidentification | 32 | 42% |
| Positive Match | 32 | 42% |
| Non-related | 10 | 13% |
| Further Investigation68 | 2 | 3% |
| Total | 76 | 100% |
Use of Watchlist Encounter Information for Misidentified Individuals
The TSC has a record of all potential terrorist watchlist encounters referred to its call center, including information on positive, negative, and inconclusive encounters.69 Therefore, the TSC has knowledge of the watchlist records involved in the negative encounters referred to its call center, as well as information on the individual that was misidentified as a potential terrorist for a period of time.
The TSC does not have any policy or procedures to proactively use information from negative encounters to reduce the incidence and impact of terrorist watchlist misidentifications. Moreover, the TSC’s strategic plan does not include goals or actions associated with reducing the incidence of misidentifications or the impact on misidentified persons, other than that covered by the formal redress process. Considering that 43 percent of all encounters referred to the TSC Call Center are negative for a watchlist match, we believe the TSC should develop strategic goals and policy specific to mitigating the adverse impact of the terrorist screening process on non-watchlist subjects, particularly for individuals who are repeatedly misidentified as potential watchlist subjects.
Additionally, we believe the TSC should consider developing the ability within its encounter tracking system or consolidated watchlist database to alert the TSC to take proactive action on watchlist records that have been the subject of a certain number of encounters. For example, the system could be programmed to automatically generate a quality assurance lead for the TSC to perform a comprehensive review of the terrorist record. Such a function would help certify that a watchlist record frequently the subject of encounters, whether the encounters are positive, negative, or inconclusive, is accurate, complete, and current. This is important for both appropriately handling suspected or known terrorists and for reducing the adverse effects on persons misidentified as watchlist subjects.
Screening agencies across the federal government are in the process of instituting an interagency agreement that will formalize the U.S. government’s review of redress inquiries from individuals who complain they were adversely affected during watchlist screening. Additionally, the TSC has developed its own SOP for processing redress complaints. We found that the TSC generally followed these procedures, the procedures are comprehensive, and TSC staff resolved redress matters logically and accurately.
However, our examination of TSC redress files also revealed that the TSC’s comprehensive redress reviews often resulted in watchlist record changes and removals. We believe that the high percentage of redress reviews resulting in changes to or removals of watchlist records provides further evidence that watchlist data needs continuous monitoring and attention.
Our review also revealed that watchlist agencies, including the TSC and nominating and screening agencies, sometimes caused unnecessary delays in closing redress inquiry reviews. We recommend that the TSC coordinate efforts for the watchlist agencies to develop timeliness measures for each stage in the redress process.
We recommend that the TSC:
Organize a working group comprised of representatives from agencies involved in the terrorist watchlist redress process to develop timeliness measures for each phase in the redress process.
Develop goals and measures for its strategic plan to reduce the incidence and impact of misidentifications.
Develop procedures to proactively review terrorist watchlist identities that are frequently the subject of watchlist encounters, no matter if the encounter was positive, negative, or inconclusive.
We recommend that the FBI:
-
Develop and implement timeliness measures to ensure that the FBI responds in a timely manner to redress inquiries from complainants subject to terrorist watchlist-related encounters involving the NCIC database, including the complainant identified by the OIG whose complaint has been pending since February 2007.
Direct connectivity to the NCIC VGTOF system and quality assurance functionality were established in May 2005 and March 2006, respectively.
In June 2004, the TSC upgraded its original watchlist, which facilitated the electronic exchange of data with participating agencies’ systems.
Many of these deficiencies are attributable to data inconsistencies and inaccuracies that resulted from the TSC’s immediate need during its earliest days to develop a comprehensive database of known or suspected terrorists.
According to TSC standard operating procedures, a U.S. person is defined as either: (1) a citizen of the United States; (2) an alien lawfully admitted for permanent residence; (3) an unincorporated association with a substantial number of members who are U.S. citizens or are aliens lawfully admitted for permanent residence; or (4) a corporation that is incorporated in the United States.
On April 27, 2007, the TSC implemented an information technology solution to delete these records.
The TSC determined that the 564 records represented 443 unique identities. As of June 15, 2007, the TSC had resolved 413 of the 443 records.
To alert the TSC of this non-standard entry of records into the TSDB, the TSC implemented a special flag, referred to as “FBI sole source,” for FBI-originated international records. This designation precludes all future electronic transactions, including related modifications and deletions, from being exported from the TSDB to VGTOF.
The total sample of 50 records consisted of 25 each for domestic and internationally known or suspected terrorists.
Officials from NCTC, the TSC, and TREX stated that each agency attempts to process nominations to the watchlist within 1 day.
By August 2004, the Attorney General, the Director of Central Intelligence, and the Secretaries of Homeland Security, State, Treasury, and Defense signed Addendum A to the original governing MOU. Addendum A contained provisions for the declassification and sharing of terrorist information, including [SENSITIVE INFORMATION REDACTED]. However, the provisions only covered information obtained after August 2004.
The State Department maintains a list of the most wanted terrorist organizations and individuals as specified by Executive Order 13224. The Rewards for Justice website is an organization operated by the FBI, CIA, DOJ, and the State Department.
The NDIU’s 34 staff included 7 individuals whose primary duty was to function as a subject matter expert. The remaining 27 staff members were assigned to specific quality assurance tasks and assisted with other quality assurance efforts as necessary.
The TSC also uses 55 business rules to ensure watchlist criteria are met in exporting records to downstream databases.
Prior to the November 2006 TSDB upgrade, NDIU analysts first used an electronic spreadsheet and then a database commonly referred to as the “quality assurance tracker” to monitor quality assurance matters. NDIU analysts continued to use the quality assurance tracker for matters requiring classified correspondence because classified information cannot be placed into the QA ticket, which is housed within the TSDB – an unclassified system. In April 2007, the quality assurance tracker program was discontinued due to a number of concerns; the concerns and the TSC’s interim solution for recording classified quality assurance matters are discussed on page 39.
Each encounter is positive, negative, or inconclusive. A negative encounter occurs when a screening agency contacts the TSC because during a screening event an individual is a potential match to a TSDB record, and the TSC (or other law enforcement responder) determines that the individual is not a match to the name on the watchlist. Conversely, a positive encounter is where the individual encountered is a match to the watchlist. An inconclusive encounter occurs when the TSC is unable to determine if the individual encountered is a match to an individual on the watchlist.
Encounters offer law enforcement agents an opportunity to obtain additional information about watchlist subjects. For example, if a watchlist subject is positively identified during an attempted border crossing, the federal agent may obtain previously unknown information, such as a new passport number, eye color, or current address.
These NDIU staff members also address QA tickets generated from TSC quality assurance efforts other than encounter-driven reviews, such as through the single review queue and during ad hoc record quality reviews.
During its review of the No Fly list, the TSC continued to receive routine No Fly list additions, modifications, and deletions through the watchlist nomination process. As a result, it is not possible to subtract the special project-driven No Fly list changes from the starting point of 71,872 records and obtain the correct number of No Fly records as of January 31, 2007.
The period of time for which a record would have been inappropriately watchlisted to the No Fly list could range from a minimum of 1 day to a maximum of about 9 months.
We have consolidated our single review queue and encounter-driven quality assurance sample selection and testing results here for ease of presentation. Although we selected records from different subsets of the TSDB, each had been subjected to the same quality assurance steps in the NDIU, making this consolidation possible. Details of our sample selection and the populations from which we selected them are provided in Appendix I.
Each entry in this column represents a TSDB record for which we determined that the identified TSDB record field was not in agreement with TIDE and VGTOF. (We limited our review to those databases.) It is possible for one record to have more than one error, and the overall total is the number of field errors.
A digital dashboard is a business management tool to visually display the status of a business project. The dashboard can provide warnings, next steps, action notices, and summaries of a project.
The TSC could provide historical data on quality assurance matters only since November 2006 when the latest version of the TSDB was deployed.
The TSC cannot place classified information into its QA tickets because this information is stored within the TSDB, which is an unclassified system.
The TSC’s revised May 2007 Redress SOP includes more detailed guidance and reflects changes within the TSC, such as technology improvements, organization structure, and staffing. The revised Redress SOP also expanded TSC redress disposition categories and provided more detailed instructions on its redress processing as well as the incorporation of new technology and terminology.
As of April 2007, the TSC allocated six analyst positions to its Redress Office, of which four positions were filled. The TSC reported that it expected to add an additional analyst position for a total of seven.
The Privacy and Civil Liberties Oversight Board advises the President and other senior executive branch officials on matters with respect to privacy and civil liberties.
The TSC reported that as of April 18, 2007, all agencies had signed the agreement except the DOD, the CIA, and the State Department.
The TSA makes final decisions on No Fly list redress appeal matters.
The FBI is typically not the agency encountering the individual, but its NCIC system is used in the screening process. Therefore, the FBI is considered the screening agency in such instances.
Screening agencies have also developed programs to assist persons repeatedly misidentified to terrorist watchlist identities. For instance, an individual can voluntarily submit personal-identifying information to the TSA and request to be placed on the TSA Cleared List. If approved for placement on the Cleared List, the individual’s name and personal-identifying information can be used to more quickly determine that the individual is not on the No Fly or Selectee lists. Similarly, the CBP and the State Department have implemented procedures to annotate records of misidentified persons in their databases to help avoid future port-of-entry screening and visa application delays. These actions are particularly helpful for a non-watchlist individual with an exact or a very similar name match to a known or suspected terrorist.
This 45 percent does not include the terrorist records that were modified or removed as part of a redress inquiry by a misidentified individual because the TSC did not specifically track those types of dispositions.
Redress matters pending as of February 27, 2007, were not included in our analysis of closed redress matters.
A typical NCIC-related encounter involves a state or local law enforcement officer conducting a routine traffic stop. The officer searches the subject’s identification information (full name and date of birth) through the NCIC system to check for any outstanding warrants on the person. In the event the person is a possible terrorist watchlist identity match, the NCIC system will instruct the officer to contact the TSC to confirm the identity of the individual as an actual watchlist subject and to be instructed on the proper handling procedures for this individual.
As stated earlier, only 4 percent of the redress referrals provided to the TSC from January 2005 through February 2007 were from non-DHS components such as the FBI.
Two of the TSC Redress Office’s informal reviews required further investigation in order to determine the relationship of the individual to a watchlist identity.
Not all potential watchlist matches are referred to the TSC. If possible, screening agencies resolve negative encounters without contacting the TSC by comparing information on the encountered individual to the potential terrorist watchlist identity match. Screening agencies contact the TSC Call Center on all encounters where it cannot definitively make this determination.