I. ATF’S RESPONSE TO WEAPON, LAPTOP COMPUTER, AMMUNITION, AND EXPLOSIVES LOSSES
During our 59-month review period, ATF reported 76 weapons and 418 laptop computers as lost, stolen, or missing, including 7 laptop computers that contained sensitive information. Of the 76 weapons, 35 were reported as stolen, 19 were reported as lost, and 12 were reported as missing during periodic inventories. ATF was unable to document what happened to the 10 additional weapons.
Of the 418 lost, stolen, or missing laptop computers, 274 were identified as missing during periodic inventories, 50 were reported as stolen, and 8 were reported as lost. ATF could not provide information about the remaining 86 lost, stolen, or missing laptop computers because the records had been destroyed in accordance with ATF’s record retention cycle or could not be found.
We found that ATF investigated laptop computer losses reported to Internal Affairs but did not investigate most laptop computer losses because they were not reported to Internal Affairs. ATF officials could not provide documentation showing whether 398 of the 418 lost, stolen, or missing laptop computers contained sensitive or classified information.
In addition, ATF did not consistently enter all lost, stolen, or missing weapons into the National Crime Information Center (NCIC) database as required. ATF made preliminary investigations into all reported losses of ammunition and explosives and found no employee misconduct.
We interviewed ATF officials, reviewed policies and investigative reports, and obtained and analyzed property records to determine the number of weapons and laptop computers lost, stolen, or missing between October 1, 2002, and August 31, 2007. We found that 76 weapons and 418 laptop computers were lost, stolen, or missing during this 59-month period.
Of the 76 weapons, 35 were reported stolen, 19 were reported lost, and 12 were reported missing. ATF was unable to document what occurred in the other 10 cases.
Of the 418 laptop computers, 50 were reported stolen, and 8 were reported lost. We could not specifically determine whether 86 laptop computers were lost, stolen, or missing because the records had been destroyed or were not found.
The remaining 274 laptop computers are those that ATF officials identified as missing during periodic inventories.18 While ATF officials offered several explanations for these items, they were unable to document adequately the circumstances or dispositions of the 274 missing laptop computers, and we included them in our totals of lost, stolen, or missing laptop computers.19 Further details about the lost, stolen, or missing items are included throughout this finding.
To investigate the 274 laptop computers reported as missing, we interviewed property management officials and reviewed property management policies and the documented results of periodic ATF inventories. Officials told us the contractor that leases laptop computers to ATF provided an electronic list of laptop computers that were scheduled for shipment to various offices and ATF staff used that list to update its property records electronically. However, according to ATF officials, many of those laptop computers were sent to other locations.20 As a result, ATF officials said the property records were incorrect. In June 2004, ATF created a separate account in its property management system to account for the pool of laptop computers belonging to the contractor that have yet to be issued to ATF employees.
We also reviewed documentation of inventory results submitted to ATF headquarters. Those documents explain that field offices at one time had the missing laptop computers in their possession but the disposition of those laptop computers was not documented. For example, one field office official believed 31 laptop computers that could not be located during an annual inventory had been returned to the contractor without the associated paperwork. Another field office official believed 29 laptop computers were missing due to the contactor’s failure to provide paperwork when removing or replacing the laptop computers. Other field office officials believed the laptop computers were “missing” due to donations and computer refreshes that were not documented. However, without documentation there is no way of knowing what happened to those “missing” laptop computers.
These explanations could be the causes for the large number of laptop computers identified as missing during periodic ATF inventories. It appears that ATF did not adequately oversee the contractor responsible for managing the laptop computers and did not ensure that exchanges, transfers, and donations of property were properly documented and processed in a timely manner to adjust the property records or remove those items from the records. However, because ATF could not provide documentation to support these explanations we included the 274 missing laptop computers in our analysis.
For perspective on the 76 weapons and 418 laptop computers included in our category of lost, stolen, or missing, we developed loss rates to compare with losses previously reported for ATF and with those experienced by other DOJ components. Comparable information is contained in the 2002 Treasury audit report and in OIG audit reports for the FBI and DEA.
To compare losses during our 59-month audit period with Treasury’s 2002 audit findings, we calculated losses per month because the audit periods were different lengths.21 We determined that ATF’s rates of loss for both weapons and laptop computers had increased substantially since the 2002 Treasury audit report. The following table shows the total losses and losses per month for both weapons and laptop computers for both audits. The two right columns compare the losses per month between our audit period and the period covered by the 2002 Treasury audit. The 1.29 weapons lost per month for our audit period was nearly three times the 0.47 weapons lost per month reported by Treasury in 2002. The 7.08 laptop computer losses per month for our audit period were approximately 50 times the 0.14 computer losses per month reported by Treasury OIG.
LOST, STOLEN, OR MISSING WEAPONS AND LAPTOP COMPUTERS
2002 TREASURY OIG AUDIT VS. CURRENT DOJ OIG AUDIT
| Category | Number of lost, stolen, or missing Items Reported | Losses Reported Per Month |
||
|---|---|---|---|---|
| 2002 Audit (36-month period) |
Current Audit (59-month period) |
2002 Audit |
Current Audit |
|
| Lost weapons | 4 | 19 | 0.11 | 0.32 |
| Stolen weapons | 13 | 35 | 0.36 | 0.59 |
| Weapons determined missing during an inventory | 0 | 12 | 0.00 | 0.20 |
| Weapons which could not be categorized as lost, stolen, or missing because documents had been destroyed or could not be found | 0 | 10 | 0.00 | 0.17 |
| Lost, Stolen, or Missing Weapons | 17 | 76 | 0.47 | 1.2922 |
| Lost laptop computers | 0 | 8 | 0.00 | 0.14 |
| Stolen laptop computers | 0 | 50 | 0.00 | 0.85 |
| Laptop computers determined missing during an inventory | 0 | 274 | 0.00 | 4.64 |
| Laptop computers which could not be categorized as lost, stolen, or missing because documents had been destroyed or could not be found | 5 | 86 | 0.14 | 1.46 |
| Lost, Stolen, or Missing Laptop computers | 5 | 418 | 0.14 | 7.0823 |
All of the items included in the table were reported within ATF as lost, stolen, or missing during a periodic physical inventory conducted by ATF staff.24 Lost and stolen weapons and laptop computers are discussed later in the report. When items are identified as lost, stolen or missing, either during an inventory or otherwise, ATF staff must prepare “Reports of Survey” to explain the losses. We used the Reports of Survey and the Internal Affairs investigative reports to categorize the items summarized in the preceding table.
Some but not all of the lost, stolen, or missing items were reported to ATF Internal Affairs, which prepared investigative reports regarding the circumstance of the loss. Of the 76 lost, stolen, or missing weapons, 63 were reported to Internal Affairs. Of the 418 lost, stolen, or missing laptop computers, 53 were reported to Internal Affairs.25
The table shows that 12 weapons were identified as missing during a physical inventory. The 12 missing weapons represent approximately 16 percent of the total lost, stolen, and missing weapons. Investigative reports at Internal Affairs indicated that six of the missing weapons were later recovered.
We compared ATF’s missing weapons with those identified as missing during our prior audits of the DEA and FBI. At the DEA, 4 (4 percent) of 91 lost, missing, or stolen weapons were identified as missing during an inventory. At the FBI, 23 (14 percent) of 160 lost, missing, or stolen weapons were identified as missing during an inventory. ATF’s percentage of weapons missing during an inventory (16 percent) is higher than the DEA’s percentage and about the same as the FBI’s percentage.
The table also shows 274 ATF laptop computers were identified as missing during periodic inventories. These losses represent approximately 66 percent of all lost, stolen, or missing ATF laptop computers. The inventory documentation submitted to ATF headquarters provided a variety of reasons for the missing computers. The primary reason was that managers believed the computers were returned to the supplier, exchanged for newer models, or donated to schools after becoming obsolete. However, managers could not demonstrate this had occurred because they could not produce the required documentation for such returns, exchanges, or donations. Consequently, we include these items in our analysis as missing, which is how we treated this issue in our DEA and FBI audits.
We compared the percentage of ATF’s missing laptop computers with those identified as missing during our prior audits of the DEA and FBI. At the DEA, 149 (65 percent) of 231 lost, stolen, or missing laptop computers were identified as missing during an inventory. At the FBI, 62 (39 percent) of 160 lost, stolen, or missing laptop computers were missing during an inventory. ATF’s percentage of laptop computers missing during an inventory (66 percent) is nearly equal to the percent missing at the DEA and higher than the percent missing at the FBI.
For 10 of the 76 lost, stolen, or missing weapons and for 86 of the 418 lost, stolen or missing laptop computers, the Reports of Survey had been destroyed at the end of the required record-retention period or were otherwise missing and no investigation reports were prepared.26 Consequently, we could not determine how these losses should be categorized – lost, stolen, or missing.
Comparison of Loss Rates
To compare ATF’s losses with those reported in audits of weapons and laptop computers at the FBI and DEA, we also calculated rates of loss per 1,000 agents because the components vary widely in number of employees. As the following table shows, for our 59-month audit period, ATF’s rate for lost, stolen, or missing weapons (.52) was nearly double those of the FBI (.29) and DEA (.28).27 ATF’s losses of laptop computers were significantly higher at nearly 3 per 1,000 agents, compared with less than 1 per 1,000 FBI or DEA agents.28 The following table shows the loss rates reported in audit reports for these three DOJ components.
LOST, STOLEN OR MISSING WEAPONS AND LAPTOP COMPUTERS
PER MONTH PER 1,000 AGENTS - ATF, FBI and DEA
| ATF | FBI | DEA | |
|---|---|---|---|
| Number of Agents | 2,461 | 12,515 | 4,929 |
| Number of Months in Audit Scope | 59 | 44 | 66 |
| WEAPONS | |||
| Lost, Stolen or Missing | 76 | 160 | 91 |
| Rate of Loss Per Month Per 1,000 Agents29 | 0.52 | 0.29 | 0.28 |
| LAPTOP COMPUTERS | |||
| Lost, Stolen, or Missing | 418 | 160 | 231 |
| Rate of Loss Per Month Per 1,000 Agents | 2.88 | 0.29 | 0.71 |
In the following table we show rates of loss per month per 1,000 agents for only those weapons and laptop computers reported stolen. As shown in the table, ATF’s rate of loss for stolen weapons (.24) was only slightly higher than the FBI (.17) and DEA (.21) rates of loss. The DEA has a policy that prohibits agents from storing their weapons in vehicles. The ATF and FBI have no such policy. For stolen laptop computers, ATF’s rate of loss per month per 1,000 agents (.34) was four times higher than the FBI (.08) and DEA (.08).
STOLEN WEAPONS AND LAPTOP COMPUTERS
PER MONTH PER 1,000 AGENTS - ATF, FBI and DEA
| STOLEN WEAPONS AND LAPTOP COMPUTERS |
ATF | FBI | DEA |
|---|---|---|---|
| Number of stolen weapons reported | 35 | 94 | 69 |
| Rate of Loss Per Month Per 1,000 Agents | 0.24 | 0.17 | 0.21 |
| Number of stolen laptop computers | 50 | 44 | 25 |
| Rate of Loss Per Month Per 1,000 Agents | 0.34 | 0.08 | 0.08 |
The next table shows rates of loss per month per 1,000 agents for the weapons and laptop computers that were lost, missing, or could not be categorized lost, stolen, or missing. ATF’s rate of loss for those weapons (.28) was significantly higher than the FBI (.12) and DEA (.07). ATF’s rate of loss for those laptop computers (2.53) was twelve times higher than the FBI (.21) and four times higher than the DEA (.63) rates of loss.
LOST AND MISSING WEAPONS AND LAPTOP COMPUTERS
PER MONTH PER 1,000 AGENTS - ATF, FBI and DEA30
| LOST OR MISSING WEAPONS AND LAPTOP COMPUTERS |
ATF | FBI | DEA |
|---|---|---|---|
| Number lost or missing weapons | 41 | 66 | 22 |
| Rate of Loss Per Month Per 1,000 Agents | 0.28 | 0.12 | 0.07 |
| Number of lost or missing laptop computers | 368 | 116 | 206 |
| Rate of Loss Per Month Per 1,000 Agents | 2.53 | 0.21 | 0.63 |
ATF officials were unable to explain why ATF’s rates of loss were higher than those of the FBI and the DEA. While one official suggested that ATF agents may carry more weapons than FBI or DEA agents, we did not find support for this explanation.
We recognize that in an organization the size of ATF some weapons and laptop computers will inevitably be lost, stolen, or missing. However, it is important that ATF take appropriate steps to minimize these losses because they could damage ATF’s operations, affect national security, or cause harm to persons whose personally identifiable information (PII) may have been compromised.31 Moreover, we are concerned that ATF’s rate of loss exceeds the rates in other DOJ law enforcement organizations.
When a weapon or laptop computer is lost, stolen, or missing, ATF must immediately report the loss, conduct an investigation, make any required entries into NCIC, and report the loss to DOJ. We discuss ATF’s reporting and investigation of lost, stolen, or missing weapons in the next sections.
Circumstances of Lost, Stolen, or Missing Weapons
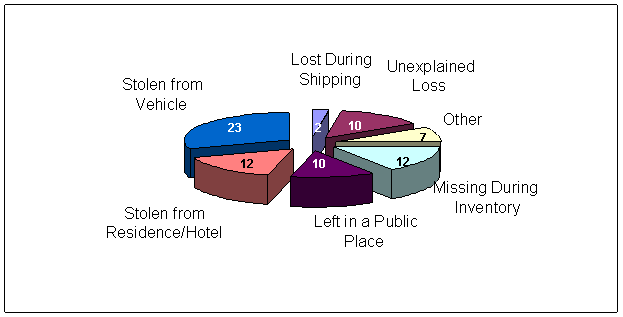
We identified 76 lost, stolen, or missing weapons during our review period. Of these, 63 were reported to Internal Affairs and 13 were not. As shown in the following chart, these losses occurred under a variety of circumstances.
NUMBER OF LOST, STOLEN, OR MISSING WEAPONS BY TYPE OF LOSS
OCTOBER 1, 2002, THROUGH AUGUST 31, 200732
| Source: OIG analysis of ATF Reports of Survey and investigative reports |
Of the 35 stolen weapons, 23 were taken from government-owned or privately-owned vehicles and 12 were stolen from offices, residences, and hotel rooms.
Of the 41 lost weapons, 12 were identified by ATF staff as missing during an inventory, 10 were left in a public place, 2 were lost during shipping, 7 were reported as “other” losses, and 10 were unexplained. Other losses included a weapon that fell into the water while an agent was fishing and was never found. Unexplained losses are those not reported to Internal Affairs, and therefore documentation about the details of the losses was not available.
We reviewed the circumstances surrounding the loss of these firearms to determine whether the losses could have been prevented. In 23 of the 63 losses reported to Internal Affairs, thefts occurred despite ATF employees taking what appeared to be reasonable precautions. However, in 40 other instances the loss or theft of weapons appeared to result from employee carelessness or failure to follow ATF policy. For example, 10 losses occurred when agents left their weapons in public places such as in bathrooms (3), a dressing room (1), a shuttle bus (1), an airplane (1), a shopping cart (1), on a chair in a garage (1), and on the tops of vehicles as the employee drove off without the weapon (2). We were unable to determine whether carelessness was a factor in the remaining 13 lost, stolen, or missing weapons because ATF staff did not report those losses to Internal Affairs and documentation about 10 of those losses was not available. The other three losses were reported missing on Reports of Survey and were treated as inventory adjustments.
From our review of investigative reports at Internal Affairs, we learned that two stolen ATF weapons were recovered from suspects arrested for crimes. One weapon stolen from a government-owned vehicle parked at the Special Agent’s home was recovered from a juvenile who used it to shoot out a window of a residence. Another weapon stolen from a cabinet in the Special Agent’s laundry room was recovered from suspects arrested for burglaries.
In addition to the loss or theft of 76 ATF-owned weapons, ATF staff lost 3 seized weapons in 2 separate incidents. Two weapons were stolen from a government-owned vehicle in Macon, Georgia, and one was lost during Hurricane Rita. The details of each loss are discussed in Appendix III.
Circumstances of Lost, Stolen, or Missing Laptop Computers
For the 59-month period covered by our audit, we identified 418 lost, stolen, or missing laptop computers. Of those 418, ATF identified 274 laptop computers as missing during an inventory. Documentation of inventory results submitted to ATF headquarters showed many of those laptop computers were kept in the property management records for several years before being deleted beginning in 2006. Officials from several ATF field offices said they believed that when laptop computers were replaced with newer models, exchanged because they were defective, donated to schools, or transferred to other ATF locations, documentation of these activities was not completed or the property records were not updated.
The eight laptop computers that were lost under other circumstances included three that were lost during shipping, one that was left on a train, one that was left on top of a car when the agent drove off, and one that was lost during a move to a new office location. Documentation about the remaining lost laptop computers did not fully explain the losses. The following table shows the lost, stolen, or missing laptop computers by loss type.
LOST, STOLEN, OR MISSING LAPTOP COMPUTERS BY LOSS TYPE
OCTOBER 1, 2002, THROUGH AUGUST 31, 2007
| Total | |
|---|---|
| Lost: | |
| Lost under various circumstances | 8 |
| Subtotal | 8 |
| Stolen: | |
| From a government-owned vehicle | 12 |
| From a personally-owned vehicle | 7 |
| From a rental vehicle | 2 |
| From an office | 14 |
| From a hotel room | 4 |
| From a residence | 2 |
| Other | 3 |
| Unexplained | 6 |
| Subtotal | 50 |
| Missing: | |
| Missing during inventory | 274 |
| Subtotal | 274 |
| Could not categorize: | 86 |
| Subtotal | 86 |
| Total | 418 |
Fifty laptop computers were stolen under various circumstances. In one incident, six laptop computers were stolen from an ATF office in Philadelphia but were recovered a week later. In another incident, five laptop computers were stolen from an ATF office in Houston. Another laptop was stolen from a room at the Cardozo School of Law in New York during a law school competition where an ATF employee was a judge. One laptop was believed to have been taken by an employee when the employee transferred to a new duty station. The employee’s supervisor referred the matter to Internal Affairs, which found no wrongdoing. Six other laptop computers were identified as stolen, but the available documentation provided no details about the nature of the thefts.
For 86 laptop computers, we could not determine whether the losses should be categorized as lost, stolen, or missing because ATF could not provide documentation used to remove those items from the property records. This occurred because ATF only retained those documents for the current year and 2 prior years.
Reporting Weapon and Laptop Computer Losses
ATF policy states that when a weapon or laptop computer is lost, stolen, or missing, the loss should immediately be reported to the Special Agent in Charge, division director, or chief who, in turn, must report the loss to the property accountable officer within 10 days. The property accountable officer, who is responsible for removing items from active property list, should then prepare a Report of Survey and provide a copy with any other documentation to Internal Affairs. However, during our review of the incident reports at Internal Affairs, we generally found that the Special Agent in Charge, division director, or chief notified Internal Affairs directly rather than submitting the incident report to the property accountable officer. When a loss is reported directly to Internal Affairs, the property accountable officer may not be aware of the loss and therefore not remove it from the property records. In addition, the property accountable officer does not have an opportunity to review the report to ensure that Internal Affairs receives complete information and documentation.33 Findings of an Internal Affairs investigation are referred to a Professional Review Board for adjudication, as described in this report under “Referring and Investigating Losses.”
ATF’s written policy does not contain procedures to assess the contents of a lost, stolen, or missing laptop computer, whether or not the laptop computer contained sensitive or classified information, or whether the loss compromised sensitive or National Security Information. An ATF Information Systems Security Officer told us that ATF Office of Science and Technology staff interviews personnel to determine what information was on the lost, stolen, or missing laptop computers, such as dates of birth, addresses, phone numbers, social security numbers (SSN), and investigative case information. However, we believe ATF needs to develop written procedures to identify the contents of lost, stolen, or missing laptop computers in order to reduce the possibility that the loss of sensitive or classified information could damage ATF operations or national security.
Weapons
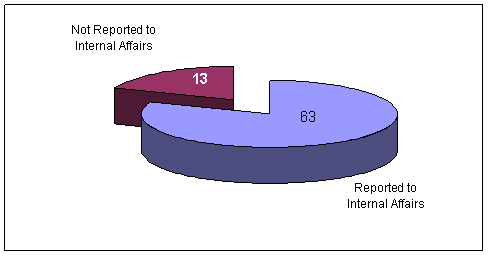
We tested whether the 76 lost, stolen, or missing weapons were reported to Internal Affairs. As shown in the following chart, 63 (83 percent) of the 76 weapons were referred to Internal Affairs.
LOST, STOLEN, OR MISSING WEAPONS REPORTED TO INTERNAL AFFAIRS
OCTOBER 1, 2002, THROUGH AUGUST 31, 2007
| Source: OIG analysis of ATF data |
Of the 76 lost, stolen, or missing weapons, 13 (17 percent) were not reported to Internal Affairs for follow-up actions even though such referral is required by ATF policy. ATF provided documentation showing these items were removed from the property records using a Report of Survey, but could not explain why the items were not reported to Internal Affairs. Unless such losses are reported to Internal Affairs and an investigation into the loss is conducted, ATF may never know the facts surrounding the loss and appropriate disciplinary action may not be considered.
The analyses found later in this report concerning the timeliness of reporting and the actions taken in response to the reports are limited to the 63 weapons that were reported to Internal Affairs.
Laptop Computers
Although ATF policy requires that all lost, stolen, or missing laptop computers be reported to Internal Affairs, the policy does not require a Professional Review Board to become involved in each loss.34 An Internal Affairs official told us that few laptop computer losses are investigated because only losses that result from failure to follow an established policy or from employee misconduct will result in any disciplinary action. ATF Policy 7500.1 provides mandatory and preferred methods of security for protecting laptop computers while they are in the office and during travel.
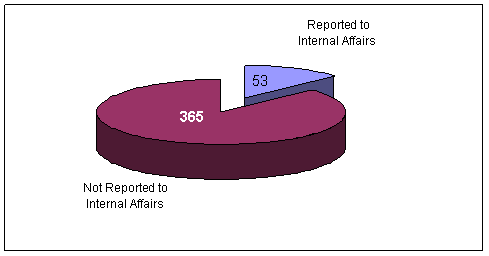
Only 53 lost, stolen, or missing laptop computers (13 percent) were reported to internal Affairs, as shown in the following table.
LOST, STOLEN, OR MISSING LAPTOP COMPUTERS REPORTED TO INTERNAL
AFFAIRS OCTOBER 1, 2002, THROUGH AUGUST 31, 2007
| Source: OIG analysis of ATF data |
The analyses that follow concerning timeliness of reporting and actions taken based on the reports are limited to the 53 that were reported to Internal Affairs.
Timeliness of Loss Reporting
To determine whether ATF staff immediately reported the loss or theft of their weapons or laptop computers to a supervisor such as a SAC, division director, or chief, we reviewed documentation maintained by the Office of Internal Affairs.35
We found that ATF staff reported 57 of 63 lost, stolen, or missing weapons to Internal Affairs, within 1 day or less from when the loss occurred. Four lost, stolen, or missing weapons were reported from 2 to 19 days after the loss occurred. In one of those cases, an agent did not report the loss of a weapon at all. Instead, 19 days after the loss occurred, a local police department issued a trace on the weapon and notified the agent’s supervisor. ATF staff could not explain why the other three losses were not reported immediately, but an Internal Affairs manager told us all employees who did not immediately report the loss of their weapons were suspended without pay and that all the lost, stolen, or missing weapons were the agents’ backup weapons. We could not determine whether the remaining two losses were reported timely because the exact loss date was unclear.
Of the 53 lost, stolen, or missing laptop computers reported to Internal Affairs, ATF staff reported 46 within 1 day or less from when the loss occurred. We could not determine whether the remaining seven laptop computers were reported timely because we could not determine the exact loss date.
Investigations and Consequences of Losses
ATF’s Office of Internal Affairs investigates, tracks, and reports allegations of misconduct involving ATF employees. In property loss cases, Internal Affairs conducts a preliminary investigation to determine whether employee actions or behavior caused a loss of property or violated ATF policies. Depending on the results, the preliminary investigation can be closed or converted to a full internal investigation. An ATF Professional Review Board adjudicates the results of any internal investigation and a headquarters-level deciding official makes a final decision on any disciplinary actions proposed by the Professional Review Board.
An Internal Affairs official told us that each reported loss of a weapon or laptop computer is assigned to an Internal Affairs agent to investigate. Upon completion of the investigation, the Internal Affairs agent prepares a Report of Investigation and provides a copy to the Internal Affairs SAC or Assistant SAC.
Disciplinary actions that can result from property losses include receiving a Letter of Caution, reprimand, suspension of from 1 to 10 days, or termination.36 Employees may also receive a Memorandum of Clearance showing they have been cleared of any wrongdoing. For the cases we reviewed, the disciplinary actions taken depended on the nature of the incident and whether the case involved a failure to properly secure or store a weapon.
The following table summarizes the numbers of lost, stolen, or missing weapons and laptop computers referred to and investigated by the Office of Internal Affairs.
LOST, STOLEN, OR MISSING WEAPONS AND LAPTOP COMPUTERS
REPORTED TO AND INVESTIGATED BY INTERNAL AFFAIRS
| A | B | C | D | E |
|---|---|---|---|---|
| Category | Number Lost, Stolen, or Missing | Number Reported to Internal Affairs |
Number Investigated by Internal Affairs | Number Not Investigated by Internal Affairs |
| Lost Weapons | 41 | 28 | 28 | 13 |
| Stolen Weapons | 35 | 35 | 35 | 0 |
| Total Lost, Stolen, or Missing Weapons | 76 | 63 | 63 | 13 |
| Lost Laptop Computers | 368 | 9 | 9 | 359 |
| Stolen Laptop Computers | 50 | 44 | 44 | 6 |
| Total Lost, Stolen, or Missing Laptop Computers | 418 | 53 | 53 | 365 |
Weapons Losses
As shown in the preceding table, 63 (83 percent) of 76 lost, stolen, or missing weapons were referred to and investigated by ATF’s Office of Internal Affairs. Of the 63 lost, stolen, or missing weapons were reported to the Office of Internal Affairs:
- 32 resulted in the employees being suspended for 1 to 10 days;
- 6 had disciplinary action still pending with the Professional Review Board as of March 2008;
- 6 resulted in the employees receiving a Letter of Caution;
- 1 resulted in the employee receiving a reprimand; and
- 1 resulted in the employee being terminated;
- 6 resulted in the employees receiving a Memorandum of Clearance; and
- 11 were closed after a preliminary investigation found no employee wrongdoing.
Based on our review of each of these cases, we did not identify any overt inconsistencies in disciplinary actions.
Prior to June 2007, most ATF employees received a 3-day suspension without pay for the first-time loss of a weapon. However, in June 2007 ATF changed the penalty for the first-time loss of a weapon from a minimum 3-day suspension to a minimum 1-day suspension. An ATF official told us the agency changed the policy because a minimum 3-day suspension for the loss of a weapon, regardless of the circumstances, might deter prompt reporting of the loss. Reducing the penalty to a 1-day suspension, the official said, would motivate the agent to report the loss quickly so that the lost, stolen, or missing item could be entered into NCIC. Some cases resulted in no disciplinary actions because ATF concluded there was no employee misconduct. One case resulted in termination because the employee had also misused his government-issued credit card and vehicle.
Some personnel received suspensions of more than 3 days because they had been involved in prior losses of weapons or the nature of the loss included other circumstances, such as not reporting the loss to a supervisor. For example, one agent received a 10-day suspension for the second loss of his weapon within a 1-year period. In another case, an agent who received a 10-day suspension had also received a 2-day suspension in 2002 for losing a weapon and a reprimand in 2003 for misuse of his official credentials. In a third case, an employee received an 8-day suspension because he did not report the loss of his weapon. Instead, a local police department issued a trace on the weapon and notified the ATF.
Laptop Computer Losses
As shown in the preceding table, Internal Affairs conducted a preliminary investigation into all 53 of the reported lost, stolen, or missing laptop computers, and opened a full investigation into 6 (11 percent) of the losses. Internal Affairs staff told us that full investigations were not conducted for the remaining 47 losses reported because the preliminary investigations found no employee misconduct. Of the six laptop computer losses that were fully investigated:
- 3 resulted in the employee receiving a written reprimand,
- 1 resulted in the employee receiving a Memorandum of Clearance, and
- 2 resulted in no documented disciplinary action.
Because ATF did not refer the remaining 365 lost, stolen, or missing laptop computers to Internal Affairs for investigation, ATF will never know the facts surrounding the losses or how to prevent their reoccurrence, and employees responsible for the losses may not receive appropriate disciplinary action.
Contents of Lost, Stolen, or Missing Laptop Computers
Beginning in November 2003, DOJ required all components to respond to and report all computer security incidents, including those that result in the loss or compromise of information, to the Department of Justice Computer Emergency Readiness Team (DOJCERT). DOJCERT is a centralized incident response team that provides Department-wide support for computer security incidents 24 hours a day, 7 days a week. DOJCERT is discussed in more detail in Finding II of this report.
In May 2006, OMB required all Department components to review their policies to ensure they had adequate safeguards in place to protect PII and to remind employees of their responsibilities for protecting such information. In May 2007, OMB required all departments and agencies to develop and implement a plan to notify persons whose PII had been compromised.
At the time of our audit, ATF did not have written procedures to determine whether lost, stolen, or missing laptop computers contained sensitive or classified information. However, an ATF Information Systems Security Officer (ISSO) told us ATF has an unwritten policy that when a user reports the loss or theft of a laptop computer, the ATF Helpdesk or the ISSO interviews the user about the contents of the laptop computer and enters the results of those interviews into the DOJCERT incident response database. In addition, Internal Affairs reports sometimes contained information about the contents of lost, stolen, or missing laptop computers.
We believe that a clear policy requiring ATF personnel to determine the contents of lost, stolen, or missing laptop computers is critical. Without knowing the contents, ATF does not know the extent of the damage these losses might have on operations, individual security, or national security.
On March 12, 2007, in response to the theft of two laptop computers, ATF’s Chief Information Officer issued a memorandum to all ATF employees explaining the importance of safeguarding laptop computers. He wrote that regardless of a thief’s intent, if sensitive information from a stolen laptop computer was accessed by the thief, the consequences could be serious. The memorandum reminded employees they should immediately report computer security incidents to the Help Desk and if the laptop computer were stolen they should also submit a Theft of Government Property report to an immediate supervisor. However, this policy still does not require ATF to determine whether lost, stolen, or missing laptop computers contained sensitive or classified information.
Unknown Contents for 398 Laptop Computer Losses
To determine whether sensitive information, including PII or classified information, may have been stored on the lost, stolen, or missing laptop computers, we interviewed ATF staff, reviewed Internal Affairs reports, and reviewed documentation of incidents ATF reported to DOJCERT. As explained earlier, interviews to determine the contents of lost, stolen, or missing laptop computers may also be documented on reports submitted to DOJCERT. We therefore asked ATF staff to provide incident reports submitted to DOJCERT and ATF Internal Affairs reports on all 53 lost, stolen, or missing laptop computers reported to Internal Affairs. ATF provided all 53 Internal Affairs reports we requested. However, it provided DOJCERT reports for only 6 (11 percent) of the 53 laptop computers.37
Of the 20 laptop computers for which ATF staff provided documentation, 7 reports indicated that the laptop computers contained sensitive information. None of the documents we reviewed indicated those stolen laptop computers contained classified information.
ATF staff could not provide documentation showing whether the remaining 398 lost, stolen, or missing laptop computers contained sensitive or classified information. We asked an official whether ATF was able to determine the contents of these laptop computers, but, as of July 2008, we had not received a response.
Unless ATF knows the contents of lost, stolen, or missing laptop computers, it cannot assess what damage those losses could have on operations, national security, or on individuals whose personal information may have been compromised. Details of sensitive information contained on the 7 stolen laptop computers are shown in the following table.
STOLEN LAPTOP COMPUTERS THAT CONTAINED SENSITIVE INFORMATION
| No. | Source | Date of Loss |
Office Reporting Loss | Encrypted38 | Nature of Contents |
|---|---|---|---|---|---|
| 1 | Internal Affairs Report | 6/25/2005 | Washington Field Division | No | Sensitive but unclassified information but did not specify the type of data. |
| 2 | Internal Affairs Report | 4/2/2006 | Los Angeles Field Division | No | Explosives licensee information. |
| 3 | Internal Affairs Report | 9/28/2006 | Detroit Field Division | No | Personal and work-related information. |
| 4 | Internal Affairs Report | 11/1/2006 | Office of Science and Technology | No | Employee evaluations, including social security numbers and other PII. |
| 5 | Internal Affairs Report and DOJCERT Report | 2/27/2007 | Financial Investigations Service Division | No | Approximately 300-500 names with dates of birth and social security numbers of targets of criminal investigations including their bank records with financial transactions. |
| 6 | Internal Affairs Report and DOJCERT Report | 2/27/2007 | Financial Investigations Service Division | No | Active case information, PII of ATF personnel, and copies of administrative reports. |
| 7 | Internal Affairs Report | 6/9/2007 | Computer Forensics Branch | Could Not Determine | Names and addresses of ATF computer forensic examiners. |
According to Internal Affairs records, ATF conducted a full internal investigation into only one of the laptop computer losses known to contain sensitive information (item 2 in the preceding table, containing explosives licensee information). ATF did not take any disciplinary action against the employees assigned any of these stolen laptop computers. An Internal Affairs manager told us only those losses that result from failure to follow an established policy or from employee misconduct result in any disciplinary action.
We believe that ATF management should strengthen its controls to ensure that ATF responds appropriately to each laptop computer loss. This includes determining the contents of lost laptop computers through interviewing employees or maintenance of inventories of information stored on laptop computers. However, because ATF has no written policy to obtain such information, it relies on users to voluntarily provide an inventory of the contents of the lost, stolen, or missing computer.
The previously mentioned memorandum regarding laptop computers, dated March 12, 2007, was a step in improving ATF’s policy because it established written guidelines to protect data and laptop computers. However, it did not require the ATF to determine the contents of lost, stolen, or missing laptop computers. The lack of a policy requiring determination of information on laptop computers is a significant deficiency because ATF laptop computers may contain sensitive information, such as PII or investigative case files.
In our audit, we sought to identify the types of information generally stored on ATF laptop computers by meeting with 16 Special Agents, 1 supervisory Special Agent, 2 contractors, 2 Task Force Officers and 2 other ATF employees in the ATF Atlanta area offices in March 2008. We interviewed those individuals about the contents of their laptop computers and found the hard-drives contained sensitive information such as names, addresses, SSNs, investigative case file information, and employees’ personal information. The sensitive information included:
- travel voucher claim forms containing Special Agents’ names and SSNs;
- a list of about 20 websites with the user’s logon and password information;
- a fingerprint request form containing an arrestee’s name, date of birth, SSN, and date of arrest;
- a document containing a fugitive’s name, SSN, biometric information, last known address, phone number, and relatives’ names;
- reports containing suspects’ names, addresses, SSNs, and dates of birth;
- recordings of phone conversations with targets of investigations;
- emergency data sheets with Special Agents’ and their family members’ names, home addresses, SSNs, and dates of birth; and
- ATF vehicle license-plate numbers and the names of the Special Agents’ to whom those vehicles were assigned.
Because ATF laptop computers contained these types of sensitive information, we believe that the lack of controls for determining the contents of lost, stolen, or missing laptop computer is a significant deficiency.
In addition, ATF should ensure laptop computers are encrypted. Although encryption does not negate the need to determine the contents of lost, stolen, or missing laptop computers, it reduces the likelihood the information will be misused. We discuss encryption in detail in Finding II.
ATF Memorandum 3120, dated March 26, 2002, requires ATF employees to enter all lost, stolen, or missing weapons into NCIC. Although the memorandum did not require ATF to enter laptop computers into NCIC, we found that some lost, stolen, or missing ATF laptop computers were entered into NCIC anyway.
On April 29, 2008, ATF issued a revised property management policy, ATF Order 1850.2D, requiring that lost, stolen, or missing firearms or equipment containing classified information should be reported to NCIC. However, the new property management policy still does not require all lost, stolen, or missing laptop computers to be reported to NCIC.39
We tested whether 72 of 76 lost, stolen, or missing weapons were entered into NCIC. We could not test the four remaining losses. We found that 7 of the 72 did not need an NCIC entry because the weapons were recovered shortly after being reported lost or stolen. Of the remaining 65, lost, stolen, or missing weapons tested, 60 (92 percent) had an NCIC record and 5 did not. Specifically, we found that:
- 45 had an active record in the NCIC database,
- 15 had an NCIC record at one time but the weapons were recovered and the records were purged from NCIC,
- 5 did not have an NCIC record. As of July 2008, ATF staff had not responded to our inquiry about why these records had not been reported to NCIC.
We also tested whether all 53 of the lost, stolen, or missing laptop computers reported to Internal Affairs were entered into NCIC. We found that 29 (55 percent) of 53 lost, stolen, or missing laptop computers we tested were entered into NCIC. In addition, we found that:
- 11 had an active record in the NCIC database;
- 18 had an NCIC record at one time but the laptop computers were recovered and the records were purged from NCIC;
- 4 were not applicable because they were mistakenly identified as lost, stolen, or missing or were recovered shortly after they were lost, stolen, or missing; and
- 20 did not have an NCIC record. Neither DOJ nor ATF had a policy requiring ATF to enter lost, stolen, or missing laptop computers into NCIC.
An ATF Office of Strategic Intelligence and Information official told us that when a weapon or laptop computer is reported lost, stolen, or missing at the agent’s residence, the loss is to be reported to the local law enforcement agency and the local law enforcement agency enters the loss into NCIC; otherwise, ATF enters the losses in NCIC. When an item is subsequently located by local law enforcement, the local agency flags the NCIC record to indicate the item has been located and then notifies ATF staff who remove the NCIC record entry. If ATF does not remove the record within 10 days, the flag entered by the locating agency causes the record to automatically be deleted from the system. Although ATF Order 1850.2D required that all lost, stolen, or missing firearms and equipment containing classified information be reported to NCIC, in our opinion the new property management policy falls short because it does not require that all lost, stolen, or missing laptop computers be reported. FBI and DEA policies require that lost, stolen, or missing laptop computers be entered into NCIC. A lost, stolen, or missing ATF laptop may have extremely sensitive case-related or operational information that could be damaging if accessed by non-ATF personnel.
Ammunition and Explosives Losses
ATF has a policy for reporting the loss of explosives, but did not have a specific written policy for reporting the loss of ammunition during our audit period. ATF’s property management policy requires employees to report losses of government property assigned to them. An ATF official told us that the policy covers losses of ammunition, which was specifically included in a revision issued in April 2008. However, the policy in place at the time of our audit did not specifically include ammunition and stated that a record is established within the property management system for each property asset, and ammunition is not included in the system. Therefore, it appears that ammunition was not property covered by the property management policy during our audit period.
An ATF Internal Affairs manager also told us that individual circumstances, such as whether the ammunition was stolen in conjunction with a stolen weapon, dictate whether lost, stolen, or missing ammunition should be referred to Internal Affairs and whether Internal Affairs conducts a full internal investigation into the loss. Because expendable items such as ammunition and explosives are not included in ATF’s property management system, we could only identify losses that ATF staff reported to Internal Affairs.
Although expendable items such as ammunition and explosives are not included in ATF’s electronic property management system, ATF accounts for those items using a paper-based perpetual recordkeeping system.40 Internal controls for ammunition and explosives are discussed later in Finding III of this report. Because these items are not included in the electronic property management system, we could only identify losses that ATF staff reported to Internal Affairs.
Ammunition
ATF staff reported to Internal Affairs 12 instances of lost, stolen, or missing ammunition for the 59-month period, October 1, 2002, through August 31, 2007. The 12 losses are detailed in the following table.
AMMUNITION LOSSES REPORTED TO INTERNAL AFFAIRS
| NO. | LOSS DATE |
FIELD OFFICE |
DESCRIPTION OF LOSS |
|---|---|---|---|
| 1 | 7/8/2003 | Lexington, Kentucky | 24 rounds of .40 caliber and 2 ammunition magazines were stolen from an ATF vehicle parked at a residence.41 |
| 2 | 3/21/2004 | Lubbock, Texas | An unknown amount of ammunition was stolen from an ATF storage shed at the Lubbock Police Department's firing range. |
| 3 | 7/14/2004 | New Haven, Connecticut | 18 boxes (360 rounds) of .40 caliber ammunition were stolen from a government-owned vehicle parked in a residence driveway. ATF later recovered 112 rounds. |
| 4 | 6/30/2005 | Tulsa, Oklahoma | A partial case of .40 caliber, a partial case .40 caliber frangible, and 1 case of .223 caliber frangible were stolen from a government-owned vehicle parked at a hotel.42 (This incident included a weapon loss that we included in our weapon loss review.) |
| 5 | 8/2/2005 | San Antonio, Texas | 3 magazines of .40 caliber ammo and 60 rounds of .40 caliber ammunition were stolen from a government-owned vehicle parked at a hotel. |
| 6 | 1/15/2005 | Honolulu, Hawaii | 39 rounds of ammunition were stolen from an ATF vehicle parked at a residence. The Special Agent received a Letter of Caution. |
| 7 | 3/1/2006 | Detroit, Michigan | 2 cases of .40 caliber were found missing during an inventory. After a division-wide e-mail requesting return of the missing ammo, one case was anonymously returned. Another was discovered lodged between two of the pallets of ammunition.43 |
| 8 | 5/2/2006 | New York, New York | 15-20 rounds of .40 caliber ammunition were stolen from a government-owned vehicle. Damage to trunk lock. |
| 9 | 6/9/2006 | Computer Forensics Branch | 24 rounds of .40 caliber missing. |
| 10 | Unknown | Colorado Springs, Colorado | 1 box miscellaneous ammunition was stolen from a government-owned vehicle. |
| 11 | Unknown | Wilmington, Delaware | 5 rounds of .22 caliber. Ammunition was stored in an unsealed envelope and must have fallen out of the envelope sometime during a move. |
| 12 | Unknown | New Orleans, Louisiana | A .40 caliber magazine with ammunition was stolen from a government-owned vehicle. |
Of the 12 incidents of lost, stolen, or missing ammunition, 1 resulted in the employee being cleared of misconduct. This incident also included an investigation of a stolen weapon discussed previously. One other ammunition loss resulted in the agent receiving a Letter of Caution. There was no report of investigation or disciplinary action for the remaining 10 incidents. Because ATF did not have specific written policies for reporting losses of ammunition to Internal Affairs it is possible that not all losses were reported for investigation, and therefore would not have been included in this review. The previous Treasury audit did not identify any reported ammunition losses.
Explosives
ATF staff reported to Internal Affairs two instances of lost, stolen, or missing explosives during our review period. The two losses are detailed in the following table.
EXPLOSIVES LOSSES REPORTED TO INTERNAL AFFAIRS
| NO. | LOSS DATE |
FIELD OFFICE |
DESCRIPTION OF LOSS |
|---|---|---|---|
| 1 | 2/27/2003 | Fort A.P. Hill, Virginia | Inert improvised explosives device stolen from camper shell of an ATF vehicle and later recovered at Fredericksburg, VA. |
| 2 | Unknown | Kansas City, Missouri | Three canine training explosives (10 grams each) were discovered missing. The explosives were found in the explosives storage unit several weeks later. |
ATF opened preliminary investigations into both incidents but found no misconduct and imposed no discipline. In both cases the explosives were either recovered or later found in the explosives storage unit. The previous Treasury audit did not identify any reported explosives losses.
Since the Treasury OIG’s 2002 audit, the number of lost, stolen, or missing weapons has increased from 0.47 per month to 1.29 per month. On an agent-per-month basis, this rate of loss is nearly double the rate of loss for the FBI and DEA. In addition, the numbers of lost, stolen, or missing laptop computers also increased dramatically since the 2002 audit. On a monthly basis, ATF’s rate of loss has dramatically increased.
ATF reported 82 percent of lost, stolen, or missing weapons and few of the lost, stolen, or missing laptop computers to Internal Affairs for follow-up actions. ATF officials did not explain why staff did not report 13 lost, stolen, or missing weapons. ATF officials told us they do not report inventory discrepancies as missing property to Internal Affairs. That decision is consistent with DOJ policy. Of the remaining 144 laptop computers,
53 (37 percent) were reported to Internal Affairs. ATF did not explain why staff did not report 91 lost, stolen, or missing laptop computers to Internal Affairs for follow-up action.
Internal Affairs opened a full internal investigation into only 6 of 53 laptop computers reported as lost, stolen, or missing. An Internal Affairs official told us ATF did not conduct an internal investigation or discipline employees for the other 47 losses because a preliminary investigation found no employee misconduct.
We determined that 92 percent of all lost, stolen, or missing weapons we tested were entered into NCIC. Although ATF was not required to enter lost, stolen, or missing laptop computers into NCIC, 55 percent of those we tested were entered anyway. We learned from our review of Internal Affairs documents that two stolen weapons subsequently were used in the commission of a crime.
ATF did not have written polices for determining the contents of lost, stolen, or missing laptop computers. ATF officials told us that when a laptop computer is lost, stolen, or missing, staff from the Help Desk or Internal Affairs or an Information Systems Security Officer interview the user of the laptop computer to determine its contents and that the results of those interviews are documented on Internal Affairs and DOJCERT reports. However, for most lost, stolen, or missing laptop computers, ATF could not provide documentation showing whether those laptop computers contained sensitive or classified information.
An ATF memorandum, dated March 12, 2007, improved ATF’s controls over laptop computers because it established written guidelines to protect data, but it did not require ATF to determine the contents of lost, stolen, or missing laptop computers.
We recommend that ATF:
- Ensure that ATF staff notify the Materiel Management Branch of all weapon and laptop computer losses and maintain copies of all supporting documentation.
- Ensure that for each loss Materiel Management provides Internal Affairs with the Report of Survey and information needed to conduct an investigation.
- Implement a written policy for reporting losses of ammunition to Internal Affairs for investigation.
- Implement procedures to determine the contents of lost, stolen, or missing laptop computers, specifically:
- whether the laptop computer contained classified information;
- whether the laptop computer contained sensitive or personally identifiable information; and
- whether the lost, stolen, or missing laptop computer was protected with encryption software.
- Require that lost, stolen, or missing weapons and laptop computers are appropriately entered into NCIC.
II. INTERNAL CONTROLS OVER WEAPONS AND LAPTOP COMPUTERS
- ATF did not maintain accurate and complete records in its property management system to track weapons and laptop computers and did not update the system to reflect the results of its inventories. Further, ATF did not submit semiannual loss reports identifying weapon and laptop computer losses to DOJ and laptop losses to DOJCERT as required. Additionally, ATF did not maintain support documentation for 5 disposed weapons and 22 disposed laptop computers tested and did not ensure that hard drives for 112 laptop computers were cleared prior to disposal.
DOJ Property Management Regulations require all components to conduct an annual physical inventory of all non-expendable personal property.44 However, at the discretion of the component head, these inventories can be conducted every 2 years rather than annually. ATF Order 3020.1 requires annual inventories of weapons. ATF performed annual inventories of weapons and bi-annual inventories of laptop computers recorded in its automated property system.
We reviewed ATF-wide inventory reports for FYs 2006 and 2007. The reports identified adjustments to the property records based on physical inventories performed. Not all divisions were listed on the ATF-wide consolidated report, so not all divisions had adjustments. We also reviewed inventory reports at the field divisions we tested. The divisions provided these reports, which include property overages and shortages, to the ATF property accountable officer. ATF policy required the property accountable officer to reconcile the shortages, post any administrative changes to the property management system, and prepare Reports of Survey for items that ATF could not reconcile.
We found that ATF property accountable officers did not consistently post changes to the property management system based on inventory results from the divisions. As a result, ATF kept many items on the active property list when it no longer had the property. This included items that were properly disposed of, as well as lost, stolen, or missing items. In one case, property was removed from the active property inventory 4 years after the item was first reported missing.45 By not timely updating the property management system based on results of annual inventories, ATF diminished its ability to maintain an accurate inventory of its weapons and laptop computers.
Reconciling Property Records to the Financial System
ATF’s financial system is not integrated with its property management system and the two systems are not reconciled. We performed tests to determine whether weapons and laptop computer purchases recorded in the financial system were recorded in the property management system.
We judgmentally selected from the financial system four purchases of weapons from April 7, 2000, through September 24, 2007. The purchases were for 1,264 weapons valued at $737,133. We found no discrepancies when we traced all the purchases to ensure that the items purchased were entered into the property management system.
ATF had no laptop computer procurement records to test because ATF did not enter these items into its financial system. Rather, ATF leased laptop computers from a contractor and the contractor used a software program to track the laptop computers ATF used.46 Once a month, the software scanned the ATF network to identify all laptop computers connected to the network during the previous 90 days and the contractor billed the ATF for those laptop computers. Because ATF leased laptop computers and was billed monthly, the agency had no laptop computer procurement records to test. Therefore, we were unable to determine the adequacy of ATF’s controls for reconciling laptop computer property records to the financial system because the leased computers were not entered into the financial system.
After the laptop computers are replaced by new leased laptop computers, most of the replaced laptop computers were disposed of. This represents a refresh cycle of 3 years that is normal in the computer industry. At the end of the refresh period, ATF owned the replaced computers and maintained a few of them for special purposes.
Inaccurate and Incomplete Property Records
We found inaccurate and incomplete data in ATF’s property management system that tracks its weapons and laptop computers. We tested weapons and laptop computers in two phases. First, we completed a 100-percent inventory of weapons and laptop computers at two field divisions. Based on the results of those tests, we performed a second phase of testing during which we selected a statistical sampling of weapons and laptop computers from the property management system and attempted to verify the information.
Preliminary Audit Testing (Phase I)
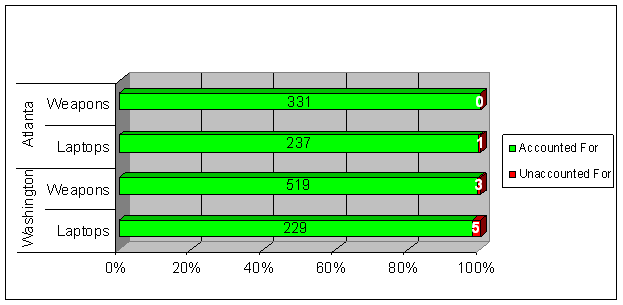
During this phase, we selected the Atlanta and Washington Field Divisions to examine the accuracy and completeness of property records in the property management system.47 We identified all weapons and laptop computers in the property management system for both divisions and completed a 100-percent review by verifying the existence of the property either by physically inspecting the equipment or by confirmation memoranda. We also evaluated property records and property management activities. The results of the review are shown in the following chart.
TOTAL ITEMS TESTED
| Source: OIG verification and analysis of ATF property management system data |
The items we did not account for were not physically present during our review and the division did not respond to a request for property confirmation memoranda.48 We consider these three weapons and six laptop computers to be unaccounted for.
For the items we did verify, we either physically verified the item or verified the item by confirmation memoranda. We detail the method of verification in the following table.
TOTAL VERIFIED ITEMS
| Field Division | ||||
|---|---|---|---|---|
| Verification Method | Atlanta | Washington | ||
| Weapons | Laptops | Weapons | Laptops | |
| Physically Verified | 280 | 210 | 462 | 189 |
| Verified by Confirmation Memoranda | 51 | 27 | 57 | 40 |
| TOTALS | 331 | 237 | 519 | 229 |
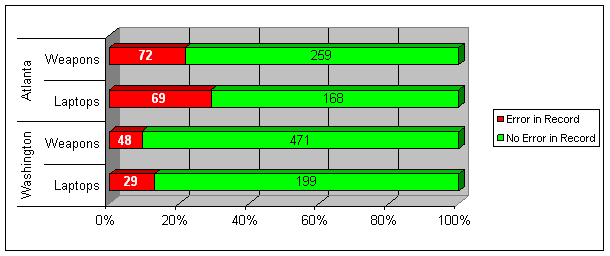
We determined for each item verified whether the user and location fields were accurate in the property management system. Of the 1,316 items we found that 217 (16 percent) had an incorrect user, incorrect location, or both in the property management system record, or the item was not included in the property management system at all. The total number of verified items with incorrect records are detailed in the following chart.
NUMBER OF PROPERT MANAGEMENT SYSTEM
ERRORS AND ERROR RATE FOR VERIFIED ITEMS
| Source: OIG verification and analysis of ATF property management system data |
We identified 1 weapon and 11 laptop computers in the Atlanta Field Division and 4 laptop computers in the Washington Field Division that ATF staff had not entered into the property management system.
ATF implemented a new automated property management system during 2004, but its property management policy was not updated to reflect implementation of the new system until April 2008. Consequently, the processes outlined in the policy were outdated between 2004 and April 2008.
Additional Audit Testing (Phase II)
Because our preliminary audit work determined that data within the property management system was inaccurate and incomplete, we performed additional testing at other ATF offices. During this phase, we statistically selected weapons and laptop computers from the property management system and physically verified each item at selected field and headquarters offices.
We selected a statistical sample of 935 weapons and 560 laptop computers from the property management system and physically attempted to verify each item. The statistical sample and locations were selected by an analysis based on quantity of personnel, weapons, and laptop computers. We verified property and evaluated property records and property management activities at the following locations: ATF headquarters divisions in Martinsburg, West Virginia; Landover, Maryland; and Glynco, Georgia; and divisional offices in Kansas City and St. Louis, Missouri; Las Vegas, Nevada; Little Rock, Arkansas; Los Angeles, Riverside, and San Francisco, California; Metairie and Shreveport, Louisiana; and Philadelphia and Pittsburgh, Pennsylvania.49
ATF was unable to provide all weapons and laptop computers for our verification. The weaknesses appear to be localized in certain offices, as reflected in the following table, which summarizes the results of verification testing at each selected location. We added the Phase I results for comparison purposes.
SAMPLE TESTING
| Location | WEAPONS | LAPTOP COMPUTERS | ||
|---|---|---|---|---|
| Accounted For | Unaccounted For | Accounted For | Unaccounted For | |
| PHASE I | ||||
| Atlanta Field Division (FD) | 331 | 0 | 237 | 1 |
| Washington FD | 519 | 3 | 229 | 5 |
| PHASE I TOTALS | 850 | 3 | 466 | 6 |
| PHASE II | ||||
| Headquarters | ||||
| Glynco, GA (HQ) | 92 | 0 | 67 | 2 |
| Landover, MD (HQ) | 0 | 0 | 31 | 0 |
| Martinsburg, WV (HQ) | 165 | 0 | 58 | 0 |
| Kansas City FD | ||||
| Kansas City, MO | 58 | 0 | 53 | 0 |
| St. Louis, MO | 84 | 0 | 30 | 2 |
| Los Angeles FD | ||||
| Los Angeles, CA | 96 | 1 | 49 | 1250 |
| Riverside, CA | 31 | 0 | 16 | 0 |
| New Orleans FD | ||||
| Little Rock, AR | 36 | 0 | 21 | 0 |
| Metairie, LA | 59 | 0 | 36 | 1 |
| Shreveport, LA | 46 | 0 | 18 | 0 |
| Philadelphia FD | ||||
| Philadelphia, PA | 77 | 0 | 48 | 0 |
| Pittsburgh, PA | 66 | 0 | 35 | 0 |
| San Francisco FD | ||||
| San Francisco, CA | 64 | 0 | 56 | 0 |
| Las Vegas, NV | 60 | 0 | 25 | 0 |
| PHASE II TOTALS | 934 | 1 | 543 | 17 |
As with the first phase of our testing in the Atlanta and Washington Filed Divisions, for the statistically selected sample in other ATF offices we physically verified the item or verified it by confirmation memoranda.
We also tested the completeness of the property records by selecting a judgmental sample of staff at seven offices and tracing property in their possession to the property management system to determine if property management system records were correct.51 The results of our review are summarized in the following table.
PERSONNEL PROPERTY TO PROPERTY MANAGEMENT SYSTEM TESTING
| Location | Personnel Selected | WEAPONS | LAPTOP COMPUTERS | ||
|---|---|---|---|---|---|
| Number Belonging to Personnel Selected | Records Incorrect in Property Management System | Number Belonging to Personnel Selected | Records Incorrect in Property Management System | ||
| Glynco (HQ) | 2 | 3 | 0 | 1 | 0 |
| Martinsburg (HQ) | 5 | 0 | Not Applicable | 5 | 1 |
| Kansas City | 6 | 3 | 1 | 6 | 1 |
| Los Angeles | 6 | 12 | 1 | 6 | 1 |
| Metairie | 5 | 13 | 0 | 5 | 1 |
| Philadelphia | 5 | 6 | 0 | 5 | 0 |
| St. Louis | 4 | 7 | 0 | 5 | 0 |
| TOTALS | 33 | 44 | 252 | 33 | 453 |
During these tests, we identified items for which conflicting information was entered in the property records.54 For instance, a record’s data elements for “office code” and “location” contained conflicting information, indicating an item was located in two different places. An ATF official explained how this may occur. He said that when an item is transferred the “office code” field is automatically updated in the record when the receiving location accepts the property in the property management system, but the “location” field must be manually updated. In these cases, the receiving location does not manually update the location field.55 We believe that the automated system should be used to prevent conflicting information by applying relationship edits between related data elements. For laptop computer records, ATF may be able to interface with the leasing contractor's tracking system to maintain more accurate records.
As discussed in Finding I, in March 2007 the Chief Information Officer in ATF’s Office of Science and Technology issued a memorandum to all ATF employees explaining the importance of safeguarding laptop computers. The memorandum stated that ATF would be implementing new security measures to encrypt laptop computer hard drives. This effort was intended to provide an additional layer of protection to help maintain confidentiality of the data stored on laptop computers. ATF staff began installing the encryption software for laptop computers in May 2007, and as of April 2008 ATF staff told us they had completed the installation on all networked laptop computers. On April 22, 2008, ATF staff reported that they had installed encryption software on all 5,774 networked ATF laptop computers. The majority of ATF laptop computers are networked and assigned to individuals as personal property. ATF has approximately 1,800 stand-alone laptop computers. ATF staff planned to encrypt these standalone laptop computers and provided disks to staff to install the encryption software.
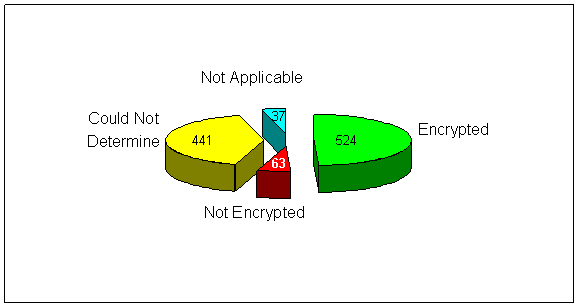
During our review of property in Phases I and II, and prior to ATF’s reported completion of the encryption software installation, we tested to determine if ATF had installed encryption software on sampled laptop computers. Sixty-three of the 1,065 laptop computers we tested did not have the encryption software installed at the time of our tests. However, 42 of the 63 unencrypted laptop computers were used strictly for a dedicated purpose such as Global Positioning System tracking or video surveillance and ATF staff told us they do not store sensitive information on those laptop computers. The remaining 21 unencrypted laptop computers were assigned to users. Of those 21 unencrypted laptop computers:
- 17 were located in the Washington Field Division;56
- 3 were located in the Atlanta Field Division; and
- 1 was located in the Los Angeles Field Division.
We could not determine the encryption status for the 180 laptop computers we verified by confirmation memoranda or the 238 we physically verified but a user was not available to log on and show us that the encryption software was installed. The remaining 23 laptop computers could not be tested because they were unaccounted for. The encryption status results are summarized in the following chart.
ENCRYPTION SOFTWARE TESTING AS OF DECEMBER 2007
| Source: OIG testing of ATF laptop computers |
Section 3.13 of DOJ’s Information Technology Security Standard 1.6, Classified Laptop and Standalone Computers Security Policy, issued November 1, 2006, requires that all classified information on laptop and standalone computers be encrypted. We determined 5 of ATF’s 18 classified laptop computers we tested were not encrypted. By not encrypting these classified laptop computers, ATF did not comply with DOJ policy and risked compromising classified information if the laptop computer were lost, stolen, or missing. Two of the unencrypted laptop computers had classified information on the hard drives at the time of our test. One of the unencrypted laptop computers was not labeled with a Property Identification Number and could not be found in the property management system. Therefore, if the laptop computer was lost, stolen, or missing there would be no record that ATF ever had it and classified information could be compromised.
As of April 2008, ATF was in the process of installing encryption software on the five classified laptop computers. However, ATF did not provide a reason why these five classified laptop computers had not been encrypted up to this point.
Reporting Requirements for Laptop Computers Containing Classified Information
Beginning March 31, 2004, the DOJ’s Office of the Chief Information Officer required ATF to report the number of laptop computers it has authorized for processing classified information. To ensure that ATF complied with the requirement, we requested this information from the DOJ CIO. The DOJ CIO had received ATF’s 2007 submission, but none for any prior years. An ATF official told us that ATF may not have known about the requirement to report classified laptop computers to DOJ in previous years.
ATF’s 2007 submission included 13 classified laptop computers. However, during our audit we found that ATF had 18 classified laptop computers. The additional five laptop computers were the same five described above as being unencrypted.
Section 11.c of DOJ Order 2630.2A, Protecting and Controlling Federally Controlled Property and Loss/Theft Reporting Procedures, and Justice Property Management Regulations 128-1.5305, requires all components, including ATF, to submit to DOJ’s Justice Management Division (JMD), semiannual reports summarizing thefts and losses of government property during the preceding 6 months. ATF has never submitted a semiannual report summarizing thefts of government property. However, during the period October 9, 2002, through July 24, 2007, ATF experienced the loss or theft of 76 weapons and 418 laptop computers. JMD sent follow-up correspondence to ATF in 2005, 2006, and 2007 reminding it to submit the semiannual reports. We have asked JMD about this and are awaiting their response. ATF submitted its first semiannual report to JMD in April 2008.
The ATF’s Chief for Materiel Management told us that ATF had not submitted previous semiannual reports because the property management system did not allow ATF to consolidate the loss information. He further explained that ATF was in the process of updating the property management system to be able to consolidate the loss information.
Although ATF’s property management system may not have been able to consolidate loss information, it appears to us that ATF did have the resources to compile lists of lost, stolen, or missing items. For example, ATF could have used the disposed records database, Report of Surveys, and Internal Affairs reports to compile lists of lost, stolen, or missing property to meet the JMD reporting requirement.
Department of Justice Computer Emergency Response Team
We tested whether ATF reported lost, stolen, or missing laptop computers to DOJCERT. We identified 53 laptop computer losses that were reported to Internal Affairs, of which 16 occurred prior to the DOJCERT reporting requirement, leaving 37 incidents that should have been reported. We found that 21 of the 37 were reported to DOJCERT, while 16 were not reported as required.
We asked ATF officials why the 16 incidents of lost, stolen, or missing laptop computers were not reported to DOJCERT, but as of July 2008 we had not received a response. Of the 16 laptop computers not reported to DOJCERT, ATF reported that 3 contained sensitive information, 6 did not contain sensitive information, and ATF could not determine whether 7 contained sensitive information. Eleven of the 16 laptop computers were not encrypted because ATF began installing encryption software after these laptop computers were lost, stolen, or missing. Two may have been encrypted because they were lost, stolen, or missing after ATF began installing encryption software. ATF reported that one of those laptop computers had sensitive information and the other did not. We could not determine the encryption status for the remaining three laptop computers because we could not determine the dates the losses occurred.
Disposal of Weapons and Laptop Computers
ATF’s process for disposing of weapons and laptop computers consists of the following steps.
- The property custodian notifies the property management representative of any excess property.
- The property management representative completes an ATF Form 1854.1, Declaration of Excess Property, and forwards it to the Property Accountable Officer.57
- The property accountable officer reports the excess property to the General Services Administration (GSA).
- GSA screens the property for transfer to other federal agencies, donation to state agencies or other authorized recipients, or offers the property for sale to the public.58
- The property accountable officer sends disposal instructions and a Transfer Order (SF 122) to the property custodian.
- Before computers are donated, the property custodian and property accountable officer ensure the hard drives are cleared and a Certificate of Data Clearing (ATF Form 1854.2) is prepared.
- The property custodian obtains signatures from the receiving organization on Transfer Order (SF 122), if donated, and forwards the Transfer Order and Certificate of Data Clearing to the property accountable officer.
- The property accountable officer adjusts the property records.
We selected a representative sample of 121 of 3,982 weapons and 176 of 4,701 laptop computers disposed of during the audit’s 59-month time frame. While not statistically selected, the sample is a representative sample because it includes disposals from headquarters and field divisions, disposals occurring during each year of the audit period, and all methods of disposal. Disposed weapons and laptop computers are destroyed, transferred to another agency, lost, missing, or stolen, exchanged, donated, returned, or removed from the active property records as an inventory adjustment. The number of items for each type of disposal are summarized in the following table.
DISPOSED PROPERTY TESTING
| DISPOSAL TYPE | WEAPONS | LAPTOP COMPUTERS |
|---|---|---|
| Destroyed | 63 | 19 |
| Transferred | 39 | 34 |
| Lost, Missing, or Stolen | 6 | 24 |
| Exchanged | 4 | 7 |
| Donated | 1 | 70 |
| Inventory Adjustment | 7 | 17 |
| Returned | 1 | 4 |
| Could Not Determine59 | - | 1 |
| TOTALS | 121 | 176 |
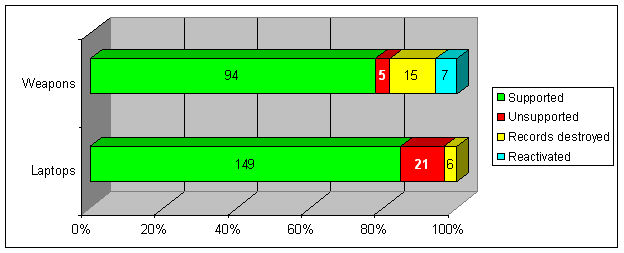
To test the controls of the disposal process, we examined whether the sample of 297 items included the proper support documentation such as a Report of Destruction (ATF Form 1850.2), Transfer Document, or Report of Survey and contained the appropriate signatures for each disposal. The following chart details whether ATF provided proper documentation for the disposed weapons and laptop computers in our sample.
SAMPLE DISPOSED PROPERTY TESTING60
| Source: ATF disposed property records |
Ninety-five percent (94 of 99) of the weapons and 88 percent (149 of 170) of the laptop computers removed from the active property records were adequately supported by documentation containing the required signatures.61 Officials at the Property Management Office told us that the records supporting the disposal of 5 weapons and 10 laptop computers were misplaced when ATF moved to its new headquarters building in August 2007.
Two laptop computers did not include all required signatures and nine laptop computers did not have the Property Identification Numbers listed on the disposal documents. In our judgment, the effect of these errors is not significant.
Before laptop computers are disposed of, the property custodian and the property accountable officer should ensure the hard drives are cleared and a Certificate of Data Clearing is prepared, as required by ATF policy. Of the 149 supported laptop computer disposals, we tested 116 to determine whether the data clearing was supported by appropriate documentation. We did not test the remaining 33 because the laptop computers were inventory adjustments, lost, stolen, or transferred to the Treasury Tax and Trade Bureau and no there were no actual laptop computers to clear.62 ATF provided a Certificate of Data Clearing for only 4 (3 percent) of the 116 laptop computers we tested. The data clearing status for 97 percent of the disposed laptop computers was not documented.
ATF property management officials told us that when computers were returned to the Materiel Management Operations Center because the item was defective or was being replaced with a newer model, the Certificate of Data Clearing was sent along with the computer. ATF provided electronic Certificates of Data Clearing for 32 laptop computers. However, only one certificate was for an item in our sample of disposed property. An Internal Affairs manager told us that under the computer lease agreements, when a laptop computer was replaced because of defect or upgrade the contractor’s technicians exchanged the laptop computer without completing any paperwork. The contract states that if a replacement involves non-volatile memory, the contractor should erase all sensitive data before parts removal, provided the laptop computer is operational.63
In addition, as discussed previously, for several years annual ATF inventories resulted in large numbers of laptop computers that could not be accounted for and in 2006 ATF began removing those missing items from its active property records. The Internal Affairs manager did not know whether the hard drives of these computers were cleared of any sensitive information that may have been on the laptop computers removed from the property records as inventory adjustments.
We compared the active property records to the disposed property records and found that 28 weapons and 197 laptop computers were contained in both active and disposed property records. An ATF official explained that if ATF does not locate an item during an inventory, Materiel Management staff removes the item from the active records and records it in the disposed records. If the item is located during a subsequent inventory, Materiel Management staff place the item back into the active records, but do not remove the item from the disposed records. The explanation is reasonable as to why an item may be in both active and disposed records. However, an item should not be recorded as both active and disposed and ATF should adjust the entry in the disposed records to note that the item was reactivated. We also found that 124 items had multiple disposal dates that included items with multiple types of disposal.
ATF did not have proper controls over disposed property nor did it provide support documentation for 5 disposed weapons and 21 disposed laptop computers. In addition, ATF did not provide documentation supporting the data clearing for 112 disposed laptop computers. Since ATF included items in both disposed and active property records, ATF did not follow established procedure to update disposed records to reflect reactivation. As a result, ATF could not determine whether the item was active or disposed. We recommend that ATF maintain support documentation for all disposed property, document data clearing of disposed laptop computers, and update active and disposed property records.
Exit Procedures for Departing Employees
The clearance process for departing employees begins when they notify their supervisor of their intent to leave ATF or when the supervisor notifies employees of a termination. The supervisor initiates an ATF Form 2391.1, Separation Checklist. The supervisor or other designated official should coordinate with the property custodian to ensure that employees return property for which ATF issued an ATF Form 1854.4 or 1854.4A, Property Issue Receipt. On or before employees’ last day of employment, the supervisor or other designated official should collect property issued including weapons, ammunition, and laptop computers. Weapons and agency-issued ammunition are to be returned to the division director, SAC, or tactical operations officer in accordance with ATF Order 3000.8, ATF’s weapons policy. The supervisor should complete and sign the Separation Checklist and provide copies to the employee and to the personnel office.
To test whether all assigned property had been returned by separated ATF employees, we judgmentally selected 30 former ATF employees from 12 locations where we performed other tests. We asked ATF staff for the 30 separation checklists, of which ATF staff could provide only 6. Each checklist contained only a statement certifying that the supervisor received all property from the employee and did not identify specific property items returned by the employee. We were also not able to use the property management system to identify items that had been associated with each separated employee. Although the system contains historical information about employees to whom property was previously assigned, those property records can only be retrieved using property identification numbers. Consequently, we were unable to perform the test to ensure separating employees had returned all weapons and laptop computers assigned to them during ATF service.
We were able to test whether the property management system still contained property records showing items assigned to separated employees. Our analysis identified 26 active weapons and 152 active laptop computers assigned to persons who had separated from ATF. This occurred because ATF staff did not update the property management system to reflect whether the items were returned.
Our audit identified weaknesses in ATF’s control over weapons and laptop computers in several areas. We found that ATF failed to adequately: (1) maintain accurate and complete records in the property management system and update the system to reflect administrative changes occurring during inventories; (2) locate all active weapons and laptop computers sampled for review; (3) report to the DOJ’s Office of the Chief Information Officer the number of laptop computers authorized to process National Security Information; (4) report all weapon and laptop losses to DOJ and all laptop loss incidents to DOJCERT; (5) maintain support documentation for disposed weapons and laptop computers and ensure that ATF clear computer hard drives prior to disposal; and (6) maintain documentation showing ATF collected all weapons and laptop computers from separating employees. Consequently, we make several recommendations for ATF to improve its management of weapons and laptop computers.
We recommend that ATF:
- Develop procedures for updating the property management system to ensure accurate and complete weapons and laptop computer records are maintained.
- Locate or report as missing all sampled items not found during the audit.
- Ensure all laptop computers are encrypted.
- Ensure complete, accurate, and timely reports are submitted to the DOJ CIO containing all appropriate ATF laptop computers authorized to process classified information.
- Ensure complete, accurate, and timely semiannual reports identifying lost, stolen, or missing weapons and laptop computers are submitted to the DOJ Security Officer and JMD.
- Develop procedures to ensure ATF completes accurate, and timely incident reports summarizing the loss of ATF laptop computers and submits those reports to DOJCERT, as required by DOJ policy.
- Maintain documentation for all disposed property, document data clearing of disposed laptop computers, and update active and disposed property records, as necessary.
- Develop procedures and maintain documentation to ensure that separated employees return all weapons, laptop computers, and other accountable property before they separate from ATF.
III. INTERNAL CONTROLS OVER AMMUNITION AND EXPLOSIVES
- We concluded that ATF had adequate physical security over both ammunition and explosives. Its inventory controls over explosives were far better than those for ammunition. ATF maintained perpetual inventory records at explosives magazines and we were able to verify the quantities of explosives on hand. In addition, ATF staff conducted independent inventories of explosives magazines during internal inspections. Recordkeeping for ammunition was less consistent. Nine of the 20 offices we tested did not maintain perpetual inventories of ammunition as required by ATF policy. Of the 11 offices that maintained perpetual records, 4 had significant inaccuracies in the records, 1 of which had 478,400 fewer rounds of ammunition in stock than was recorded on the perpetual inventory. ATF also was not enforcing its policy that field offices conduct annual ammunition inventories and submit the results to ATF’s Materiel Management Branch. It appeared that no office had ever submitted an annual ammunition inventory to ATF headquarters, nor had ATF taken any follow-up action to obtain annual ammunition inventories. ATF officials could not explain the absence of perpetual inventories or for not ensuring that annual ammunition inventories are conducted and submitted to headquarters. Without inventory controls over ammunition, ATF is subject to the loss or theft of ammunition without detection.
In 2002, the Treasury OIG reported that ATF had limited written policies regarding controls over ammunition, no standard recordkeeping, and no physical inventories. As a result of the Treasury audit, ATF implemented new policies that required all divisions and the ATF Academy to conduct a baseline inventory of all ammunition, and report the results to the Property and Fleet Management Section of the Materiel Management Branch. The memorandum also established a requirement for an annual inventory of all ATF-owned ammunition and required a perpetual inventory system for ammunition. It also required an annual inventory of all ATF-owned ammunition and that a disinterested person assist in conducting all inventories.
We sought to review the last two annual inventories of ammunition submitted to the Chief of the Property and Fleet Management Section, but we were unable to perform the review because ATF could not produce documentation for any of the inventories. We asked ATF officials why the inventory records were not available, but as of July 2008 ATF had not responded.
We also reviewed ammunition controls at 20 ATF offices where we tested weapons and laptop computers. Of the 20 offices, we found that 11 kept perpetual inventory records as required and 9 did not. At each location, we compared the perpetual records for each type of ammunition to the actual inventory stored at the office. We noted that five of the offices had accurate perpetual record systems and six offices had inaccurate records. One office had inaccuracies in all but one type of ammunition that was short 478,400 rounds. We attributed the large shortage to inadequate recordkeeping. The perpetual record was apparently not updated as transactions occurred. The official responsible for the ammunition believed the missing ammunition had probably been given to the military. While this may be correct, ATF has no way of knowing what happened to the missing ammunition without a record of the transactions. Nine offices did not keep perpetual records at all. Our results are summarized in the following table.
AMMUNITION RECORDS TESTING
| Location | Summary of Ammunition Records | ||
|---|---|---|---|
| Perpetual Records Kept? | Records Accurate? | Description of Inaccuracies | |
| Atlanta, Georgia | No | N/A | Atlanta did not keep any ammunition records. |
| Macon, Georgia | No | N/A | Macon did not keep any ammunition records. |
| Savannah, Georgia | No | N/A | Savannah did not keep any ammunition records. |
| Richmond, Virginia | Yes | Yes | N/A |
| Bristol, Virginia | Yes | Yes | N/A |
| Roanoke, Virginia | Yes | Yes | N/A |
| Norfolk, Virginia | Yes | No | Shortage of seven cases of .40 caliber ammunition. |
| Martinsburg, West Virginia | Yes | No | Shortage of one case of .40 caliber ammunition. |
| Glynco, Georgia | Yes | Yes | N/A |
| Headquarters | Yes | No | Perpetual records did match actual inventory for 19 of 20 types. One caliber had a shortage of 478,400 rounds. |
| Kansas City, Missouri | Yes | No | Shortage of 10 cases of .40 caliber ammunition. |
| Las Vegas, Nevada | No | N/A | Las Vegas began documenting inventory records just prior to the audit site visit. |
| Little Rock, Arkansas | Yes | Yes | N/A |
| Los Angeles, California | No | N/A | Los Angeles began documenting inventory records on 10/15/2007, just prior to the audit site visit. |
| San Francisco, California | No | N/A | San Francisco began documenting inventory records just prior to the audit site visit. |
| New Orleans, Louisiana | No | N/A | New Orleans began documenting inventory records just prior to the audit site visit. |
| Shreveport, Louisiana | Yes | No | Shortage of seven cases of .223 caliber ammunition. According to the office, this ammunition was issued during the aftermath of Hurricane Katrina. No specific records were kept of this distribution. |
| Philadelphia, Pennsylvania | No | N/A | Philadelphia only logged ammunition used. No baseline was established. |
| Pittsburgh, Pennsylvania | No | N/A | Pittsburgh did not keep any ammunition records. |
| St. Louis, Missouri | Yes | No | Shortage of one case of .40 caliber ammunition. |
The nine offices that did not keep perpetual inventories and the one office that had significant deficiencies in its perpetual inventory system did not follow procedures to accurately account for all stored ammunition. One office did not keep complete perpetual records because an agent who worked in the office believed that the requirement to keep the perpetual records and submit annual inventories had been rescinded. We asked ATF’s Chief Financial Officer to provide information confirming that the requirement had been rescinded. As of July 2008, we had not a received response.
Reconciling Ammunition Records to the Financial System
During our review, we judgmentally selected 12 ammunition shipments to 8 locations where we performed testing. The disbursements were for .223 caliber ammunition shipped between September 26, 2006, and April 11, 2007. We attempted to trace these shipments of ammunition to the perpetual inventory records that were to be maintained at these locations. However, none of the 12 shipments made to the 8 locations where we performed testing were recorded in the perpetual inventory records. Although ATF policy requires the maintenance of perpetual records, five of the eight locations did not keep ammunition inventory records. At two of the other field offices, records were retained for only the last year, a period that did not include the shipments. In the eighth location, which was the headquarters ammunition facility, an agent told us that the shipment may have been intended for the Baltimore office. Since the receiving location for the Baltimore office is the headquarters facility, that shipment would have been picked up by the Baltimore office and logged into that office’s inventory.64 Unless ATF offices maintain complete and accurate perpetual records, ATF cannot ensure it has received all the ammunition that it has paid for or that ammunition has not been lost, stolen, or missing.
Physical Security
Ammunition was stored in various locations at the different ATF offices that we tested. Smaller ATF field offices kept ammunition in vaults within the office space and access to the vaults was controlled by key cards and alarm systems. Agents had access to these vaults. Larger field offices and divisions kept ammunition in warehouse facilities or at a firing range. The warehouse facilities stored other equipment in addition to ammunition. Not all agents had access to these facilities. The following photograph shows ammunition stored in a vault located in the basement of ATF office space. The vault was padlocked and had a security system.
AMMUNITION STORAGE

| Source: OIG photograph of ATF storage of ammunition |
The next photograph shows ammunition in an ammunition storage facility for a larger division. The storage facility was an ATF-owned warehouse that also housed ATF vehicles and tactical equipment.
AMMUNITION STORAGE

| Source: OIG photograph of ATF storage of ammunition |
Treasury’s 2002 audit reported that ATF had satisfactory procedures for ensuring the physical security of its ammunition, and we found that ATF continued to have proper physical security of its ammunition.
The Treasury OIG reported in its 2002 audit that controls over physical inventories of explosives lacked independent review. In response to the finding, ATF required that a disinterested person participate in all future inventories of explosives magazines. In addition, ATF mandated that a perpetual record of each type of ATF-owned explosive be maintained.
ATF Memorandum 3325, dated May 14, 2002, required an annual inventory of all explosives located in ATF magazines. Also, the memorandum explained that ATF divisions must keep a Daily Summary of Transaction Record to be used as a perpetual inventory for each explosives magazine. In addition, the ATF Explosives Industry Operations Section conducted annual inspections of all ATF magazines, which included an inventory review by persons independent of daily responsibility for the magazine. In addition, ATF’s Explosives Industry Operations Section performs annual inspections of all ATF explosives magazines that include physical inventories by “disinterested persons” who are independent of daily responsibility for the magazine.
We reviewed explosives at 16 ATF locations and found that each kept perpetual inventory records as required. At each location, we compared the perpetual records for each type of explosive to the actual inventory stored at the location. We found that the explosives on hand did not correspond with the amounts recorded in the perpetual records at 8 of 16 locations. Our results are summarized in the following table.
EXPLOSIVES RECORDS TESTING
| Location | Summary of Explosives Records | ||
|---|---|---|---|
| Perpetual Records Kept? | Records Accurate? | Description of Inaccuracies | |
| Atlanta, Georgia | Yes | No | Overage of 9 pieces of 1-pound booster. |
| Leesburg, Virginia | Yes | Yes | N/A |
| Falls Church, Virginia | Yes | Yes | N/A |
| Bristol, Virginia | Yes | Yes | N/A |
| Chantilly, Virginia (Explosives Technology Branch) | Yes | Yes | N/A |
| Fort A.P. Hill, Virginia (Three magazines) |
Yes | No | Shortage of two weatherproof fuse lighters. |
| Front Royal, Virginia (Six magazines) |
Yes | No | Overage of 18 cases of ammonium nitrate and an overage of 1,250 feet cord explosive. |
| Millersville, Maryland (Explosives Technology Branch) | Yes | Yes | N/A |
| Kansas City, Missouri | Yes | No | Overage of three cast boosters. |
| Little Rock, Arkansas | Yes | Yes | N/A |
| Los Angeles, California | Yes | No | Overage of one item. Another item was incorrectly classified on the inventory records. |
| San Francisco, California | Yes | No | Shortage of one 6-gram slip on booster. |
| New Orleans, Louisiana | Yes | No | Shortage of two cast boosters. |
| Reading, Pennsylvania (Philadelphia Field Division) | Yes | No | Overage of one piece of slurry explosive. |
| Camden, New Jersey (Philadelphia Field Division) | Yes | Yes | N/A |
| St. Louis, Missouri | Yes | Yes | N/A |
We concluded that ATF’s control over explosives was adequate because all offices kept perpetual explosives inventory records as required. However, as shown in the preceding table, three magazines were missing several pieces of explosives and five magazines had more pieces of explosives than were recorded on their perpetual inventory records. We considered the missing items as minor discrepancies. One magazine had an overage in stock of 9 pieces of an item and another had overages of 18 pieces of one item and 1,250 feet of another item.
Reconciling Explosives Records to the Financial System
We reviewed the only two purchases for explosives that occurred within our audit period, both of which were sent to the K-9 Training facility at Front Royal, Virginia. We were able to trace both shipments from the invoices to the perpetual log kept with the magazines at Front Royal.
Physical Security
ATF’s Explosives Industry Operations Orange Book, Federal Explosives Law and Regulations, regulates how explosives are to be stored. An ATF official told us that only certified personnel had access to explosives magazines. In addition, ATF Memorandum 5400 requires an independent physical security review completed by the ATF’s Industry Operations. Industry Operations reviewed whether each magazine adhered to structural specification and access requirements. We reviewed inspection reports and confirmed that magazines met the structural requirement and the magazines we reviewed were all secured. Therefore, we found that ATF’s physical controls over explosives were adequate.
The following photo shows an explosives magazine which was located in a fenced area surrounded by barbed wire. The magazine’s door also had a double lock.
EXPLOSIVES STORAGE

| Source: OIG photograph of ATF explosives magazine |
We concluded that ATF’s controls over explosives were adequate. However, we identified continued weaknesses in controls over ammunition. Although ATF developed written procedures to enhance controls over ammunition in response to the 2002 Treasury audit, ATF failed to enforce its policy. Specifically, ATF did not perform annual inventories of ammunition and did not maintain accurate and complete perpetual inventory records of ammunition.
We recommend that ATF:
- Enforce current requirements to perform annual inventories of ammunition and maintain a perpetual inventory system at all ammunition storage locations to ensure accurate and complete records.
Footnotes
As of January 2008, 271 of 274 laptop computers ATF identified as missing during inventories had been removed from the active property records.
One ATF official said the laptop computers were not missing and that we should report those items as “inventory discrepancies.” Other ATF officials believed those laptop computers had been donated, transferred, or returned to the contractor but could not provide the supporting documentation. We categorize these items as lost because ATF cannot document the circumstances surrounding their “missing” status and cannot document the disposition of the items. We treated these items similarly in our FBI and DEA audits.
ATF staff did not provide information about exactly when this occurred.
The 2002 Treasury OIG audit covered the 36-month period from October 1, 1998, through September 30, 2001. The current audit covered the 59-month period from October 1, 2002, to August 31, 2007.
Laptop computers identified as missing during an inventory were generally not reported to Internal Affairs. For weapons, we could not determine the circumstances for weapons not being reported because ATF could not provide documentation about 10 of the 13 weapons not reported to Internal Affairs. The other three were reported missing on Reports of Survey and were treated as inventory adjustments.
We know from the property management system that these items were removed based on Reports of Survey. ATF staff told us the records for 8 of the 10 weapons and for 78 of the 86 laptop computers were destroyed in accordance with ATF’s written policy that personal property records are to be destroyed 3 years after the property is disposed of. ATF staff could not locate the other records. In Finding I, we discuss concerns regarding reporting items to Internal Affairs.
Of the 76 lost, stolen, or missing weapons our audit identified, 12 (16 percent) were documented as missing during periodic inventories.
The number of lost laptop computers for all 3 components included items identified during periodic inventories as missing.
To determine the losses reported per month per 1,000 agents, we first divided the number of total losses (76) by the number of months of the reporting period (59) to determine the number of losses per month. We then divided the losses per month by the number of total agents (2,461) to determine the number of losses per month per agent. Then we multiplied the number of losses per month per agent by 1,000, calculated as {[(76÷59) ÷2,461] ×1,000}.
Numbers in this table include weapons and laptop computers reported lost or missing and those that could not be categorized as lost, stolen, or missing. Statistics for the FBI and DEA also include weapons and laptop computers identified as missing during periodic inventories.
According to OMB Memorandum M-07-16, dated May 22, 2007, PII is any information about an individual maintained by an agency, including, but not limited to, education, financial transactions, medical history, and criminal or employment history and information which can be used to distinguish or trace an individual’s identity, such as name, social security number, date and place of birth, mother’s maiden name, and biometric records, including any other personal information which is linked or linkable to an individual.
The scope of our audit covered the 59-month period from October 1, 2002, through August 31, 2007. We asked ATF for documentation of all weapons and laptop computers identified as lost, stolen, or missing since October 1, 2002. ATF provided documentation for items lost, stolen, or missing from September 26, 2002, to July 24, 2007.
On April 29, 2008, ATF issued a new property management policy that allows the SAC, division director, or chief to report losses directly to Internal Affairs. However, ATF’s new policy does not ensure that such losses are also reported to the property accountable officer so that the property can be removed from the property records to maintain an accurate inventory.
JMD policy states that inventory discrepancies do not need to be referred to a Board of Survey. ATF categorized many laptop computer losses as inventory discrepancies, but ATF could not provide documentation confirming that the losses were only inventory discrepancies and not laptop computers that were identified as missing during an inventory.
ATF did not define that term “immediately.” We defined “immediately” as 1 day or less. Any item reported after 1 day would not be considered as having been reported immediately.
ATF officials did not consider a Letter of Caution as a disciplinary action; however, we included it in our report as a form of discipline.
ATF provided DOJCERT reports for nine other lost, stolen, or missing laptop computers. Four of those were lost, stolen, or missing during the period covered by our audit and five were lost, stolen, or missing after the period covered by our audit.
Laptop computers lost, stolen, or missing prior to May 2007 did not have encryption software installed.
Although DOJ policy does not require that lost, stolen, or missing laptop computers be entered into NCIC, FBI and DEA have policies that require that such laptop computers be entered into NCIC.
An ammunition magazine is a compartment in the weapon, or a small box that can be attached to the weapon, which holds ammunition to be fed into the firing chamber of the weapon. An explosives storage magazine is usually several feet tall and wide.
Frangible rounds are designed to break apart when they hit walls or other hard surfaces to prevent ricochets during close-quarters combat.
A pallet is a portable platform for storing or moving goods that are stacked on it. See a photo of a pallet in Finding III, Ammunition Controls section.
DOJ Property Management Regulations cover personal and real property.
ATF requires that a loss be reported to the Materiel Management Branch within 10 days after the loss is identified.
The monthly lease amount was $310, which includes $77 for the laptop and $233 for support services such as managing the server and providing data security and round-the-clock technical support.
The Atlanta Field Division includes field offices in Georgia that include Atlanta, Macon, Savannah, Columbus, and Augusta. The Washington Field Division includes field offices in Washington, D.C., Virginia, and West Virginia. The Virginia offices include Falls Church, Richmond, Roanoke, Charlottesville, Norfolk, Bristol, and Winchester. West Virginia has a single field office in Martinsburg.
A property confirmation memorandum was a document we used to verify property that was not physically available for verification because the personnel in possession of the property were out of the office during our visit. We left confirmation memoranda for these personnel to list property in their possession, have a supervisor confirm the property, and send to us.
The universe of weapons and laptop computers for each audited location and details of our sample by property type, location, and type of test appear in Appendix II.
ATF staff in the Los Angeles office believed 12 unaccounted for laptop computers had been donated, but they could not provide copies of the donation forms.
We performed this test at seven locations because all personnel at the other locations were already included in the sample.
One weapon in Kansas City was assigned to another individual and one weapon in Los Angeles listed an incorrect location.
One laptop computer was assigned to another user and location in Martinsburg. One laptop computer in Kansas City was not in the property management system. One laptop computer in Los Angeles listed an incorrect location. One laptop computer in New Orleans did not have a user listed.
The property management system database contains data elements to record the office the item is assigned to and the location where it can be found, as some offices operate in multiple locations. Those elements are related because property that is assigned to a specific office should be found in a limited set of locations.
When a property item is transferred, the sending office’s property custodian sends an e-mail through the property management system identifying the property to be transferred to the receiving office’s property custodian. When the receiving property custodian electronically accepts the new property, the office code database field is automatically updated in the property management system to reflect the receiving location office code.
We conducted testing in the Washington Field Division shortly after ATF began installing the encryption software.
At headquarters the property management representative completes an ATF Form 1630.1, Facilities Service Support Form, and ATF Form 1851.1, Property Transfer Record, and forwards the forms to the property accountable officer who removes the property from the property management system.
Weapons can only be sold to the public after they have been rendered permanently inoperative.
We could not determine the reason for disposal from ATF records.
ATF has a 3-year document retention policy for property records. As a result, we were unable to verify disposal documents for all items selected that ATF disposed of prior to FY 2005.
We excluded seven weapons from testing because property records for those weapons were reactivated when the weapon was found or when it was discovered that the wrong record had been deleted. We also excluded 15 weapons and 6 laptop computers from testing because the supporting documentation had been destroyed in accordance with ATF’s record retention practices.
Only the law enforcement offices of the ATF transferred to the Department of Justice in January 2003.
Non-volatile memory is computer memory that can retain the stored information even when not powered. Examples of non-volatile memory include read-only memory, flash memory, and most types of magnetic computer storage devices such as hard disks, floppy disks drives, and magnetic tape.
We did not verify whether the ammunition was logged into the Baltimore office’s inventory. However, when the headquarters facility received the ammunition it should have recorded the ammunition in its inventory and then removed the ammunition from its inventory once the Baltimore office retrieved the ammunition.