I. FBI’S RESPONSE TO WEAPON AND LAPTOP LOSSES
- Our 2002 audit found that over a 28-month period the FBI lost or had stolen 354 weapons and 317 laptop computers. Our follow-up audit found that over a 44-month period the FBI lost or had stolen 160 weapons and 160 laptop computers, including 10 that contained sensitive or classified information. We noted improvements in the rate of loss for each category of equipment except for stolen laptop computers, which increased slightly. However, we found that the FBI did not know whether many of the laptop computers that were reported lost or stolen contained sensitive or classified information. We also found that the FBI has not taken adequate corrective action on several recommendations outlined in the 2002 audit report. As a result of our 2002 audit, the FBI established deadlines for reporting lost and stolen weapons and laptop computers, entering those losses into NCIC, and referring the losses for investigation. But this follow-up audit determined that the FBI did not consistently follow those procedures.
Rate of Weapon and Laptop Losses
To determine whether the FBI has made progress in reducing the number of lost and stolen weapons and laptop computers, we first compared the rate of loss from our 2002 audit to this follow-up audit. We found that, except for stolen laptop computers, the rate of loss decreased, as detailed in the following table.39
MISSING WEAPONS AND LAPTOP COMPUTERS
2002 AUDIT VS. FOLLOW-UP AUDIT40
| Category | Number of Lost or Stolen Items Reported | Losses Reported Per Month | ||
|---|---|---|---|---|
| 2002 Audit (28 Month Period) |
Follow-up Audit (44 Month Period) |
2002 Audit |
Follow-up Audit |
|
Lost Functional Weapons |
107 |
48 |
3.82 |
1.09 |
Stolen Functional Weapons |
105 |
94 |
3.75 |
2.14 |
Lost Training Weapons |
142 |
18 |
5.07 |
0.41 |
Stolen Training Weapons |
0 |
0 |
0 |
0 |
Total Lost or Stolen Weapons |
354 |
16041 |
||
Lost Laptop Computers |
300 |
116 |
10.71 |
2.64 |
Stolen Laptop Computers |
17 |
44 |
0.61 |
1.00 |
Total Lost or Stolen Laptops |
317 |
160 |
||
| Source: OIG analysis of FBI data |
We noted improvements in the rate of loss for each category of equipment except for stolen laptop computers, which increased slightly. However, despite the FBI’s progress in decreasing the rate of loss for weapons and laptops, the FBI still reported 160 weapons and laptops that were lost or stolen. We recognize that in an organization the size of the FBI, some weapons and laptops will inevitably be stolen or go missing. However, it is important that the FBI take appropriate steps to minimize these losses. When losses occur, the FBI must timely report the loss, be able to identify the contents of lost laptops, and determine whether the laptop is encrypted. In addition, the FBI must investigate these losses and thefts, enter required data into the National Crime Information Center (NCIC), and report the losses to DOJ as required.
We found that the FBI has not taken adequate corrective action on several recommendations outlined in our 2002 audit report. Further, the FBI did not determine for all of its lost or stolen laptop computers whether they contained sensitive or national security information. All users of FBI laptop computers had access to sensitive information and the equipment was authorized for processing classified information up to the Secret level. The FBI does not know which of its laptop computers actually contained classified information.42
In the following sections, we report on: (1) the circumstances surrounding each FBI weapon and laptop loss, (2) the contents of the lost or stolen laptop computers, (3) the FBI’s internal and external loss-reporting process, including entry into NCIC, and (4) the FBI’s efforts to investigate losses.
In our 2002 audit, we noted that in many instances the loss of weapons was preventable because employees either did not adequately safeguard property that had been assigned to them or follow FBI policies. Our 2002 audit also found five instances in which lost or stolen FBI weapons were subsequently used in the commission of a crime.
As shown in the table below, for the current review period 94 of 160 (59 percent) missing weapons were stolen from FBI vehicles, private vehicles, or employee residences. These lost and stolen weapons included handguns, rifles, shotguns, and submachine guns. Pistols accounted for 133 of the 160 (83 percent) lost weapons.
LOST AND STOLEN WEAPONS BY TYPE
FEBRUARY 1, 2002, THROUGH SEPTEMBER 30, 2005
| Pistol | Shotgun | Submachine Gun |
Rifle | Total | |
|---|---|---|---|---|---|
Lost: |
|||||
Unexplained Loss |
40 |
3 |
0 |
0 |
43 |
Miscellaneous43 |
23 |
0 |
0 |
0 |
23 |
Subtotal |
63 |
3 |
0 |
0 |
66 |
Stolen: |
|||||
From FBI Vehicle |
28 |
6 |
5 |
7 |
46 |
From Residence |
11 |
0 |
0 |
0 |
11 |
From POV 44 |
11 |
1 |
0 |
0 |
12 |
Other 45 |
20 |
3 |
1 |
1 |
25 |
Subtotal |
70 |
10 |
6 |
8 |
94 |
Total |
133 |
13 |
6 |
8 |
160 |
| Source: OIG analysis of FBI Forms FD-500 (Reports of Lost and Stolen Weapons) |
Although our follow-up review of FBI files found instances where thefts occurred despite reasonable precautions taken by FBI employees, we also found examples of lost or stolen weapons that resulted from employees’ carelessness or failure to follow FBI policy. Details of those losses are listed in Appendix III.
In March 2001, the FBI Director issued a memorandum requiring that all losses of laptop computers be reported to OPR because, “the loss of a laptop with classified or sensitive information could be potentially more damaging to the FBI than a lost weapon.”
The FBI also issued a memorandum dated November 1, 2002, outlining circumstances under which employees would be held accountable for the cost of the lost or stolen property. The memorandum stated that employees were responsible for securing property assigned to them and would be personally responsible for the value of any property that was lost, stolen, or not returned to the government.
Similar to the reports of lost and stolen weapons, many laptop computer losses could have been avoided had employees been more careful or had followed FBI policies. Details of these losses are listed in Appendix IV.
As shown below, we were unable to determine the circumstances of the losses for 116 of 160 missing laptop computers (72 percent) because FBI documentation did not include a description of how the item was lost. Sixty-two of these laptops were identified as lost when the FBI conducted its biennial inventories. The remaining 44 laptop computers (28 percent) were stolen from vehicles and other locations.
LOST AND STOLEN LAPTOP COMPUTERS
BY LOSS TYPE
FEBRUARY 1, 2002, THROUGH SEPTEMBER 30, 2005
| Total | |
|---|---|
Lost: |
|
Unexplained Loss |
116 |
Stolen: |
|
From FBI Vehicle |
23 |
From Residence |
4 |
Other 46 |
17 |
Subtotal |
44 |
Total |
160 |
| Source: OIG analysis of FBI Forms FD-500 |
Reporting Weapons and Laptop Computer Losses
During our initial review in 2002, we found that the FBI did not specify deadlines for submitting the Report of Lost or Stolen Property form (Form FD-500) to report loss of property. As a result, we recommended that the FBI establish and adhere to firm deadlines to ensure that: (1) employees promptly report the loss or theft of FBI property to their supervisors; (2) supervisors report losses or thefts to headquarters units, including the Firearms Training Unit, OPR, the Asset Management Unit, and the Security Division; (3) OPR initiates and completes an investigation into the loss; and (4) information from the Form FD-500 is entered into NCIC.
In response, the FBI revised its policy on August 14, 2002, requiring that employees report lost or stolen weapons and laptop computers to their division or field office within 5 days after discovery of the loss. Division or field offices, in turn, are required to submit a Form FD-500 to the Asset Management Unit within 10 days of the loss. All losses of weapons and laptop computers are required to be entered into NCIC and forwarded to the Inspection Division for investigation.47 Laptop computer losses are required to be reported to the Security Division.
We reviewed the reporting actions that the FBI took in response to the lost or stolen weapons and laptop computers by examining the Forms FD-500. We assessed whether the loss was reported to the Asset Management Unit, entered into NCIC, referred for investigation, and if a laptop, reported to the Security Division. The table below categorizes our findings.
FBI REPORTS OF THE LOSS OR THEFT OF
WEAPONS AND LAPTOP COMPUTERS
FEBRUARY 1, 2002, THROUGH SEPTEMBER 30, 2005
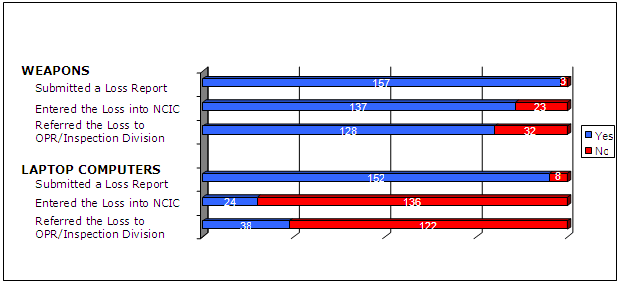
| Source: OIG analysis of FBI data |
Of the 160 missing weapons, the FBI was able to provide Forms FD 500 for 157 weapons. The remaining three weapons were missing the required forms. We asked the Asset Management Unit officials about the missing forms and were told that they existed at one point but at the time of our review they could not be found. Despite not having the Forms FD 500, the Asset Management Unit retained minimal information regarding the weapon losses, such as the serial numbers, by recording that information onto a list that was provided to us during our follow-up review. Of the 157 for which there was a Form FD 500, we found:
18 were reported using an outdated Form FD-500.48 The old form did not capture critical information such as the date of loss, NCIC entry, and whether OPR was notified.
92 weapon losses were reported on the new Form FD 500. However, 51 of the 92 new Forms FD 500 were incomplete because the individual preparing the form did not enter critical information such as the date of loss, NCIC entry, and whether the loss was referred to OPR for investigation.
54 were reported late—more than the required 10 days—thus possibly delaying timely investigation regarding the circumstances of the loss. See Appendix V for details on the number of days losses were reported late.
Of the 160 missing laptop computers, the FBI was able to provide Forms FD-500 for 152 laptops, while 8 laptops were missing the required form. Similarly, we asked the Asset Management Unit officials about the missing forms and were told that they existed at one point but at the time of our review, they could not be found. Despite not having the Forms FD-500, the Asset Management Unit retained minimal information regarding the laptop losses, such as barcodes and serial numbers, by recording the information onto a list that was provided to us during our follow-up review. Of the 152 that were reported using a Form FD-500, we found:
24 were reported using an outdated Form FD-500.49 The old form did not capture critical information such as the date of loss, NCIC entry, and whether OPR was notified.
107 laptop losses were reported on the new Form FD-500. However, 82 of the 107 new Forms FD-500 were incomplete because the individual preparing the form did not enter critical information such as the date of loss, NCIC entry, and whether the loss was referred to the Security Division as well as OPR for investigation.
38 were reported late—more than the required 10 days—thus possibly delaying timely investigation regarding the circumstances of the loss. See Appendix VI for details on the number of days losses were reported late.
Regarding the reporting process for both weapons and laptop computers, Asset Management Unit officials explained that the field offices are responsible for submitting complete, accurate, and timely Forms FD-500. According to these officials, the Asset Management Unit’s responsibility is essentially to ensure that property is accurately tracked in PMA. However, this understanding is contrary to the duties and responsibilities that have been assigned to the PMO in the Accountable Property Manual. The Accountable Property Manual states that the PMO is responsible for the overall administration, coordination and control of the FBI’s Property Management Program. For a comprehensive listing of the lost and stolen weapons and laptops, see Appendices V and VI.
Thus, although the FBI strengthened its policy for reporting lost or stolen weapons and laptop computers by revising the Form FD-500 and establishing a new 10 day policy for reporting losses, the FBI did not ensure that its staff consistently used the revised form or reported the loss within 10 days, as required. We recommend that the FBI ensure that its staff prepare complete and accurate loss reports using the latest version of the Form FD-500 and submit those reports to the appropriate offices in a timely manner.
Contents of Lost or Stolen Laptop Computers
Our review of the 152 Forms FD-500 for lost and stolen laptops revealed that 101 were identified as not containing sensitive or classified information, 43 were not marked as either containing or not containing sensitive or classified information, and 8 were marked as containing sensitive or classified information.50 We asked the Security Division for any information that it had on the 160 laptop losses. We were provided limited information on only 12 laptop losses that the Security Division reviewed. Two of the 12 laptop losses that the Security Division reviewed were initially part of the 101 that were identified on the Forms FD-500 as not containing sensitive or classified information. The Security Division determined that these two laptop computers did contain sensitive, but unclassified information. Therefore, we added these two laptop losses to the eight that were identified on the Forms FD-500 as containing sensitive or classified information. Details related to the 10 laptops are provided in the table below.
DETAIL ON LAPTOP LOSSES
CONTAINING SENSITIVE OR CLASSIFIED INFORMATION
| No. | Date of Loss |
Office Reporting Loss |
Type of Loss |
Encrypted? | Nature of Contents |
|
|---|---|---|---|---|---|---|
1 |
07/12/02 |
Boston Field Office |
Stolen |
Yes |
Software for creating identification badges.51 |
|
2 |
09/02/02 |
Indianapolis Field Office |
Lost |
Unknown |
Unknown |
|
3 |
09/24/02 |
New Orleans Field Office |
Stolen |
Unknown |
Used to process surveillance-related electronic digital imaging. |
|
4 |
07/15/03 |
Phoenix Field Office |
Lost |
Unknown |
Unknown |
|
5 |
03/11/04 |
Security Division |
Stolen |
Yes |
System security plan for an electronic access control system. |
|
6 |
05/19/04 |
Washington Field Office |
Lost |
Unknown |
Unknown |
|
752 |
05/06/05 |
Security Division |
Lost |
Unknown |
Unknown - SCU determined contents to be sensitive, but unclassified. |
|
853 |
06/24/05 |
CJIS Division |
Stolen |
Yes |
Unknown - SCU determined contents to be sensitive, but unclassified. |
|
951 |
08/21/05 |
San Diego Field Office |
Stolen |
Unknown |
Unknown - SCU determined contents to be sensitive, but unclassified. |
|
10 |
Unknown |
Quantico Laboratory Division |
Stolen |
Unknown |
Names, addresses, and telephone numbers of FBI personnel. |
|
| Source: FBI Forms FD-500 |
As previously stated, 8 of the 10 laptop losses were identified on the Forms FD-500 as containing sensitive or classified information the Forms FD-500 for these eight laptop losses did not specifically make a distinction as to whether the sensitive information included National Security Information (NSI). We asked Asset Management Unit and Security Division officials whether they could identify if any of the eight laptops did in fact contain National Security Information. The Security Division provided us information to indicate that the laptop loss reported by the CJIS Division on June 24, 2005, contained sensitive but unclassified information.54 FBI officials did not know whether the remaining seven laptops that were identified as sensitive actually contained National Security Information.55
According to OPR and Investigation Division records, the FBI investigated 6 of the 10 laptops losses that were known to contain sensitive or classified information.56 Of the six laptop losses that were investigated, one resulted in a 3-day suspension, two investigations were pending as of February 2006, and three resulted in no action taken against the employee. The FBI did not investigate the remaining four losses, including the laptop computers that contained personal identifying information of FBI personnel and software for creating identification badges.57
Similarly, we asked FBI Security Division officials if they conducted any type of review to determine the contents of the remaining seven laptop losses or to assess the potential damage to national security and the FBI’s operations. Security Division officials stated that they are reviewing the Forms FD-500 and contacting the appropriate field offices to determine what kind of information was on the laptops. However, the Security Division officials informed us that because these losses occurred some time ago it is doubtful that the FBI would still have information about the content of the laptops.
51 Laptop Losses
The Forms FD-500 for 43 of the 51 laptop computers did not indicate whether the laptops contained sensitive or classified information, as required. The employee who completed the form did not check the box to indicate whether sensitive or classified information was or was not contained on the laptop, nor did the Accountable Property Officer or the Asset Management Unit complete that section of the form when it was submitted. An analysis of the 51 laptop computers is provided in the table below.58
ANALYSIS OF THE 51 LAPTOP COMPUTERS
UNKNOWN TO HAVE SENSITIVE OR CLASSIFIED INFORMATION
| Category | Assigned To Employee |
Unassigned | Total |
|---|---|---|---|
Unexplained Losses59 |
3 |
22 |
25 |
Loss Identified During FBI Physical Inventories |
5 |
16 |
21 |
Stolen from Vehicle |
1 |
1 |
2 |
Stolen from FBI Office |
0 |
1 |
1 |
Other |
2 |
0 |
2 |
TOTAL |
11 |
40 |
51 |
| Source: FBI Forms FD-500 |
Seven of these 51 laptop computers were assigned to divisions within the FBI that handle some of the most sensitive information related to national security. Six of the 51 laptop computers were assigned to the Counterintelligence Division and 1 was assigned to the Counterterrorism Division. Yet, the FBI did not know the content of these computers or whether they contained sensitive or classified information.
Of these 51 laptops, 11 were referred to FBI’s OPR/Inspection Division. Further, only two resulted in disciplinary action, including one letter of censure and one 3-day suspension. The documentation maintained at OPR did not contain the contents of these laptop computers.
Even though the FBI has a policy requiring that employees disclose the contents of lost or stolen laptops, this policy was not enforced. Most of the Forms FD-500 as detailed in Appendix IV did not have a description of the type of information contained on the laptop. This is a significant deficiency because some of these laptops may have contained classified or sensitive information such as personally identifiable information or investigative case files.60 Without knowing the contents of these lost and stolen laptop computers, it is impossible for the FBI to know the extent of the damage these losses might have had on its operations or on national security.
Aside from reviewing the Forms FD-500 we asked FBI officials if they could determine the content of the 51 lost or stolen laptop computers and whether they contained sensitive or classified information. FBI officials explained that they did not maintain such information and therefore could not determine the content of the laptops or whether sensitive or classified information was contained on them. We asked FBI officials why they do not have this information. Security Division officials speculated that its SCU may not have been notified of the lost and stolen laptop computers and therefore would not have followed up in determining the contents of the lost or stolen laptops. However, our review of all 152 Forms FD-500 for lost and stolen laptop computers found that 64 were marked as having been referred to the Security Division.
We also asked FBI officials why they do not go to the respective field offices and divisions to obtain this information. As previously mentioned, Security Division officials stated that they are reviewing the Forms FD-500 and contacting the appropriate field offices to determine what kind of information was on the laptops.
FBI officials acknowledged to the OIG that there was a breakdown in obtaining the necessary information on the contents of the laptops that were lost or stolen. The FBI Security officials suggested that part of the cause may be attributed to the lack of a centralized unit within the FBI that could identify the contents of lost or stolen laptops or make sure that Forms FD-500 are complete and accurate. Further, the Security Division officials stated that they have since started tracking this type of information with the implementation of the Portable Electronic Device (PED) Application in June 2006.61
We believe that the FBI was lax in adhering to its own policies of reporting the contents of lost or stolen laptop computers. The FBI has to be more diligent in ensuring that it responds appropriately and aggressively to each laptop loss.
The NCIC is a computerized database of criminal justice information, such as stolen property, convicted offender registries, and an index of individuals incarcerated in the federal prison system. The NCIC system is generally regarded by law enforcement agencies as the primary method for tracking stolen or recovered firearms. Criminal justice agencies enter records into NCIC, which are then accessible to law enforcement agencies nationwide. Data regarding lost or stolen weapons and laptop computers should be promptly entered into NCIC. Failure to enter these items into NCIC could result in reducing the chances of recovering the weapon or laptop computer or identifying the weapon if it is used in the commission of a crime. In addition, FBI policy states that lost and stolen laptops are required to be entered into NCIC.
Our 2002 audit found that 14 of the 276 (5 percent) lost or stolen weapons had not been entered into NCIC. In our follow-up audit, we initially found no NCIC records for 23 of the 160 (14 percent) lost or stolen weapons and no NCIC record for 136 of the 160 (85 percent) lost or stolen laptops.62 Of the 23 weapons and the 136 laptop computers, 11 weapons and 16 laptop computers had an NCIC number recorded on the corresponding Form FD-500, but we did not find a record in NCIC.63 For a detailed listing of the weapons and laptops that were not found in NCIC see Appendices IX and X.
At our exit conference, FBI officials stated that 10 of the 23 weapons currently do not have a record in NCIC. Specifically, the FBI provided us information on the following:
6 weapons had active records, 3 of which occurred as a result of our review.
7 weapons were recovered and the record was purged from NCIC as a result.
3 weapons were not entered into NCIC.64
7 weapons were at one point entered into NCIC but later purged with no explanation.
We also queried NCIC to determine whether the lost and stolen weapons and laptop computers were recovered and, for the weapons, whether they were used in the commission of a crime. We identified no instances where law enforcement recovered any of the 160 lost or stolen weapons, or the 160 lost or stolen laptop computers. Therefore, we could not conclude whether any of the missing weapons were used in a crime. However, after completion of our fieldwork, the FBI reported to us that seven weapons had been recovered. Details of those weapons are listed in Appendix III.
Asset Management Unit officials explained that the field offices are responsible for entering lost or stolen weapons and laptop computers into NCIC. In our judgment, the FBI has improved its practice of entering lost or stolen property into NCIC. However, 85 percent of the lost or stolen laptop computers were not entered into NCIC, as required by FBI policy. The FBI should immediately enter into NCIC its lost or stolen weapons and laptop computers to ensure that any recovery of these property items will result in the FBI being notified.
Referring and Investigating Losses
Our 2002 audit found that losses of weapons and laptops were not regularly referred to OPR and that disciplinary action was not taken when individuals did not follow FBI policies concerning the handling of weapons and laptops. As a result, we recommended the FBI revise its policy and establish criteria for disciplining employees whose negligence resulted in the loss or theft of a weapon or laptop. In response to our recommendation, the FBI stated that it would require weapon and laptop losses to be referred to OPR.65
OPR’s investigative responsibilities were transferred to the Inspection Division in February 2004. Specifically, the Inspection Division is responsible for investigating weapon and laptop losses while OPR is still responsible for adjudicating disciplinary matters.
Inspection Division officials told us that it delegates responsibility for conducting most investigations of lost or stolen weapons and laptops to the field office that reported the loss. If the results of the investigation warrant disciplinary action, the case is forwarded to OPR for adjudication. Inspection Division officials told us that in many cases the office that conducted the investigation found no evidence of misconduct and consequently no disciplinary action was taken.
REFERRALS AND INVESTIGATIONS OF WEAPON AND LAPTOP LOSSES
| Category | Number of Lost or Stolen Items66 | REFERRED | INVESTIGATED | |||
|---|---|---|---|---|---|---|
| Referred To OPR |
Referred to Inspection Division | Not Referred | OPR/ID Investigated | Not Investigated |
||
Lost Functional Weapons |
48 |
19 |
16 |
13 |
12 |
36 |
Stolen Functional Weapons |
94 |
50 |
35 |
9 |
58 |
36 |
Lost Training Weapons |
18 |
8 |
0 |
10 |
0 |
18 |
Stolen Training Weapons |
0 |
0 |
0 |
0 |
0 |
0 |
Total Lost or Stolen Weapons |
160 |
77 |
51 |
32 |
70 |
90 |
Lost Laptop Computers |
116 |
9 |
9 |
98 |
13 |
103 |
Stolen Laptop Computers |
44 |
13 |
7 |
24 |
8 |
36 |
Total Lost or Stolen Laptops |
16067 |
22 |
16 |
122 |
21 |
139 |
| Source: OIG analysis of FBI data |
The Inspection Division officials also stated that investigations were not pursued if preliminary information indicated that there was no negligence or misconduct on the part of the employee. For example, items identified as lost or stolen during a physical inventory were not considered by the Inspection Division to be indicative of negligence or misconduct. Details of our review are explained below.
Weapons Loss
The MAOP requires that each weapon loss must be referred to OPR. However we found that 32 weapons (20 percent) were not referred. Further, of the total 160 lost or stolen weapons OPR/Inspection Division opened an internal investigation into 70 (43 percent) of those losses. OPR/Inspection Division explained that it did not open an internal investigation for the remaining 90 losses for the following reasons:
22 losses did not receive requisite notification from field offices
58 had no evidence of employee misconduct that would warrant an internal investigation
10 were training weapons
Of the 70 weapon losses that resulted in an internal investigation the action taken was as follows:
43 resulted in suspensions of the responsible employees, ranging from 3 to 7 days,
17 resulted in no disciplinary action,
5 resulted in the employees receiving a Letter of Censure,
1 resulted in the employee being terminated, and
4 investigations were still pending.
We found it troubling that many of the weapon losses were not referred to OPR/Inspection Division for investigation even though the requirement in the MAOP clearly states that each weapon loss must be referred to OPR. As we previously mentioned, FBI officials told us that they do not investigate these losses because of insufficient information to indicate possible misconduct or negligence by an employee or the fact that the weapon was not specifically assigned to an employee.
Laptops Loss
The MAOP requires that each laptop loss must be referred to OPR. We found that 122 laptops (76 percent) were not referred. Further, of the total 160 lost or stolen laptops OPR/Inspection Division initiated an internal investigation into 21 (13 percent) of the losses. OPR/Inspection Division explained that it did not initiate an internal investigation for 139 losses because of the following reasons:
122 losses did not receive requisite notification from field offices
17 had no evidence of employee misconduct that would warrant an internal investigation
Of the 21 laptop losses that resulted in an internal investigation the action taken was as follows:
3 resulted in 3-day suspensions of the responsible employees,
11 resulted in no disciplinary action,
1 resulted in the employee receiving a Letter of Censure, and
6 investigations were still pending.
Similar to lost or stolen weapons, OPR/Inspection Division explained that cases are opened when there is sufficient evidence of an employee’s misconduct, and that cases were not opened if the lost or stolen laptop was not assigned to specific FBI personnel.68
We found it troubling that the overwhelming majority of laptop losses were not referred to OPR/Inspection Division for investigation even though the requirement in the MAOP clearly states that each laptop computer loss must be referred to OPR. As we previously mentioned, FBI officials told us that they do not investigate losses because of insufficient information to indicate possible misconduct or negligence by an employee or the fact that the laptop was not specifically assigned to a person.
Based on the relatively low number of investigations initiated, the FBI, in our judgment, has not been as diligent as it should be in investigating weapon and laptop losses.
Lack of Centralized Oversight and Monitoring
According to the MAOP, the Forms FD-500 are to be forwarded to the attention of the FBI’s PMO. The PMO is responsible for reviewing the details of lost and stolen items and requesting any additional information. In addition, the Accountable Property Manual states that the PMO’s duties include the overall administration, coordination and control of the FBI’s Property Management Program, including: (1) ensuring that adequate systems exist and are documented for accountability of property within the FBI: and (2) communicating and monitoring internal controls of the FBI for maintaining adequate property accountability.
The FBI’s response to lost and stolen weapons and laptop computers demonstrated several weaknesses that resulted in inadequate reporting of weapon and laptop losses within the FBI. When reports were submitted, there did not appear to be any type of review at the Asset Management Unit to ensure that necessary information and documentation was received. Also, there did not appear to be consistent treatment by the divisions and field offices in notifying proper headquarters units, such as the Security Division and the Inspection Division. These deficiencies could have been avoided had the FBI provided more diligent oversight and monitoring in addressing the weapon and laptop losses.
The Asset Management Unit officials explained that its responsibility is to track property as opposed to ensuring that all of the proper procedures are followed for reporting lost and stolen items. However, we found this understanding to be different from what the FBI’s Accountable Property Manual prescribes. We recommend that the FBI ensure that the Asset Management Unit provides oversight and monitoring for all weapon and laptop losses.
Our follow-up audit found decreases from our 2002 audit in the number of losses and the loss rates for weapons and laptops. However, while the number and rate of losses have declined overall, the amount is still significant, and we found that the FBI has not taken adequate corrective action on several recommendations outlined in our 2002 audit report.
For example, we found that many of the forms that were used to report losses were incomplete, and critical information such as the date of the loss, NCIC entry, and whether OPR was notified of the loss was not provided by the divisions or field offices. Also, we found that the Asset Management Unit was not able to find all Forms FD-500 related to the lost and stolen weapons and laptop computers. The FBI was unable to determine what was on many of the laptops. Even when some of the lost or stolen laptops were identified as containing sensitive or classified information, the Security Division examined few of these losses to determine the damage that these losses may have had on the FBI’s operations and national security.
Weapons and particularly laptop computers were not always being entered into NCIC. In addition, we found that weapon and laptop losses were not consistently referred to OPR/Inspection Division for investigation.
We recommend that the FBI:
Ensure that the Asset Management Unit maintains all Forms FD-500 with accompanying documentation and required information.
Ensure that the most current version of the Form FD-500 is used to report weapon and laptop losses.
Ensure that all Forms FD-500 that are submitted to the Asset Management Unit are complete, accurate and timely. Specifically, the FBI should ensure that the contents of the lost or stolen laptop computers accompany the Form FD-500.
Revise the Form FD-500 to include:
whether or not the loss was reported to the Inspection Division for investigation;
-
separate designation for “sensitive” and “classified” categories;
-
tracking of the classification level of NSI contained on a laptop;
-
whether sensitive information contained personally identifying information; and
whether the lost or stolen laptop computer was protected with encryption software.
Ensure that the Security Division performs a damage assessment of all laptops that are lost or stolen and maintains documentation on this information.
Ensure that weapon and laptop losses are appropriately entered into NCIC.
Assign to the Asset Management Unit monitoring responsibilities over weapon and laptop losses to ensure that all proper notifications are made.
- In our 2002 audit, we reported that the FBI failed to give sufficient priority to property management. Periodic inventories of accountable property were not conducted, departing employees did not always return all property that had been issued to them, and the destruction of outdated, damaged, or excessed laptop computers was not adequately documented. Additionally, while the FBI documented the disposal of laptop computers, it did not adequately document that all sensitive or classified information had been sanitized prior to their disposal. In our follow-up audit we noted improvements in the areas of conducting physical inventories and reconciling property records to the financial records. However, we identified continued weaknesses in several areas. Specifically, the FBI failed to adequately: (1) maintain records on how many of its laptop computers were authorized to process NSI; (2) improve its documentation of the disposal of excess laptop computers and hard drives to ensure that all sensitive or classified information had been sanitized prior to disposal; (3) report weapon and laptop losses to the DOJ; (4) submit incident reports of lost or stolen laptop computers to DOJCERT; and (5) improve the process to ensure that property is recovered from employees before they leave FBI service.
The DOJ Property Management Regulations requires all components to conduct an annual physical inventory of all non-expendable personal property. At the discretion of the component head, however, these inventories can be conducted every 2 years rather than annually.
The FBI’s regulations require an annual inventory of all sensitive capitalized assets and sensitive property items, which include weapons and laptop computers. The FBI is also required to conduct a full inventory of all property and equipment every 2 years.
In our 2002 audit report, we concluded that the FBI failed to give sufficient attention to property management. The FBI chronically failed to complete the required biennial physical inventories of accountable property. Therefore, we recommended that the FBI conduct biennial inventories of accountable property and implement a policy requiring annual inventories of sensitive items, such as weapons and laptops.
The FBI concurred with our recommendations and notified all of its divisions that, effective with the 2003 biennial inventory, completion of biennial inventories of all accountable property and annual inventories of sensitive items, including weapons and laptop computers, was required. The policy also stated that the inventory of weapons would include issued weapons as well as weapons stored in the gun vault.
During our follow-up audit, we reviewed FBI-wide inventory reports for the years 2003 through 2005. We noted that the FBI had completed biennial inventories of all accountable property and annual inventories of sensitive items, including weapons and laptop computers. We believe that this completion of regular inventories improved the FBI’s ability to account for and control its weapons and laptop computers.
Reconciling Property Records to the Financial System
In our 2002 audit report, we determined that the FBI’s financial system was not fully integrated with the PMA. As a result, the financial and property management systems did not automatically verify whether the number of items actually purchased agreed with the number of items placed into inventory. We recommended that the FBI implement a policy requiring that property records be reconciled with financial records to ensure the completeness of the FBI’s property records.
In response to this recommendation, the FBI stated that the Asset Management Unit and Contract Unit would coordinate to ensure that the PMA was updated manually to include purchases of non-capitalized property. Further, FBI divisions were instructed to generate and review on-order reports on a monthly basis to ensure that newly purchased property was added to the PMA.69 In addition, the Asset Management Unit generated delinquent on-order reports and distributed them to the appropriate APOs for follow-up.
In our follow-up review, we determined that the FBI’s financial system was still not fully integrated with the PMA, although all divisions currently have the capability to generate an on-order report. In addition, we verified that FBI divisions have been instructed to generate the report on a monthly basis to review newly purchased property that should be placed in the PMA. We also noted that the Asset Management Unit generates delinquent on-order reports and distributes all copies to the APOs for follow-up. A t the time of our follow-up review the FBI, in collaboration with the DOJ, was planning for future replacement of the Financial Management System and PMA systems with the implementation of the Unified Financial Management System (UFMS). The UFMS will replace financial systems DOJ-wide, integrating them with property management systems. T he FBI expects that it will begin implementing the UFMS in December 2006. However, the process will not be completed until October 2009 and the FBI is not projected to begin processing transactions in the UFMS until Fiscal Year 2010.
During our follow-up review, we judgmentally selected 10 disbursements for the purchase of weapons since February 1, 2002, traced all the purchases to the PMA, and noted no discrepancies. The disbursements related to the purchase of 455 weapons.
We also judgmentally selected 10 disbursements for the purchase of laptops since February 1, 2002, traced all the purchases to the PMA, and again noted no discrepancies. The disbursements related to the purchase of 108 laptops.
As a result of our follow-up review, we determined that the FBI had implemented a sufficient policy requiring that property records be reconciled to the financial records to ensure the property records are complete.
Accuracy and Completeness of Property Records in the PMA
In our 2002 audit, we performed two tests to determine the accuracy and completeness of the PMA. We judgmentally selected weapons and laptop computers from the PMA and physically verified their existence. We also judgmentally selected items that were physically located at selected field and headquarters offices and traced them to the PMA. In our 2002 audit the FBI was able to provide all weapons and laptop computers for our physical verification.
During our follow-up audit, we performed the same two tests to determine the accuracy and completeness of the PMA. First, we selected a random sample of 497 weapons and 477 laptop computers from the PMA and physically verified their existence. We evaluated property records and property management activities at FBI headquarters and offices in New York, New York; Los Angeles, California; Washington, D.C.; Chicago, Illinois; and Miami, Florida.70 We also tested the completeness of the property records by selecting a sample of 10 weapons and 10 laptop computers held at each of the field offices. We reviewed and traced them to the PMA and found no discrepancies.
To test the accuracy and completeness of the property records, we selected a sample of 974 items – 497 weapons and 477 laptop computers – recorded in the PMA and physically verified their existence. The FBI was able to provide all weapons and laptop computers for our physical verification, except for one weapon and two laptop computers assigned to FBI headquarters for which they provided confirmations of their existence. The following table summarizes our testing.
TOTAL SAMPLE ITEMS TESTED
WEAPONS TESTED AND VERIFIED |
LAPTOPS TESTED AND VERIFIED |
||||||||
| Location | PMA | FLOOR | PMA | FLOOR | |||||
|---|---|---|---|---|---|---|---|---|---|
| Tested | Verified | Tested | Verified | Tested | Verified | Tested | Verified | ||
FBI HQ |
260 |
260 |
10 |
10 |
348 |
348 |
10 |
10 |
|
New York |
69 |
69 |
10 |
10 |
42 |
42 |
10 |
10 |
|
Los Angeles |
55 |
55 |
10 |
10 |
29 |
29 |
10 |
10 |
|
Washington, D.C. |
44 |
44 |
10 |
10 |
24 |
24 |
10 |
10 |
|
Chicago |
36 |
36 |
10 |
10 |
16 |
16 |
10 |
10 |
|
Miami |
33 |
33 |
10 |
10 |
18 |
18 |
10 |
10 |
|
TOTALS |
497 |
497 |
60 |
60 |
477 |
477 |
60 |
60 |
|
| Source: OIG analysis of FBI PMA data |
In addition to selecting a sample to verify the accuracy and completeness of the property management records, we analyzed the universe of 52,263 weapons and 26,166 laptop computer recorded in PMA as of November 2005 to ensure that data was entered properly for each item, including a barcode number assigned by the FBI, the serial number, the cost center code for the office where the item is located, a description of the item, and other necessary information.71 For weapons, we found 260 cost center names and 39 serial numbers were blank. For computers, we found that 864 cost codes, 971 cost center names, 92 serial numbers and 38 model numbers were blank. There were also 10,424 laptop computers that were not assigned to FBI personnel. However, during our audit the FBI took corrective action to assign laptops to its personnel, and as of May 2006 the FBI had only 124 unassigned laptop computers.72
Reporting Requirements for Laptop Computers Containing NSI
In our 2002 audit, we reported that the FBI maintained records indicating which of its laptop computers were authorized to process classified information. Specifically, the FBI had a total of 10,003 laptop computers with the following security levels: 5 Top Secret; 8,000 Secret; 1,711 unclassified; and 287 miscellaneous (damaged, no hard drive, unusable). However, during our follow-up audit, FBI officials told us that they no longer maintained this type of information.
The DOJ’s Office of the Chief Information Officer (DOJ CIO) requires the FBI to report the number of laptop computers it has authorized for processing classified information. To ensure that the FBI complied with the requirement, during our follow-up audit we requested this information from the FBI and the DOJ CIO, but neither could provide it. FBI officials informed us that they did not track such information and the DOJ CIO confirmed that the FBI had not provided it to them. However, the DOJ CIO requested that the FBI provide a report containing the information by June 4, 2006.
Prior to DOJ’s CIO requests, the FBI deployed the PED Application to register all FBI electronic devices, including laptop computers. The PED Application draws baseline information from the FBI’s PMA and requires users to register their assigned devices and to indicate the security classification of each device. FBI officials told us that they are in the process of completing the registration for the FBI’s approximately 23,000 laptops. As of September 14, 2006, the FBI had provided information containing classification levels for 1,925 of its approximately 25,000 laptop computers.
Although the FBI deployed the PED Application to begin to track security classification levels in June 2006, the FBI did not maintain records indicating the classification of its laptop computers prior to the implementation of the PED.
DOJ Semiannual Theft Reports
DOJ regulations require all components to submit to DOJ semiannual reports summarizing thefts of government property that occurred within the preceding 6 months from January 1 and July 1. In our 2002 audit, we found that four of the five Semiannual Reports submitted by the FBI to the DOJ were submitted late, ranging from 6 to 106 days.73 In addition, the semiannual reports were inaccurate with respect to the number of weapon and laptop losses. We recommended that the FBI submit complete, accurate, and timely semiannual reports to the DOJ.
Our follow-up review found that the FBI has not corrected these deficiencies. The FBI did not submit a semiannual report for the period between January 1, 2002, and June 30, 2002. The overall period covered by the reports that we reviewed were submitted from July 1, 2002, through December 31, 2005. We reviewed the seven semiannual reports submitted by the FBI during the audit period and found all the reports to contain incomplete and inaccurate information. Although the reports listed the barcode numbers, descriptions, dollar values, and location of items, some reports did not contain the date of the incident. Further, when the reports asked whether corrective measures were taken to prevent repetition and the status of the actions taken, the answer was given as “unknown.”
During the period covered in our follow-up review, FBI records documented the loss or theft of 160 weapons and 160 laptop computers. However, in the semiannual reports the FBI reported to the DOJ only 106 lost and stolen weapons and 97 lost and stolen laptop computers, as shown in the table below.
ACCURACY OF FBI’S SEMIANNUAL REPORTS TO THE DOJ
| Semi- Annual Period Ended | Weapon Losses | Laptop Computer Losses | Total | |||
|---|---|---|---|---|---|---|
| Reported to DOJ | FBI Property Records | Reported to DOJ | FBI Property Records | Reported to DOJ | FBI Property Records | |
06/30/02 |
NA |
40 |
NA |
11 |
NA |
51 |
12/31/02 |
22 |
20 |
21 |
21 |
43 |
41 |
06/30/03 |
17 |
17 |
14 |
12 |
31 |
29 |
12/31/03 |
23 |
34 |
22 |
41 |
45 |
75 |
06/30/04 |
12 |
12 |
21 |
42 |
33 |
54 |
12/31/04 |
4 |
4 |
4 |
6 |
8 |
10 |
06/30/05 |
20 |
27 |
10 |
24 |
30 |
51 |
12/31/0574 |
8 |
6 |
5 |
3 |
13 |
9 |
TOTALS |
106 |
160 |
97 |
160 |
203 |
320 |
| Source: OIG analysis of FBI data |
Further, only 4 of the 10 laptop computers that were identified as having sensitive or classified information were reported to the DOJ. The remaining six were not reported. Only 30 of the 51 laptop computers that were unknown as to whether they contained sensitive or classified information were reported to the DOJ. In our judgment, the FBI has not adequately improved its procedures relating to the timely and accurate reporting of thefts of government property to the Justice Management Division, Facilities and Administrative Services Staff (FASS) DOJ Security Officer.
DOJCERT
DOJ regulations require all components to submit immediate reports summarizing incidents involving the loss of both classified and unclassified systems, to the Department of Justice Computer Emergency Response Team (DOJCERT). The DOJCERT assists in handling computer security incidents throughout DOJ.75
We contacted DOJCERT officials to determine if the FBI submitted the required incident reports for the 160 laptop computers that were identified as lost or stolen during our review period. We determined that of the 160 laptops that FBI reported as lost or stolen during the 44-month review period, it had only submitted 1 incident report to the DOJCERT. This incident report contained information regarding a laptop computer that contained sensitive information reported stolen by the FBI’s Criminal Justice Information Services (CJIS) Division on June 24, 2005. The FBI did not report any of the other lost or stolen laptop computers to the DOJCERT, including the other 9 that the FBI believed contained sensitive or classified information.
We asked the FBI’s Enterprise Security Operations Center (ESOC), the unit responsible for submitting incident reports summarizing computer losses, why only one incident was reported to the DOJCERT. In response, the ESOC officials stated that prior to an OMB memorandum, Reporting Incidents Involving Personally Identifiable Information and Incorporating the Cost for Security in Agency Information Technology Investments, dated July 12, 2006, the FBI was only responsible for submitting incidents to the DOJCERT that pertained to the loss of Personally Identifiable Information.76 However, as stated previously, as a result of our review we identified a stolen laptop containing the names, addresses and phone numbers of FBI personnel that was not reported to the DOJCERT. Further DOJCERT officials told us that the reporting of incidents involving the loss of both classified and unclassified systems to the DOJCERT has been a requirement since the inception of the United States Computer Emergency Readiness Team (US-CERT) in 2003.77
Disposal of Weapons and Laptop Computers
In our 2002 audit report, we found that the documentation for laptop disposals did not establish whether hard drives were properly destroyed and disposed of and were free of classified information. We recommended that the FBI improve the documentation showing that outdated, damaged, or excess laptop computers and hard drives were properly discarded.
In response to this recommendation, the FBI said it would implement an automated system for tracking information technology throughout its life cycle, including its disposal. Further, the FBI Security Division issued guidance in November 2003 governing the improved documentation of the destruction of excess laptops and hard drives. The guidance specifically addressed the clearing, sanitization and destruction of all media types, including computer hard drives.
However, the guidance does not specifically include the requirement for documenting that laptops and other media are properly discarded.
The MAOP requires that all computers that have processed sensitive or classified information be “sanitized and declassified” and sent to FBI headquarters for disposal. Field offices are required to initiate the disposal of excess laptop computers by entering a “Declaration of Excess” and an “Excess Property Detail Report” into the PMA as well as by submitting to the Asset Management Unit a Form FD-519 (Requirements and Certification for Cannibalization and Destruction of Equipment).
During our follow-up audit at FBI headquarters, we obtained Forms FD-519 that included laptop computers, which were disposed of between February 1, 2002, and September 30, 2005. We selected a judgmental sample of ten laptop computers from the Forms FD-519 and traced them to the PMA, confirming that the PMA accurately showed the excess laptops as disposed.
At the five field offices we visited, the available documentation pertaining to hard drives from excessed laptops did not indicate that the field offices removed hard drives and sent them to FBI headquarters for disposal. The available documentation that we examined also did not include evidence of whether any classified information had been sanitized. Further, we found evidence at the Los Angeles Field Office and the New York Field Office that some laptop computers had been destroyed, but there was no documentation to show that the hard drives were removed and forwarded to FBI headquarters. We were told that all hard drives from Los Angeles and New York were degaussed and destroyed at the field office instead of being forwarded to FBI headquarters.78 The New York Field Office received degaussing equipment in June 2006; however, it had not forwarded hard drives to FBI Headquarters for more than 2 years. Records at FBI headquarters also did not sufficiently document that hard drives from field offices were received and properly destroyed. Specifically, the records did not include names of employees, the reason for destruction, and the location and method of destruction, as required. Further, the FBI policy states that t he destruction of Top Secret and Sensitive Compartmented Information (SCI) must be witnessed and recorded by two employees with security clearances commensurate with the classification of the material being destroyed. We cannot be certain that the FBI followed the policy since we could not determine if any of the hard drives that were destroyed contained Top Secret or SCI information.
In sum, despite our prior recommendation, the FBI did not document that specific computers had been “sanitized and declassified” before being disposed. Officials at each of those locations told us they believed that excess laptop computers and hard drives had been properly discarded. However, they could not provide evidence that proper procedures were followed. We again recommend that the FBI document the completion of all required steps for disposing of excess laptop computers and hard drives that previously processed sensitive or classified information.
Exit Procedures for Departing Employees
In our 2002 audit report, we found indications that the FBI was not recovering all issued weapons and laptops from employees before their departure. We recommended that the FBI strengthen procedures to ensure departing employees return all property issued to them or reimburse the government. In response to the recommendation, the FBI revised its policy and distributed an electronic communication to all employees who were leaving, notifying them that they could be held accountable for lost or stolen FBI property.
The process for departing FBI employees includes an exit interview with the employee’s supervisor and completion of certain forms. FBI procedures call for the supervisor to review the PMA printout and recover all issued property listed on that document. In addition, the supervisor should complete a Report of Exit and Separation (Form FD-193) and a Receipt for Government Property (Form FD-281). The Form FD-281 is used for both receiving and returning government property. The Form FD-193 documents a variety of actions that must be completed upon an employee’s departure.
During our follow-up review, we judgmentally selected the files of 50 former employees and the Forms FD-281 and FD-193 for both weapons and laptops issued to each of the 50 employees. We asked for these documents at both the FBI Records Management Division and at each of the field offices that we reviewed. However, the FBI could provide only 19 of the required 50 Forms FD-281 for weapons and laptop computers, and only 32 of the 50 Forms FD-193.
The following table shows the number of Forms FD-281 and the Forms FD-193 reviewed for the five field offices.
TOTAL FORMS FD-281 AND FD-193 REVIEWED
FEBRUARY 1, 2002, THROUGH SEPTEMBER 30, 2005
| New York | Los Angeles | Washington D.C. | Chicago | Miami | TOTALS | |
|---|---|---|---|---|---|---|
FD-281 |
3 |
10 |
2 |
0 |
2 |
17 |
FD-281 |
0 |
2 |
0 |
0 |
0 |
2 |
FD-193 |
10 |
6 |
5 |
6 |
5 |
32 |
| Source: OIG analysis of FBI data |
Based on our review of the 160 weapon losses, we concluded that four of the lost or stolen weapons were the result of an agent leaving the FBI and not returning a weapon. In our judgment, the FBI has not sufficiently strengthened its exit processing for departing employees to obtain all weapons.
The FBI also revised its policy to require that all laptop computers issued to an individual be documented on a Form FD-281. The forms should be signed by the individual with custody of the property and maintained at the division office. We did not find any cases that resulted in an agent leaving the FBI and not returning a laptop.
In sum, although the FBI revised its policy to strengthen procedures to ensure that departing employees return all property that had been issued to them or reimburse the government for the cost of the property, we noted that the policy is not being followed consistently.
In response to our August 2002 audit, the FBI has taken steps to address weaknesses in physical inventories and reconciling weapons and laptop computers to the financial system. However, we identified continuing weaknesses in several areas. Specifically, the FBI failed to adequately: (1) maintain records on how many of its laptop computers were authorized to process NSI; (2) improve its documentation of the disposal of excess laptop computers and hard drives to ensure that all sensitive or classified information had been sanitized prior to disposal; (3) report weapon and laptop losses to the DOJ; and (4) ensure that property is recovered from employees before they leave FBI service. Therefore, we make several recommendations for the FBI to improve its management of weapons and laptop computers.
We recommend that the FBI:
-
Maintain and submit complete, accurate, and timely reports to the DOJ CIO containing all appropriate FBI laptops authorized to process classified information.
Improve the documentation supporting the destruction of excess laptop computers and hard drives.
Revise its guidance regarding when field offices can degauss their own hard drives.
Submit complete, accurate, and timely Semiannual Reports to the DOJ Security Officer JMD, FASS.
Submit complete, accurate, and timely incident reports summarizing the loss of appropriate FBI laptop computers to the DOJCERT, as required.
Strengthen the exit processing for departing employees to ensure that all weapons, laptops, and other issued property is returned to the FBI.
Because the audit periods were different lengths, we analyzed the rate of loss on a monthly basis.
Our review period for the 2002 audit covered 28 months, from October 1, 1999, to January 31, 2002. Our review period for our follow-up audit covered 44 months, from February 1, 2002, to September 30, 2005.
The FBI objected to the inclusion of 43 of these 160 weapons because while they were reported as lost or stolen during our 44 month follow-up period, the loss actually occurred before our follow-up period. We did not delete these weapons from the table because: (1) the losses were not categorized as such in the FBI's official property management system until after the beginning of our follow-up period, (2) our approach in the follow-up audit was consistent with our approach in the 2002 audit, which also included weapons that were reported as lost or stolen during our review period, (3) none of these 43 weapons were included in the 354 lost or stolen weapons reported in the 2002 audit, (4) to delete them would give the appearance that the FBI had 43 fewer lost or stolen weapons than was actually the case.
As we explain in Finding II, the FBI did not maintain records indicating which of its laptop computers were authorized to process National Security Information.
These weapons were lost under a variety of circumstances. For example, one weapon was stolen from a rental car. Another was stolen from a Special Agent’s desk drawer at a field office.
These laptop computers were stolen under a variety of circumstances. For example, one laptop was stolen from a hotel room. Another was stolen from a Special Agent’s privately owned vehicle.
Since the issuance of our initial audit report in 2002, the FBI reorganized OPR and the Inspection Division. In February 2004, the FBI transferred the responsibility for investigations of alleged employee misconduct from OPR to the Inspection Division. The OPR continues to be responsible for adjudicating disciplinary matters.
The Form FD-500 was updated on July 24, 2002, to include new fields. An additional 47 FD-500’s submitted prior to July 24, 2002 did not contain critical information such as the date of loss, NCIC entry, and whether OPR was notified.
An additional 21 Forms FD-500 that were submitted prior to July 24, 2002 did not contain critical information such as the date of loss, NCIC entry, and whether OPR was notified.
In addition to the 43 laptop losses for which the Forms FD-500 were not marked to indicate whether the laptops contained or did not contain sensitive or classified information, there were 8 laptop losses for which the Property Management Unit did not retain the Forms FD-500 and had no information on whether these laptops contained or did not contain sensitive or classified information. Therefore, we combined these 8 laptop losses to the 43 and discuss the FBI’s response to these losses in more detail later in our report in the 51 Laptop Losses section.
The Form FD-500 for the laptop loss from the Boston Field Office was marked to indicate that it did not contain sensitive/classified information and that it did contain sensitive/classified information. Because both answers are mutually exclusive and the description of the contents was consistent to information that can be considered sensitive/classified, we considered this laptop as containing sensitive/classified information.
The Forms FD-500 for these laptop losses indicated that the corresponding laptops did not contain sensitive or classified information. However, according to subsequent information that we obtained from the Security Division’s Security Compliance Unit (SCU), the SCU concluded that the laptops contained sensitive but unclassified information.
The laptop computer that was reported as being stolen from the Criminal Justice Information Services (CJIS) Division was also the only laptop computer reported to DOJCERT.
The CJIS Division laptop loss was also included as one of the 12 laptop losses that the Security Division reviewed. Of the 12 laptop losses that the Security Division examined, only 3 were identified as containing sensitive information. Five of the 12 laptops were determined by the Security Division to not contain sensitive or classified information and for the remaining 4; the Security Division did not know whether the laptops contained any sensitive or classified information.
According to the FBI Security Handbook, sensitive information is information that, if disclosed, could adversely affect the ability of the FBI to accomplish its mission. Examples of sensitive information might be the identity of undercover agents, names of people under investigation, tax return information, or personal data on individuals. Classified information (National Security Information) is information that has been determined pursuant to Executive Order 12958 or any predecessor order to require protection against unauthorized disclosure and is marked to indicate its classified status when in documentary form. For further details on the classification levels of Classified National Security Information see Appendix XVII.
OPR investigated laptop losses that are referred to in the above table as numbers 2, 3, 4, 8, and 9.
See Appendix IV for a detailed description of the disciplinary action taken relating to the 160 FBI laptops that we identified in our follow-up audit as being lost or stolen.
Eight of the 22 laptops that were not assigned to an employee and for which the loss was unexplained did not have Forms FD-500.
Personally Identifiable Information is any information about an individual maintained by an agency, including, but not limited to, education, financial transactions, medical history, and criminal or employment history and information which can be used to distinguish or trace an individual's identity, such as their name, social security number, date and place of birth, mother’s maiden name, biometric records, etc., including any other personal information which is linked or linkable to an individual.
The FBI deployed the Portable Electronic Device (PED) Application to register all FBI electronic devices, including laptop computers. The PED Application draws baseline information from the FBI’s PMA and requires users to register their assigned devices and to indicate the security classification of each device.
In our prior audit, we did not determine whether lost or stolen laptop computers were entered into NCIC because there was no requirement at the time to enter lost or stolen laptop computers into the NCIC.
An NCIC number is a unique record number that is assigned to an entry made into NCIC.
Two weapons were claimed to have been found and therefore not entered into NCIC. However PMA continued to show these weapons as being lost or stolen and the FBI did not provide evidence that these weapons were found. One weapon was inoperable and disabled, although the FBI did not provide evidence of this.
Of the 160 weapon losses, 11 were reported lost and 35 were reported stolen after February 2004. Of the 160 laptop losses, 42 were reported lost and 16 were reported stolen after February 2004.
Of the 160 lost and stolen laptop computers, the FBI did not know whether 51 of these laptops had sensitive or classified information. Of the 51, 37 were lost, 6 were stolen, and the remaining 8 had no Forms FD-500 describing the loss as being either lost or stolen; therefore, we included the 8 in the lost category. Also, of the 51, 11 were referred to OPR/Inspection Division and from these 11 losses, 9 were investigated by OPR/Inspection Division; for the remaining two, OPR/Inspection Division lacked sufficient information to open an internal investigation.
-
When we began our follow-up audit, there were over 10,000 laptops that were not specifically assigned to FBI personnel. All laptop computers are required to be charged out in the PMA and assigned to individuals in an effort to strengthen accountability and minimize unexplained losses. We found that as of March 2006, 37 percent of the FBI’s laptop computers had not been recorded as being assigned to individuals. However, after we inquired about this issue in March 2006, the FBI made a significant effort to assign the laptop computers to specific individuals. Therefore, as of May 2006 less than 1 percent of the FBI’s laptop computers were not assigned to individuals.
An on-order report reflects capitalized and non-capitalized property valued at $1,000 and above, and also sensitive property that should be entered into the PMA.
The universe of weapons and laptop computers for each audited location and details of our sample, by property type, location, and type of test, appear in Appendix II.
The PMA uses a variety of data fields to identify each item, including a barcode number assigned by the FBI, serial number, cost center code for the office where the item is located, description of the item, and other necessary information.
See Appendix X for an analysis of the FBI’s property records.
DOJ Semiannual Reports should contain the following information: description, indicating if government or personal property; serial number, if any; dollar value; date and location of incident; results of any investigation conducted by the appropriate agency; and any corrective measures taken to prevent repetition. Loss or theft of ADP equipment shall also include the following: a copy of the Federal Protective Service or other investigative report; and a statement from the owner or user of the ADP equipment categorizing the information as NSI, sensitive information or non-sensitive information.
The DOJ Semiannual Report ending December 31, 2005, contained information relating to lost or stolen weapons and laptop computers that occurred during the audit period ending September 30, 2005. Our analysis did not include losses that occurred after September 30, 2005.
According to the DOJCERT, computer security incidents are any unexpected, unplanned event that could have a negative impact on IT resources. Computer security incidents can include the loss of both classified and unclassified systems, unauthorized removal of computer equipment, and exploited weaknesses in a computer system that allows unauthorized access to password files.
Personally Identifiable Information is any information about an individual maintained by an agency, including, but not limited to, education, financial transactions, medical history, and criminal or employment history and information which can be used to distinguish or trace an individual's identity, such as their name, social security number, date and place of birth, mother’s maiden name, biometric records, including any other personal information which is linked or linkable to an individual.
The United States Computer Emergency Readiness Team (US-CERT) is a partnership between the Department of Homeland Security and the public and private sectors. Established in 2003 to protect the nation's Internet infrastructure, US-CERT coordinates defense against and responses to cyber attacks across the nation.
Degaussing is the process of erasing data that is stored in magnetic media, such as hard drives, floppy disks and magnetic tape, thereby rendering previous data unrecoverable.