The United States' efforts to control drugs and narcotics, through a number of offices and agencies, date back to 1915. In July 1973, the President established the Drug Enforcement Administration (DEA) within the Department of Justice (Department) as the successor to the Bureau of Narcotics and Dangerous Drugs.
The DEA's mission is to: 1) enforce the controlled substances laws and regulations of the United States; 2) bring to justice those individuals or organizations involved in the growing, manufacturing, or distributing of controlled substances destined for illicit traffic in the United States; and 3) reduce the availability of illicit controlled substances in the domestic and international markets. The DEA's primary responsibilities include the:
- investigation of major violators of controlled substance laws for prosecution;
- management of a national drug intelligence program in cooperation with federal, state, local, and foreign officials to collect, analyze, and disseminate strategic and operational drug intelligence information;
- seizure and forfeiture of assets derived from or used in illicit drug trafficking;
- enforcement of the Controlled Substances Act pertaining to the manufacture, distribution, and dispensation of legally produced controlled substances;3
- coordination and cooperation with federal, state, and local law enforcement officials on mutual efforts for drug enforcement and reduction of illicit drug availability in the United States; and
- management of programs associated with drug law enforcement counterparts in foreign countries and liaison with the United Nations, Interpol, and other organizations on international drug control programs.
To accomplish its mission, the DEA's headquarters in Arlington, Virginia, oversees 237 domestic offices and 80 foreign offices in 58 countries. As of FY 2003, the DEA had approximately 4,680 special agents and 4,949 support staff. From FY 2003 to FY 2004, the DEA's budget increased from $1.660 billion to $1.677 billion.4 Information technology (IT) is essential to the DEA's ability to properly manage its operations and administrative functions. Funding for the DEA's IT-related projects increased from $201 million in FY 2003 to $224 million in FY 2004.
The Information Technology Management Reform Act of 1996 (known as the Clinger-Cohen Act) requires the head of each federal agency to implement a process for maximizing the value of the agency's IT investments and for assessing and managing the risks of its acquisitions. A key goal of the Clinger-Cohen Act is for agencies to have processes in place to ensure that IT projects are being implemented at acceptable costs and within reasonable timeframes, and that the projects are contributing to tangible, observable improvements in mission performance. In addition, the Clinger-Cohen Act requires the head of each agency to develop, maintain, and facilitate the implementation of architectures as a means of integrating business processes and agency goals with IT.
The Office of Management and Budget (OMB) Circular A-130 requires each federal agency to establish and maintain a capital planning and investment control process for IT (also known as Information Technology Investment Management, or ITIM). As described more fully in Appendix 3, the ITIM process has three components: select, control, and evaluate. The process integrates the agency's strategic and financial management plans and its acquisition and budget processes. Further, the process helps shape the agency's Enterprise Architecture (EA), which provides a strategy that will enable the agency to support its current state and also act as the roadmap for transition to its target environment.
The following chart describes the fundamental phases of this IT investment approach.
Fundamental Phases of the IT Investment Approach
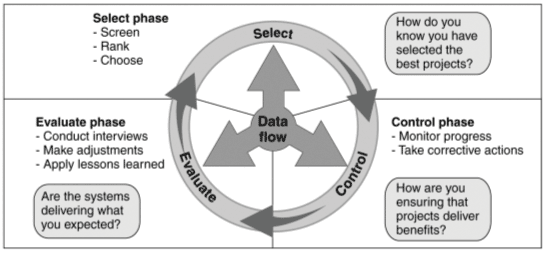
Source: The U.S. Government Accountability Office (GAO).
| There are 3 different phases to the data flow - Select, Control and Evaluate.
Select phase
How do you know you have selected the best projects? Control phase
How are you ensuring that projects deliver benefits? Evaluate phase
Are the systems delivering what you expected? |
In August 2001, the Department of Justice Information Technology Investment Management Process (Guide) was issued to implement the Clinger-Cohen Act, OMB Circular A-130, and other IT management requirements. The Guide is intended to help make measurable improvements in mission performance and service delivery to the public through the strategic application of IT.
In doing so, the Guide uses the select/control/evaluate methodology to implement the strategic and performance directives of the Clinger-Cohen Act and other requirements affecting IT investments. The Guide is also intended to promote a process that builds on existing structures to provide maximum benefit across the Department and with other federal agencies. This process is intended to allow the Department to focus IT management on the Department's strategic missions. Further, the process establishes investment review procedures that drive budget formulation and execution for IT systems, and it provides the methods, structures, disciplines, and management framework that govern the way IT is deployed throughout the Department. The Guide applies to all IT projects in all of the Department's components, and requires each Departmental component to:
- designate a component Chief Information Officer (CIO);
- establish an Executive Review Board that will approve the entire component IT portfolio and oversee the decisions made about specific investments; and
- establish a component ITIM process that incorporates the Department's ITIM process but is customized to function within the component's unique environment.
By January 2002, each component was required to submit to the Department an ITIM plan incorporating the above items. The DEA submitted its ITIM plan in December 2001. The JMD officially approved the DEA's Plan in March 2002. The 2002 approval letter states that the DEA ITIM process conforms to the guidelines defined by the GAO, the OMB, and the Department. It also states that the plan is clear and comprehensive in its statement of the ITIM policy and its definition of organizational roles, responsibilities, and deliverables.
To date, the Department has not issued any formal guidance on EA. However, according to the Assistant Director of the Department's Policy and Planning Staff within the Office of the Chief Information Officer, the order providing such guidance should be released in the first quarter of FY 2005. To begin developing its EA, the DEA used guidance from the OMB, the Federal Chief Information Officer's Council, and the DEA's Strategic IT Plan to develop its EA program.
We identified and reviewed six IT-related reports issued since May 2000 by the GAO and the OIG that are applicable to aspects of this audit.
In May 2000, the GAO reported that although almost all federal agencies had created some type of ITIM process, none had implemented stable processes that address all three phases of the select/control/evaluate approach.5 According to the GAO, one barrier to implementing reliable ITIM has been the lack of specific guidance on the required processes. The GAO further stated that the select/control/evaluate approach provides sound advice, but does not describe the organizational processes involved.
In February 2002, the GAO reported that the federal government as a whole had not reached a mature state of EA management.6 In particular, about 52 percent of federal agencies reported having at least the management foundation that is needed to begin successfully developing, implementing, and maintaining an EA, and about 48 percent of agencies have not yet advanced to this basic stage of maturity. Specifically, the GAO determined that the DEA had achieved Stage-2 maturity. At Stage-2 maturity, the DEA established a sound EA management foundation with the assignment of roles and responsibilities and the establishment of plans for developing EA products.
In March 2002, pursuant to the FY 2001 Government Information Security Reform Act, the OIG issued three reports on three of the DEA's administrative and investigative IT systems.7 The reports identified vulnerabilities with management, operational, and technical controls. Significant vulnerabilities were noted in the following areas:
- security policies, procedures, standards, and guidelines;
- system and network backup and restoration controls;
- password management;
- log-on management;
- account integrity management;
- system auditing management;
- physical controls;
- software upgrading procedures;
- personnel controls;
- contingency planning; and
- system configuration.
The reports also stated that these vulnerabilities occurred because the DEA either lacked sufficient guidance, did not fully enforce compliance with existing security policies, did not develop a complete set of policies to effectively secure the systems, or lacked timely and effective oversight from the Department and DEA management in addressing known problems.
In February 2004, pursuant to the Federal Information Security Management Act (FISMA), the OIG issued a report on the DEA's system used to access and analyze classified information. The report assessed the system's compliance with FISMA and related information security policies, procedures, standards, and guidelines. The report identified weaknesses in the areas of management, operational, and technical controls. The report also identified high-risk vulnerabilities from unauthorized use, loss, or modification of data.
The report stated that the vulnerabilities occurred because the DEA did not always enforce its policies in accordance with current Department policies and procedures for the system. Furthermore, many of the vulnerabilities identified during this audit could have been prevented if the DEA had followed up on and applied corrective actions for similar vulnerabilities identified by the DEA and OIG in previous years and applied them to the system.
This report dealt primarily with the DEA's management of information security and not the agency's handling of IT investments or its EA. However, according to the CIO Practical Guide, an agency is required to address information security within its EA. The DEA has documented in its EA Program Plan that information security will be addressed as a separate layer within the target architecture, which has not yet been developed.
Framework for Assessing IT Investment Management
To address the lack of guidance as reported in its May 2000 report, the GAO developed the IT Investment Management Framework (ITIM Framework) to provide a common methodology for discussing and assessing IT capital planning and investment management practices at federal agencies.
According to the GAO, the ITIM Framework enhances previous federal IT investment management guidance by embedding the select/control/evaluate approach within a framework that explicitly describes the organizational processes required to implement sound ITIM. Based on the best practices of leading organizations, the ITIM Framework is a hierarchical model comprised of five maturity stages, which represent steps toward achieving stable and mature investment management processes. Each stage builds upon the lower stages and enhances the organization's ability to manage its investments. As an agency advances through these stages, the agency's capability to effectively manage IT increases. In March 2004, the GAO revised the ITIM Framework to reflect the incorporation of EA into all five maturity stages. Our assessment of the DEA's IT investment management was done using the revised framework.
The following chart describes the five maturity stages of the IT Framework.
| The Five Stages of Maturity Within ITIM
[Image not available electronically] Source: The U.S. Government Accountability Office. |
With the exception of the first stage, each maturity stage is comprised of critical processes that must be implemented and institutionalized for the organization to satisfy the requirements of that stage. These critical processes are further broken down into key practices that describe the types of activities in which an agency should be engaged to successfully implement each critical process. An organization that has these critical processes in place is in a better position to successfully invest in IT. The following chart describes the ITIM Framework's five stages and associated critical processes.
| The ITIM Stages of Maturity With Critical Processes
[Image not available electronically] Source: The U.S. Government Accountability Office. |
As established by the ITIM Framework, each critical process is comprised of five core elements that indicate whether the implementation and institutionalization of a process can be effective and replicated. The five core elements are: 1) purpose, 2) organizational commitment, 3) prerequisites, 4) activities, and 5) evidence of performance.
With the exception of the "purpose" core element, each of the other core elements contains key practices. The key practices are the attributes and activities that contribute most to the effective implementation and institutionalization of a critical process. The following chart summarizes the inter-relationships of components in an ITIM critical process.
| Components of an ITIM Critical Process
[Image not available electronically] Source: The U.S. Government Accountability Office. |
Framework for Assessing and Improving Enterprise Architecture Management
Enterprise Architectures provide a clear and comprehensive picture of an entity, whether an organization or a functional or mission area that crosscuts more than one organizational unit. According to the GAO, investing in IT without defining these investments in the context of an EA often results in systems that are duplicative, not well integrated, and unnecessarily costly to maintain and interface.
An EA is made up of four components: Business Architecture, Applications Architecture, Data Architecture, and Technical Architecture. Together, these components provide a clear picture of how an organization accomplishes its mission, goals, and objectives. It also provides the baseline from which initiatives are planned and later compared.
Business Architecture focuses on "what" is done as opposed to "who" does it. It captures the business itself, independent of any technology, by describing the business areas and processes including common information requirements. Business Architecture is based on an agency's strategic plan and is linked to the application, data, and technology layers of the EA.
Applications Architecture is the means by which the agency and its personnel create, reference, update, or delete data acquired and collected by an agency. In essence, Application Architecture provides the link between the data and the entities required to perform the business functions, allowing an agency to fulfill its mission.
Data Architecture describes the data an agency needs for business operations and provides a data-related viewpoint. Data Architecture consists of universally accepted definitions that an agency uses to describe data. Completed Data Architecture provides an overall picture of the information an agency collects, manipulates, and stores in order to accomplish its mission.
Technical Architecture provides the platform for many business operations, the applications, and the enterprise data. Technical Architecture is what allows the entities performing business functions to use applications to manipulate the data necessary for an agency to accomplish its mission.
Since the late 1980s, EA Management Frameworks have emerged within the federal government, beginning with the publication of the National Institute of Standards and Technology framework in 1989. In 1992, the GAO issued EA guidance entitled Strategic Information Planning: Framework for Designing and Developing System Architecture. This EA Management Framework was intended to:
- provide a basis for systematically determining information needs,
- identify and analyze information and data needs and relationships,
- identify and analyze alternative ways to satisfy information needs, and
- provide factors to be considered in arriving at the best way to satisfy information needs.
Since 1992, other federal entities have issued EA Management Frameworks, including the Department of Defense, the Department of the Treasury, and the Federal Chief Information Officers Council (CIO Council). Although the various frameworks use different structures, the frameworks are fundamentally consistent in purpose and content, and are being used today to varying degrees by many federal agencies.
In April 2003, the GAO, in collaboration with the OMB and the CIO Council, published a new EA Management Framework.8 The new EA Management Framework provides measures for management to assess progress toward the desired end and to take corrective action to address unacceptable deviations.
The GAO EA Management Framework consists of three basic components: 1) five hierarchical stages of management maturity, 2) categories of attributes that are critical to the success in managing any endeavor, and 3) elements of EA management that form the core of the CIO Council's Practical Guide.9
Consistent with the ITIM Framework, the EA Management Framework outlines five maturity stages. These stages include steps toward achieving a stable and mature process for managing the development, maintenance, and implementation of an agency's EA. As an organization improves its EA management capabilities, its EA management maturity increases.
With the exception of the first stage, each maturity stage is composed of four critical success attributes that are critical to the successful performance of any management function. They are:
- Demonstrates Commitment by the head of the enterprise providing support and sponsorship to achieve the success of the EA effort.
- Provides the Capability to Meet Commitment by developing, maintaining, and implementing EA through adequate resources, clear definitions of roles and responsibilities, and implementing organizational structures and process management controls that promote accountability and effective project execution.
- Demonstrates Satisfaction of Commitment to develop, maintain, and implement EA by producing EA plans and products.
- Verifies Satisfaction of Commitment by measuring and disclosing the extent to which efforts to develop, maintain, and implement the EA have fulfilled stated goals or commitments. Measuring performance allows for tracking progress toward stated goals, allows appropriate actions to be taken when performance deviates significantly from goals, and creates incentives to influence both institutional and individual behaviors.
Collectively, these attributes form the basis by which an organization can institutionalize management of any given function or program, such as EA management. Each attribute contains core elements that contribute to the effective implementation and institutionalization of a critical success attribute. Appendix 4 summarizes the interrelationships of components in the EA management process.
The DEA's Management of IT Infrastructure
The DEA seeks to manage its IT investments through agencywide repeatable processes rather than a single office. To illustrate the processes, the DEA has created a graphic illustration called "The House" (see Appendix 5) showing how strategic planning, budgeting, procurement, ITIM, quality management, IT security, System-Development Life-Cycle program management, and EA work together to accomplish the DEA's mission. In reference to ITIM and EA, The House shows how each phase of the ITIM process relates to one or more of the architectural models. For example, by consulting The House, a DEA staff member can see that in the Control Phase of ITIM, the Data, Application, and Technology architectures should be reviewed before making a decision about the status of the project.
Reflecting the DEA's decentralized ITIM, several divisions manage major IT initiatives: the Operations Division, the Intelligence Division, the Financial Management Division, the Operational Support Division, and the Inspection Division. These divisions are responsible for specific networks and applications supporting their respective missions.
The Office of Diversion Control, within the DEA's Operations Division, manages the design, development, and operation of the infrastructure and applications supporting DEA programs with the medical community and the chemical and pharmaceutical industries. The DEA's Intelligence Division manages the classified network and the associated applications. The El Paso Intelligence Center, within the Intelligence Division, develops and manages infrastructure and applications that support customers at the federal, state, and local levels. The Financial Management Division is responsible for managing the DEA's financial management systems.10
The DEA Chief Information Officer is the Assistant Administrator for the Operational Support Division, and reports to the DEA Administrator. The Deputy CIO is the Deputy Assistant Administrator for the Office of Information Systems and reports to the CIO. The Deputy CIO is responsible for the design, deployment, and operation of DEA's general support networks, the majority of application systems supporting DEA's mission, and the supporting quality management program. Staff in the Office of Information Systems work closely with customers from virtually all DEA offices, both in headquarters and the field (domestically and internationally). The Deputy CIO also manages the DEA-wide programs for IT strategic planning, IT capital planning and investment control, and EA.
The Office of Information Systems coordinates with each office to ensure that the procedures and applications developed by these offices are in compliance with the DEA-wide programs for IT strategic planning, IT capital planning and investment control, and the EA. The Office of Investigative Technology is responsible for the systems that support telecommunications intercepts.
The Office of Security Programs in the Inspection Division is responsible for DEA's IT security program. This includes development of policies and procedures, management of system certification and accreditation, coordination with the Department of Justice, reporting as required by the FISMA, and security monitoring of DEA networks.
Recent Efforts
The DEA has established three governing committees to facilitate its EA and ITIM development processes: 1) the Executive Review Board, 2) the Business Council, and 3) the Compliance Council. Together, the three governing committees are responsible for ensuring that the DEA's EA and ITIM meet all federal and Departmental requirements. The Executive Review Board is responsible for providing leadership to implement a managed IT capital planning and investment control process. The IT capital planning and investment process includes the development and maintenance of an agencywide EA. The DEA's CIO and the DEA's Chief Financial Officer (CFO) jointly chair the Executive Review Board.
The Business Council is responsible for ensuring that projects and investments recommended by program managers are consistent with the DEA's mission, strategic plan, capital planning goals, EA, and security policy. The Deputy Assistant Administrator, Office of Information Systems, chairs the Business Council.
The Compliance Council is responsible for evaluating IT investments and the DEA's EA to ensure compliance with legislative regulations and DEA policy. The Chief of the Strategic Business Management Section, Office of Information Systems, who is also the Chief Architect, chairs this committee.
In accordance with OMB guidance and best practices as outlined by the Federal CIO Council, the DEA has begun the construction of an EA. At the time of our audit, the DEA had completed a high-level "as is" EA. A high-level "as is" EA is a representation of current capabilities and technologies and is expanded as additional segments are defined.
The DEA's high-level "as is" EA defines four architectural layers: 1) the business processes to accomplish the mission, 2) the information, 3) the software applications supporting the business, and 4) the technology necessary to perform the mission. The DEA's CIO has approved the DEA's high-level "as is" EA.
As stated previously, in December 2001 the DEA developed the "ITIM Process and Transition Plan" in an effort to improve its IT investment management practices and comply with the Department's and other statutory regulations. The purpose of the plan is to better ensure that technological resources are linked to the DEA mission and IT Strategic Plan while providing a solid return on investment. According to the plan, the DEA would phase in ITIM over three years, in three phases ending in FY 2004. Each phase would correspond to one fiscal year. Phase 1 would focus on the business and budget side of ITIM, while Phases 2 and 3 would focus on the technical side. Also, in Phase 2 ITIM would integrate security activities, and in Phase 3 ITIM would integrate EA activities.
The following excerpts from the plan provide an overview of how the DEA's select, control, and evaluate processes for ITIM are intended to operate.
Select
During the Select Phase, new projects are introduced to the Executive Review Board for consideration. A program manager prepares a Concept Proposal for funding consideration by the Executive Review Board.11 When completed, the program manager sends the Concept Proposal to the ITIM Management Group to be processed through the Business Council and the Executive Review Board. If the Executive Review Board determines that the concept has merit, then the program manager may spend an initial amount of money to prepare a business case for inclusion in the budget process.12
Control
During the Control Phase, funded investments are under development. A program manager submits monthly status reports to the ITIM Management Group for analysis. These reports include expenditures and work completed to date. The ITIM Management Group collects this information for the entire portfolio, analyzes the data, and identifies investments that might be at risk. The ITIM Management Group follows up with at-risk investments to determine if problems exist and how the problems should be solved.
Evaluate
During the Evaluate Phase, all IT investments currently in operation or maintenance and in need of continued funding are monitored to ensure that the investment is appropriately managed and continues to produce expected results and mission benefits. Periodic progress reviews are conducted to evaluate the investment's continued value to mission benefits and alignment with EA direction. The Business Council predetermines which investments are candidates for retirement or upgrade, and passes this recommendation to the Executive Review Board, which uses this information for funding decisions.
The JMD officially approved the DEA's Plan in March 2002. The March 2002 approval letter states that the DEA ITIM process conforms to the guidelines defined by the GAO, the OMB, and the Department. Further, it states that the Plan is clear and comprehensive in its statement of the ITIM policy and its definition of organizational roles, responsibilities, and deliverables.
Footnotes
- The Controlled Substances Act Title, II of the Comprehensive Drug Abuse Prevention and Control Act of 1970, is the legal foundation of the government's fight against the abuse of drugs and other substances. This law is a consolidation of numerous laws regulating the manufacture and distribution of narcotics, stimulants, depressants, hallucinogens, anabolic steroids, and chemicals used in the illicit production of controlled substances.
- The budget excluded Federal Retirees and Health Benefit Costs.
- The report is entitled Information Technology Investment Management: An Overview of GAO's Assessment Framework (GAO/AIMD-00-155) dated May 2000.
- The report is entitled Information Technology, Enterprise Architecture Use Across the Federal Government Can Be Improved (GAO-02-6) dated February 2002.
- The three systems audited were the El Paso Intelligence Center Information System (02-09), Merlin System (02-13), and Firebird System (02-10).
- The framework is entitled Information Technology, A Framework for Assessing and Improving Enterprise Architecture Management, Version 1.1, (GAO-03-584G) dated April 2003.
- Federal Chief Information Officers (CIO) Council. A Practical Guide to Federal Enterprise Architecture, Version 1.0, February 2001. This publication is also known as the CIO Council's Practical Guide, which is a step-by-step process guide intended to assist agencies in defining, maintaining, and implementing EAs by providing a disciplined and rigorous approach to EA management.
- For a further breakdown of how DEA divisions are laid out, see the DEA Organization Chart in Appendix 6.
- The Concept Proposal is a 2- to 5- page document that presents a high- level concept for a new investment. At this stage, the document represents an idea that the program manager wishes to bring to the attention of the Executive Review Board for funding consideration.
- The funding for preparing the business case is not included as a line item within the DEA's approved budget. The program manager must find alternative resources to produce the business case.