After accomplishing the initial objective of developing and implementing a consolidated watch list database, the TSC has moved into a new phase of its operations. The TSC has established an operating structure and new procedures for its call center. The physical size and activity of the TSC call center has experienced significant growth, and management has implemented procedures for nominating individuals for inclusion in the database, as well as for removing persons from the watch list. Further, the TSC has undertaken measures to increase information sharing and outreach. However, we identified areas in need of improvement; including weaknesses in staffing and the need for enhanced controls over the receipt, acceptance, and accuracy of incoming data.
As of April 2005, the TSC was divided into three major branches: Information Technology, Operations, and Administration. The Information Technology (IT) Branch, headed by a Chief Information Officer (CIO) appointed in August 2004, oversees IT planning and systems architecture, including the design, maintenance, and modification of the TSDB that houses the consolidated watch list information. The Administration Branch handles personnel matters, security and guard services, budgetary issues, and logistics and physical space. The Operations Branch houses the TSCís 24 hour, 7 day a week call center and the Nominations Group, which is responsible for additions, deletions, and modifications to the consolidated watch list.43 This Branch also handles inquiries, complaints, and comments from the law enforcement community. The Tactical Analysis Group, which is also part of the Operations Branch, performs analysis on encounters with potential terrorists to identify useable intelligence and forwards the information to the necessary parties as rapidly as possible. The general structure of the TSC is illustrated on the following organizational chart.
| Terrorist Screening Center Organization |

|
| Source: TSC Draft Organizational Chart as of April 2005 |
Because the TSC is a multi-agency effort, personnel from the DOJ, the DOS, the DHS, the Department of Defense (DOD), and the United States Postal Service (USPS), along with various contractors staff all three branches. The September 2003 MOU executed in response to HSPD 6 required that the Principal Deputy of the TSC be a DHS employee. Neither the MOU nor any formal TSC protocols require other leadership roles, such as Branch or Unit management positions, to include representation from the various participating agencies.
Since its inception, the TSC Director has worked with the heads of the participating agencies to establish the TSCís staffing level and determine the number of detailees from each agency. For fiscal year (FY) 2004, the expected number of personnel at the TSC was 157. As of November 9, 2004, a total of 177 staff were on board. The expectations are compared to the staff on board in the following exhibit.44
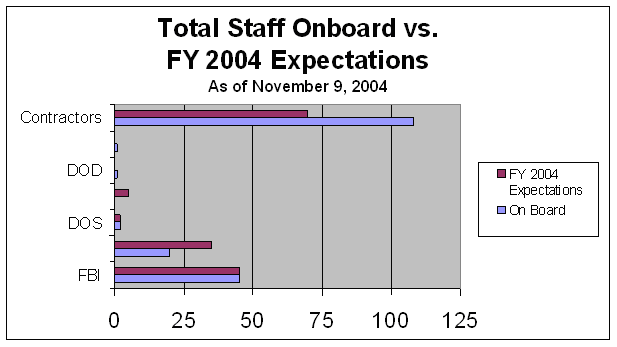
| Source: TSC Administrative Unit |
By the beginning of November 2004, DHS contributions fell 10 staff short of expectations. According to the TSC Director, she has repeatedly asked the DHS to provide additional employees, without success. To make up for the shortfall from the DHS, the TSC hired additional contractors, and as of November 9, 2004, more than half of the TSC personnel (108 of 177 total staff, or 61 percent) were contractors. The FBI is the next largest provider of TSC personnel, with about a quarter of the staff in the organization.
Participating agencies have also provided staff on a Temporary Duty (TDY) basis, with details of 60 to 90 days. In addition, these organizations loaned existing contractors to the TSC, some of whom have since become TSC-paid contractors. A total of 73 percent of the staff on board as of November 2004 were permanent TSC employees or contractors hired by the TSC. This staffing breakdown is displayed in the following table.
| TSC STAFFING INFORMATION AS OF NOVEMBER 9, 2004 |
|||
|---|---|---|---|
| SOURCE | NUMBER TDY/LOAN |
NUMBER PERMANENT TSC |
TOTAL |
| FBI | 21 | 24 | 45 |
| DHS | 13 | 7 | 20 |
| DOD | 1 | 0 | 1 |
| DOS | 1 | 1 | 2 |
| USPS | 0 | 1 | 1 |
| Contract45 | 12 | 96 | 108 |
| TOTAL | 48 | 129 | 177 |
| Source: TSC Administrative Unit |
The rotating nature of much of the TSCís staff and the large percentage of contract employees has impacted the TSCís development. For example, the TSC lacks historical knowledge of its own organization. Only one individual, a contractor that was originally on loan from the FBI but whose contract has since been assumed by the TSC, has been with the organization since its creation in September 2003. Only about five additional individuals currently on staff with the TSC were at the organization during its planning phase, including the Director and two of the Deputy Directors. In addition, short TDY periods force the TSC to continually train and orient new personnel.46
The TSC was created outside the normal budget process. As a result, no government staff positions were granted to the TSC by the Office of Management and Budget (OMB), and funding for FY 2004 was derived from the Departments of Homeland Security, Justice, and State, as well as NCTC. The FY 2004 OMB allocations for each of these agencies are detailed in the following chart.
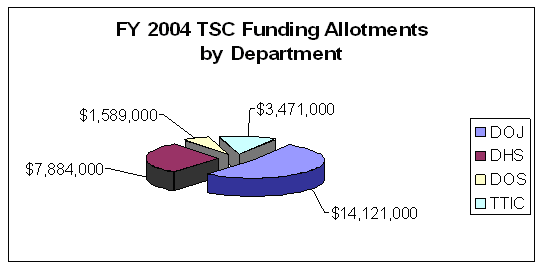
| Source: FBI Budget Formulation Office and the TSC Administrative Unit |
According to the OMB allocations, the TSCís FY 2004 budget was set at about $27 million. As of September 30, 2004, participating agencies had contributed a total of $27.5 million to the TSC. While the DHS and DOS both contributed the full amount specified by the OMB, NCTCís contribution of $3 million was $471,000 short of its FY 2004 allocation. The FBI provided $15 million to the TSC in FY 2004, almost twice as much as any other participating agency and $879,000 more than the OMB requirement. The following table distinguishes between the amount of funding allotted and the amount provided from each agency for FY 2004.
| DEPARTMENT | DOJ/FBI | DHS | DOS | NCTC | TOTAL |
|---|---|---|---|---|---|
| Alloted | $14,121,000 | $7,884,000 | $1,589,000 | $3,471,000 | $27,065,000 |
| Provided | $15,000,000 | $7,884,000 | $1,589,000 | $3,000,000 | $27,473,000 |
| Source: TSC Administrative Unit |
According to TSC management, the FY 2004 funding figures were based on conservative estimates of initial operating capability and did not represent a baseline estimate of future TSC needs. Further, the approved FY 2005 budget was $29 million and TSC officials assert that this amount is below normal operating requirements.47 The TSC has estimated that the total resources required to accomplish the activities outlined in HSPD-6 and the resulting MOU amount to $50 million in funding and a staff size of 267. The TSC also analyzed the resources needed to meet the requirements of new initiatives that would affect the TSCís mission beginning in late FY 2005. According to this analysis, TSC officials believe that the organization will need an initial budget of $142 million and 455 personnel, with recurring costs of $118 million each successive fiscal year. As of April 2005, Congress was considering an OMB-approved $40 million supplemental appropriation request for FY 2005.
As noted in Chapter 4, on December 1, 2003, the TSC initiated operations in its call center, providing law enforcement agencies with around-the-clock access to consolidated information regarding known or suspected terrorists. The basic tasks performed by call center staff Ė namely fielding inquiries, researching terrorist information, and facilitating the identification and apprehension of terrorists Ė remains the same as the functions performed at the point of initial operating capability. However, the creation of the consolidated watch list has allowed TSC screening staff to begin all research with a single database Ė the TSDB. The general process flow of activity surrounding a possible hit against the TSDB is summarized in the following exhibit.
| CALL SCREENING PROCESS FLOW |
|---|
[Not Available Electronically]
|
| Source: The Terrorist Screening Center |
The first step in the process when a person is encountered domestically or at the border is that the identity of an individual is searched in a law enforcement system such as NCIC or the Interagency Border Inspection System (IBIS). For example, an individual stopped by a police officer for speeding will be queried in NCIC, or an individual attempting to enter the United States at a border crossing is queried in IBIS. Although law enforcement officials cannot connect directly to the TSDB, the TSC exports the consolidated watch list records to all supporting agency databases eligible to receive the information. If the queried identity appears to match a record in the TSDB, the law enforcement official receives a response to contact the TSC.48 When the inquiry is received by the TSC, call center staff assist in determining if the encountered individual positively matches the identity of a known or suspected terrorist on the consolidated watch list. First, the screeners search the TSDB to obtain all basic identifying information available. Then, the screeners search supporting agency databases to locate any additional information that may assist in making an identification or provide further detail about the subject, some of which may be classified. For all calls received, the call screeners record details about the inquiry on a Call Intake Form. If the TSC call screener determines that the encountered individual does not match the identity of an individual on the watch list, the caller is immediately informed of the negative results.
If the subject is positively identified or the match attempt is inconclusive, the TSC call screener forwards the Call Intake Form, via facsimile, to the FBIís CT Watch. CT Watch is then responsible for coordinating the law enforcement response to the encounter, including making further attempts to establish positive identity and, if necessary, deploying agents to take appropriate action.
For every inquiry that TSC call screeners refer to CT Watch, the screeners are responsible for obtaining information on the disposition of the encounter, such as whether or not the subject was arrested, questioned, or denied entry into the United States. This information is recorded into an internal TSC database.49
In addition to domestic or border encounters, the TSC is involved when foreign individuals apply for a United States visa. According to State Department officials at the TSC, when a person overseas applies for a visa, U.S. government officials search the CLASS database, which receives watch list information from the TSC. If this search reveals a possible identity match with an individual recorded in the TSDB, the official will send the TSC a cable (a secure, electronic communication). A State Department representative at the TSC will review the cable along with information within supporting agency databases to determine if the person requesting a visa is an individual with ties to terrorism. This information will be used by the U.S. government officials overseas to either issue or deny the visa application.50
One way to illustrate the development and maturation of the TSC is to examine the increase in activity at its call center. The TSC generates weekly statistical reports detailing the total number of calls received, the origin (e.g., state or local law enforcement or border patrol), the result of the identity determination (i.e., positive, negative, or inconclusive match), the disposition (e.g., arrested or questioned and released). At times during our audit, the reported data contained small mathematical errors. While the reports are now mathematically correct, we believe the TSC should establish controls to ensure that its call data is checked regularly for accuracy.
Based on TSC weekly call reports, as of January 23, 2005, TSC call screeners had responded to 18,534 inquiries from federal, state, and local agencies regarding encounters with known or suspected terrorists. Of these inquiries, the TSC determined in 9,510 instances (51 percent) that the individual encountered was an individual of interest.
As shown in the following charts, at the start of its call center operations in December 2003, the TSC received approximately 8 to 11 calls per day. For the month of January 2005, the TSCís call volume had reached an average of 85 calls per day. The percentage of calls resulting in a positive identification match was 43 percent for the period of December 2003 through January 2005.
| TSC CALL VOLUME For the Period December 1, 2003, through January 23, 2005 |
|---|
[Not Available Electronically]
|
| Source: TSC Management |
This 965 percent growth in call volume from December 2003 to January 2005 is attributable, in part, to the TSCís successful communication and outreach to the law enforcement and intelligence communities. This increase in call volume has been accompanied by an increase in actual positive identity matches. According to the TSC, this increase indicates that the quality and dissemination of information has improved. TSC staff is also aware that major events with national security implications, such as the presidential inauguration, stimulate an increase in call center activity. The breakdown of the identity determinations resulting from calls to the TSC call center is displayed in the following chart.
| TSC CALLS - IDENTITY DETERMINATIONS For the Period December 1, 2003, through January 23, 2005 |
|---|
[Not Available Electronically]
|
| Source: TSC Management |
When a law enforcement or intelligence agency has identified an individual as a potential terrorist threat to the United States and wants the individual to be added to the consolidated watch list, that person must be "nominated" for inclusion in the TSDB.51 Nominations occur in two ways Ėindividuals may be added through the Routine Nomination Process, or they may be deemed an immediate threat that requires use of the Emergency/Expedited Nomination Process. The Routine Nomination Process, the most common of the two nomination methods, involves the submission of international or domestic terrorist-related names by government agents to either NCTC or the Terrorist Watch and Warning Unit (TWWU) at the FBI. Staff members review the information and decide whether or not the person is an appropriate candidate for inclusion on the TSCís watch list and whether or not sufficient identifying information is available. If so, the information is forwarded to the TSC for inclusion in the consolidated database.
The Emergency Nomination Process is used when there is an imminent threat and a watch list record needs to be quickly created or highlighted. When an imminent threat exists, the requesting agency informs the TSC directly and TSC staff create a record in the TSDB and all supporting databases. If the threat contains a nexus to international terrorism, the TSC creates additional files of all the information gathered on the subject for submission to NCTC and subsequent creation of a record in the TIPOFF system.
At the time of our review, the TSC process for including a name in the TSDB was more of an acceptance than nomination. TSC staff did not review the majority of the records submitted unless an automated error occurred while the records were uploaded to the database. While we recognize that the ultimate decision for nomination into the consolidated database should be done by analysts who have access to originating documentation, the TSC needs to ensure that the information that is placed into the TSDB accurately represents the data that was submitted by the nominating agency. In addition, the TSC should establish controls to ensure that it can trace the origin of the record to the agency that nominated it. When comparing TSDB records to the source information, we identified differences for which the TSC could not provide an adequate explanation. Our testing of the accuracy and completeness of database records is contained in Chapter 7.
To gain a better understanding of the nomination process, we met with the Chief of the Nominations Unit in July 2004 and walked through the process of uploading the daily nominated records into the TSDB. As part of that process, we found that the TSC was using an unclassified, stand-alone system on which to conduct a "dirty word search," that is, a search that seeks to identify classified information within the file and presents it for deletion prior to uploading the file into the unclassified TSDB. This process presents a dilemma if classified information is found on the file because the presence of any classified information on what is supposed to be an unclassified system would result in security issues. Based on our identification of this weakness and subsequent discussions with the CIO, the TSC officially changed the designation of the stand-alone system from unclassified to classified in September 2004.
In addition, we initially found no formal back up plan for receiving daily nominations and uploading these records into the TSDB. On at least one occasion, the two individuals responsible for performing the upload of records from NCTC and the FBI were both out of the office, and as a result no records were uploaded that day. This type of situation leaves the database vulnerable to omissions and the screeners with potentially outdated and incomplete information. After we identified this problem, the TSC informed us that it had established a back-up plan under which the responsibilities will be shared by five employees. However, as of November 15, 2004, the TSC had not formalized this plan in writing. As mentioned previously, enhancing the database to automate the daily upload of records nominated for inclusion in the TSDB would avoid the need to rely on such human intervention.
Removal of Names from the Watch Lists
The TSC removes names from the consolidated database and as of October 2004, 3,673 records had been removed from TSDB 1B since its creation in June 2004. Like the nomination process, there are two ways in which these removals are processed, referred to by the TSC as automatic removals and specific removals. Specific removals occur through quality assurance processes and as the result of misidentifications; these are discussed in further detail in Chapter 8. Automatic removals occur when the TSC receives an automated prompt from a supporting system of a participating agency, as described below.
When an international terrorist record is to be removed from the TSDB, the TSC will accept an electronic indicator to delete the record from the daily update file sent by NCTC.52 When the TSC exports an update file from the TSDB to the participating agencies, the supporting systems that contained the subject record receive a deletion indicator as well, thereby removing the record from all supporting databases.
For example, as shown by the red arrow in the following screen print, the TSDB 1B main screen displays a box next to each database that receives exports of information from the TSC. On each record, these boxes are marked with a "Y" (yes) or "N" (no) depending on whether the database is approved to receive the record. If one of the boxes is left blank, the database defaults to "N." When a source agency such as NCTC deletes a record, it sends the record marked for deletion to the TSC where staff members delete the record from the TSDB. During the daily export of records to participating agencies, the TSDB sends the same type of deletion prompt to the agency databases marked "Y" for receipt of the particular record, thereby removing the record from all supporting databases.
[SENSITIVE INFORMATION REDACTED]
|
| Source: TSC Nominations Unit |
Similar to its role in the nomination process, the TSC does not analyze these deletion requests and relies on the supporting agencies to conduct the necessary analysis that would lead to record deletion. As the owners of the data, the supporting agencies are responsible for making decisions regarding the appropriateness of an individual being watch listed.
When a domestic terrorist record needs to be removed from the TSC database, the appropriate FBI field office sends the TWWU a form that must be completed for any new submissions, provision of supplemental information, or removal requests on persons of a terrorist threat. When the form is received by the TWWU, it is reviewed for completeness and appropriate action. If complete, the form is forwarded to the TSC for removal of the record from the TSDB and all supporting systems.
Foreign Government Information Sharing
Another important aspect of the TSCís operations is the sharing of appropriate information with foreign governments. According to the September 16, 2003, MOU that was signed by the participating agencies to create the TSC and outline its core requirements, the parties were required, to the extent permitted by law, to provide appropriate information about suspected terrorists to foreign governments that cooperate with the United States. [SENSITIVE INFORMATION REDACTED]
Outreach to Additional Departments/Agencies
The TSC represents a new approach to information sharing and coordination among law enforcement, the intelligence community, and international agencies by offering one central point where all known terrorist-related information can be reviewed against the information of an encountered individual. To enhance the effectiveness of the governmentís efforts for terrorist screening, the TSC communicates with law enforcement agencies in many ways, including: 1) informing law enforcement personnel of the mission, role, and functions of the TSC; 2) educating law enforcement personnel on techniques for handling encountered individuals; and 3) promoting awareness that front-line law enforcement officers often have opportunities for gathering information that may be useful in on-going cases.
The TSC has established an outreach program that targets federal departments and agencies, informing them of the TSCís mission and determining what agency-specific opportunities exist for screening appropriate individuals against the TSCís consolidated watch list. In addition, TSC officials have attended numerous Chiefs of Police conferences and intelligence community gatherings, established booths at the federal law enforcement training center in Quantico, Virginia, and made presentations about its operations to state and local law enforcement agencies. TSC officials informed us that, from December 1, 2003, through June 30, 2004, they briefed approximately 2,000 people in 11 states and the District of Columbia on the efforts and usefulness of the TSC.
TSC officials said they also are working to identify specific organizations and industries that need to be informed of the TSCís role and functions. Officials also said that they have established a plan that includes creation of a website to provide basic information about the agency and the purpose of the consolidated database. Yet, based on our review of the TSCís outreach program, we believe the TSC should develop a more vigorous plan to target and prioritize specific organizations and industries, and establish a timeline to complete these outreach goals. We also believe that any outreach plan should be incorporated into the TSCís strategic plan, once the strategic plan is formally developed.
Private-Sector Information Sharing
According to HPSD 6, the DHS was charged with developing guidelines "to govern the use of such information to support state, local, territorial, and tribal screening processes, and private sector screening processes that have a substantial bearing on homeland security." The TSC has developed procedures for supporting state, local, territorial, and tribal screening processes using the data contained within the TSC. However, as of October 2004, the DHS had not developed guidelines for private-sector screening or sharing of information.
In a drafted report to Congress dated October 2004, the TSC indicated that regular private-sector screening is anticipated in the future because DHS was finalizing a plan to screen individuals at certain private high-risk infrastructure facilities, such as hazardous material drivers.53 DHS personnel assigned to the TSC are expected to perform the private-sector screening, but they will not be permitted to directly release identifying information to private organizations. However, as of October 29, 2004, DHS officials had not developed a formal plan for how this would be accomplished.
As a developing organization, the TSC has spent significant time establishing and implementing basic operating procedures. However, as exhibited by the activity in the TSC call center, the use of the TSC and its resources is expanding and management must take action to improve processes in certain areas. For example, the TSC needs to create formal plans for automating the daily upload of records to the TSDB and for implementing the DHSís system for private-sector screening. In addition, the TSC should address staffing issues, including the heavy reliance on contractors and short-term temporary staff.
We recommend that the TSC:
- Develop staffing protocols to ensure that the TSC remains a multi-agency operation and make further efforts to encourage DHS to provide additional staff.
- Take steps to increase the number of permanent government personnel and long-term TDY staff employed by the TSC to take advantage of valuable expertise and institutional knowledge and to reduce the necessity of constant orientation and training.
- Ensure that the information placed into the TSDB accurately represents the data that was submitted by the nominating agency. In addition, the TSC should establish controls to ensure that it can trace the origin of the record to the nominating agency.
- Take measures to automate the daily upload of records nominated for inclusion in the TSDB to reduce the need for human intervention.
- Develop a more vigorous outreach plan that includes specific target organizations and industries, and establish timelines for the completion of outreach goals. Incorporate the plan into the TSC strategic plan, when formally created.
- Encourage the DHS to finalize guidelines to allow the TSC to begin regular screening for private sector organizations.
Footnotes
- The nomination process is discussed in further detail later in this chapter.
- We could not compare staffing numbers and expectations for different points in time because the TSC did not track the actual staffing levels. As a result, we compared available information, consisting of the FY 2004 expectations and the November 9, 2004, actual staffing levels. As of March 2005, the FY 2005 expectations had not been finalized.
- The number of contract personnel in the column labeled "Number Permanent TSC" are contractors that are not on loan from other agencies, but instead are paid directly by the TSC.
- Further examples of the negative effect of the TDY environment are provided in Chapter 8, Management of the TSC Call Center.
- The FY 2005 appropriation for the TSC was incorporated into the FBI's overall appropriation, thus eliminating the need to transfer funds between agencies.
- This description of the process flow reflects the general process for call screening. There can be variances depending on the type of encounter, such as a border inquiry that would require the border patrol agent to first call the Department of Homeland Security's call center (the National Targeting Center), which in turn would contact the TSC.
- See Appendix III for detailed information on call center activity.
- The State Department's visa application review activities represent, in general, a process that existed prior to the creation of the TSC and continues to be conducted by DOS personnel. Our review of TSC activities focused on domestic and border processes and encounters.
- The nomination process described here relates to the articulated process for maintaining the TSDB, which is done on a record-by-record basis. As noted in Chapter 5, the 1A and 1B databases were initially populated by accepting universes of records from source databases.
- Because NCTC is not a component of the Department of Justice, we did not perform a detailed review of its procedures for removing names from the consolidated watch list.
- Terrorist Screening Center: Draft Report to Congress, Pursuant to the Intelligence Authorization Act for Fiscal Year 2004, Section 360 (October 29, 2004). For example, in preparation for the July 2004 Democratic National Convention, the TSC received the names of 18 hazardous material drivers from the Transportation Security Administration for screening.