In 2001, at the request of the Attorney General, the Office of the Inspector General (OIG) conducted audits of the controls over weapons and laptop computers at the Federal Bureau of Investigation (FBI), the Drug Enforcement Administration (DEA), the Federal Bureau of Prisons, and the United States Marshals Service. These audits resulted from concerns about the Department of Justice’s (DOJ) accountability for weapons and laptop computers. The OIG issued separate reports concerning each component and an overall report summarizing the results.
In August 2002 we issued the report concerning the DEA’s control over weapons and laptop computers. Our report identified weaknesses in the DEA’s management of weapons and laptop computers, including purchases, receipts and assignments, transfers, returns of property from employees leaving the DEA, physical inventories, and property disposals.1 We made 22 recommendations in our 2002 report to help the DEA address these deficiencies, such as reiterating policy regarding procedures and controls over weapons and laptops, ensuring losses were reported as required, and maintaining complete, accurate, and current inventory records.
Results in Brief
The purpose of this follow-up audit was to determine whether the DEA has made progress since our 2002 audit concerning its control over weapons and laptops. To assess the DEA’s progress, we performed a comparative analysis using the findings from our 2002 audit and this follow‑up review. We found that the DEA’s rate of loss for weapons more than doubled since the 2002 audit, while the rate of loss for laptop computers declined by more than 50 percent.
Our 2002 audit found that DEA employees were not reporting lost or stolen weapons to the DEA in a complete and timely manner. In addition, the DEA had failed to ensure that all lost or stolen weapons were entered in the National Crime Information Center (NCIC) database. During our follow‑up audit, we found that these same weaknesses have persisted. The DEA has not adequately and promptly reported incidents of lost or stolen weapons and laptop computers to DEA headquarters and has not ensured that lost or stolen property was entered in the NCIC database. The DEA’s failure to report losses and enter relevant information in the NCIC database also reduces the DEA’s chances of recovering this lost property.
The DEA Board of Professional Conduct’s case files did not contain information for 226 of the 231 lost or stolen laptop computers regarding either the content or whether or not the laptop was encrypted. Therefore, the DEA could not provide assurance that 226 of the laptops identified as lost or stolen during our review period did not contain sensitive or personally identifiable information (PII). In addition, since the DEA did not begin to install encryption software on its laptops until November 2006, few of the laptops lost or stolen during our review period were protected by encryption software.
In our 2002 audit we reported that the DEA had significant weaknesses in its internal controls over weapons and laptops. This follow-up audit found that while the DEA has improved its controls and procedural compliance in its physical inventories, the DEA has failed to retain adequate documentation necessary to support laptop acquisitions, disposals, and losses. We also found that because the DEA failed to document laptop serial and property numbers on the DEA Employee Clearance Record forms, the DEA was not ensuring that assigned laptops were returned.
In this follow-up report, we made seven recommendations designed to reinforce the need for the DEA to improve its internal controls governing the accountability of weapons and laptop computers. We again emphasized the need to submit timely and accurate DEA Forms 29 and ensure all losses are promptly entered into the NCIC database. In addition, DEA must submit complete and accurate semiannual Department Theft and DOJ Computer Emergency Response Team (DOJCERT) incident reports.
Our report contains detailed information on the full results of our review of the DEA’s control over weapons and laptop computers. The remaining sections of this Executive Summary address our audit approach and summarize our audit findings.
Audit Approach
In this follow-up audit we conducted our fieldwork at DEA headquarters, headquarters-level offices, and six field division offices. The scope of this 2007 follow-up audit covered the 66-month period between January 2002 and June 2007.
Our work included determining the DEA’s practices and procedures for responding to losses and assessing the DEA’s internal controls over its weapons and laptops. We conducted physical inventories and tested the accuracy and completeness of DEA records for weapons and laptops. We tested DEA-owned and assigned weapons, as well as personally owned weapons authorized for official purposes. We also queried the NCIC database to determine if lost, stolen, or missing weapons and laptops were entered into the database in a timely manner.
Further, we assessed the DEA’s internal and external reporting practices for lost or stolen weapons and laptops. Specifically, we evaluated whether the DEA promptly and appropriately notified the DOJ of incidents of loss. Our audit also examined the actions taken by the DEA in response to lost or stolen weapons and laptops, including whether the DEA determined what information was on the laptop and whether any discipline was imposed. Additionally, we reviewed the DEA’s practices for ensuring that DEA-owned weapons and laptops were returned to the agency by employees leaving the DEA.
Where appropriate, we also compared results from this follow-up review of the DEA to results in our February 2007 follow-up audit of the FBI’s controls over its weapons and laptop computers.2 Specifically, we computed and compared the rates of losses for weapons and laptops per 1,000 agents per year for these two agencies, and we evaluated the circumstances regarding reported losses.
Appendix I contains more information on our audit objectives, scope, and methodology.
Property Management Regulations and Responsibility
The Office of Management and Budget Circular A-123 and the DOJ’s Justice Property Management Regulations require DOJ components to issue detailed operating procedures for protecting federal property against fraud, waste, and abuse. The DEA Property Management Handbook contains guidelines for the general management of property, stating that weapons and laptop computers must receive an asset number, be entered into one of the DEA’s independently operated property subsystems, and be inventoried annually.3
The Firearms Training Unit is responsible for the overall management of the DEA’s inventory of weapons and the DEA’s weapon property system – the Weapons Database, which includes information such as the weapon make, model, serial number, name of the responsible custodian, location, acquisition date, and cost. Each of the DEA’s field divisions has a designated Primary Firearms Instructor assigned to control the weapons inventory for that division. For each headquarters unit, division office, district office, resident office, and foreign country office, a Property Custodial Assistant is designated for property management, including laptop computers. Information on laptop computers is maintained in the DEA’s Fixed Asset Subsystem, including the laptop asset number, serial number, manufacturer, model number, acquisition date, cost, physical location, property condition, and the name of the responsible Property Custodial Assistant.
DEA Lost or Stolen Weapons and Laptop Computers
Our 2002 audit found that over a 26-month period the DEA had 16 weapons and 229 laptop computers lost or stolen. In this follow-up audit, we determined that over a 66-month period 91 weapons and 231 laptop computers were lost or stolen. Comparing the results of these two audits, we found that the DEA’s monthly rate of loss for laptop computers decreased by more than 50 percent, while the rate of loss for weapons more than doubled from 0.61 to 1.37 weapons a month as shown in the following table.4
DEA MISSING WEAPONS AND LAPTOP COMPUTERS
2002 AUDIT COMPARED TO FOLLOW-UP AUDIT
| Category | Number of Lost or Stolen Items Reported |
Losses Reported Per Month |
||
|---|---|---|---|---|
| 2002 Audit | Follow-up Audit |
2002 Audit | Follow-up Audit |
|
| Lost Weapons | 4 | 22 | 0.15 | 0.33 |
| Stolen Weapons | 12 | 69 | 0.46 | 1.04 |
| Total Lost or Stolen Weapons | 16 | 91 | 0.61 | 1.37 |
| Lost Laptop Computers | 2295 | 206 | 8.81 | 3.12 |
| Stolen Laptop Computers | 0 | 25 | 0.00 | 0.38 |
| Total Lost or Stolen Laptops | 229 | 231 | 8.81 | 3.50 |
Weapons Losses
Our follow-up review examined the DEA Board of Professional Conduct case files regarding lost or stolen weapons and laptops. We found many instances when losses occurred despite reasonable precautions taken by DEA employees.6 However, we also found instances when losses resulted from employees failing to follow DEA policy. For instance, the DEA Agents Manual, Section 6122.42 Firearms Security, Safety and Storage, specifically states that DEA-issued and authorized personally owned pistols may not be left unattended or temporarily stored in an official government or privately owned vehicle. Our review found that 44 of the 69 stolen DEA weapons were taken from vehicles. This was similar to our 2007 follow-up audit of the FBI, which reported 58 weapons stolen from vehicles. We determined that the DEA had 1.62 weapons stolen from vehicles per 1,000 agents per year, while the FBI had a lower rate of 1.26 weapons stolen from vehicles per 1,000 agents per year. However, in total the FBI had 3.49 lost or stolen weapons per 1,000 agents per year, while the DEA had 3.36 weapons.
Weapons Stolen From Vehicles and Total Lost or Stolen
Per 1,000 Agents Per Year
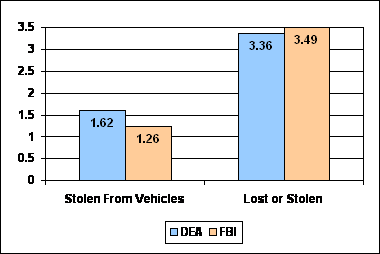
| Source: OIG analysis of DEA and FBI follow-up audit data |
Laptop Computer Losses
Similar to the lost and stolen weapons, we found that many laptop computer losses were avoidable if DEA employees had exercised appropriate diligence and complied with DEA policy. For example, one laptop was left in a taxi and another was stolen from checked luggage. However, we were unable to analyze the circumstances behind the vast majority of laptop losses because the DEA could not provide us with information for 206 of 231 missing laptop computers (89 percent). The DEA identified 149 of these 206 laptops as missing when conducting annual laptop inventories. The remaining 25 laptop computers (11 percent) were reported as stolen from vehicles and other locations such as hotels. Appendix IV includes more detail on reported laptop losses.
Comparing the DEA and FBI follow-up audit results for stolen laptop computers, we found that the DEA and FBI both averaged nearly 1 laptop computer stolen per 1,000 agents annually. In total, the DEA reported 8 laptops stolen from vehicles while the FBI reported 23 laptops.
Laptop Computers Stolen From Vehicles and Total Stolen
Per 1,000 Agents Per Year
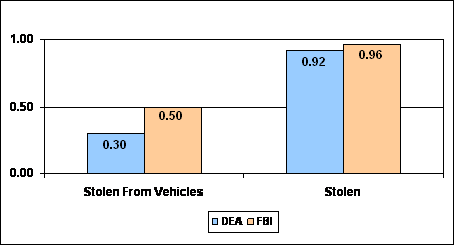
| Source: OIG analysis of DEA and FBI follow-up audit data |
Reporting Lost or Stolen Weapons and Laptops
DEA policy requires the responsible employee to file a police report in the jurisdiction where the loss or theft of a weapon or laptop occurred. The employee or their immediate supervisor also must ensure the weapon is entered in the NCIC database by the local police agency responsible for the jurisdiction in which the loss or theft was reported.7 Within 48 hours of the event, the responsible employee also must submit Part 1 of the DEA Form 29, which is used to record pertinent information related to the loss. (Appendix XI contains a copy of DEA Form 29.)
In October 2002 the DEA Administrator issued a memorandum requiring laptop losses to be reported to the DEA Board of Professional Conduct and the DEA Office of Professional Responsibility within 48 hours of an incident. In the past, lost or stolen weapons and laptops reported by the DEA field offices were only referred by the Board of Professional Conduct to the DEA Office of Professional Responsibility if documentation suggested any form of misconduct related to the loss, theft, or destruction of a weapon or laptop.
On March 30, 2007, the DEA issued an additional policy clarifying reporting responsibilities for lost or stolen weapons. This policy requires all lost or stolen weapons to be referred to the DEA Office of Professional Responsibility, which determines whether it will conduct an investigation or assign the reporting office to perform the investigation.
Data regarding lost or stolen weapons and laptops also must be promptly entered into NCIC so that information is available to law enforcement personnel. The DEA is a non-record entering agency for NCIC, meaning that DEA employees do not enter data into the system, but rather must rely on local law enforcement agencies to perform the task.
Weapon and Laptop Losses Not Reported in a Timely Manner
Similar to our finding in the first DEA audit, we found during this follow‑up audit that the DEA failed to ensure that lost or stolen weapons were reported in a complete and timely manner. While a DEA Form 29 was completed for each of the 91 missing weapons, 37 of the 81 forms (46 percent) were not completed within the 48-hour timeframe.8 We determined that 2 weeks elapsed between the time of the incident and when DEA personnel reported the loss in 19 of the 37 forms (51 percent) submitted after the 48-hour deadline. This failure can hinder timely investigations regarding each loss. In addition, 13 of the 81 forms (16 percent) did not contain critical information such as the correct serial number or whether the weapon was entered into NCIC.
We found similar issues with respect to missing or stolen laptops during our follow-up audit. For example, of the 110 DEA Forms 29 examined for the 231 laptop computers reported missing, 9 forms were submitted within the required timeframe and 31 forms were submitted late.9 Of those 31, 20 were filed anywhere from 15 days to 4.7 years late. However, due to incomplete information, we were unable to determine if the remaining 70 forms were submitted within the 48-hour timeframe.
Contents of Lost or Stolen Laptop Computers
Since October 2002, the DEA has required a statement identifying whether a lost or stolen laptop contained DEA sensitive or classified information when reporting the incident. However, we found that DEA Board of Professional Conduct files contained these statements for only 5 of the 231 laptop computers reported lost or stolen during this 66-month review period. Of the five statements submitted, DEA records indicated that four laptops did not contain sensitive or classified information while the fifth contained sensitive case information.
We asked DEA senior managers what the DEA did to determine the contents of the remaining 226 lost or stolen laptop computers. The DEA was unable to provide information regarding what was on the laptops. The DEA told the OIG that “ DEA is unable to provide, with certainty, assurance that the content of many of these laptops is not sensitive information because it does not remotely (in an automated manner) manage its laptops.” The DEA’s Security Programs Information Security Section Chief stated that an investigator generally attempts to determine what information may have been lost or compromised. However, the Section Chief told us there is no way to determine exactly what was on the laptop unless it is recovered.10 We believe the DEA’s inability to determine what was on the many stolen or missing laptops was a significant failure.
Encryption of Laptop Computers
According to a DEA policy implemented on July 30, 2007, all DEA laptop computers used to process sensitive information must be encrypted.11 As shown in the following table, we determined that as of December 2007, 3,393 of the DEA’s 5,287 laptop computers had been encrypted. As of December 2007, the DEA also reported that 155 additional laptops were in the process of being encrypted, while the remaining 1,739 laptops were exempt from the encryption requirement because they were not used to process sensitive information. According to DEA policy implemented on July 30, 2007, these laptops are used by Special Agents or Investigative Technology Specialists exclusively to support electronic surveillance and other digital monitoring functions.
DEA LAPTOP COMPUTERS ENCRYPTED
Laptops in Use as of December 2007
| Category | Number | Percent |
|---|---|---|
| Encrypted | 3,393 | 64% |
| Exempt | 1,739 | 33% |
| In Progress12 | 155 | 3% |
| Total | 5,287 | 100% |
During our fieldwork in this follow-up audit, we attempted to assess whether laptops reported lost or stolen were encrypted to protect the data and, if not encrypted, what data was on the laptops. Our assessment of the contents of laptops at the field sites we visited consisted of a visual inspection of programs and recently modified files. Our review did not examine the entire contents of the laptops.
We found that 79 of 164 laptops we sampled were not encrypted. Of the 79 laptops that were not encrypted, we identified at least 5 that contained sensitive case-related information or PII. Our limited testing did not find sensitive case information or PII on the remaining 71 laptops.
Entering Losses into NCIC
During the initial audit in 2002, we determined that 6 of the 16 lost or stolen weapons were not entered into the NCIC database. In this follow‑up audit we queried the NCIC database for the 91 lost or stolen weapons and found that 11 were not entered into the database, while 7 of the weapons were entered in the database with incorrect serial numbers.
Regarding laptops, we found that only two DEA Forms 29 contained sufficient documentation showing that the laptops were entered into NCIC. We queried the NCIC database for the lost or stolen laptops and found that 229 of the 231 laptops reported lost or stolen did not have a record in the NCIC database as required by DEA policy.
Internal Controls
Internal controls for management of accountable property are intended to provide reasonable assurance that resources are adequately safeguarded and that reliable data on this property is maintained and properly reported. During this audit, we assessed the DEA’s internal control structure and compliance with procedures for conducting inventories, maintaining sufficient and accurate property records, reporting incidents of loss to the DOJ, accounting for the disposal of property, and ensuring exiting employees remit DEA-issued property.
In our 2002 audit report we found that the DEA did not physically inventory weapons on an annual basis and that the DEA’s separation of duties over weapons inventorying at the Firearm Training Unit was inadequate. We also found that although weapons were excessed to other law enforcement agencies with proper documentation, the DEA failed to ensure that the other agencies actually received the weapons. In addition, although there was a category for weapons on the DEA Employee Clearance Record, (DEA Form 171a, see Appendix XII), the form did not require details of the weapons returned or provide details of the accountable property retrieved from an employee leaving the DEA.13 We examined each of these issues again in the current audit.
Physical Inventories
DEA regulations require an annual inventory of all sensitive capitalized assets and sensitive property items, which include weapons and laptop computers. In our follow-up audit, we reviewed DEA-wide inventory reports from 2002 through 2006 and determined that physical inventories of weapons and laptops were conducted as required.
Reconciling Property Records to the Financial System
In our 2002 audit report, we determined that the DEA’s financial system was not integrated with its weapons inventory system – the Weapons Database – to ensure inventory accuracy. In addition, the financial system did not include an audit function that allowed edits made to the Weapons Database to be tracked by an automated exception report. The DEA’s financial system also had not been fully integrated with its Fixed Asset Subsystem. As a result, the systems did not automatically verify that the number of laptops actually purchased agreed with the number of items placed into inventory. To improve the controls over its weapons and laptop computer inventories, we recommended that the DEA develop internal controls to ensure the reliability of inventories in the Weapons Database and integrate its financial and property management systems so that inventory would be routinely updated as laptops were purchased.
In our follow-up review, we found that the DEA’s financial system still is not integrated with its Weapons Database. However, we consider control procedures, such as providing field components with inventories for reconciliation purposes and verifying the accuracy of the Weapons Database by Primary Firearm Instructors through a physical inventory implemented by the DEA since our prior audit, to be sufficient for ensuring that information in the Weapons Database is accurate and complete. In addition, all entries into the Weapons Database were completed by the Firearms Training Unit at Quantico, Virginia, which incorporated appropriate separation of duties.
With respect to laptops, we found that the DEA’s financial system is fully integrated with its Fixed Asset Subsystem, which accounts for laptops, and the DEA had properly segregated the duties of staff taking physical inventories, performing reconciliations, and modifying the property management system.
Accuracy and Completeness of Inventory Records
In our 2002 audit we tested the accuracy and completeness of the Weapons Database and the Fixed Asset Subsystem. On a sample basis we selected weapons from the Weapons Database and laptop computers from the Fixed Asset Subsystem to physically verify their existence. The DEA provided all weapons and laptop computers for our physical verification.
During our follow-up audit we tested 4,331 DEA-owned and 763 personally owned weapons. We were able to verify 4,320 (99.7 percent) of the sampled DEA-owned weapons and all 763 of the personally owned weapons we sampled. The DEA was unable to account for 11 weapons in our sample. The DEA believed seven of these weapons were destroyed but had no supporting documentation concerning their destruction. For the remaining four weapons, two were issued to Special Agents on assignment, one weapon was an erroneous entry into the Weapons Database, and the last weapon was a non-functional training weapon that could not be located.
We conducted similar testing on a sample of DEA laptop computers. Our sample comprised 3,007 of the DEA’s 7,381 total laptop computers. We considered that the DEA accounted for the laptop if it was able to present the laptop for our verification or provide documentation supporting that the laptop existed. We also accepted documentation showing that the laptop was lost, stolen, destroyed, or surplused after the date of our statistical sample. The DEA was unable to account for 42 of the 3,007 sampled laptops (1 percent). Additionally, we found 20 laptops assigned to DEA headquarters components were not entered in the Fixed Asset Subsystem, and the DEA took immediate corrective action by adding these laptops to the inventory.
Reporting Losses to DOJ
DOJ regulations require all components to submit to DOJ semiannual reports on January 1 and July 1 summarizing the loss or theft of government property that occurred within the preceding 6 months. 14 In our 2002 audit, we found that the DEA did not submit any semiannual Department Theft Reports for 1999 and 2000, and the first semiannual report for 2001 was submitted 36 days late. In addition, the semiannual reports submitted by the DEA were inaccurate with respect to the number of weapon losses.
For this follow-up audit we again tested the DEA’s submission of semiannual Department Theft Reports. We also analyzed the DEA’s compliance with DOJ regulations requiring all components to immediately notify the Department of Justice Computer Emergency Response Team (DOJCERT) of incidents involving the loss of laptops.
DOJ Semiannual Reports – Our follow-up review found that the DEA has not corrected its deficiency in reporting to the DOJ on the weapons and laptop computers that were lost or stolen during semiannual reporting periods. During the time period covered by our audit, 11 semiannual Department Theft Reports were required to be submitted to the DOJ. However, the DEA was only able to provide, and DOJ only had on file, 3 of the 11 semiannual reports required during our testing period.
We reviewed the three semiannual Department Theft Reports submitted by the DEA during our audit period, and found that one report was complete, but the other two reports contained errors and omissions. While two of the three reports were submitted in a timely manner, we were unable to determine if the third report was submitted when required. We asked the DEA Deputy Assistant Administrator, Office of Administration, about the remaining eight reports. She told us that the administrative clerk who prepared the semiannual theft reports typed over the prior report and failed to retain a paper or electronic copy of the reports.
In addition, we found that the DOJ Justice Management Division was not aware of 67 weapons and 176 laptops that were lost or stolen during our review period because the DEA did not submit the required semiannual Department Theft Reports. Only 20 weapons and 24 laptops were reported to the Justice Management Division as required by DOJ regulations.
DOJCERT Notification - The DOJCERT assists in handling computer security incidents throughout DOJ. DOJCERT officials told us that DOJCERT was not required to track or report lost or stolen DEA laptops prior to May 2006. We identified 15 lost or stolen laptops from May 2006 through June 2007 that had been reported to the DEA’s Board of Professional Conduct. However, DOJCERT only received reports from the DEA on three laptops during this time period.
Disposal of Weapons and Laptop Computers
In our 2002 audit report we found that DEA weapons excessed to other law enforcement agencies were supported by proper documentation. However, the DEA failed to follow up with these law enforcement agencies to ensure that the shipped weapons were actually received. We recommended the DEA ensure that the Firearms Training Unit document confirmations for receipt of the weapons. In our previous audit, we did not note any problems with the DEA’s procedures for the disposal of laptops.
During our follow-up audit we selected a statistical sample of 295 weapons (43 destroyed and 252 surplused) from a universe of 7,300 excessed and destroyed weapons from January 2002 through February 2007. We found appropriate supporting documentation for all items tested, including confirmations from local law enforcement agencies that received the surplused weapons.
Additionally, we selected a sample of 166 laptops from a universe of 3,214 excessed and destroyed DEA laptop computers. The DEA could not provide sufficient supporting documentation for 15 of these 166 laptops tested (9 percent). For 13 of these 15 instances, we found that DEA did not retain any supporting documentation concerning the disposal. The DEA was unable to provide sufficient documentation to support the disposal for the other two instances.
We also found that the DEA’s laptop disposal process is decentralized and that supporting documentation is maintained at each DEA location worldwide. During our testing, the DEA was unable to provide the OIG with requested disposal documentation in a reasonable amount of time. We believe the DEA should retain copies of all disposal documentation at centralized locations in each division office to manage the program more effectively, enable quicker reconciliations, and provide adequate audit trails. This added control would also elevate the DEA’s oversight over laptop disposals and increase the overall accountability for excessing laptops.
Exit Procedures for Departing Employees
In our 2002 audit report we found that although there was a category for weapons on the DEA’s Employee Clearance Record, details of the weapon were not included on the form, such as serial numbers or property description. In addition, the form did not require information about what type of accountable property was retrieved from an employee who left the DEA.
During our follow-up audit we reviewed Employee Clearance Records at DEA field division offices for departing employees between January 1, 2005, and August 2, 2007. Our testing found that the DEA was appropriately completing the weapons section on the Employee Clearance Records, providing the DEA an important control over the weapons assigned to departing employees. However, we found that the DEA was still not documenting the Employee Clearance Records with specific details on laptop computers, such as serial number, property numbers, and make and model, returned by departing employees. Due to the lack of any specific details identifying laptop computers, we were unable to determine from this form whether DEA‑issued laptop computers were returned by departing employees.
Conclusions and Recommendations
Our follow-up audit found that the DEA decreased its rate of loss for laptop computers since our 2002 audit by more than 50 percent. In our prior audit report, we reported that the DEA could not determine if any of the lost, missing, or stolen DEA laptop computers resulted in a compromise of investigative information. In this audit, we found that the DEA still could not determine what was on its lost or stolen laptops. We found that for 226 of the 231 lost or stolen laptops reported in our follow-up audit review period, the DEA is unable to provide any assurance that the lost or stolen laptops did not contain sensitive information.
In addition, we found in this audit that the number of losses and the loss rate for weapons more than doubled from 0.61 to 1.37 per month since our last review.
The DEA has taken several steps since our 2002 audit to improve its ability to account for lost or stolen weapons and laptops computers. For instance, we found that the DEA performed annual physical inventories of weapons and laptops and reconciled these inventories to its financial system records.
However, this follow-up audit found that the DEA still requires significant improvements in its overall control over weapons and laptops. The DEA must ensure that DEA policy and guidelines are consistently enforced when an incident of loss or theft occurs. We found that the DEA did not sufficiently and promptly report incidents of loss to DEA headquarters or DOJCERT. Additionally, the DEA was not ensuring that lost or stolen weapons and laptops were entered in the NCIC database as required by DEA policy. These findings mirror weaknesses that we identified in our 2002 audit. Further, the DEA was unable to provide assurance that lost or stolen laptops did not contain sensitive information, failed to effectively maintain documentation for disposal of laptops, failed to submit required semiannual reports of weapon and laptop losses to the DOJ, and failed to adequately ensure that property was recovered from employees before separating from employment with the DEA.
This audit report contains seven recommendations related to ensuring compliance with DEA policies and reporting requirements. Specifically, we recommend that the DEA accurately and promptly report weapon and laptop losses to its headquarters and the appropriate DOJ components, revise its encryption policy to require that all laptops be encrypted, ensure that firearms and laptop property losses are entered in the NCIC database and verified by management for accuracy, and verify that property issued to departing employees is adequately documented and retrieved upon separation.
U.S. Department of Justice Office of the Inspector General. The Drug Enforcement Administration’s Control over Weapons and Laptop Computers, Audit Report 02-28, (August 2002).
U.S. Department of Justice Office of the Inspector General. The Federal Bureau of Investigation’s Control over Weapons and Laptop Computers Follow-Up Audit, Audit Report 07-18, (February 2007).
At the time of our audit, the DEA Property Management Handbook was being revised.
Because the audit periods were different lengths, we analyzed the rate of loss on an equivalent monthly basis. Our review period for the 2002 audit covered 26 months, from October 1, 1999, to November 30, 2001. Our review period for the follow-up audit covered 66 months, from January 1, 2002, to June 30, 2007.
The DEA reported that 229 laptops were unaccounted for during the prior audit. The DEA was unable to provide any details as to the number of lost versus stolen laptops.
Board case files contain copies of the DEA Form 29, a property/accident synopsis form that briefly describes the incident, what was lost or stolen, the responsible individual, the proposed disciplinary action, and the final disciplinary action taken. This file also includes a copy of the letter of proposed disciplinary action, documents regarding the proposed disciplinary action, and copies of any other investigation results.
The NCIC is a database of criminal justice information, such as criminal record history, fugitives, stolen property, and an index of individuals incarcerated in the federal prison system. Criminal justice agencies enter records into NCIC, which are then accessible to law enforcement agencies nationwide.
We reviewed 81 DEA Forms 29 reporting the loss of 91 weapons. Multiple weapons lost in a single incident are reported on a single DEA Form 29.
In addition, as we explain in the next section, nearly all of the 231 laptop losses reported during our 66-month review period occurred before DEA began encrypting laptops.
On March 28, 2007, the DEA submitted a memorandum to the DOJ Chief Information Officer requesting a 60-day extension to May 31, 2007, for meeting the DOJ requirement to ensure that all unclassified laptops had encryption to protect sensitive data. This memorandum noted that the DEA began encrypting laptop computers in mid‑November 2006. The DOJ Chief Information Officer approved the DEA’s request. According to DEA policy implemented on July 30, 2007, all laptop computers used to process sensitive information must be encrypted.
DEA officials informed us that these laptops were assigned to personnel in temporary duty status, have compatibility issues with the encryption software, require additional memory, or need batteries.
The DEA Employee Clearance Record is a form used by DEA to document that an exiting employee has returned badges, credentials, weapons and other property and has cleared various internal departments such as finance and procurement.
DOJ Order 2630.2A, Protecting and Controlling Federally Controlled Property and Loss/Theft Reporting Procedures.