The Bureau of Alcohol, Tobacco, Firearms and Explosives (ATF) employs 4,845 Special Agents, Explosives Industry Operations Investigators, and support personnel. To fulfill the ATF’s mission, these personnel are responsible for maintaining the agency’s weapons, laptop computers, and other sensitive property such as ammunition and explosives. As of August 17, 2007, ATF had 22,476 weapons and 7,505 laptop computers assigned to ATF offices and employees located throughout the United States and in 5 foreign countries.
In 2001, the Attorney General requested that the Office of the Inspector General (OIG) conduct audits of the controls over weapons and laptop computers throughout the Department of Justice (DOJ) to address concerns about DOJ’s accountability for such property. The OIG performed a series of audits during fiscal year (FY) 2002 that examined controls over weapons and laptop computers at the Federal Bureau of Investigation (FBI), Federal Bureau of Prisons, Drug Enforcement Administration (DEA), and United States Marshals Service.1 We found substantial losses and weak controls over management of this property throughout DOJ law enforcement agencies.
ATF transferred to DOJ in January 2003 from the Department of the Treasury (Treasury) after the OIG completed its first round of weapons and laptop audits.2 In 2002, the Treasury OIG had conducted an audit of ATF’s controls over sensitive property, including firearms, laptop computers, ammunition, and explosives.3 The Treasury audit concluded that ATF’s controls over firearms and laptop computers were adequate and that ATF generally took appropriate actions in response to lost, stolen, or missing property. The audit also concluded that ATF’s controls over ammunition and explosives needed improvement. ATF concurred with the findings and recommendations in the review and subsequently reported that it had implemented new controls to address these weaknesses.
As a result of Treasury’s 2002 audit, ATF required all its divisions to conduct a baseline inventory of ammunition and report the results to headquarters. ATF required that an annual 100-percent inventory of all ATF-owned ammunition be performed and that such reviews include a disinterested person to assist in conducting ammunition inventories.4 ATF also required that a disinterested person directly participate in all future inventories of ATF explosives. In addition, ATF required that records of each type of ATF-owned ammunition and explosive be maintained indefinitely.
OIG Audit Approach
This audit of the ATF’s controls over its weapons, laptop computers, and other sensitive property is one of a series of follow-up audits that the OIG is conducting to examine DOJ components’ controls over their weapons and laptop computers.5 The objectives of this audit were to assess: (1) the adequacy of ATF’s actions taken in response to weapons, laptop computers, ammunition, and explosives identified as lost, stolen, or missing; and (2) the effectiveness of ATF’s internal controls over weapons, laptop computers, ammunition, and explosives. Our other audits of controls over weapons and laptop computers in DOJ components did not include a review of ammunition and explosives. However, we included ammunition and explosives in this audit because the 2002 Treasury OIG audit identified weaknesses in these areas. Our review covered the 59-month period from October 1, 2002, through August 31, 2007.
During this audit, we interviewed or met with various ATF officials, including ATF’s Chief Financial Officer and Chief of the Materiel Management Branch.6 We also reviewed documents and tested controls at ATF headquarters offices in Washington, D.C.; Landover, Maryland; Martinsburg, West Virginia; 7 field divisions and 24 field offices associated with those divisions; and 3 ATF training facilities.
Our audit examined ATF’s actions in response to lost, stolen, or missing weapons, laptop computers, ammunition, and explosives, and whether ATF followed current DOJ procedures after weapons or laptop computers were lost, stolen, or missing. We also queried the to identify lost, stolen, or missing ATF weapons and laptop computers that were recovered or weapons used in the commission of a crime. We also examined whether national security or investigative information may have been contained on ATF lost laptop computers.
In addition, we reviewed ATF’s internal controls over accountable property, its exit procedures for departing employees, and its disposal of property. Our review included a physical verification of a sample of weapons and laptop computers. We also tested the accuracy and completeness of the property records, and we reviewed controls over ammunition and explosives to determine whether ATF stores and properly accounts for this property. Appendix I contains a further description of our audit objectives, scope, and methodology.
OIG Results in Brief
Over the 59-month period we tested, 76 weapons and 418 laptop computers were lost, stolen, or missing from ATF. ATF’s rate of weapons loss per month has nearly tripled since Treasury’s 2002 audit, and the rate of loss per month for laptop computers was 50 times higher than what the 2002 audit revealed. According to ATF officials, the much higher rate of laptop computer losses resulted primarily from adjustments ATF made to its inventory records to correct inaccurate data accumulated over several years.
We also found serious deficiencies in ATF’s response to these lost, stolen, or missing items. ATF staff did not report many of the lost, stolen, or missing weapons and laptop computers to ATF’s Internal Affairs Division (Internal Affairs), as required by ATF’s property management policies. In addition, ATF did not report most of the missing laptop computers to ATF Internal Affairs for investigation. We also found that ATF staff did not enter 5 lost, stolen, or missing weapons into NCIC and did not document what data was contained on 398 of the 418 lost, stolen, or missing laptop computers. Consequently, ATF could not provide assurance that these computers did not contain sensitive information, personally identifiable information (PII), or classified information. Because ATF did not begin to install encryption software on its laptop computers until May 2007, few if any of the laptop computers lost, stolen, or missing during our review period were protected.7
Treasury’s 2002 audit reported that ATF’s controls over firearms and laptop computers were adequate. However, our audit identified weaknesses in several areas. First, ATF staff could not locate several active weapons and several laptop computers sampled for our review. Second, ATF staff did not maintain accurate and complete records in ATF’s property management system, nor was the system regularly updated as required by ATF’s property management policy. In addition, ATF did not maintain adequate documentation for disposed weapons and laptop computers and did not ensure that it had cleared computer hard drives prior to disposal.
ATF, like all DOJ components, is also required to report to DOJ information regarding losses of weapons and laptop computers. However, ATF staff did not report any lost, stolen, or missing weapons and laptop computers in the required semiannual reports to DOJ. ATF staff also did not report to DOJ the number of laptop computers authorized to process National Security Information (NSI), and ATF did not report 16 incidents of lost laptop computers to the DOJ’s Computer Emergency Response Team (DOJCERT), as required by Department policy.
Our audit concluded that ATF had adequate controls over the explosives in its possession. We also concluded that ATF had proper physical security over its ammunition. However, we identified continued weaknesses in ATF’s ammunition accountability and controls. We tested accountability and controls for ammunition at 20 ATF field offices during our audit and found that 11 field offices followed perpetual inventory recordkeeping requirements for ammunition, but 9 offices did not maintain such records.8 Also, ATF could not provide documentation that any field office had submitted annual ammunition inventories to ATF headquarters, as required by ATF policies.
In our report, we make 14 recommendations to assist ATF in improving its controls over weapons, laptop computers, and ammunition.
Our report contains detailed information on the full results of our review of ATF’s control over weapons, laptop computers, ammunition, and explosives. The remaining sections of this Executive Summary describe in more detail our audit findings.
ATF'S Weapon, Laptop Computers, Ammunition, and Explosives Losses
To determine the number of lost, stolen, or missing weapons and laptop computers, we reviewed records maintained by ATF’s Internal Affairs and property management office. We also reviewed incident reports of lost, missing, or stolen property reported to Internal Affairs and the results of any subsequent investigations, including any disciplinary actions that were taken. We also assessed the results of periodic inventories that field offices submitted to ATF headquarters, and the documents the property management office used to remove weapons and laptop computers from the property records. Inventory results included lists of property that field offices reported as missing during periodic inventories. We also interviewed field staff to obtain information about ammunition and explosives losses.
Rates of Weapon and Laptop Computer Losses
For perspective on ATF’s 76 weapons and 418 laptop computers identified as lost, stolen, or missing, we developed loss rates to compare both with the loss rates previously reported for ATF and with those experienced by other DOJ components. We were able to identify comparable information in the 2002 Treasury audit report and in OIG audit reports for the FBI and DEA.
To compare losses during our 59-month audit period with Treasury’s 2002 audit findings, we used the measure “losses per month” because the audit periods were different lengths. We determined that ATF’s rates of loss for both weapons and laptop computers had significantly increased since the 2002 Treasury audit report.
The following table shows the total losses per month for weapons and laptop computers for both audits. We used the Reports of Survey and the Internal Affairs investigative reports to categorize the items summarized in the table. The two right columns compare the losses per month between our audit period and the period covered by the 2002 Treasury audit. The 1.29 weapons lost per month for our audit period was nearly three times the 0.47 weapons lost per month reported by the Treasury in 2002. The 7.08 laptop computers losses per month for our audit period were approximately 50 times the 0.14 computer losses per month reported by Treasury OIG.
LOST, STOLEN, OR MISSING WEAPONS AND LAPTOP COMPUTERS
| Category | Number of lost, stolen, or missing Items Reported | Losses Reported Per Month |
||
|---|---|---|---|---|
| 2002 Audit (36-month period) |
Current Audit (59-month period) |
2002 Audit |
Current Audit |
|
| Lost weapons | 4 | 19 | 0.11 | 0.32 |
| Stolen weapons | 13 | 35 | 0.36 | 0.59 |
| Weapons determined missing during an inventory | 0 | 12 | 0.00 | 0.20 |
| Weapons which could not be categorized as lost, stolen, or missing because documents had been destroyed or were missing9 | 0 | 10 | 0.00 | 0.17 |
| Lost, Stolen, or Missing Weapons | 17 | 76 | 0.47 | 1.2910 |
| Lost laptop computers | 0 | 8 | 0.00 | 0.14 |
| Stolen laptop computers | 0 | 50 | 0.00 | 0.85 |
| Laptop computers determined missing during an inventory | 0 | 274 | 0.00 | 4.64 |
| Laptop computers which could not be categorized as lost, stolen, or missing because documents had been destroyed or were missing9 | 5 | 86 | 0.14 | 1.46 |
| Lost, Stolen, or Missing Laptop computers | 5 | 418 | 0.14 | 7.0811 |
All of the items included in the table were reported within ATF as lost, stolen, or missing during a periodic physical inventory conducted by ATF staff.12 Lost and stolen weapons and laptop computers are discussed later in this executive summary. When items are identified as missing, either during an inventory or otherwise, ATF staff must prepare “Reports of Survey” to explain the losses.
Some but not all of the lost, stolen, or missing items were reported to ATF Internal Affairs, which prepared investigative reports regarding the circumstance of the loss. Of the 76 lost, stolen, or missing weapons, 63 were reported to Internal Affairs. Of the 418 lost, stolen, or missing laptop computers, 53 were reported to Internal Affairs.13
The table shows that 12 weapons were identified as missing during a physical inventory. The 12 missing weapons represent approximately 16 percent of the total lost, stolen, and missing weapons. Investigative reports at Internal Affairs indicated that 6 of the missing weapons were later recovered.
We compared ATF’s missing weapons with those identified as missing during our prior audits of the DEA and FBI. At the DEA, 4 (4 percent) of 91 lost, missing, or stolen weapons were identified as missing during an inventory. At the FBI, 23 (14 percent) of 160 lost, missing, or stolen weapons were identified as missing during an inventory. ATF’s percentage of weapons missing during an inventory (16 percent) is higher than the DEA’s percentage and about the same as the FBI’s percentage.
The table shows that 274 ATF laptop computers were identified as missing during periodic inventories. These losses represent approximately 66 percent of all lost, stolen, or missing ATF computers. The inventory documentation submitted to ATF headquarters provided a variety of reasons for the missing computers. The primary reason was that managers believed the computers were returned to the supplier, exchanged for newer models, or donated to schools after becoming obsolete. However, managers could not demonstrate this had occurred because they could not produce the required documentation for such returns, exchanges, or donations. Consequently, we include these items in our analysis as missing, which is how we treated this issue in our DEA and FBI audits.
We also compared the percentage of ATF’s missing laptop computers with those identified as missing during our prior audits of the DEA and FBI. At the DEA, 149 (65 percent) of 231 lost, stolen, or missing laptop computers were identified as missing during an inventory. At the FBI, 62 (39 percent) of 160 lost, stolen, or missing laptop computers were missing during an inventory. ATF’s percentage of laptop computers missing during an inventory (66 percent) is nearly equal to the percent missing at the DEA and higher than the percent missing at the FBI.
For 10 of the 76 lost, stolen, or missing weapons and for 86 of the 418 lost, stolen or missing laptop computers, the Reports of Survey had been destroyed at the end of the required record-retention period or were otherwise missing and no investigation reports were prepared.14 Consequently, we could not determine how these losses should be categorized – lost, stolen, or missing.
To compare ATF’s losses with those reported in audits of weapons and laptop computers at the FBI and DEA, we also calculated rates of loss per 1,000 agents because the components vary widely in number of employees. As the following table shows, for our 59-month audit period, ATF’s rate for lost, stolen, or missing weapons (0.52) was nearly double those of the FBI (0.29) and DEA (0.28). ATF’s losses of laptop computers were significantly higher at nearly 3 per 1,000 agents, compared with less than 1 per 1,000 FBI or DEA agents. The following chart shows the loss rates reported in audit reports for these three DOJ components.
ATF, FBI, AND DEA LOST, STOLEN, OR MISSING
WEAPONS AND LAPTOP COMPUTERS
[Image Not Available Electronically]
Source: OIG analysis of ATF, FBI, and DEA data
Types of Losses
We found that 35 (46 percent) of the ATF’s 76 weapons lost, stolen, or missing during this review period were stolen from Special Agents’ residences, hotel rooms, and government-owned or privately-owned vehicles. The remaining 41 (54 percent) of the 76 lost, stolen, or missing weapons were identified as missing during an inventory, left in a public place, lost during shipping, lost under other circumstances, or the losses were unexplained. We determined that in 40 of the 76 losses (53 percent), the loss or theft of weapons appeared to have resulted from employees’ carelessness or failure to follow ATF policy.
For laptop computers, we found that 50 (12 percent) of the 418 were stolen. Of these, 21 were stolen from a vehicle; 20 were stolen from an office, residence, or hotel; and 9 were unexplained because ATF could not provide information on the nature of the theft. Of the remaining 368 lost, stolen, or missing laptop computers, 274 were identified as missing during an inventory and 94 were lost during shipping, left in a public place, or were unexplainably lost.
Reporting Weapons Losses
All lost, stolen, or missing weapons are required by ATF Order 1850.2C to be reported to ATF Internal Affairs. Of the 76 lost, stolen, or missing weapons, ATF reported 63 (83 percent) to Internal Affairs. As of July 2008, ATF was unable to explain to us why the remaining 13 weapons (17 percent) were not reported.
For the 63 weapons losses that were referred to Internal Affairs, we reviewed documentation to determine whether: (1) the employee immediately reported the loss or theft to a supervisor; (2) Internal Affairs investigated the incident; and (3) ATF took disciplinary action against the employee, if appropriate.15 We summarize the results in the following chart.
ACTIONS TAKEN ON 63 LOST, STOLEN, OR MISSING WEAPONS
REPORTED TO INTERNAL AFFAIRS16
OCTOBER 1, 2002, THROUGH AUGUST 31, 2007
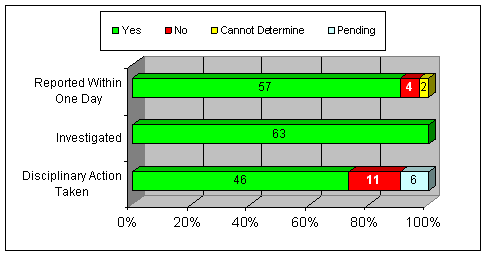
| Source: OIG analysis of ATF data |
We found that ATF investigated all lost, stolen, or missing weapons reported to Internal Affairs and appeared to take appropriate disciplinary action in these cases. Two weapons ATF staff reported as stolen were used to commit crimes. One weapon, stolen from an ATF vehicle parked at the Special Agentís residence, was recovered after a suspect used the stolen weapon to shoot through the window of a residence. Another weapon, stolen from an ATF Special Agentís residence, was recovered from suspects arrested in connection with a burglary.
Reporting Laptop Computer Losses
ATF policy requires that all lost, stolen, or missing laptop computers be reported to Internal Affairs. Of the 418 laptop computers identified as lost, stolen, or missing during the 59-month audit period, 274 (66 percent) were reported as not being located during a physical inventory. 17 However, of the remaining 144 laptop computers, ATF only reported 53 (37 percent) to Internal Affairs. We concluded that ATF did not follow proper procedures to report the remaining 91 laptop computer losses and did not provide a reason why it did not report those losses.
From information maintained by Internal Affairs, we examined whether in the cases reported to Internal Affairs: (1) the ATF employee immediately reported the loss or theft to a supervisor, (2) Internal Affairs investigated the incident, and (3) ATF took disciplinary action against the employee. We also reviewed whether the evidence indicated that the missing laptop contained sensitive or classified information. We summarize the results in the following chart.
ACTIONS TAKEN ON 53 LOST, STOLEN, OR MISSING LAPTOP COMPUTERS
REPORTED TO INTERNAL AFFAIRS18
OCTOBER 1, 2002, THROUGH AUGUST 31, 2007
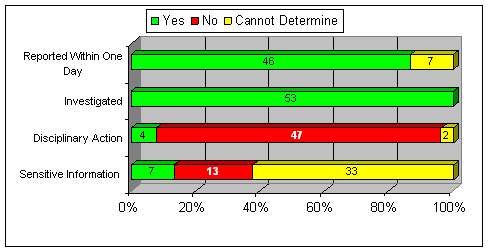
| Source: OIG analysis of ATF data |
We found that ATF investigated all lost, stolen, or missing laptop computers reported to Internal Affairs, although few of those investigations resulted in disciplinary actions against the employees responsible for the losses.
Contents of Lost, Stolen, or Missing Laptop Computers
ATF’s property management policy does not include written procedures requiring ATF to assess the contents of lost, stolen, or missing laptop computers. As explained below, we found that ATF did not regularly attempt to determine whether the lost, stolen, or missing laptop computers contained sensitive or classified information.
ATF’s Information Systems Security Officer from the Office of Science and Technology (OST) told us that staff from OST and Internal Affairs interview users about the content of lost, stolen, or missing laptop computers when staff report them missing. OST staff also told us the results of those interviews are documented in ATF Internal Affairs reports and incident reports submitted to DOJCERT.
We asked ATF for incident reports submitted to DOJCERT and ATF Internal Affairs reports on all 53 lost, stolen, or missing laptop computers reported to Internal Affairs. We did not ask for more than these 53 because we knew ATF did not have any records for the others.
ATF provided all 53 Internal Affairs reports. However, it provided DOJCERT reports for only 6 (11 percent) of the 53 laptop computers.19 Those reports indicated that ATF made inquiries into the contents of 20 lost, stolen, or missing laptop computers. Seven of the reports indicated that the lost laptop computers contained sensitive information, and 13 reports indicated that the lost laptop computers did not contain either sensitive or classified information.
ATF could not provide adequate information regarding whether the remaining 398 lost, stolen, or missing laptop computers contained sensitive or classified information. Without knowing the contents of lost, stolen, or missing laptop computers, ATF could not assess what damage these losses could have had on ATF’s operations or national security. Moreover, since ATF did not begin installing encryption software until May 2007, few if any of these lost, stolen, or missing laptop computers were encrypted.
Entering Losses of Weapons and Laptop Computers into NCIC
ATF policy requires that all lost, stolen, or missing weapons be entered into NCIC. It does not require that lost, stolen, or missing laptop computers be entered into NCIC.20
To test how often ATF’s lost, stolen, or missing weapons were entered into NCIC, we reviewed documentation during our audit for 72 of the 76 weapons.21 We found that seven lost, stolen, or missing weapons were not required to be entered into NCIC because the weapons were recovered shortly after being lost or stolen. Of the remaining 65 lost, stolen, or missing weapons, 5 were not entered into NCIC in accordance with ATF’s written policy. As of July 2008, ATF staff had not responded to our inquiry about why these losses were not entered into NCIC.
Ammunition and Explosives Losses
ATF has a policy for reporting the loss of explosives, but did not have a specific written policy for reporting the loss of ammunition at the time of our audit. ATF’s property management policy requires employees to report losses of government property assigned to them. An ATF official told us that policy covers losses of ammunition, which was specifically included in a revision issued in April 2008. However, the policy in place at the time our audit did not specifically include ammunition and stated that a record is established within the property management system for each property asset, and ammunition is not included in the system. Therefore, it appears that ammunition was property not covered by the property management policy during our audit period. An ATF Internal Affairs manager told us that individual circumstances, such as whether the ammunition was stolen in conjunction with a stolen weapon, dictate whether lost, stolen, or missing ammunition should be referred to Internal Affairs and whether Internal Affairs conducts a full internal investigation into the loss. Because expendable items such as ammunition and explosives are not included in ATF’s property management system, we could only identify losses that ATF staff reported to Internal Affairs.
Ammunition
ATF staff reported to Internal Affairs 12 instances of lost, stolen, or missing ammunition for the 59-month period from October 1, 2002, through August 31, 2007. Of the 12 incidents, 1 resulted in an employee receiving a Memorandum of Clearance and another resulted in the employee receiving discipline.22 There was no full report of investigation for the remaining 10 incidents because a preliminary investigation found no employee misconduct.
Explosives
ATF reported two instances of lost, stolen, or missing explosives to Internal Affairs during our review period. ATF opened preliminary investigations on both instances, but found no misconduct. The explosives were recovered in both incidents.
Internal Controls Over Weapons and Laptop Computers
DOJ Property Management Regulations require all DOJ components to conduct a physical inventory of all non-expendable personal property, which includes weapons and laptop computers, at least biennially. We determined that ATF had performed annual inventories of weapons and biennial inventories of laptop computers recorded in its automated property system.
We reviewed the ATF inventory reports for the two most recent fiscal years. The reports identified adjustments to the property records based on the physical inventories that were performed. ATF policy requires that shortages of property be reconciled, administrative changes be posted, and that a Report of Survey be prepared for items that could not be reconciled. However, we found that changes were not posted in the ATF’s property management system based on inventory reports. As a result, ATF kept many items on the active property list even though it no longer had the property.
Reconciling Property Records to the Financial System
ATF’s financial system is not integrated with its property management system and the two systems are not regularly reconciled. We therefore performed tests to determine whether weapons and laptop computer purchases recorded in ATF’s financial system were also recorded in its property management system.
We judgmentally selected from the financial system 4 purchases for 1,264 weapons valued at $737,133. We traced all the purchases to ensure that the items were entered into the property management system, and we found no discrepancies.
ATF had no laptop computer procurement records to test because its laptop computers are leased rather than purchased outright and entered into the financial system. ATF replaces laptop computers after 3 years with new leased computers, and ATF retains ownership of the laptop computers that are replaced.23 The ATF disposed of most of the replaced laptop computers, but ATF keeps a few of the replaced computers for special purposes. As a result, all ATF-owned laptop computers at the time of our audit were items that ATF had kept after their leases expired. Therefore, we were unable to determine the adequacy of ATFís controls for reconciling laptop computer property records to the financial system because the leased computers are not entered into the financial system.
Accuracy and Completeness of Property Records in the Property Management System
ATF’s property management system accounts for weapons and laptop computers, but we found that it was unable to account for all items located in the system. To evaluate the property management system, we tested weapons and laptop computers in two phases. First, we completed a 100-percent inventory of weapons and laptop computers at ATF’s Atlanta and Washington Field Divisions. We then performed a second phase of testing during which we selected from the property management system a statistical sample of weapons and laptop computers located at 14 field offices. We sought to verify the existence of all sampled weapons and laptop computers at the 16 locations tested.
We were able to verify all but 4 (less than 1 percent) of the 1,788 weapons in our sample, and all but 23 (2.2 percent) of the 1,032 laptop computers.
The following table summarizes the results of verification testing at each selected location. Items identified in the table as “Accounted For” are those that we were able to verify through either physical observation by auditors or confirmation memoranda from ATF officials verifying that they had viewed the equipment and confirmed the identifying information, such as manufacturer, model, and serial number or documentation showing that the item had been disposed of.
SAMPLE TESTING OF WEAPONS AND LAPTOP COMPUTERS
RECORDED IN THE ATF PROPERTY MANAGEMENT SYSTEM
| Location | WEAPONS | LAPTOP COMPUTERS | ||
|---|---|---|---|---|
| Accounted For | Unaccounted For | Accounted For | Unaccounted For | |
| Atlanta Field Div. (FD) | 331 | 0 | 237 | 1 |
| Washington FD | 519 | 3 | 229 | 5 |
| SUBTOTALS | 850 | 3 | 466 | 6 |
| Headquarters | ||||
| Glynco, GA | 92 | 0 | 67 | 2 |
| Landover, MD | 0 | 0 | 31 | 0 |
| Martinsburg, WV | 165 | 0 | 58 | 0 |
| Kansas City FD | ||||
| Kansas City, MO | 58 | 0 | 53 | 0 |
| St. Louis, MO | 84 | 0 | 30 | 2 |
| Los Angeles FD | ||||
| Los Angeles, CA | 96 | 1 | 49 | 12 |
| Riverside, CA | 31 | 0 | 16 | 0 |
| New Orleans FD | ||||
| Little Rock, AR | 36 | 0 | 21 | 0 |
| Metairie, LA | 59 | 0 | 36 | 1 |
| Shreveport, LA | 46 | 0 | 18 | 0 |
| Philadelphia FD | ||||
| Philadelphia, PA | 77 | 0 | 48 | 0 |
| Pittsburgh, PA | 66 | 0 | 35 | 0 |
| San Francisco FD | ||||
| San Francisco, CA | 64 | 0 | 56 | 0 |
| Las Vegas, NV | 60 | 0 | 25 | 0 |
| SUBTOTALS | 934 | 1 | 543 | 17 |
| TOTALS | 1784 | 4 | 1009 | 23 |
When we verified all weapons and laptop computers in the Atlanta and Washington Field Divisions, we also determined for each item whether the user and location of the property were accurately recorded in the property management system. Of the 1,316 items we verified in the Atlanta and Washington Field Divisions, we found that 217 (16 percent) had an incorrect user, incorrect location, or both in the property management system record, or the item was not included in the property management system at all.
We also tested the completeness of the property records by tracing weapons and laptop computers in the actual possession of a sample of field office staff back to the property records. For this analysis we selected a sample of 33 staff at 7 field offices.24 These 33 staff members maintained 44 weapons and 33 laptop computers in their possession. We traced each item to the property management system to determine if its records were correct. We found that the records for two weapons and four laptop computers reflected incorrect information on users or locations.
During our testing, we also identified items for which conflicting information was entered in the property records. For instance, the property management system database contains data elements to record the office to which the item is assigned and the specific location where it can be found, because some offices operate in multiple locations. We found property records that contained conflicting office and location information, in effect showing the item was in different locations at the same time.
Encryption
ATF began installing encryption software on its laptop computers in May 2007, and ATF staff told us that as of April 2008 ATF had completed the installation on all of its networked laptop computers. The majority of ATF laptop computers are networked and assigned to individuals as personal property.
During our review of accountable property, which occurred from August 2007 through December 2007 and prior to ATF’s reported completion of encryption installation, we tested to determine if ATF had installed encryption software on sampled laptop computers. Of the 1,065 laptop computers tested, 63 were unencrypted. Of the 63 unencrypted laptop computers, 42 were used for a dedicated purpose, such as Global Positioning System tracking and video surveillance. ATF personnel told us they do not store sensitive information on these laptop computers. However, the remaining 21 unencrypted laptop computers were assigned to users, such as Special Agents who may have processed sensitive information.
We were unable to test the encryption status of 441 laptop computers because they were verified by confirmation memorandum (180), were unaccounted for (23), or the user was not available to access the encryption software (238).
DOJ regulations have required that all classified information on a laptop or standalone computer be encrypted. We reviewed the encryption status for ATF’s classified laptop computers and found that 5 of the 18 classified laptop computers we tested were not encrypted. By not encrypting classified laptop computers, ATF did not comply with DOJ policy and risked compromising classified information. As of April 2008, ATF reported that it was in the process of encrypting the five unencrypted classified laptop computers.
Reporting Requirements for Laptop Computers Containing Classified Information
Since March 2004, the DOJ Chief Information Officer (CIO) has required all DOJ components, including ATF, to report annually the number of laptop computers it has authorized for processing classified information. However, the DOJ CIO only received a submission from ATF in 2007, and none for any prior years. An ATF official told us that ATF may not have known about the requirement to report classified laptop computers to DOJ.
ATF’s 2007 submission included 13 classified laptop computers. However, during our audit we found that ATF had 18 classified laptop computers. The additional five laptop computers were the same five described above as being unencrypted.
Reporting Property Losses to DOJ
DOJ requires all components, including ATF, to submit semiannual reports summarizing thefts of government property during the preceding 6 months. In the 5 years after it transferred into the Department, ATF never submitted a semiannual report to DOJ summarizing thefts of government property. The Justice Management Division (JMD) sent follow-up correspondence to ATF in 2005, 2006, and 2007 reminding it to submit the semiannual reports, but ATF never submitted the required reports. An ATF official told us that ATF never submitted the semiannual reports because the property management system did not allow ATF to consolidate the loss information. He further stated that ATF is in the process of updating its property management system so that it will be able to consolidate loss information in the future. We have asked JMD about this response and are awaiting its answer. Moreover, in our judgment, ATF could have prepared the required semiannual reports using ATF Reports of Survey.
Department of Justice Computer Emergency Response Team
Since March 2005, DOJ has required all components, including ATF, to submit immediate reports summarizing incidents involving the loss of both classified and unclassified systems to DOJCERT. DOJCERT assists in handling computer security incidents throughout DOJ. ATF also requires such incidents to be reported to its Internal Affairs office.
We used the incidents reported to Internal Affairs to determine if all incidents of lost, stolen, or missing laptop computers reported internally to ATF had been reported to DOJCERT. We identified 53 laptop computer losses that were reported to Internal Affairs, of which 16 occurred prior to the DOJCERT reporting requirement, leaving 37 incidents that should have been reported. We found that 21 of the 37 had been reported to DOJCERT, while 16 were not reported as required.
As of July 2008, we had not received a response from ATF on the reasons why those 16 laptop computers were not reported to DOJCERT. Reporting of these incidents is an important step to ensure that appropriate actions can be taken as soon as possible to mitigate the consequences of laptop computer losses.
Disposed Weapon and Laptop Computer Records
We reviewed a sample of records of ATF disposed weapons and laptop computers to determine if the dispositions were supported by appropriate documentation. Weapons and laptop computers recorded in the property management system as disposed include items that are destroyed, transferred to another agency, lost, stolen, exchanged, donated, or returned. Weapons and laptop computers that are identified as missing during a physical inventory are also removed from active status in ATF’s property management system and recorded as disposed items.
We examined whether records for each of the sampled 297 weapons and laptop computers included the proper support documentation and whether each document contained the appropriate authorizations for each disposal. Our review found that ATF was unable to provide documentation supporting proper disposition for 5 (5 percent) of 99 disposed weapons and 21 (12 percent) of 170 disposed laptop computers.
Officials at the ATF Materiel Management office told us that the records supporting the removal of all 5 unsupported weapons and 10 of the 21 unsupported laptop computers from the active property records were misplaced when ATF moved to its new headquarters building in August 2007. In addition, two laptop computer disposals did not include all required signatures and nine did not have the Property Identification Numbers listed on the disposal documents.
Not “clearing” data on laptop computers prior to disposal exposes ATF to security risks. Before laptop computers are disposed of, ATF policy requires the property custodian and the property accountable officer to ensure that hard drives are cleared and a Certificate of Data Clearing is prepared. However, ATF could only provide these certificates for 4 (3 percent) of 116 laptop computers we tested. While ATF officials told us they believe that most of the hard drives were cleared of data, the data clearing status for 97 percent of the disposed laptop computers was not documented and therefore could not be confirmed.
Exit Procedures for Departing Employees
On or before an employee’s last day of employment, an ATF supervisor or other designated official is required to collect property issued to the employee, including weapons, ammunition, and laptop computers. The supervisor is supposed to complete and sign a separation checklist, and provide copies to the employee and the personnel office.
We requested the separation checklists and property information for a sample of 30 former employees. ATF could provide only 6 of the 30 separation checklists, and we found no information on the 6 separation checklists specifying the property being returned. The separation checklist provided to us includes only a statement certifying that the supervisor received all property from the separating employee. In addition, ATF’s property management system does not allow a query to determine the property that the separating employee possessed.25 As a result, ATF has no documentation showing whether all of the property assigned to separating employees has been recovered. Consequently, we were unable to test to ensure that separating employees returned all weapons and laptop computers prior to their separation from ATF service.
Internal Controls Over Ammunition
In 2002, the Treasury OIG reported that ATF had limited written policies regarding controls over ammunition, no standard recordkeeping, and no physical inventories. As a result of the Treasury audit, in May 2002 ATF issued new policies in ATF Memorandum 1851, Ammunition Inventory, requiring ATF divisions to perform an annual inventory – assisted by a “disinterested person” – of all ATF-owned ammunition and to maintain a perpetual inventory system for ammunition.
We sought to review the last two annual ammunition inventories. However, we were unable to perform the review because ATF could not produce documentation from any ammunition inventories. As of July 2008, ATF officials had not provided us with the required documentation, and have not directly answered why they cannot provide the documentation.
We also reviewed ammunition at 20 ATF offices where we tested weapons and laptop computers. Of the 20 offices, we found that 11 maintained perpetual inventory records for ammunition, as required, and 9 did not. For the 11 offices that maintained perpetual records, the records in 5 of the offices were accurate regarding ammunition, while the records in the 6 other offices contained inaccuracies. One of those 6 offices had significant inaccuracies in all but one type of ammunition, including records for one caliber ammunition that undercounted 478,400 rounds. The inventory was apparently not updated as transactions occurred. The official responsible for the ammunition believed the missing ammunition had probably been given to the military. While this may be correct, ATF has no way of verifying what happened to the missing ammunition without a record of the transactions.
The nine offices that did not maintain perpetual inventories and the one office that had significant deficiencies in its records did not follow ATF procedures to account for all stored ammunition. For example, an agent in an office that did not keep complete perpetual records said he believed that the requirement to keep the perpetual records had been rescinded, a statement ATF headquarters had not confirmed. As a result of not keeping accurate perpetual records, ATF risks the undetected loss of ammunition.
Reconciling Ammunition Records to the Financial System
During our review, we selected 12 shipments of ammunition to trace from purchase through distribution to ammunition inventories at 8 locations. We were unable to trace any shipment into inventory records at any of the eight receiving locations. Although ATF policy requires the maintenance of perpetual records, five of the eight locations did not keep ammunition inventory records. At two of the other field offices, records were retained for only the previous year, which did not include the tested shipments. At the headquarters ammunition facility (the eighth location), an agent told us that the shipment may have been intended for the Baltimore office and would not have been recorded on the headquarters facility inventory.
Physical Security
The Treasury OIG’s 2002 audit reported that ATF had satisfactory procedures for ensuring the physical security of its ammunition. Our audit concluded that ATF continued to have proper physical security over ammunition. We found that ammunition was stored and secured using various methods depending on the size of the ATF office we tested. Smaller ATF field offices kept ammunition stored in vaults within the office space. The vaults had key card access with alarm systems and only ATF personnel had access to these vaults. Larger field offices and divisions kept ammunition in warehouse facilities or at a firing range. The warehouse facilities stored other equipment items in addition to ammunition.
Internal Controls Over Explosives
The Treasury OIG’s 2002 audit reported that ATF controls over the physical inventories of explosives lacked independence because they did not include personnel who were independent of daily responsibility for the explosives. In response to the finding, ATF required that a disinterested person participate in all future inventories of explosives. ATF also mandated that a perpetual record of each type of ATF-owned explosive be maintained.
We reviewed 16 ATF locations and found that each kept perpetual inventory records of explosives as required. At each location, we compared the perpetual records for each type of explosive to the actual inventory stored at the location. We found that eight of the locations had accurate perpetual records and eight had inaccuracies. In addition, ATF’s Explosives Industry Operations Section performs annual inspections of all ATF explosives magazines, which include a physical inventory review by “disinterested” persons independent of daily responsibility for the magazines.
We concluded that ATF’s controls over explosives were adequate. All offices kept perpetual explosives inventory records as required, each magazine had an annual independent inspection that included an inventory review by an independent person, and we only found minor discrepancies.26
Reconciling Explosives Records to the Financial System
We reviewed the two ATF purchases of explosives that occurred within our audit period, both of which were sent to the ATF’s K-9 training facility. We were able to trace both shipments from the invoices to the perpetual log at the training facility. Therefore, we were able to reconcile the purchases of explosives to the explosives inventory.
Physical Security
Storage of explosives is regulated by ATF’s Explosives Industry Operations Section. We found explosives storage was uniform among the ATF offices we visited. In ATF Memorandum 5400, ATF required an independent physical security review of all magazines that found all magazines reviewed were secured. Therefore, we concluded that ATF’s physical controls over explosives were adequate.
Conclusion and Recommendations
Our audit found significant increases in the ATF’s rate of loss for weapons and laptop computers since the Treasury audit was issued in 2002, and the ATF’s rate of loss for weapons was nearly double the rates of loss for the FBI and DEA. In addition, ATF staff did not follow established policy to report many lost, stolen, or missing weapons and laptop computers to ATF Internal Affairs, investigate losses, or enter reports of lost, stolen, or missing weapons into NCIC. We also found that ATF did not know whether most of its lost, stolen, or missing laptop computers contained sensitive or classified information.
We concluded that ATF’s controls over weapons and laptop computers were not adequate. ATF did not maintain accurate and complete records in its property management system or maintain support documentation for disposed weapons and laptop computers, nor did it document that laptop computer hard drives were cleared prior to disposal. In addition, ATF could not locate all of the active weapons and laptop computers sampled for review. It also did not report to the DOJ CIO the number of laptop computers authorized to process classified information or report all weapon and laptop computer losses to DOJ and all laptop computer loss incidents to DOJCERT, as required. Furthermore, we determined five of ATF’s classified laptop computers were not encrypted. In addition, ATF could not provide documentation to show that it received all weapons and laptop computers from separating employees.
We determined that ATF’s controls over explosives were adequate. However, we identified continued weaknesses in controls over ammunition. Although ATF had developed written procedures to enhance controls over ammunition in response to the 2002 Treasury audit, ATF failed to enforce its policy to perform annual inventories of ammunition and maintain accurate and complete perpetual ammunition inventory records.
Our audit report makes 14 recommendations for ATF to improve its controls over weapons, laptop computers, and ammunition. The recommendations include that ATF follow established policy to report all weapons, laptop computers, and ammunition losses to Internal Affairs and ensure that all necessary information for investigation is complete and accurate. Also, ATF should ensure that it is able to determine the contents of all lost, stolen, or missing laptop computers. In addition, ATF should maintain accurate and complete records in its property management system. Furthermore, ATF should enforce current requirements to perform annual inventories of ammunition and to maintain accurate and complete ammunition records.
Footnotes
U.S. Department of Justice, Office of the Inspector General, The Department of Justice’s Control Over Weapons and Laptop Computers Summary Report, Audit Report 02-31, (August 2002).
ATF’s law enforcement functions became part of the Department of Justice on January 24, 2003, as a result of the Homeland Security Act.
U.S. Department of the Treasury, Office of Inspector General, Protecting the Public: Bureau of Alcohol, Tobacco and Firearms’ Control over Sensitive Property Is Adequate, Audit Report 02-097, (June 2002).
The ATF policy does not define “disinterested person.” The Treasury audit report defined the term as a person who is independent of daily responsibility for the inventory and independent of the custodial function. In this report, we have used ATF’s terminology when citing the requirement.
See, e.g., U.S. Department of Justice, Office of the Inspector General, The Federal Bureau of Investigation’s Control Over Weapons and Laptop Computers Follow-Up Audit, Audit Report 07-18, (February 2007) and U.S. Department of Justice, Office of the Inspector General, The Drug Enforcement Administration’s Control Over Weapons and Laptop Computers Follow-Up Audit, Audit Report 08-21, (March 2008).
Materiel” is a term used to refer to equipment and supplies, especially in military organizations, which is also used by ATF.
Encryption software protects information on computers so that the information is unreadable without proper authorization.
Perpetual inventory is an inventory accounting system in which book inventory is updated continuously, as opposed to periodic inventories in which updates are made on a recurring basis.
ATF staff told us the records for 8 of the 10 weapons and for 78 of the 86 laptop computers were destroyed in accordance with ATF’s written policy that personal property records are to be destroyed 3 years after the property is disposed of. ATF staff could not locate the other records.
Laptop computers identified as missing during an inventory were generally not reported to Internal Affairs. We could not determine the circumstances for weapons not being reported because ATF could not provide documentation about 10 of the 13 weapons not reported to Internal Affairs. The other three were reported missing on Reports of Survey and were treated as inventory adjustments.
We know from the property management system that these items were removed based on Reports of Survey. ATF staff told us the records for 8 of the 10 weapons and for 78 of the 86 laptop computers were destroyed in accordance with ATF’s written policy that personal property records are to be destroyed 3 years after the property is disposed of. ATF staff could not locate the other records. Later in this Executive Summary and in Finding I, we discuss concerns regarding reporting items to Internal Affairs.
ATF policy requires that lost, stolen, or missing weapons and laptop computers be reported to a supervisor “immediately.” ATF did not further define what was meant by immediately. We considered a loss to have been reported “immediately” if it was reported within 1 day.
For a comprehensive list of lost, stolen, or missing weapons, see Appendix III.
DOJ policy refers to reporting losses to a Board of Survey. DOJ does not require apparent inventory processing discrepancies to be referred to a Board of Survey.
For a comprehensive list of lost, stolen, or missing laptop computers, see Appendix IV.
ATF provided DOJCERT reports for nine other lost, stolen, or missing laptop computers. Four were lost, stolen, or missing during the period covered by our audit and five were lost, stolen, or missing after the period covered by our audit.
We found that while DOJ policy does not require that lost, stolen, or missing laptop computers be entered into NCIC, the FBI and DEA both have policies that require that lost, stolen, or missing laptop computers be entered into NCIC.
We were unable to test whether four lost, stolen, or missing weapons were entered into NCIC.
A Memorandum of Clearance clears the employee of any wrongdoing. This disciplinary action was the result of an investigation that also included review of a weapon loss.
This refresh cycle of 3 years is normal in the information technology industry. The monthly lease amount per computer was $310, which includes $77 for the laptop and $233 for support services such as managing the server and providing data security and round-the-clock technical support. Because ATF leased laptop computers and was billed monthly, ATF had no laptop computer purchasing records to test.
We performed this test at 7 of the 14 field offices (excluding Atlanta and Washington) because all of the personnel at the other 7 locations were already included in another sample we used to trace items from the property records to the person.
We were not able to use the property management system to identify items associated with each separating employee because names are not recorded in a standard format and no other identifiers, such as employee numbers are used.
A magazine is a secured storage container for explosives. See the photograph of an explosives magazine in Finding III.