I. EOUSA MANAGEMENT OF THE VNS
We determined that government VNS users were generally satisfied with the work of the contractor and sub-contractor. However, EOUSA has not proactively assessed the accuracy of data within the VNS and a significant percentage of victim notifications are returned due to incorrect address information. For example, in our attempt to contact over 2,700 victims via mail, the correspondence that we sent to approximately 18 percent of these individuals was returned as undeliverable. Further, because data in the VNS has never been archived, storage space on the VNS server has been filled to almost 80 percent of its capacity, affecting both data access speed and performance of the system. While EOUSA has articulated its intent to resolve this issue, no schedule or written plans for doing so have been established. EOUSA needs to address other matters related to the future of the VNS, including following through on its plans to add additional government participants and establishing a succession plan for key program officials.
In FY 2000, EOUSA entered into a contract with AT&T to create the VNS. In addition to creating the actual information technology hardware and software for data entry and reporting, the contractor was required to establish and staff a Call Center to assist government and victim users of the VNS. It did so by sub-contracting with Appriss, Incorporated, to run and maintain the VNS Call Center. AT&T was also to supply training, Help Desk support, and system maintenance and enhancements. Once the system was developed, field deployment of the VNS began in October 2001. The VNS was fully operational by January 2002.
The VNS has a firm fixed-price contract, which was originally set to expire in September 2007, but which has been extended for 6 months.21 The annual cost to maintain the system is approximately $3.6 million. The primary VNS server is located at the Justice Data Center in Rockville, Maryland, with a mirrored back-up system located at the VNS Call Center in Louisville, Kentucky.
We reviewed the VNS contract and spoke with numerous federal VNS users to find out if they were satisfied with the system and the Call Center.
Satisfaction with Contractor Performance
To evaluate the performance of AT&T and Appriss in terms of contract fulfillment and services provided to federal VNS users, we conducted interviews with personnel at VNS-participating agencies. We also reviewed the results of an FY 2003 BOP survey of its employees who utilized the VNS.
The federal VNS users we interviewed stated that they were not aware of any problems that occurred with the administration or fulfillment of the VNS contract. They also said that contracting personnel were very responsive to users’ requests. Federal VNS users also expressed satisfaction with the working relationship they had with the contractors.
The VNS Call Center
We determined that access to the Call Center is limited to DOJ‑cleared staff and meets all the facility security requirements as described in the VNS contract. We toured the Call Center and spoke with the contractors and the sub-contracted personnel who worked there. The physical security of the facility generally appeared to be adequate to prevent access by unauthorized personnel.
According to the VNS operations manual, the primary purpose of the Call Center is to support: (1) victims by ensuring that information is captured and updated in the VNS and appropriate notifications are sent in an expeditious manner; (2) government agencies by providing system help and ensuring that information is transferred from external systems correctly; and (3) data and system integrity through the application of security, backup, and recovery processes. In addition to its duties as a Help Desk, Call Center employees assist federal VNS users with importing data for large cases that involve 300 or more victims.
To fulfill its mission, the Call Center maintains a toll-free telephone number that victims can call to obtain case information from either an automated system or by speaking with Call Center staff.22 As indicated in the chart below, data provided by the Call Center show 78,850 calls were placed in FY 2005. The number of calls decreased in FY 2006 to 63,959. Of these totals, 11,391 and 13,988 calls in FYs 2005 and 2006, respectively, required staff assistance from Call Center personnel.
| Calls to the VNS Call Center | ||
| FY 2005 | FY 2006 | |
|---|---|---|
| Inbound | 66,748 | 49,408 |
| Operator | 8,019 | 10,023 |
| Help Desk | 3,372 | 3,965 |
| Abandoned Calls23 | 711 | 563 |
| Total Calls | 78,850 | 63,959 |
Additional Suggested Tasks for Call Center
According to BOP survey respondents and other government personnel we interviewed, they utilize the VNS Call Center for administrative purposes, as well as to address technical and access problems and to perform troubleshooting. The survey respondents generally had a positive opinion of the services provided by the Call Center, commenting that Call Center staff members were helpful, quick to respond, and open to suggestions for improvement. BOP officials did, however, state that they would like the VNS Call Center to notify victims of an escapee when the event occurs during BOP non-business hours, because the Call Center is open most of the time.24
Call Center personnel also commented that the automated ticketing system – called Tracker – for logging all calls they receive could be improved. Tracker is an internal database that is used by Call Center personnel to track calls from victims and federal VNS users, as well as to provide the VNS Project Manager with weekly reports on the status of Help Desk activity and system-related matters. However, t he Call Center staff has to manually add specific information, such as callers’ names, contact information, and a summary of the problem. According to the VNS Project Manager, Tracker is functional for VNS purposes, but it is not a good interface for the Help Desk staff. Because the Call Center staff must manually create the ticket, it is very difficult to determine if all calls and issues are recorded and tracked.
The Call Center Manager explained that the Tracker system is rudimentary because all tracking activities have to be performed manually and the system cannot be easily searched. For example, in order to go back and check for specific information, a staff member has to review the entire list of calls, rather than zeroing in on a particular timeframe. Additionally, although a newer version of the Tracker software is available, Call Center employees said they are still using the original version.
Regarding a newer version of Tracker, during the audit a VNS official told us that Tracker is part of the record used by the contractor to provide weekly reports on the status of Help Desk activity and system-related matters. The VNS Project Manager stated that Tracker is an older system and is not as user-friendly to operate as are newer programs, but that it was being used due to a software compatibility issue. The VNS Project Manager also advised that the newest version of the Tracker software, called Front Range, will be installed during 2007.
We believe that upgrading Tracker to Front Range will help improve the quality of the contracted services provided, thus leading to an improvement in the service the VNS provides to victims. The ability to more easily analyze the content of user calls should allow EOUSA to identify and address existing problems that large numbers of victims might be having with the system, as well as allow EOUSA to forestall issues that may be in the developmental stage. However, the creation of the Tracker ticket should have some mechanism to ensure that tickets are created and that this task does not need to be performed manually.
In August 2007, an EOUSA official advised us that as of July 5, 2007, Tracker’s upgrade to Front Range, which has greater report-tracking capability than Tracker, was complete. Moreover, EOUSA stated that it plans to implement Front Range’s feature to automatically e‑mail a caller upon the closing of a ticket. Additionally, a brief survey will accompany the e‑mail to address any Call Center service problems experienced during operator assistance.
EOUSA’s upgrade to Front Range demonstrates its willingness to follow through on its plans to improve the VNS. We believe it is important for the agency to implement these plans for establishing the Front Range feature that will automatically e‑mail a caller upon closure of a ticket.
In addition to ensuring that the terms of the VNS contract are fulfilled, EOUSA is also responsible for the content of the VNS. Victim information goes into the VNS when one of the various participating agencies enters the data in their own information systems and the data is uploaded to the VNS. After the initial victim record is created in the VNS through the upload process, any participating agency can enter additional information related to its cases directly into the VNS. Federal VNS users also have the option to remove a person from a case if that person is deemed to no longer be a victim.
According to the VNS Manual, when victims are added to the VNS from an agency information system, they are automatically associated with an investigative case, which, in turn, may be associated with one or many court cases. Victim records are thus automatically linked to all court cases associated with an investigative case, and if an event occurs for any associated case or defendant, each victim should be notified. However, federal VNS users can, when necessary, break the link between a victim and a specific court case or defendant if a victim is found not to be associated with that particular case or defendant.
The USAOs are responsible for creating all VNS records associated with agencies that do not participate in the VNS. For all non-participating investigative agencies, the USAO prosecuting the case creates the case and enters victim information into LIONS, the USAO case management system. Victim-related information is then uploaded electronically from LIONS to the VNS. However, in some cases with large numbers of victims, USAOs (as well as all other VNS-participating agencies) may enlist assistance from the VNS Call Center staff to create victim records in the VNS.
We interviewed federal VNS users to obtain feedback about the accuracy of VNS data. In addition, we assessed the controls and procedures in place to ensure the accuracy of information in the VNS.
VNS User Feedback
We asked users of the VNS at the FBI, the USPIS, the BOP, the DOJ Criminal Division, and USAOs about the accuracy of the data in the system. In general, users at these components considered VNS data to be accurate. However, a VNS Call Center analyst questioned the accuracy of data related to court events. Specifically, problems occur when inaccurate court schedule information is entered into LIONS and is subsequently transferred to the VNS. In addition, BOP staff said that incomplete and inaccurate data is found in the information retained in the VNS. Additionally, responses to the 2003 BOP employee survey included negative comments about the accuracy of data in the system, a desire to have victim addresses updated, and claims that some data entered into the VNS by the FBI and USAOs was inaccurate or incomplete.
Undeliverable Correspondence
One measure of VNS data accuracy is the rate at which VNS correspondence is returned as undeliverable – that is, when the contact information for a victim is inadequate. We discussed with federal VNS users undeliverable mail and e-mail, along with policies and procedures for updating information in the VNS.
Interviews with most federal VNS users verified that there were no policies or procedures in place that required them to update victim contact information in the VNS when letters were returned. A BOP official stated that all returned notifications were forwarded to the USAO. At one USAO, we noticed a large number of notification letters sitting on the floor piled in bins. When we asked a Victim/Witness staff person about it, she stated that the letters had been returned because of inaccurate addresses and one of her responsibilities was to attempt to locate updated contact information.
USAO and EOUSA representatives stated that employees regularly use online databases to search for people by former addresses and social security numbers. They said that if a different address is located, the victim record is updated in the VNS. When a USAO receives undeliverable mail in large victim cases, the USAOs bundle the undeliverable envelopes and send them to the Call Center. The Call Center, in turn, modifies the victim records in the VNS to identify them as “opted-out” of the system, and then shreds the letters. According to the VNS Project Manager, this is done because the VNS lacks the resources to perform follow‑up in such instances.
We also experienced problems with undeliverable correspondence in the course of conducting our victim surveys. When we attempted to contact 2,762 victims who were considered to be active in the VNS, 498 of our letters (18 percent) were returned as undeliverable.25 The fact that 18 percent of the “active” victim records in our sample contained invalid addresses indicates that a significant number of victims may not be receiving notifications of case events.
We asked EOUSA officials what steps were taken for e-mails that were undeliverable. EOUSA acknowledged that returned e-mail notifications were a problem and that the problem was increasing in significance as the use of e‑mail notification was rising. The VNS Project Manager further commented that EOUSA was in the process of establishing a protocol for identifying and getting information about undeliverable e‑mail to federal VNS users for action.
In June 2007, EOUSA officials acknowledged to us that there was a problem with undeliverable correspondence, but noted their belief that it is the victim’s responsibility to keep contact information up‑to‑date. Victims can update their information by various methods, such as via the VNS website or by contacting the USAO Victim-Witness Coordinator responsible for their case. According to the VNS Project Manager, federal VNS users are trained to make reasonable best efforts to find correct mailing addresses when correspondence is returned as undeliverable.
In response to our discussions with them on this issue, in August 2007 EOUSA officials informed us that they are researching approaches to implement a nation-wide procedure regarding undeliverable correspondence. The officials noted that this concern has become a higher priority for EOUSA and that this new procedure may be included in the next VNS contract.
VNS Procedures and System Controls
According to the VNS Project Manager, the accuracy of information in the VNS is largely dependent upon what was provided or entered originally by the participating agency. He added that there was no process for routinely checking the accuracy of victim files in the VNS and testing for accuracy of VNS data has not been performed. The FBI, the USPIS, and the BOP also have not tested the accuracy of the VNS data they entered.
An address is not required to enter a victim into the VNS. Rather, in order to add a victim to the VNS, the only required fields that must be entered are the victim’s first name and last name or the victim’s prefix and last name. However, in order for the victim to be sent an initial notification letter, there must be an address listed for the victim. If there is no address for the victim in the VNS when a letter is selected as a method of notification, the "initial" notification is left in a "pending" state and the victim will not be sent the initial notification letter until an address for that victim is added to the VNS. When an initial notification is stopped for lack of a mailing address, the VNS alerts the responsible federal VNS user that a necessary notification was not sent due to the missing information. The VNS Manual directs federal VNS users to address these alerts. While the system does not have a control to ensure that federal VNS users respond to these alerts or confirm that the notifications are ultimately sent, it does leave the notification in a pending state to alert the user the notification has not been sent.
In sum, there are few internal controls to ensure the accuracy and completeness of information in the VNS. This means that victims whose contact information in the VNS is incorrect could be missing the opportunity to attend court events or be updated on defendant status. Although EOUSA believes it is the victim’s responsibility to update all contact information, in our judgment, it is also EOUSA’s responsibility to ensure that victim records in the VNS are as accurate as possible. We believe that EOUSA should work with other VNS-participating agencies to develop procedures for ensuring victim contact information is current and undeliverable correspondence is pursued to help ensure victims receive case-related notifications from the VNS.
In response to the concerns we raised, EOUSA officials explained that federal VNS users have the ability to generate a number of reports that allow for review of the data entered. At this time, the VNS does not automatically validate the mailing addresses of victims. EOUSA has reviewed the use of such automation and concluded that, at this time, such a process would require significant resources.
In addition to reviewing the current status of information in the VNS, we also inquired about EOUSA’s future plans for the VNS. We examined the VNS contract, which was initiated on August 1, 2000, and runs through September 30, 2007. The contract includes a clause allowing for a 6‑month extension of services. According to the VNS Project Manager, the DOJ Justice Management Division (JMD) is responsible for procurement actions related to the VNS contract. JMD invoked the 6-month extension contract provision in June 2007 and EOUSA officials told us that they have provided necessary information to JMD for the next VNS contract.
We also examined EOUSA’s long‑term plans for the system, including the archiving of older data, replacing system hardware, outreach to additional federal agencies, and succession planning for management of the system.
Archiving and Storing VNS Data
The VNS contract states that the contractor will archive VNS data periodically. However, EOUSA and contract officials confirmed that VNS historical records have never been archived and they have no immediate plans to do so.
Contract employees, as well as EOUSA officials with whom we spoke, stated that all data entered into the VNS since it went online in October 2001 has been retained. According to contract employees, however, storage space on the server is an issue and the system needs to be upgraded for storage space. In its FY 2007 budget request, EOUSA confirmed that storage space in the system was an emerging issue. Specifically, the increased number of victims and notifications was pushing the current system to its physical capacity and this had limited the speed at which data could be accessed and become a bottleneck in the system. At the time of the budget request, the storage array as configured had 126 of its original 626 gigabytes of storage space remaining, meaning that the system was almost 80 percent full. This also meant that there was little room for future expansion for increasing data needs, and that the 6‑year old technology used by the system is a bottleneck that limits data access speed.
In examining EOUSA’s plans for archiving data, we also identified a concern with the established archiving criteria. The VNS contract states that records should be archived 36 months after a defendant is released from confinement. We asked EOUSA to provide a query to determine how many inmates in the VNS had been released prior to April 30, 2004, and we were told the VNS cannot readily obtain that information because it does not have a "released by BOP" field to make that determination. However, release of an inmate (such as permanent release, release to a halfway house or on furlough) are notifiable events.
In response to our discussions with EOUSA regarding our concern with VNS data never having been archived, in August 2007 EOUSA officials informed us that they plan to replace the existing equipment with new equipment in the near future. According to EOUSA officials, this will resolve the capacity issue and the need to archive or remove data from being accessible online.
System Hardware
In addition to issues related to archiving data, one staff person from the VNS Call Center expressed concern that VNS hardware is becoming outdated. We reviewed documentation related to this matter and found that EOUSA’s FY 2007 budget request stated that most of the equipment was 6‑years old and coming to the end of its useful life span. A partial replacement of equipment was funded in FY 2006. However, more equipment needs to be replaced. The remaining equipment still in need of replacement includes the data storage system and the database servers. The replacement equipment and labor cost was projected at $700,000.
EOUSA Outreach to Other Agencies
Historically, EOUSA has coordinated with certain federal agencies to participate and use the VNS in carrying out their responsibilities to notify victims of case events. We examined these efforts as well as EOUSA’s current efforts or plans to add new participating agencies.
At its inception, the VNS included the USAOs, the FBI, and the BOP. Since that time, the VNS has added two new agencies: the USPIS in FY 2004 and the DOJ Criminal Division in FY 2006. According to EOUSA, it is very expensive to modify the VNS by adding other investigative agencies’ various case management systems. For that reason, EOUSA stated that it is not economically feasible to include all other agencies in the VNS because most investigative agencies have too few victims associated with their cases. Accordingly, EOUSA has focused its outreach efforts on agencies that have the most victims associated with their cases, such as the USPIS.
As of October 5, 2007, the FBI and USPIS were responsible for 1.2 million (79 percent) of the victims in the VNS. The number of victims, by agency, is shown in the following chart.
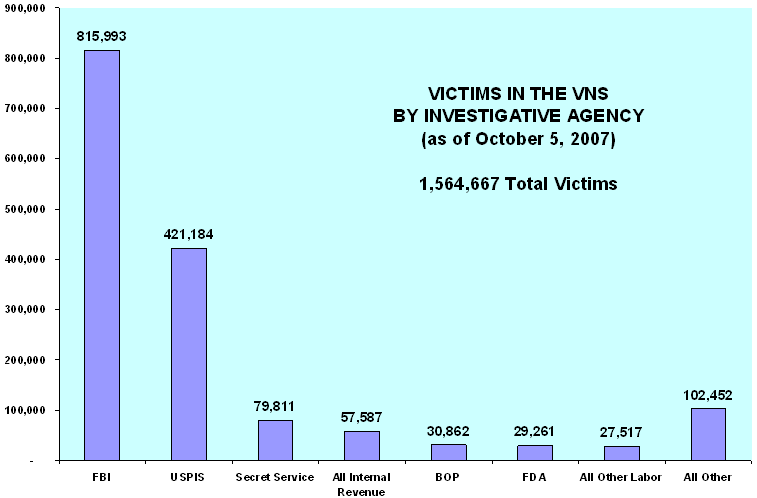
Source: OIG analysis of VNS data
Although not all investigative agencies participate in the VNS, all are mandated by statute to provide victims with information during the investigative phase.26 We interviewed officials from several agencies that do not participate in the VNS: the Bureau of Alcohol, Tobacco, Firearms and Explosives (ATF); the Drug Enforcement Administration (DEA); the United States Marshals Service (USMS); the Department of Homeland Security’s Bureau of Immigration and Customs Enforcement (ICE), and the United States Secret Service (USSS). According to representatives with whom we spoke from most of these non-participating agencies, they utilize their own resources to provide various forms of victim notification services similar to the type that the VNS was created to handle. We asked these agencies about their interest in the VNS and any contact they had with EOUSA officials about the system.
DEA officials stated that EOUSA approached the DEA when the VNS was first created, but the DEA declined to participate because the agency wa s worried about manpower, and issues related to system interface and security.
An ATF official said that ATF special agents were interested in using the VNS, and he had requested information about the system from the VNS Project Manager. However, he stated that he did not receive a response to his inquiry and therefore the ATF had not had the opportunity to evaluate the benefits of using the VNS.
USMS headquarters officials told us that EOUSA had not contacted the agency about participating in the VNS.
The USSS does not have its own, or access to, any automated system to use for victim notification, and the USSS had never been contacted about joining the VNS. According to the USSS National Victim Coordinator, this is a concern because USSS cases are continually involving more victims. Therefore, the USSS official believed that joining the VNS was something that could be very helpful.
The ICE official we interviewed stated that ICE had never been contacted about participating in the VNS and had no interest in doing so.
According to EOUSA officials, the agency is planning to create a universal interface that will allow all agencies with victim notification responsibilities to utilize the VNS through a web-based portal. According to EOUSA officials, creating this interface would eliminate the high cost of customized connections and the need for prioritizing outreach efforts. We agree with this plan and believe that it would eliminate the necessity for government agencies to duplicate the infrastructure for victim notification responsibilities.
Outreach for Court Event Data
The Administrative Office of the U.S. Courts (AOUSC) does not currently participate in the VNS, but EOUSA plans to connect the AOUSC’s automated case management system to the VNS.27 The purpose of adding the AOUSC to the VNS is to link public, court-docketed events directly with the VNS. This would eliminate the current need for USAO personnel manually to enter this information into LIONS so that it can be uploaded to the VNS. This manual process is time-consuming, increases the opportunity for human error, and increases the chances that court event information in the VNS may be incorrect, untimely, or never provided to the victim.
The proposal to connect the AOUSC to the VNS was approved by the AOUSC’s Judicial Conference on September 19, 2006, pending funding to be provided by EOUSA. As of June 2007, EOUSA officials informed us that a draft Memorandum of Agreement (MOA) between EOUSA and the AOUSC for electronic VNS participation had been prepared and EOUSA was working on acquiring funding to develop the necessary interface. The estimated start-up cost for this endeavor was $800,000, and while EOUSA requested the necessary funding from the OVC, it did not receive sufficient funding in FY 2007’s allocation to fund the AOUSC data changes. Therefore, EOUSA used its own appropriated funding to pay for the changes. The final step is for the AOUSC to develop software to extract its data to be sent to the VNS. The AOUSC estimates that developing this software will not be complicated and will cost $31,854. In August 2007 EOUSA officials provided us with a copy of the signed MOA between EOUSA and the AOUSC and noted that both agencies are working together to make necessary changes to the VNS for the connection.
Although the proposal has been endorsed by the AOUSC, it only addresses the development of the interface. According to EOUSA officials, they also will have to obtain approval from the Chief Judge in each judicial district to include court event information from that district in the VNS. Only then will all court event information flow directly from the AOUSC to the VNS. We believe that once the MOA is finalized and the interface is developed, EOUSA should work with the AOUSC to pursue the necessary approvals from the Chief Judges so that all USAOs can benefit from the electronic sharing of court docket information.
VNS Project Management and Succession Planning
The VNS is managed by a single Project Manager. According to EOUSA officials, there are no formalized succession or contingency plans to continue the management of the VNS at the headquarters level should anything happen to key personnel. EOUSA’s senior management informally discussed with us a contingency plan that could be implemented if the VNS Project Manager left. Yet, although it appears that EOUSA has considered how management of the VNS would proceed in the absence of the Project Manager, no formalized plan of action has been created. The amount of decision-making authority and system knowledge concentrated in the position makes the VNS Project Manager a critical person with responsibility for the VNS’s uninterrupted day-to-day operations. We believe the importance of the service the VNS provides to millions of victims warrants a more concrete plan for the future. Thus, we believe it is important that EOUSA develop a formalized plan that could be implemented in the case of the current Project Manager’s departure.
In addition, EOUSA does not have a formalized list of the future needs of the VNS, including enhancements to the system, upgrades to the system, replacement of outdated equipment, or growth of the system to meet the needs of federal VNS users and victims. At the beginning of the audit, EOUSA provided us with a list of future engineering changes, and since that time, we have been provided a current list of engineering changes for the VNS. Other than the engineering changes, however, EOUSA does not have any formalized long-term plans for the VNS. When we spoke with EOUSA officials about this in June 2007, they explained that all future plans for the VNS are limited to the short-term because of the upcoming expiration of the contract on September 30, 2007. However, in August 2007 EOUSA officials advised us that it has been developing a succession plan that will address any contingency issues.
We reviewed several aspects of VNS operations to evaluate EOUSA’s management of the system. We found that federal VNS users were generally satisfied with the services being provided by the contractor and sub-contractor, and these users, on the whole, found the VNS Call Center to be helpful. However, we determined that limitations in the software used to track calls to the VNS Call Center prevented EOUSA from conducting detailed analyses of suggestions for improving the VNS. While EOUSA has stated that it has addressed this issue with a software upgrade, we believe it is important for the agency to implement all of its planned enhancements.
We also found that there are few internal controls to ensure the accuracy and completeness of information in the VNS. Most importantly, this means that victims whose contact information in the VNS is incorrect or unavailable could be missing the opportunity to attend court events or be updated on defendant status. We attempted to contact over 2,700 victims as part of a victim survey, and in 18 percent of these instances, our correspondence was returned as undeliverable.
Further, VNS data, which dates back to October 2001, has never been archived and storage space on the VNS server has been filled to almost 80 percent of its capacity, a situation that has affected both data access speed and performance of the system. Also, although EOUSA has informed us that instead of archiving VNS data, it plans to expand the capacity of the system to alleviate the need for archiving, EOUSA has not yet established a formalized schedule or plan for doing so.
In addition, EOUSA has performed outreach to a limited number of federal agencies, selecting those agencies that have the most victims to keep informed, such as the USPIS. EOUSA is in the process of developing a universal interface that would allow all federal investigative agencies to upload victim information directly to the VNS. EOUSA is also currently in the process of establishing a connection between the AOUSC and the VNS, which would allow court information to flow directly to the VNS, thus improving the accuracy of court-related data and reducing the amount of manual labor required.
Finally, there are no formalized succession or contingency plans in place to ensure continuity of the VNS if the Project Manager who directs the VNS leaves his position.
We recommend that EOUSA:
-
Develop a written plan to: (1) archive VNS data, which should include a schedule for the initial archiving, parameters for subsequent archiving, and the criteria it will utilize to determine the records ready for archiving; or (2) acquire new equipment that will resolve the capacity issue.
Ensure that it is utilizing the newer version of the Tracker software, called Front Range, to allow for a more user-friendly data extraction and reporting function. Further, ensure that Front Range’s feature that automatically e‑mails the caller upon the closing of a ticket has been enabled and is being utilized to the fullest extent.
Develop a universal interface for federal investigative agencies to upload data directly to the VNS.
Work with the AOUSC to develop the hardware to connect the VNS and the AOUSC, develop a plan to connect individual federal court districts to the VNS using this interface, and endeavor to ensure that all federal districts are connected to the VNS.
Work with VNS-participating agencies to develop and implement procedures for federal VNS users to ensure that victims’ contact information is current and updated.
Develop long-range plans for the VNS and its management that include: (1) future software and hardware upgrades, (2) replacement of outdated equipment, (3) expansion of VNS server storage capacity, (4) a projection of enhancements needed to account for the future needs of government and victim users, and (5) a formal succession plan for VNS project management.
Work with VNS-participating agencies to develop and implement a nationwide procedure for addressing undeliverable correspondence and e-mail.
II. THE VNS’s EFFECTIVENESS FOR VICTIMS
Overall, the victims who responded to our survey were generally satisfied with the VNS and indicated that they felt VNS notifications were useful and easy to understand. However, our survey identified areas where improvements in the VNS could be made. Most notably, 25 percent of our survey respondents indicated that they had not heard of the VNS prior to receiving our survey, had never received a notification, or were not aware that they were registered as victims in the VNS. Further, although EOUSA encourages victims to obtain case information through the VNS website, only a small percentage of our respondents actually utilized it. Accessing the VNS website can be confusing and some victims find it difficult to navigate. Moreover, a large number of victims who responded to our survey were dissatisfied with the amount of information available to them regarding restitution and believe that knowing the custody status of offenders is important. We also determined that government VNS users can change a victim’s VNS participation status from active to inactive without recording a reason for doing so, and without notifying the victim. We identified a significant number of victims who have been opted-out of the VNS with no reason recorded.
To assess the VNS’s effectiveness and victim satisfaction with the system as a whole, we conducted surveys of both active and inactive users to examine their level of satisfaction with the VNS. Additionally, we reviewed a 2003 BOP survey of its own VNS users. We also conducted our own review of VNS services from the perspective of a victim active in the system. Specifically, we requested and were provided a test victim account that we used to access the VNS victim-user website, known as the Victim Internet System (VIS), and the VNS Call Center ’s automated and staff assistance.
VNS Active Victim User Satisfaction
Our survey of victims identified as being active in the VNS covered many different aspects of the system, including the notification process, use of the VIS, and interaction with the VNS Call Center. From a universe of 618,203 victims active in the VNS during FYs 2005 and 2006, we selected a stratified sample and mailed out surveys to 2,762 victims. We received 691 responses for a 25-percent return rate. We reviewed these submissions and identified 531 valid responses upon which we conducted our subsequent analyses.28
Overall, we found that our victim respondents were generally satisfied with what is provided to them through the VNS and that they found VNS services, such as the Call Center and the VIS, relatively easy to use. However, we identified areas of concern in our respondents’ knowledge of the VNS’s existence, overall use of the VIS by victims active in the system, and information provided in the area of restitution.
Victim Notifications
In our survey, we solicited comments from victim respondents regarding notifications of case information from the VNS and found that 173 (25 percent) of the original 691 survey respondents indicated that they did not know about the VNS, had never received a notification, or were unaware of their status as a victim of a federal crime. Further, some of these respondents reported that our survey was the first piece of correspondence they believed they had received regarding the VNS, and thus they had no idea why they had received the survey.
The number and nature of these comments is troubling. Based upon our analysis, it appears that there are a significant number of federal crime victims who have no knowledge that their personal information is contained within such a government database. We are aware of the statutory requirements that victims be notified of events that occur in their cases (and, thus, require that their information be contained in the VNS). However, in addition to the legal requirement to include them in the VNS, it is also important that EOUSA ensure that victims: (1) are aware that they are victims of a federal crime, (2) are aware that their personal information is contained within the VNS, and (3) have been afforded the opportunity to decide whether they wish to receive notifications of events that occur within their cases.
In light of victims’ comments, we reviewed notification data provided by EOUSA. According to EOUSA, at the time we deployed our survey each of the 173 respondents had been sent between 1 and 160 notifications, with the average number of notifications sent being 18.29
The fact that a quarter of our respondents indicated they did not know they were victims, despite the fact that EOUSA indicated that the individual had been sent at least one notification, indicates that the VNS might not be as effective as possible at keeping victims informed of case events. These results are similar to comments from the 2003 BOP survey of its employees who utilized the VNS. According to that survey’s results, BOP users noted that in large fraud cases many victims were surprised by the notifications. In other instances, BOP users reported receiving calls from victims who indicated that they did not understand why they were being contacted and did not know anything about the inmate referred to in the VNS notification that was sent to them.
We spoke with EOUSA officials about this issue and they acknowledged that they have no formal follow-up process to ensure that victims receive notifications from the VNS. In contrast to EOUSA, the BOP has formalized initial notification quality control procedures included in their policies and procedures for the VNS. According to BOP policies, BOP staff perform follow-up work subsequent to sending notification correspondence to victims by ensuring each victim receives the notification. If the victim’s preferred method of contact is unsuccessful, BOP staff are required to follow up with a notification letter to the victim.
According to EOUSA officials, sending follow-up letters would be overly burdensome on federal VNS users, and EOUSA was moving towards using the VIS as an alternative to written notification. However, we believe that, because the purpose of the VNS is to notify victims, the responsibility to do so should not end with making sure notifications are sent. Further, because our survey also identified that relatively few respondents were actively using the VIS, we believe EOUSA should take steps to ensure that victims are receiving at least their initial notifications, including improving its efforts to update victim contact information and addressing undeliverable correspondence and e-mail.30
Understanding Notifications
The format of the notification letters sent to victims is standardized. Prior to February 2006, federal VNS users were able to edit the text and adjust the format of the notification letters. EOUSA removed this editing capability to ensure that all notifications sent to victims contained necessary, standardized language. Although federal VNS users can add additional information to a letter, they cannot alter the format to ensure that it fits with the specific case for which it is being sent.
During the course of our audit, we spoke with federal VNS users and the VNS Call Center about the notifications. Many noted that information in notifications became confusing and sometimes contradictory when various types of notifications were combined in the same letter, and that the standard templates allowed little room to change information to clarify or correct the letters. Some also believed that letters generated by the VNS are vague and impersonal and can be insensitive to victims. Moreover, Call Center personnel told us that 70 to 80 percent of victims who contact the VNS Call Center do not know why they have been sent these letters, and that the letters do not clearly indicate that recipients are receiving the correspondence because they have been identified as victims of a federal crime.
The VNS Project Manager told us the standard templates were created to ease the notification burden for federal VNS users and allow them more time to assist victims in other ways, such as FBI Victim Specialists who provide other social services directly to victims in the field. According to EOUSA officials, they are aware that changes to the standard letters have been requested, but they said that certain language is required and the information currently conveyed is designed to provide the required information in a brief and accurate manner. EOUSA officials also noted that they have revised the standard language of the notifications once, at the behest of and with input from government VNS users. Moreover, the current template allows federal VNS users to add as much additional text to any of the standard language as necessary to help clarify the event for the victims. EOUSA officials also stated that they will make constructive revisions to the standard language of the notifications as necessary to meet statutory notification requirements.
In light of this issue, we asked survey respondents to indicate how easy it was to understand the information provided in the notifications they received. As shown in the following table, more than 80 percent of the responses indicated that the notifications were at least understandable, while less than 20 percent indicated that they found the notifications difficult to understand.
| How easy is it for you to understand the information in the notifications? |
|||
| Choices | Number of Respondents |
Percent of Respondents |
Grouped Percentages |
| Very Easy to Understand | 119 | 26 | 82 |
| Easy to Understand | 120 | 26 | |
| Understandable | 134 | 30 | |
| Difficult to Understand | 51 | 11 | 18 |
| Very Difficult to Understand | 8 | 2 | |
| Extremely Difficult to Understand | 21 | 5 | |
| Totals | 45331 | 100 | 100 |
Usefulness of Notifications
We also asked the respondents to our survey about the usefulness of the information provided in the notifications. As shown in the following table, we found that almost half (48%) of the 448 victims who responded to this question found notifications to be useful to some degree, while 69 of the 448 respondents (15%) indicated they were not useful.
| Overall, how useful was the information provided to you in the notification(s)? |
|||
| Choices | Number of Respondents |
Percent of Respondents |
Grouped Percentages |
| Very Useful | 68 | 15 | 48 |
| Useful | 148 | 33 | |
| Neutral | 163 | 36 | 36 |
| Not Useful | 37 | 8 | 15 |
| Not Useful at All | 32 | 7 | |
| Totals | 44832 | 10033 | 10033 |
The Victim Internet System
As previously noted, t he VIS is a web-based application that allows victims to have access to a subset of VNS data via the Internet. To determine the effectiveness of the VIS for victims, we included questions about the VIS in our victim surveys. We also utilized our test victim account and conducted our own testing of the VIS to assess how easy or difficult it was to use.
In analyzing the completed surveys, we observed that only 98 of the 531 victims who returned valid responses indicated that they accessed the VIS to review their case information.34 This 18-percent VIS usage rate may be of concern to EOUSA, as officials informed us on more than one occasion that EOUSA prefers and has attempted to encourage victims to utilize the Internet-based VIS instead of relying on written notifications or the Call Center.
Accessing the VIS
As shown in the following graphic, which depicts the frequency with which the 98 victim respondents indicated that they had accessed the VIS, 27 victims (28 percent) stated that they had not accessed the website since they first set up their account while 45 percent of the respondents used it monthly or quarterly.
How often have you accessed the VNS website (VIS) for information?
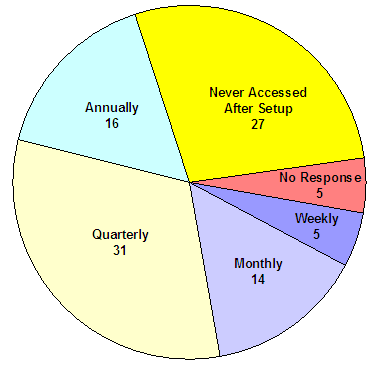
Source: OIG survey of active victims
In our survey, we also asked victims how easy or difficult the process was to set up their website accounts. As shown in the following chart, the majority of the victims (58 out of 98) who accessed the website found setting up their user accounts to be easy while 14 victims found it somewhat or very difficult.
How easy or hard was the process to set up
your VNS website (VIS) account?
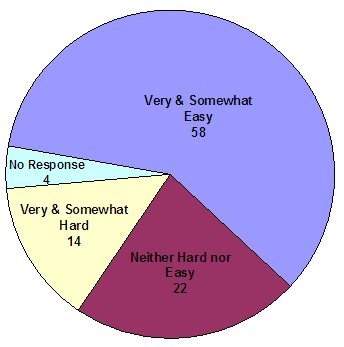
Source: OIG survey of active victims
Despite this relatively positive overall response, some of the responding victims commented on problems they encountered with the process. Their comments included: “ I tried to access the VNS website, but was unable;” “I received the VNS letter, but [the] letter has no VIN number or PIN number;” and “[I need] easier access to [the] website.”
We also utilized our test victim status to set up a VIS user account. In doing so, we noted that the process includes steps that could be confusing for victims. Specifically, notification letters advise victims to use their Victim Identification Number (VIN) and Personal Identification Number (PIN) anytime they contact the Call Center or log on to the VIS. When we accessed the VIS, we were clearly requested to input our VIN. However, we were not clearly asked for the PIN. Rather, we were asked for our VNS Login ID (Password) to enter the website. EOUSA officials explained that the first time a victim logs into the VIS, they need to use their PIN as the VNS Login ID. Victims are then prompted to create a VNS Login ID for future access to the VIS. The originally issued PIN, however, remains active for access to the VNS Call Center. None of this was explained on the VIS website, nor in the letters. EOUSA officials stated that they will undertake a review of VIS access to improve these controls and work to explain this procedure in more detail.
Comprehension of VIS Data and Ease of Navigation
We also addressed the comprehensibility of information in the VIS in our victim survey. We asked victims how easy it was for them to understand the information on the website, and found that only 9 out of 98 respondents indicated that the information was difficult to understand, while the majority found the information easy to understand.
How easy was it for you to understand the information
on the VNS website (VIS)?
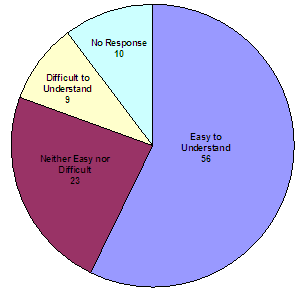
Source: OIG survey of active victims
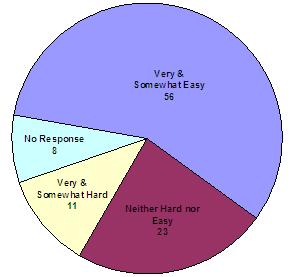
In addition, we analyzed our survey results to determine the ease with which victims navigated the VIS. According to the responses we received, only 11 of the 98 respondents found navigating the VIS to be difficult.
How easy or hard is it to navigate or find information
within the VNS website (VIS)?
Source: OIG survey of active victims
Usefulness of VIS Information
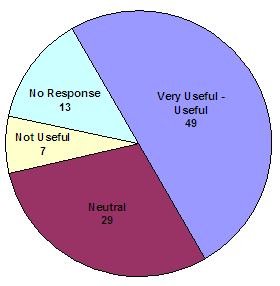
One survey question asked victims if they thought the information provided on the VIS was useful. As depicted in the following graphic, one-half of the respondents found information on the VIS to be useful, while only seven victims indicated the information was not useful.
Overall, how useful is the information provided to you
on the VNS website (VIS)?
Source: OIG survey of active victims
Restitution
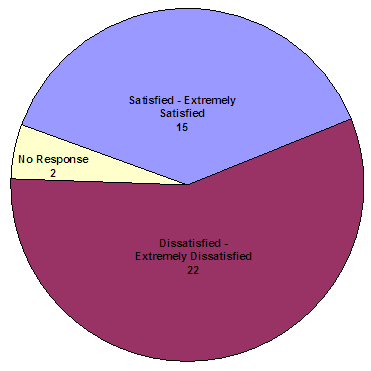
In our conversations with EOUSA officials, they stated that victims frequently asked about restitution.35 In light of this, we included questions about the level of satisfaction victims had in regard to restitution information available on the VIS. Of the 98 respondents who utilized the VIS, 39 (40 percent) indicated that they accessed the website for information regarding restitution. Of those respondents, 56 percent were dissatisfied or extremely dissatisfied with the restitution information they received from the VIS. This analysis is shown in the following chart.
How satisfied were you with the restitution information you received?
Source: OIG survey of active victims
Many of the respondents who indicated that they were dissatisfied with the restitution information provided additional comments, such as:
I received little notice, not restitution, not even updates. I had to send in victim information on more than 2 occasions – and I currently don't know if I'll get any of my money back.
I seemed to get the "run around." There were no direct answers to my questions regarding restitution. The only thing that I was told was that they were proceeding with the investigation and I would be informed and updated. I haven't heard anything in a couple [of] years.
Because of the concern regarding restitution information noted by EOUSA and reaffirmed by the response to our survey, we used our test victim account to review restitution information provided in the VIS. We found that t he information in the VIS related to restitution was not clearly written. Specifically, it was not apparent from the information available on the website whether or not our test victim was awarded restitution, and we believe that it would have been helpful if the VIS clearly indicated whether our case had restitution considerations. We discussed the restitution issue with EOUSA officials, who noted that informing victims that they are not receiving restitution is not required. However, EOUSA officials stated that they will change the language in the VIS “help” section to indicate that restitution information will only appear as that information is approved by the USAOs. Considering the importance that responding survey victims placed on restitution, we believe that the VIS could be improved by clearly indicating whether or not a case had restitution considerations, and we encourage EOUSA to make the described changes to language in the VIS to further clarify this matter to victims.
The VNS Call Center
In addition to the Internet-based VIS, a Call Center is maintained where victims can call a toll-free number and receive assistance via an automated response system or speak with an operator to receive information. While the automated system provides automated readings of notifications and gives victims the option to access other services available through the automated system, operators who staff the live assistance option can provide victims answers to a limited number of questions, direct victims where to call for further information, and provide information to federal VNS users.
We included questions about victims’ experience with the VNS Call Center in our survey of victims identified as active in the VNS. Initially, we asked victims whether they called the toll-free number for Call Center assistance and found that only 59 (11 percent) of the 531 valid victim responses indicated that they had called the toll-free number, while 383 (72 percent) responded they had not done so. We then assessed the responses from the 59 victims who responded that they had called the toll-free number and determined that 29 indicated that they had terminated their calls before receiving assistance for a variety of reasons.
We also reviewed our response data to determine what type of Call Center assistance our respondents had utilized: automated assistance, staff assistance, or a combination of both. As shown in the following table, we found that of the 59 respondents who had utilized the Call Center, 22 used automated assistance, 20 used staff assistance, and 15 utilized a combination of both.36
| What type of assistance did you receive from the Call Center? | |||
| Type of Assistance | Number | Percentage37 | |
| Automated | 22 | 37 | |
| Operator | 20 | 34 | |
| Both | 15 | 25 | |
| No Answer | 0 2 | 0 3 | |
In order to capture all of the victims utilizing a particular type of assistance, we included the 15 victims who indicated they had utilized both types of Call Center assistance in our separate analyses of automated and operator assistance.
Automated Assistance
As noted in the preceding table, of the 57 victims using Call Center services, 37 (65 percent) used automated assistance or a combination of automated and operator assistance. Additional questions answered by these 37 victims indicated that while 12 of them (32 percent) always or often received information, 15 (41 percent) responded that they never or rarely received information, and 5 (14 percent) only sometimes received information.
Did you receive the information you wanted
from the automated system?
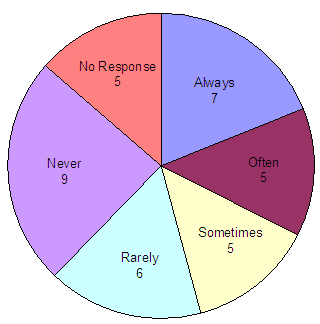
Source: OIG survey of active victims
We also asked our survey respondents about the ease with which they were able to access information about their cases by using the automated system. As shown in the following chart, the majority of respondents – 21 – (57 percent) indicated that they found the automated system to be at least somewhat easy to use, while 11 respondents (30 percent) indicated that accessing information was not easy.
How easy is it to access information through the automated system?
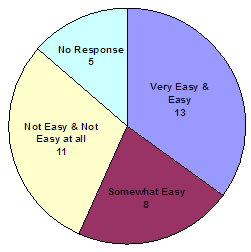
Source: OIG survey of active victims
In response to our questions regarding what additional information the respondents would like to be able to receive from the automated assistance service, victims generally indicated that they would like current and more case information, such as restitution and custody status. Additionally, they would like to be able to easily gain access to a human operator from the automated assistance.
Similar to our evaluation of the VIS, we used our test victim account to assess the automated assistance provided by the VNS Call Center. We were able to access some of the automated features and identified areas that we believe could cause confusion for victims attempting to utilize these functions. For example, we noted some confusion in the numbers a victim needs to press in order to access certain VNS services. At the first prompt, the caller must press “2” to hear information in Spanish. Another prompt instructed the caller to press “2” at anytime during the message to return to the main menu. However, when we pressed “2,” we were not directed to the beginning menu option. Rather, pressing “2” prompted an automated message that advised us to call the number on our initial notification letter if we needed assistance, and also advised us we could go to the website. Additionally, once we entered the automated system and made our first selection, there was no means for us to speak with an operator aside from hanging up and calling back.
Moreover, events were listed by defendant but not all historical events were provided, although this information was provided when we used the VIS. There also was no information available for any government-contact personnel working on a case. In addition, the automated assistance spelled out rather than said each defendant’s name. As a result, it was a very long process to get to the defendant’s information.
Overall, from the results of our survey as well as our own testing, we found that accessing the VNS’s automated assistance could be challenging. The automated assistance was sometimes confusing, information available was limited in comparison to information available for the same case via the VIS, and obtaining the information could be a lengthy process. We believe that EOUSA should take necessary steps to improve the automated assistance system and make it more user‑friendly for victims. At a minimum, users should be able to access an operator at any time during the call by pressing a single key, such as “0.”
Call Center Operator Assistance
In addition to the Call Center’s automated assistance, our victim survey included questions regarding the use of Call Center operator assistance via its toll-free number. According to Call Center staff, they can provide contact information for further assistance and provide case-specific information related to 10 areas:
- Current offender custody status
- Current investigative status of case
- Arrests made in the case
- Sentencing information
- Pleas made by defendant
- Type of next court event
- Date of next court event
- Time of next court event
- Inmate location
- Inmate scheduled release date
As indicated in the chart on page 38, we found that 35 of the 59 victims who indicated that they utilized Call Center services also indicated that they had utilized the Call Center’s operator assistance. For this analysis, we evaluated information provided by these 35 respondents who had utilized the operator assistance. As shown in the following chart, 16 respondents (46 percent) indicated that they always or often received the information they wanted, while only 6 respondents (17 percent) indicated that they never or rarely received the information.
Did you receive the information you wanted?
(from Live Call Center Assistance)
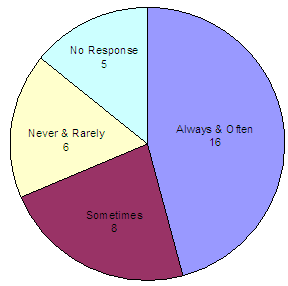
Source: OIG survey of active victims
We also solicited comments from the survey respondents about the Call Center’s operator assistance. We found that 14 out of 29 respondents indicated that they were dissatisfied with the system because: (1) it lacked information regarding restitution; (2) it did not contain the updated information on the case or the custody of the defendant; and (3) the system generally did not have enough information and assistance.38
In response to these comments, EOUSA stated that the Call Center service level for victims is appropriate given the goals of the VNS project and the information available to individuals at the Call Center. Those goals are to provide victims the information required by the applicable statutes and the Attorney General Guidelines for Victim-Witness Assistance. EOUSA officials further explained that when victims have questions beyond the scope of VNS-related events, Call Center personnel direct the caller to the victim staff person of the agency currently involved with the case. This ensures that the victim speaks with someone who is familiar with the facts of the case and can provide the most up-to-date, accurate information, including information that is not available in the VNS.
We identified several additional issues when we performed our own evaluation of the Call Center ’s operator assistance. For example, we found that the only opportunity a victim has to speak with an operator occurs at the beginning of the call. If a caller does not immediately select that option (perhaps before the caller has received much information or had the time to develop questions), the caller must hang up, call back, and select to speak with a human operator at the outset of the call.
Another issue we identified is that, according to the VNS contract, a victim must have the option of speaking directly with a Call Center operator to be able to obtain case information in either English or Spanish. However, as of June 2007, the Call Center had only a single Spanish-speaking operator on staff, meaning that there are times each day when the Call Center is unable to provide this service to victims. According to EOUSA officials, subsequent to our discussion, they informed the contractor of the requirement that a Spanish‑speaking operator must be on duty during all Call Center operating hours. As a result, the contractor is now planning to add another Spanish-speaking operator to the Call Center.
In sum, while some victim survey respondents commented on their displeasure with the Call Center ’s operator assistance, the majority of our survey respondents indicated that they received the information they needed. However, based on our testing, we believe EOUSA could improve the effectiveness of the Call Center’s operator assistance by allowing callers to access a human operator at more points during a call, having a Spanish-speaking operator on duty during all hours of operation, and by allowing Call Center operators to provide more information to victims who contact them.
Availability of Custody Status Data
Access to defendant custody data is one of the most important features of the VNS. The Attorney General Victim Witness Guidelines direct agencies to notify victims of the release or escape of an offender or suspected offender. However, the USAOs do not consistently enter defendant custody status information into the VNS during the prosecutorial phase.39 The VNS Project Manager stated that the USAOs do not consistently enter into the VNS custody status information on defendants during the criminal justice process and obtaining this information is not a top priority for the VNS.
We included questions about the importance of custody status in our survey of victims active in the VNS. As shown in the following graphic, 375 out of the 531 victims who responded to this question (71 percent) indicated that they considered knowing the custody status of the defendant to be “Extremely Important,” “Very Important,” or “Important.”
How important is it for you to know the custody status (incarcerated or not incarcerated) of the defendant(s)/inmate(s) in your case?
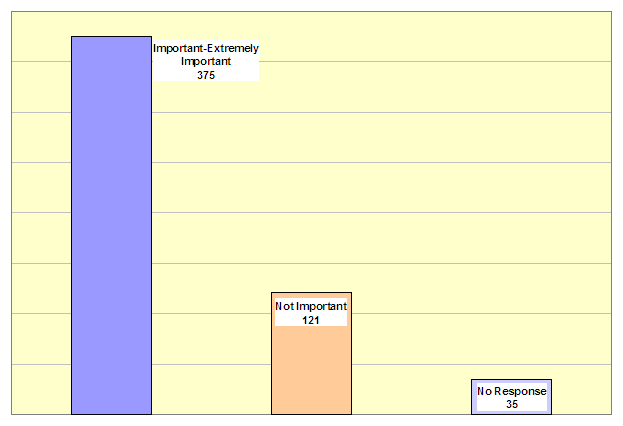
Source: OIG survey of active victims
The USMS is the only entity that tracks the pre-sentencing custody status of federal defendants. We believe that it is important for the custody status of defendants in the prosecutorial phase to be provided to victims, as required by DOJ guidelines. We raised this issue with EOUSA officials in June 2007, noting that we were told by USMS officials that the USMS had never been approached by EOUSA to connect to the VNS. In response, EOUSA officials stated that funding an electronic interface between the VNS and the USMS was an issue, but requested contact information for the USMS officials we interviewed.
In August 2007, EOUSA officials advised us that providing custody status to victims would be a priority and that they had reached out to the USMS regarding this issue. According to EOUSA, the USMS is willing to provide custody status information to VNS. Further, EOUSA has provided direct appropriated money to fund any system changes that will be needed to accept data from the USMS.
Victims No Longer Active in the VNS
In addition to surveying active victims, we conducted a survey of victims who were no longer active in the VNS. These victims had once been active in the VNS, but had, for a variety of reasons, been “deactivated” and were now in an “opt-out” status.40 We designed this part of the survey to determine whether the opted-out victims received an initial notification from a federal agency regarding the VNS and whether they subsequently chose not to receive notifications.
Victims may choose to “opt-out” of the VNS themselves or be opted-out when a federal VNS user chooses to stop sending them notifications. The VNS contains a field that offers one of four options that may be chosen to record the reason a victim is opted-out, as follows:
Contact Choice indicates that the victim chose to be opted-out. Federal VNS users issue letters to these victims confirming they have been opted-out of the VNS.
Invalid Address indicates the victim was opted-out due to an invalid address or letters that could not be delivered. Because of incorrect addresses there is no letter sent to alert the victim that they were opted-out of the system.
User Choice indicates the federal VNS user has decided to opt a victim out of the VNS. However, federal VNS users do not send letters alerting victims that they were opted-out of the system.
No Longer a Victim indicates that the federal VNS user determined the person who was originally notified of being a victim is no longer considered one.
Through our analyses of VNS data, we determined that 164,493 victims were opted-out of the system between the VNS’s inception in October 2001 and September 20, 2006. We further analyzed the data to determine the reason these victims were opted-out of the system.
| VICTIMS OPTED-OUT OF THE VNS October 2001 to September 20, 2006 |
||
|---|---|---|
| Opt-Out Reasons | Number of Registrants |
Percentage |
| Contact Choice | 4,144 | 3% |
| Invalid Address | 79,597 | 48% |
| User Choice | 28,486 | 17% |
| No Longer a Victim | 17 | <1% |
| No Reason Given | 52,249 | 32% |
| Total | 164,493 | 100% |
| Source: OIG analysis of VNS data |
We are concerned with the high number of victims identified as opted out due to invalid address information. This number is in addition to our other findings related to undeliverable mail and incorrect contact information. We believe that these opted-out victims with invalid address information are further evidence that EOUSA needs to improve its efforts to maintain up-to-date contact information, as recommended in Finding I.
We are also concerned with the high percentage of victims opted out of the VNS with no reason given. We discussed this issue with EOUSA officials, who confirmed that it is not mandatory to include in the VNS the reason a victim is opted-out. We believe that because there is no requirement for recording why someone was removed from the VNS, there is no easy means available to review a record to ensure that the victim was opted-out for a valid reason.
To maximize our response rate from those victims more recently opted-out of the system, we identified 71,179 victims who were opted-out of the VNS during the 2 full fiscal years prior to our analysis – 2005 and 2006. As shown in the following table, 73 percent of these 71,179 victims were opted-out of the VNS due to an invalid address, while 10 percent were opted-out with no reason provided.
| VICTIMS OPTED-OUT OF THE VNS October 1, 2004, through September 30, 2006 |
||
|---|---|---|
| Opt-Out Reasons | Number of Registrants |
Percent Value |
| Contact Choice | 1,580 | 2% |
| Invalid Address | 52,029 | 73% |
| User Choice | 10,548 | 15% |
| No Longer a Victim | 56 | <1% |
| No Reason Given | 6,966 | 10% |
| Total | 71,179 | 100% |
| Source: OIG analysis of VNS data |
We then analyzed this data, selected a sample, and sent surveys to 480 victims.41 We received 58 responses to our survey, resulting in a 12‑percent response rate.42 We then analyzed these 58 responses and isolated 44 out of the total that we considered to be valid.
We conducted analyses on these 44 responses and determined, as the following graphic shows, that only 18 percent (8 respondents) chose not to receive notification information.
Did you choose not to receive notification from the Victim Notification System?
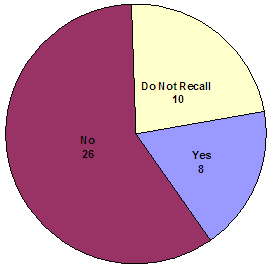
Source: OIG survey of victims opted-out of the VNS
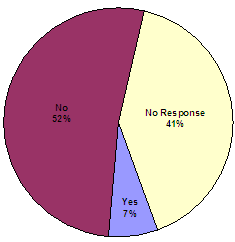
Furthermore, only three of our respondents (7 percent) indicated that they were informed by a federal agency that they were opted-out of the VNS and would no longer receive notifications.
If it was not your choice, were you informed by a federal agency that you would no longer receive notification?
Source: OIG survey of victims opted-out of the VNS
Overall, based on the high rate of undeliverable surveys, as well as the relatively low overall response rate, our survey of opted-out victims did not provide clear evidence about why victims opt-out of the system. However, we found that the majority of our respondents who did not choose to opt-out were not informed by a federal agency that they would no longer receive notifications from the VNS.
To gauge if victims are effectively being notified by the VNS of important case-related information, we conducted a survey of victims considered to be active in the VNS, utilized VNS services from a victim’s perspective by using a VNS test user account, and interviewed federal VNS users and VNS Call Center personnel. In general, the victims who responded to our survey were satisfied with the VNS and indicated that they felt VNS notifications were useful and easy to understand.
However, we identified areas in which we believe EOUSA could improve the services the VNS provides to victims. For example, approximately 25 percent of our victim respondents were unaware of the VNS, had never received a notification, or were unaware of their status as a victim of a federal crime, despite having been sent at least one VNS notification. These results indicate that many victims may not have been notified of case events.
Our interviews with government VNS users and Call Center personnel, as well as our own review of notifications provided to victims, found that notifications sent through the VNS did not always provide enough information to victims and that the standardized language within them can sometimes limit the effectiveness of the information provided.
From our survey, we determined that while the VNS website generally provides useful and understandable information to victims, the process and requisite passwords required to access it can sometimes be confusing and difficult. Additionally, we found that our respondents desired more information regarding restitution than what was provided on the website. Through our survey, we also determined that only a small portion of our respondents were using the VNS website – VIS – to obtain information about their cases.
We also surveyed victims about their use of the Call Center and performed our own testing of Call Center services to determine if the services it provides are effective. We found that the automated assistance was difficult to access, limited information was available to the caller, and the system was difficult to navigate and not user-friendly. We also found that the operator assistance option only allowed a person one opportunity to reach a human operator (and then only at the beginning of the call), a Spanish-speaking operator was not available during all hours of operation, and operators provided little information.
In addition to those victims considered to be active in the VNS, we also analyzed data on and conducted a survey of those victims who had previously been active in the system but were no longer active (referred to as “opted‑out” in the VNS). We found that the VNS allows federal VNS users to opt a victim out of the system without recording a reason for doing so. According to data in the VNS, as of September 20, 2006, more than 160,000 victims had been opted-out of the VNS since its inception, with more than 50,000 of them having been opted-out with no reason recorded. We are concerned that because there is no requirement to list a reason, there is no easy means to determine if the decision to opt-out a particular victim was proper.
Our survey of victims opted-out of the VNS found that the majority of the individuals who responded to our survey indicated that it had not been their choice to be opted-out of the VNS and that most were not informed by a federal agency that they would no longer receive notifications from the VNS.
We recommend that EOUSA:
- Improve the Call Center automated assistance to allow callers to reach an operator at any point during a call.
- Follow up with the sub-contractor at the VNS Call Center to fulfill its requirement to have a Spanish‑speaking operator available during all hours of operation.
- Work with the USMS to ensure that the accurate custody status of defendants is available to victims utilizing VNS services.
- Ensure that information regarding restitution is consistent throughout the VIS so that it is clear to victims whether restitution information is available to them.
- Work with VNS-participating agencies to develop a requirement for federal VNS users to record a reason for opting a victim out of the VNS.
III. REVIEW OF VNS INFORMATION SECURITY
We evaluated the VNS’s information security and privacy policies and identified various deficiencies, including EOUSA’s implementation of systems and communications protection controls, identification and authentication, website privacy, and web application controls. As a result, the VNS may be susceptible to unauthorized use, access, or data modification. Because the VNS contains personally identifiable information (PII) for federal crime victims, such as names, contact information, and some social security numbers, EOUSA must improve its information security practices to help ensure that the data is appropriately protected against loss and misuse.
During our interviews with VNS contractor personnel, we were informed that some recommended security patches for the system had not been installed because the patches had not been approved by EOUSA. In addition, during the course of our audit we were apprised of several attempted electronic break-ins to the VNS, which contains personally identifiable information (PII) from federal crime victims throughout the world. After discussing these security issues with EOUSA officials, we determined that the sensitive nature of this information (names, contact information, some social security numbers), as well as the possible consequences of failing adequately to protect it, warranted a more in-depth review of the VNS’s information security. Therefore, the OIG contracted with outside auditors, Urbach, Kahn, & Werlin, LLP (UKW), to conduct an independent assessment in accordance with the Government Accountability Office’s (GAO) Generally Accepted Government Auditing Standards.43, 44
Objectives, Scope, and Methodology of Review
We conducted an independent assessment to evaluate whether the VNS was properly configured to prevent unauthorized use, access, and data modification from sensitive and potentially vulnerable access points. We also determined whether information security control weaknesses exist surrounding the VNS’s web interface; as well as to identify weaknesses associated with data collection, transmission, data storage, and PII. Further, we assessed the VNS’s compliance with applicable federal information security policies and procedures for DOJ and EOUSA.
We performed a vulnerability assessment of the information security configuration of the VNS and tested web application security controls for the VIS. In order to identify whether the VNS complied with DOJ and federal privacy and information security policies, we performed interviews, on-site observations, and reviews of information security-related documents.
Overview of Information Security Controls Review Results
We concluded that the following information security control weaknesses exist within the VNS:
| Information Security Control Areas | Function |
|---|---|
| Systems and Communications Protection | To prevent unauthorized and unintended information transfer via shared system resources. |
| Identification and Authentication | To verify the identity of users when accessing the system. |
| Website Privacy | To protect data collection and PII. |
| VNS Vulnerability Assessment | To determine the adequacy of security measures, identify security deficiencies, provide data from which to extrapolate the effectiveness of proposed security measures, and confirm the adequacy of such measures after implementation. |
| Web Application Controls | To identify issues related to vulnerabilities and risks associated with web applications. |
We concluded that these deficiencies exist because EOUSA did not always fully develop, enforce, or formalize information technology (IT) security and privacy policies and procedures in accordance with current DOJ policies and procedures. We considered these weaknesses a moderate risk to the protection of the VNS and its data from unauthorized use, disclosure, loss, or modification in accordance with Federal Information Processing Standards (FIPS) Publication (PUB) 199.45 Specific details regarding findings identified during this review are discussed within the following sections.
Systems and Communications Protection Controls
The purpose of systems and communications protection controls is to prevent unauthorized and unintended information transfer between systems that share the same resources. We tested 12 control areas and identified weaknesses in transmission integrity and data validation.
Transmission Integrity and Data Validation
Transmission integrity and data validation are controls used to check for completeness and accuracy of data entered into a system. To ensure the integrity of transmitted data and its validation, encryption should be used for the transmission of interfacing data files.
The Department’s Information Technology Security (ITS) standards require that checksums, hash totals, and record counts be used by applications to verify data integrity.46 Components are strongly encouraged to have an automated means of detecting both intentional and unintentional modifications of data. Further, the Department’s ITS standards require that communication channels are protected using FIPS-approved encryption modules.
We reviewed the transmission integrity and data validation documentation for five entities that transmit data into the VNS. Four were Department components – the FBI, the BOP, USAOs, and the Criminal Division. The fifth was the USPIS.
Although EOUSA is presently encrypting the transmission of data files received from the USAOs, the DOJ Criminal Division, and the USPIS, this is not the case for the BOP and the FBI. Moreover, we found that EOUSA did not always perform data validations as to the completeness or accuracy of data files received from the BOP and the FBI.
By not encrypting the transmitted data or performing data integrity checks, EOUSA does not have the ability to detect or prevent the alteration of transmitted data files. EOUSA acknowledged these deficiencies and is currently discussing the implementation of complete session encryption for BOP and FBI data. At the time of this report, both the FBI and the BOP stated that the necessary course of action was initiated in order to encrypt the data transmitted to the VNS.
Identification and Authentication
Identification and authentication controls are used to verify the identity of users when accessing the system. For this area, our review found a weakness in one of the six control areas tested.47 Specifically, we found a deficiency regarding how system security information is reported in the VNS system security plan (SSP).
User identification and authentication is the process of uniquely identifying and authenticating users or devices before establishing a connection. Identification and authentication procedures are commonly communicated to the users in an SSP. A system security plan is designed to provide an overview of the security requirements of the system and describe the controls in place. SSPs are a key component of certification and accreditation packages and are relied upon by the designated approving authority to authorize a system’s operation.
To maintain accreditation, the Department’s ITS standards require each system to be reviewed annually. Further, system documentation should be modified to include any new security controls if they have been added post-development.
We found that the VNS system security plan had not been updated with the correct procedural information, contact information, and the correct process of authenticating users before establishing a network connection. We also identified that the document contained inaccurate information. For example, the VNS SSP states: “The VNS application will not blank the screen but will disconnect the user from the VNS after 10 minutes of inactivity.” However, we found that the VNS application is currently set to disconnect the user after a period of 20 minutes of inactivity.
Without an updated SSP, the depiction of the VNS’s system security and control environment may be inaccurate or incomplete, which means that the individuals approving the certification and accreditation document are doing so based upon out-of-date information.
Website Privacy
Website privacy controls and data protection methods are enforced to protect data collection and PII. We identified a weakness in one of the seven control areas tested.48 Our review revealed that the VNS’s external linking practices failed to provide disclaimers or notifications to users when they are about to visit a third-party website. The intent of external linking notifications is to notify users that they will no longer be protected by the privacy policies of the current site they are visiting once they navigate to another website via a hyperlink.
The Department’s Guidance for the Implementation of Office of Management and Budget (OMB) Policies for Federal Agency Websites states that websites should provide visitors an appropriate notification and a disclaimer statement when the individual leaves a Department website via a non‑government link.
Occasionally, a federal VNS user will insert a hyperlink into the VNS that, when pursued, will send a victim using the VIS to another website that has additional information. For example, a third-party website might have social services information for victims. The VIS does not provide a disclaimer notification to users when visiting these third-party websites through a hyperlink. Without a disclaimer notification, VIS users may be unaware that differing privacy policies are in effect.
The VNS’s VIS Web Application Controls Testing
The testing of web application controls is designed to identify issues related to vulnerabilities and risks associated with web applications. These vulnerabilities often result in the loss of confidentiality, integrity, and availability of data.
We utilized commercially available software tools to evaluate the VIS’s web application information security controls.49 We identified the following vulnerabilities:
The VIS may allow manipulation within a web application, which can exploit security issues.
The configuration of the VIS allows for the possibility that users could bypass the entry of usernames and passwords of linked web pages. As a result, individuals could gain access to unauthorized information.
The application may be vulnerable to attacks that can allow malicious users to retrieve data or alter server settings.
The VNS server configuration allowed for access to common default directories. Default directories often contain vulnerabilities that can be exploited over the web. Common default directories are installed during initial installation and all non-essential directories should be removed by the administrator and essential directories should be protected by authentication.
The VNS uses JavaScript, a computer language used to create interactive websites and web applications, which has certain risks inherent to its use. For example, JavaScript may be able to scan a network, identify all web-enabled devices, and send attacks or commands to these devices.
The potential existed for unauthorized users to access web server administrative interfaces. These interfaces are used by the website administrator to maintain the website and are usually not available to the public.
The VNS is susceptible to exploits in which an attacker uses the software on a web server to access data in a directory prohibited for use by the attacker. Moreover, the execution of arbitrary commands and code by an attacker may be possible.
The sensitive information contained within the VNS was not adequately protected against the loss of confidentiality, integrity, and availability of data. The vulnerabilities found in the VNS’s VIS web application controls are significant because the system contains personally identifiable information for federal crime victims that includes names, contact information, and some social security numbers. Therefore, EOUSA should take necessary actions to improve its website security to help protect the identities of victims of federal crimes.
The VNS Vulnerability Assessment
A vulnerability assessment is the systematic examination of an information system that determines the adequacy of security measures, identifies security deficiencies, provides data from which to extrapolate the effectiveness of proposed security measures, and confirms the adequacy of such measures after implementation.
We performed a vulnerability assessment to identify the information security controls implemented for the VNS environment. We reviewed the VNS’s current information security controls to determine whether they were implemented to adhere to the Department’s standards. We identified vulnerabilities within the three areas described below.50
Unnecessary or Vulnerable Service
System services can be used to operate computer servers or trigger operating system functions. These services can pose serious security threats to the system and network if they are not secured. Further, unnecessary services should be disabled.
During the review of VNS information security controls, we found unnecessary or vulnerable services operating on the system. If not properly secured or disabled, these services could be exploited to launch attacks against the VNS infrastructure. For example, the VNS file transfer protocol (also commonly referred to as “FTP”), designed for the transfer of files remotely over large distances, was identified as an older version of this protocol. This version permits passing of user identification and password as well as session data in plain text without encryption. Allowing log-ins and passwords to pass between client and server in plain text makes them vulnerable to session high-jacking. Therefore, this service should be disabled and all transfers of files be done with encryption.
Patch Management
Patch management is the process of controlling the deployment and maintenance of interim software releases into the system’s environment. It is used to maintain operational efficiency and effectiveness, overcome security vulnerabilities, and maintain the stability of the system’s environment.
Patches are developed by software manufacturers following the identification of system security weaknesses that can be exploited. When systems’ patches are not current, the risk posed by the weaknesses the patches were created to address is increased.
We found that EOUSA did not always apply application and server patches in a timely manner. Several patches that had been available since 2002 and 2005 had not been applied. In essence, by not applying the patches, EOUSA has allowed a known system vulnerability to continue to exist. As a result, at a minimum, the VNS is susceptible to a disruption of its operations. This disruption could be caused by a “Trojan Horse” - a destructive program that masquerades as a benign application before it is executed. The VNS may also be vulnerable to a buffer overflow, which occurs when a program or process tries to store more data in a temporary data storage area than it was intended to hold. This data can overflow into adjacent storage areas, corrupting or overwriting the valid data held in them.
Network Device and Server Security
Network device and server security refers to the management of device settings and configurations implemented in order to secure the system and network infrastructure.
By not implementing security standards and best practices to protect against common vulnerabilities, the VNS may be susceptible to unauthorized use, access, or data modification of system configuration and password files. Because of these vulnerabilities, VNS data that is being transmitted across the system may be intercepted and redirected to a person who is not authorized to receive the data. Additionally, an attacker could possibly interfere with system operations and cause the system to become inoperable.
We found that the sensitive information contained in the VNS may be susceptible to unauthorized use, access, or data modification. We identified deficiencies with EOUSA’s implementation of systems and communications protection controls, identification and authentication, website privacy, web application controls, unnecessary or vulnerable system services, patch management, and network device and server security. These deficiencies exist because EOUSA did not always fully develop, enforce, or formalize IT security and privacy policies and procedures in accordance with current Department information security policies and procedures.
Because the VNS contains personally identifiable information for federal crime victims such as names, contact information, and some social security numbers, EOUSA must improve its information security practices to help ensure that the data is appropriately protected.
We recommend that EOUSA:
Perform data integrity checks and implement the encryption of data files received to ensure completion and accuracy in accordance with Department policy.
Update the VNS system security plan to reflect complete and accurate user identification and authentication security information as required by Department standards.
Ensure that a disclaimer notification is developed for the VIS application to notify users when they are about to visit a third-party website through a hyperlink.
Modify the VIS application to protect against common web attacks in accordance with the recommendations listed for the specific vulnerabilities in Appendix XI.
Terminate unnecessary or vulnerable services identified on the VNS servers.
Apply application and server patches in a timely manner.
Adequately secure network devices and server configurations in accordance with the recommendations listed for the specific vulnerabilities in Appendix X.
The Federal Acquisition Regulation (FAR) System Subpart 16.202-1 states that a firm fixed-price contract provides for a price that is not subject to any adjustment based on the contractor’s cost experience in performing the contract. This contract type places upon the contractor maximum risk and full responsibility for all costs and resulting profit or loss. It provides maximum incentive for the contractor to control costs and perform effectively and imposes a minimum administrative burden upon the contracting parties.
“Inbound” calls are calls to the automated toll-free number for which no live assistance was provided. “Operator” calls are from victims who dialed the toll-free number and selected "0" to speak with an operator. “Help Desk” calls are from personnel at VNS-participating agencies for application support.
“Abandoned Calls” are instances where a caller hung up before completing the call or talking to a Call Center operator.
The VNS Call Center is operational Monday through Friday, from 7:00 a.m. to 2:00 a.m.; Saturday from 7:00 a.m. to 12:00 a.m.; and Sunday 10:00 a.m. to 12:00 a.m.
Our attempt to contact victims in the VNS was performed as part of a survey related to victim satisfaction with the VNS. The results of our survey are conveyed in Finding II. The complete scope and methodology of this survey is contained in Appendix VII.
Once these cases are forwarded to a USAO for prosecution, the notifications become the responsibility of the USAO and are then processed through the VNS.
The AOUSC is responsible for working with government agencies to coordinate and implement new legislation and procedures and to develop and support automated systems and technologies used throughout the courts. The AOUSC manages the federal courts' case management and electronic case files system, which provides the courts with enhanced and updated docket management; allows the courts to maintain case documents in electronic form; and gives each court the option of permitting case documents such as pleadings, motions, and petitions to be filed with the court over the Internet.
Additional information on this survey’s scope and methodology can be found in Appendix VII.
The data on notifications sent includes information provided via numerous methods, including letter, e-mail, or posting on the VNS website, VIS.
Information about victim use of the VIS, which we obtained through our survey, begins on page 31.
Out of the 531 overall valid responses to our survey, 453 respondents answered this particular question, while 78 did not. Thus, we excluded from the analysis depicted in this table the 78 survey respondents who did not respond to this question.
Out of the 531 overall valid responses to our survey, 448 respondents answered this particular question, while 83 did not. Thus, we excluded from the analysis depicted in this table the 83 survey respondents who did not respond to this question.
We conducted all of our analyses related to the VIS on this universe of 98 respondents who indicated that they accessed the VIS to review case information.
Restitution is defined on the VIS as a court order directing the defendant to pay a fixed amount of money to the victim in order to compensate the victim for loss incurred as a result of the crime.
Two of the 59 respondents who indicated that they had called the toll-free number did not respond to this question.
Respondent comments on Call Center operator assistance can be found in Appendix IX.
During the prosecutorial phase, a defendant may be released on bond or remanded into the custody of the respective U.S. Marshal to stand trial. Once a defendant has been convicted, sentenced, and remanded to a BOP correctional facility, the defendant moves to the incarceration phase and the provision of custody status information becomes the responsibility of the BOP.
According to the VNS Manual, “opt-out” indicates the status of a registered victim or contact who does not receive notifications and cannot access the VNS Inbound phone line or Internet web page. Although these victims are no longer considered to be active in the VNS, their names and information remain in the system.
A detailed description of our opt-out survey’s scope and methodology can be found in Appendix VIII.
Of the 480 surveys that we sent out, 58 percent (280) were returned as undeliverable.
In this section of our report, “we” and “our” refer to the auditors working under the direction of the OIG.
The OIG regularly contracts with independent auditing firms to fulfill its responsibilities under the Federal Information Security Management Act.
The FIPS PUB 199, Standards for Security Categorization of Federal Information and Information Systems is required to be used by federal agencies to categorize all information and information systems collected or maintained by or on behalf of each agency based on the objectives of providing appropriate levels of information security according to a range of risk levels. The three levels of risk – low, moderate, and high – identify the potential impact on organizations or individuals should there be a breach of security. The FIPS PUB 199 defines the potential impact as moderate if the loss of confidentiality, integrity, or availability could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals.
A checksum is a type of redundancy check used to protect the integrity of data by detecting errors. Hash totals are used as an integrity check to identify files or verify their integrity. Record counts are used to ensure that records are not lost during transmission.
The six control areas of identification and authentication we tested were controls for policy and procedures, user identification and authentication, device identification and authentication, identifier management, authenticator management, and cryptographic module authentication.
The seven control areas of website privacy we tested were relevant content, approval of content, external linking, tracking mechanisms, persistent tracking mechanisms, disclaimers for tracking mechanisms, and privacy policy.
See Appendix XI for the full details and results of web application testing. The test procedures were limited to the arrangements made with EOUSA, which required that non-destructive testing be performed. In other words, our testing could identify that a vulnerability existed, but we could not attempt to exploit that vulnerability to examine the effect of the weakness or any possible consequence of an external exploitation of the weakness.
See Appendix X for the full details and results of the vulnerability assessment.