| Return to the USDOJ/OIG Home Page |
Federal Bureau of Investigation's Management of Information Technology Investments
Report No. 03-09
December 2002
Office of the Inspector General
The Federal Bureau of Investigation (FBI or Bureau) is the principal investigative arm of the Department of Justice (DOJ). To execute its responsibilities, the FBI’s Headquarters in Washington, D.C. provides program direction and support services to 56 field offices, approximately 400 satellite offices known as resident agencies and more than 40 foreign liaison posts.
As of June 2002, the FBI had over 11,000 Special Agents and over 16,000 other employees who performed professional, administrative, technical, clerical, craft, trade, or maintenance operations. The FBI’s budget authority increased 31 percent from $3.339 billion in FY 2001 to nearly $4.371 billion in FY 2002.8 Of this budget authority, $714 million was allocated to information technology (IT) projects in FY 2002 compared to $353 million in FY 2001.
The terrorist attacks of September 11, 2001, prompted the Attorney General to make counterterrorism the DOJ’s highest priority. The DOJ reflected these new priorities in its Strategic Plan for Fiscal Years 2001 – 2006, which was issued in November 2001. In the Strategic Plan, the Attorney General recognized that the fight against terrorism requires the DOJ “to improve the integrity and security of its computer systems and make more effective use of information technology.”
In response to the DOJ’s new priorities following September 11, 2001, the FBI proposed fundamental changes in its strategic priorities and business practices. In May 2002, the Director of the FBI announced a major reorganization that dedicates more resources to the prevention of terrorism.9 Although the core missions of the FBI remain intact, the proposed changes would transform the Bureau’s role from reactive to preventive. To accomplish this transition, FBI officials have repeatedly told Congress that new and improved IT is required to support a redesigned and refocused FBI. In testimony before the Senate Judiciary Committee on June 6, 2002, the Director released the FBI’s top ten priorities in the post-September 11 era, with the number one priority being protecting the United States from terrorist attacks. Number ten on the list of priorities is upgrading technology to successfully perform the FBI’s mission. Clearly, the FBI’s future ability to prevent terrorism and other crimes depends on modern information technology and effective management of technology.
2. The FBI’s Management of IT Infrastructure
The FBI has three divisions that manage major IT projects: the Information Resources Division (IRD), the Criminal Justice Information Services Division (CJIS), and the Laboratory Division. As discussed below, the FBI is attempting to centralize the management of IT, rather than manage IT within divisions.
The IRD provides the day-to-day support services to manage the information systems of the FBI. The IRD’s responsibilities include management of all hardware, software, and IT peripheral equipment located at the FBI’s Headquarters, field offices, and other offsite locations.
The IRD has been restructured in recent years to increase the oversight and jurisdiction of the Chief Information Officer. Until November 2001, the Chief Information Officer of the FBI was the Assistant Director of IRD who reported to the Director. However, to give the Chief Information Officer greater authority over the entire FBI, the Chief Information Officer was moved out of IRD and into the Director’s office, pursuant to a restructuring approved by Congress on November 30, 2001. Additionally, to support the Chief Information Officer, the Information Resources Management Section10 was moved out of IRD and into the Chief Information Officer’s office, following another restructuring in February 2002. Also, in February 2002, the IT Investment Management Program Office was formed (within the Information Resources Management Section) and was staffed with one individual whose responsibility was to manage the FBI’s IT investment management program. Based on these actions, the FBI recognizes that centralizing the management of IT requires a Chief Information Officer to have Bureau-wide oversight and jurisdiction, rather than be isolated within a division.
The CJIS Division uses several significant IT systems to manage and disseminate relevant criminal justice information to the FBI and other law enforcement agencies. For example, the National Crime Information Center 2000 is a nationwide information system that supports federal, state, and local law enforcement agencies. Additionally, the CJIS Division is responsible for managing the Integrated Automated Fingerprint Identification System and the National Incident-Based Reporting System. To support the management of these systems, the CJIS Division maintains a Contract Administration Office, which provides quality assurance, configuration management, and project management support services necessary to manage these and other systems under its jurisdiction.
The Laboratory Division manages several forensic computer systems that provide forensic and technical services to law enforcement agencies. A significant system includes the Combined DNA Index System (CODIS), which provides software and support services to state and local laboratories to establish databases of criminals, unsolved crime scenes, and missing persons. A component of CODIS, the National DNA Index System, shares DNA profiles from convicted offenders and crime scenes to laboratories throughout the United States. To manage these systems, the Laboratory Division maintains its own project management office.
The FBI has recognized that its IT infrastructure was significantly outdated and did not effectively support user needs. Although recent upgrades have changed these numbers, as of September 2000, over 13,000 desktop computers were 4 to 8 years old and could not run basic software packages, some communication networks were up to 12 years old and were obsolete, and multiple user-applications existed that were neither web-enabled11 nor user-friendly.12 On June 6, 2002, the Director stated to the Senate Judiciary Committee:
3. Prior Reports on the FBI’s IT and DOJ Oversight of Components’ IT
Reports issued by the Office of the Inspector General (OIG) over the past 12 years have highlighted many IT inefficiencies at the FBI. In 1990, the OIG issued a report entitled, “The FBI’s Automatic Data Processing General Controls.” This report found 11 major internal control weaknesses, many of which are still applicable today. Specifically the report stated that:
Regarding the first weakness, the FBI’s IT infrastructure is still severely outdated, as we previously mentioned. Regarding the second weakness, the FBI has recently restructured the IRD and Information Resources Management Section to reduce the fragmented management structure that existed among the three divisions responsible for managing IT. Regarding the third weakness, as discussed later in the report, the FBI is still developing an enterprise architecture framework, which includes the technical or data architecture. Regarding the fourth weakness, as discussed later in the report, the FBI did not have formally established IT investment review boards or committees until March 2002. Regarding the fifth weakness, the FBI’s major investigative systems remain labor intensive, complex, non-user friendly, and many Special Agents still do not use these systems.
The OIG’s July 1999 special report on the handling of intelligence information related to the DOJ’s campaign finance task force13 stated that FBI personnel were not well versed in the Automated Case Support (ACS) system14 and other databases. Additionally, a November 1999 report on the death of a federal inmate, Kenneth Michael Trentadue, noted deficiencies in uploading key evidence into the ACS.
A March 2002 report entitled, “An Investigation of the Belated Production of Documents in the Oklahoma City Bombing Case,” analyzed the causes for the belated production of many documents in the Oklahoma City bombing case. This report concluded that the ACS system is extraordinarily difficult to use, has significant deficiencies, and is not the vehicle for moving the FBI into the 21st century. The report noted that inefficiencies and complexities with the ACS combined with the lack of a true information management system were contributing factors in the FBI’s failure to provide hundreds of investigative documents to the defendants in the Oklahoma City Bombing Case. These reports illustrate that the FBI has not given sufficient attention to correcting its deficiencies in information management and the ACS.
In May 2002, pursuant to the FY 2002 Government Information Security Reform Act, the OIG issued a report on the FBI’s administrative and investigative mainframe systems. This report identified continued vulnerabilities with management, operational, and technical controls. Significant vulnerabilities were noted in the following areas:
The report stated that these vulnerabilities occurred because the DOJ and FBI security management had not enforced compliance with existing security policies, developed a complete set of policies to effectively secure the administrative and investigative mainframes, or held FBI personnel responsible for timely correction of recurring findings. Further, the report indicated that FBI management has been slow to correct identified weaknesses and implement corrective action. Therefore, many of these deficiencies repeat year after year in subsequent audits.
In March 2002, the Commission for the Review of FBI Security Programs issued a report titled, “A Review of FBI Security Programs.” This Commission, chaired by former FBI Director William H. Webster,was established to investigate the espionage of a FBI Supervisory Special Agent, Robert Hanssen.15 The report identified a wide range of problems affecting the FBI’s computer systems and information security policies, including the following:
According to the report, these findings resulted from the FBI’s lack of attention to IT security in developing and managing computer systems.16
Additionally, the General Accounting Office (GAO) has issued several reports and related testimony that highlight deficiencies with the FBI’s IT. In June 2002, the Comptroller General provided the following testimony before a subcommittee of the United States House of Representatives Appropriations Committee:
In a review of the DOJ’s Campaign Finance Task Force, the GAO reported in May 2002 that the FBI lacked an adequate information system that could manage and interrelate the evidence that had been gathered in relation to the Task Force’s investigations.18 Also, as part of a government-wide assessment of federal agencies, the GAO reported in February 2002 that the FBI needed to fully establish the management foundation that is necessary to successfully develop, implement, and maintain an enterprise architecture.19
The deficiencies in IT management are not solely attributable to the FBI itself, but are also attributable in part to DOJ actions. In December 2000, the GAO issued a report on the Immigration and Naturalization Service’s (INS) investment management capability.20 This report stated that the DOJ was not guiding and overseeing the INS’s IT investment management (ITIM) approach. The report highlighted the DOJ’s responsibility, as required by the Clinger-Cohen Act of 1996, to ensure that its components implement an effective ITIM process. According to the report, the DOJ had not provided the INS, or any other component, sufficient direction, guidance, and oversight of ITIM activities. Further, the report stated:
The DOJ issued ITIM guidance in August 2001 and required the components to develop an ITIM process by January 2002. This guidance, and the FBI’s ITIM process, are further discussed later in this introduction.
4. The FBI’s Current IT Investment Efforts
In a statement before the House Subcommittee on Appropriations in March 2002, FBI Director Mueller stated: “Without question, we all believe [information infrastructure] is the number one problem confronting the FBI today, recognize that for a number of reasons the situation developed over time, and know that in the future a better approach to technology upgrades must be used.”
In the FBI Information Technology Upgrade Plan (FITUP), prepared and submitted to Congress in September 2000, the Bureau stated that a lack of funding was the cause for not making meaningful upgrades to its IT infrastructure since 1994. Congress responded to this concern by appropriating a total of approximately $2.2 billion for FBI IT projects and systems for FYs 1997 to 2002.20 The FBI received $335.6 million of this amount in January 2002 from the Emergency Supplemental Appropriations Act for information technology. The following table summarizes the funds appropriated for FBI IT investments since FY 1997.
Funds Appropriated for FBI IT Investments Since FY 1997
| Fiscal Year | Total IT Investments (in millions) |
| 2002 | $714.0 |
| 2001 | $352.8 |
| 2000 | $293.0 |
| 1999 | $332.0 |
| 1998 | $241.2 |
| 1997 | $309.2 |
| Total | $2,242.2 |
| Source: Exhibit 53s22 prepared by the FBI |
The FBI has several critical initiatives underway to upgrade its infrastructure and investigation applications. Additionally, the FBI has undertaken a major hiring initiative to recruit private sector IT experts who can assist in designing and managing the sizable IT projects recently funded by Congress. For example, the FBI’s last two Chief Information Officers were hired from the private sector. Also, in March 2002, the FBI announced the hiring of a project executive from the private sector to manage Trilogy. Further, in June 2002, the FBI announced the hiring of an executive from the private sector to become the new Executive Assistant Director for Administration.
5. Trilogy: The FBI’s Largest IT Investment
Currently, the FBI’s largest IT project designed to improve IT infrastructure and office automation is the Trilogy project, formerly known as the FITUP. In September 2000, the FITUP was established to enhance the investigative support for FBI agents. The FITUP noted the following IT needs:
To address the above needs, the FITUP, renamed to Trilogy, is intended to upgrade the FBI’s: (1) hardware and software – referred to as the Information Presentation Component (IPC), (2) communication networks – referred to as the Transportation Network Component (TNC), and (3) five most important investigative applications – referred to as the User Applications Component (UAC). The IPC and TNC upgrades will provide the physical infrastructure needed to run the applications from the UAC portion of Trilogy. The UAC portion is intended to upgrade and consolidate five of the FBI’s 42 investigative applications. Because there are 37 other investigative applications and approximately 160 non-investigative applications that Trilogy will not address, Trilogy is only a starting point towards upgrading the FBI’s entire IT infrastructure.
In November 2000, Congress appropriated $100.7 million for the first year of the $379.8 million Trilogy project, which was to be funded over a three-year period (from the date contractors were hired). The $100.7 million was a combination of new program funding and a re-direction of base resources. The FBI combined the IPC and TNC portions for continuity when it requested contractor support, since both encompass physical IT infrastructure enhancements. The contractor for the IPC/TNC portions was hired in May 2001. As a result, the originally scheduled completion date for these initiatives was May 2004. A separate contractor was hired in June 2001 to complete the UAC portion of Trilogy by June 2004.
After the terrorist attacks on September 11, 2001, the importance of giving FBI agents and analysts the technological tools necessary to perform their duties was heightened in the eyes of Congress, the Attorney General, and the Director. Because the goal of Trilogy is to address many of the technological needs of the FBI, successful completion of the project in the shortest amount of time possible was viewed as increasingly critical to the FBI’s fight against terrorism. Rather than wait three years for the benefits of Trilogy, Congress fully funded the FBI’s original request of $379.8 million and provided an additional $78 million in January 2002 to speed up its deployment.23 With the supplemental funding, the FBI indicated to Congress that it would complete the deployment of hardware (including new desktop computers), networks, and software by July 2002. Additionally, the FBI would seek to accelerate upgrades to the five user applications. However, as discussed later in this report, the FBI did not meet its July 2002 milestone and is not expecting to complete the deployment of hardware, software, and networks until March 2003.
Although we believe the FBI must have sufficient resources to upgrade its technology through Trilogy and other projects, it must also have the management processes in place to effectively utilize those resources. With the recent influx of funding to the FBI, Congress expects the FBI to make significant strides in upgrading its IT infrastructure. But we believe the FBI will be successful in doing so only if it has effective IT management control processes in place. Later in this report, we provide an assessment of the FBI’s management of Trilogy.
6. Framework for Assessing IT Investment Management
Several recent management reforms have required federal agencies to improve their management processes for selecting and managing IT investments. In particular, the Clinger-Cohen Act of 1996 requires the head of each agency to implement a process for maximizing the value of the agency's IT investments and for assessing and managing the risks of its acquisitions. A key goal of the Clinger-Cohen Act is for agencies to have processes in place to ensure that IT projects are being implemented at acceptable costs and within reasonable time frames, and that the projects are contributing to tangible, observable improvements in mission performance.
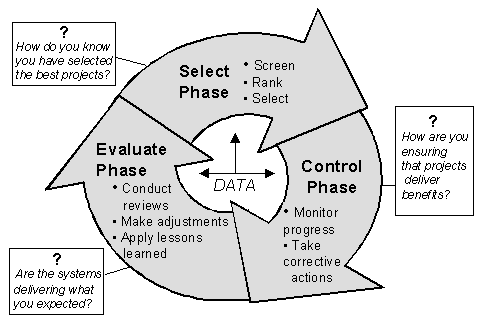
The Clinger-Cohen Act defines requirements for capital planning and control of IT investments and mandates a select/control/evaluate approach that federal agencies must follow. The following graphic describes the fundamental phases of this IT investment approach.
Fundamental Phases of the IT Investment Approach
Source: GAO
According to a GAO report, while almost all federal agencies have created some type of IT investment management process, none has implemented stable processes that address all three phases of the select/control/evaluate approach.24 One barrier to implementing stable IT investment processes has been the lack of specific guidance regarding what processes are required to build a stable, reliable IT investment management organization. The select/control/evaluate approach provides sound advice, but it does not provide a comprehensive discussion of the organizational processes involved.
To address this concern, in May 2000 the GAO developed the IT Investment Management Framework (Framework) to provide a common methodology for discussing and assessing IT capital planning and investment management practices at federal agencies. The Framework enhances previous federal IT investment management guidance by embedding the select/control/evaluate approach within a framework that explicitly describes the organizational processes required to carry out good IT investment management.
The Framework, based on best practices of leading organizations, is a hierarchical model comprising of five maturity stages. These maturity stages represent steps toward achieving stable and mature investment management processes. Each stage builds upon the lower stages and enhances the organization's ability to manage its investments. As agencies advance through these stages, the agencies’ capability to effectively manage IT increases. The following graphic describes the five maturity stages of the Framework.
The Five Maturity Stages of the ITIM Framework
Source: GAO
With the exception of the first stage, each maturity stage is composed of critical processes that must be implemented and institutionalized for the organization to satisfy the requirements of that stage. These critical processes are further broken down into key practices that describe the types of activities that an agency should be engaged in to successfully implement each critical process. An organization that has these critical processes in place is in a better position to successfully invest in IT. The following graphic describes the Framework’s five stages and associated critical processes.
The ITIM Framework’s Stages of Maturity with Critical Processes
Source: GAO
As established by the Framework, each critical process contains five core elements that indicate whether the implementation and institutionalization of a process can be effective and repeated. The five core elements are:
With the exception of the “purpose” core element, each of the other core elements contains key practices. The key practices are the attributes and activities that contribute most to the effective implementation and institutionalization of a critical process. The following graphic summarizes the interrelationships of components in an ITIM critical process.
Components of an ITIM Critical Process
Source: GAO
In August 2001, the DOJ’s Justice Management Division (JMD) issued the Guide to the Department of Justice Information Technology Investment Management Process (Guide). In response to various regulations and guidelines issued in the last several years (including the Clinger-Cohen Act, Executive Order 13011, and the Office of Management and Budget (OMB) Circular A-130), the DOJ issued the Guide to fulfill its obligation and responsibility to make measurable improvements in mission performance and service delivery to the public through the strategic application of IT.
The Guide uses the select/control/evaluate methodology to implement the strategic and performance directives of the Clinger-Cohen Act and other statutory provisions affecting IT investments. The Guide is intended to promote a process that builds on existing structures to provide maximum benefit across the entire DOJ and with other federal agencies. This process allows the DOJ to focus IT management on the strategic missions of the DOJ. Further, it promotes an investment review process that drives budget formulation and execution for information systems, and restructures the way the DOJ performs its functions before investing in IT. In addition, this process provides the methods, structures, disciplines, and management framework that govern the way IT is deployed throughout the DOJ. The Guide applies to all IT projects from all DOJ components.
The Guide requires each component to:
Further, by January 2002 each component was required to submit to the DOJ an ITIM plan incorporating the above stipulations.
8. The FBI’s Recent Efforts to Implement an ITIM Process
In an effort to improve its IT investment management practices and comply with DOJ and other statutory regulations, the FBI developed the “ITIM Model and Transition Plan” (Plan) with support from a contractor. The initial draft of the Plan was completed and submitted to JMD in January 2002. The FBI has retained this contractor to assist in the ongoing implementation of the ITIM process. The FBI estimates total costs for developing its ITIM process will be in excess of $4 million through FY 2003.
The purpose of the Plan is to establish and define the FBI’s Stage Two25 methodology and build the foundation for enhanced IT investment management. It identifies the gaps between the FBI’s current IT investment processes and the required IT management practices for Stage Two maturity.
The following excerpts from the FBI’s Plan provide an overview of how the FBI’s select, control, and evaluate processes for IT investment management are intended to operate upon implementation.26
Select
In the Select phase, potential projects will be initiated by the project sponsor via the development of a preliminary feasibility analysis (concept paper), followed by the development of a more-robust business case analyses (OMB Exhibit 300). The project proposal package will be submitted to the Technical Review Board27 to be assessed for any technical risks and then submitted to the Project Oversight Committee28 for a business review. The Project Oversight Committee will assemble the multiple requests and prioritize these requests against predefined selection criteria. A “candidate” fiscal project portfolio will then be developed and presented to the Executive Review Board29 for final evaluation and approval, and ultimately for submission to the fiscal budget process.
Control
In the Control phase, the current fiscal year IT portfolio will be tracked by the functional project management office and individual project teams. Monthly status reports will be created and presented to the Project Oversight Committee, who will work to mitigate any project related risks. Projects with exceptions to the baseline plans will be subsequently presented to the Executive Review Board for decisions about budget, scope, timeline and/or projected outcomes. During the control phase, a project will be able to receive approval to: proceed “as is,” proceed with modified funding levels and/or modified functionality, or be terminated.
Evaluate
In the Evaluate phase, IT investments that are in the operations and maintenance mode will be monitored by the Executive Review Board to ensure that expected benefits are being realized. Periodic program reviews will be conducted, wherein each IT investment will be evaluated against predefined performance metrics and criteria. Based on the reviews, decisions will be made about: future phases of existing projects; and the current policies and procedures governing the entire IT investment management, the systems development life-cycle, and other related processes. Advocacy arguments (to modify existing management practices and procedures) are also constructed during this phase, if applicable.
JMD officially approved the FBI’s Plan in May 2002, although officials from the IRD told us that in February 2002 they received verbal approval to initiate their ITIM process.30 The May 2002 approval letter states that the FBI ITIM process conforms to the guidelines defined by the GAO, OMB, and DOJ. Further, it states that the Plan is clear and comprehensive in its statement of the ITIM policy and its definition of organizational roles, responsibilities, and deliverables. Additional JMD comments, as well as our own independent assessment of the Plan, are discussed later in this report.
The FBI started its ITIM process in February 2002 by appointing the three oversight review boards discussed above (the Technical Review Board, the Project Oversight Committee, and the Executive Review Board). Also, in February 2002 the FBI held training seminars for each division to introduce the concepts of the Plan. In March 2002, the FBI began pilot testing the select phase of the Plan for FY 2004 proposed IT project enhancements. In May 2002, the pilot test of the select phase was completed and the ITIM contractor issued the, “Post Implementation Review: FBI ITIM Pilot.”
The Plan recognizes that as the FBI’s ITIM process moves through the maturity stages, other key components of IT infrastructure must evolve to optimize the IT investment function. These components include an IT strategic plan, an enterprise architecture framework, and project management. According to the Framework, an effective IT function will include these components and mature IT investment management processes are dependent on the components being in place.